2024-6-4 16:47:35 Author: securityboulevard.com(查看原文) 阅读量:0 收藏
As technology continues to revolutionize healthcare operations, protecting patient data has never been more challenging. In the ongoing struggle against data breaches, last year marked a tipping point, as an unprecedented 133 million healthcare records were breached, according to the HIPAA Journal.
In this blog, we will delve into the HIPAA compliance framework, with a particular focus on the sections around access control and MFA and how adding identity security controls across your organization can help you comply with HIPAA.
What is the HIPAA Act
HIPAA, the Health Insurance Portability and Accountability Act, is a crucial piece of legislation enacted in 1996 in the United States. Its primary objective is to safeguard individuals’ medical information, ensuring the privacy and security of their health data. HIPAA’s relevance to healthcare providers cannot be overstated, as it mandates strict guidelines for handling sensitive patient information.
One of the core aspects of HIPAA compliance is the protection of electronic protected health information (ePHI). ePHI includes any electronic health information that identifies an individual and is transmitted or maintained by a covered entity or business associate. This encompasses a wide range of data, from medical records and billing information to patient demographics and lab results. Securing and protecting these sensitive patient data and records against malicious actors is critical.
Access control and multi-factor authentication (MFA) are crucial elements in preventing unauthorized access to ePHI and achieving HIPAA compliance. Let’s dive into the specifics.
Access Control Requirements
According to HIPAA’s Security Rule, which states “HIPAA-covered entities must implement the appropriate administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and security of electronic protected health information (ePHI),” organizations are required to implement technical safeguards to protect ePHI. These technical security approaches must include an access control system to ensure only authorized individuals can access ePHI.
HIPAA requires organizations to implement the following access control measures:
- Policies and procedures for electronic information systems that maintain ePHI to allow access only to authorized users, programs, processes, or other systems. Admin controls involve establishing policies, procedures and guidelines for managing user access. Technical controls utilize solutions such as authentication systems, encryption, and access logs to control electronic access. Physical controls restrict physical access to facilities and equipment where ePHI is stored or processed.
- Role-based access control (RBAC) is a common approach used to manage access to ePHI within healthcare organizations. RBAC assigns permissions based on users’ roles and responsibilities, ensuring individuals only have access to the information necessary to perform their job functions.
Enforcing Access Controls in HIPAA
In accordance with the Security Rule, organizations must develop written policies and procedures for granting access to ePHI. Policies and procedures must also specify who has access to what information and how these access points will be tracked and monitored.
To comply with the Security Rule, organizations must enforce:
- Processes to grant and deny access to ePHI.
- Access must be granted only to individuals with a business reason to use the ePHI.
- Ability to revoke access when no longer needed.
- Regularly monitoring to ensure access is granted and withdrawn in a timely manner.
In addition, organizations must be able to protect ePHI in the event of a security breach by, for example, encrypting personal information during storage and transmission and implementing an emergency access procedure.
Lastly, in terms of access controls, organizations must maintain an audit trail that records who has accessed ePHI. This audit trail must contain information regarding when and by whom access was granted and revoked, as well as what data was accessed.
Strong Authentication for HIPAA
While the HIPAA Security Rule does not specifically mandate the use of MFA, HIPAA mandates the implementation of “reasonable and appropriate” security measures to protect patient data. MFA aligns perfectly with these requirements, providing robust access control and an additional layer of security that helps healthcare organizations meet HIPAA’s stringent security mandates.
Here’s how HIPAA addresses strong authentication and recommends MFA as a security best practice:
- Strong Authentication Requirement: HIPAA’s Security Rule requires covered entities to implement procedures for verifying the identity of users seeking access to ePHI. This includes the use of authentication methods that are “reasonable and appropriate”.
- Recommendation of MFA: MFA is a security best practice for enhancing authentication and access control. The Department of Health and Human Services (HHS), which enforces HIPAA, has issued guidance recommending the use of MFA as part of a comprehensive security program.
- Flexibility in Implementation: HIPAA allows covered entities to determine the most appropriate authentication measures based on their specific risk factors, organizational size, complexity, and capabilities. Even though MFA is not explicitly mandated, HIPAA offers organizations the flexibility to choose the authentication methods that best meet their security needs and risk profile; for example, passwords, biometrics, tokens, or MFA.
Strengthening HIPAA Compliance with Silverfort
Access Control System
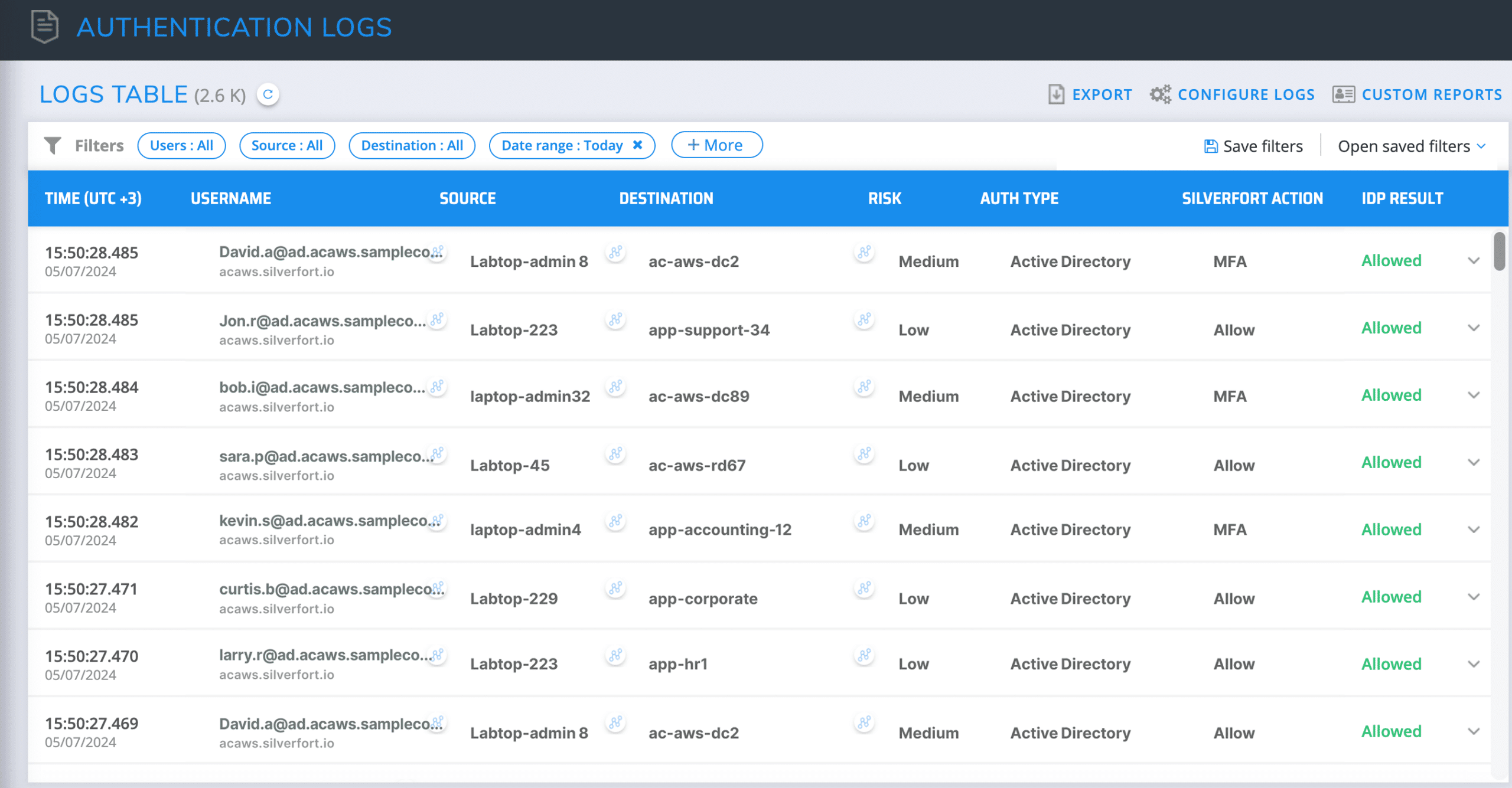
To answer HIPAA’s access control requirements, Silverfort’s continuous authentication capabilities monitor and analyze user behavior in real time. Silverfort detects user behavior, devices, locations, and other risk factors to calculate the risk score of each user authentication request. If any unauthorized or abnormal behavior is identified, the system can take immediate action, such as terminating the session or requesting additional authentication. This means that access to ePHI can be tightly controlled, ensuring that only authorized individuals have access to sensitive data, which is a critical requirement of HIPAA.
Applying Access Policies
With Silverfort, organizations can configure user access policies in compliance with HIPAA regulations. Access policies are configured based on users, groups, and organizational units (OUs), as well as the least privileges necessary for your systems, processes, and applications. By implementing these policies, organizations can gain full visibility into user accounts, access requests, and authentications, as well as create and monitor log files to detect malicious or irregular activities.
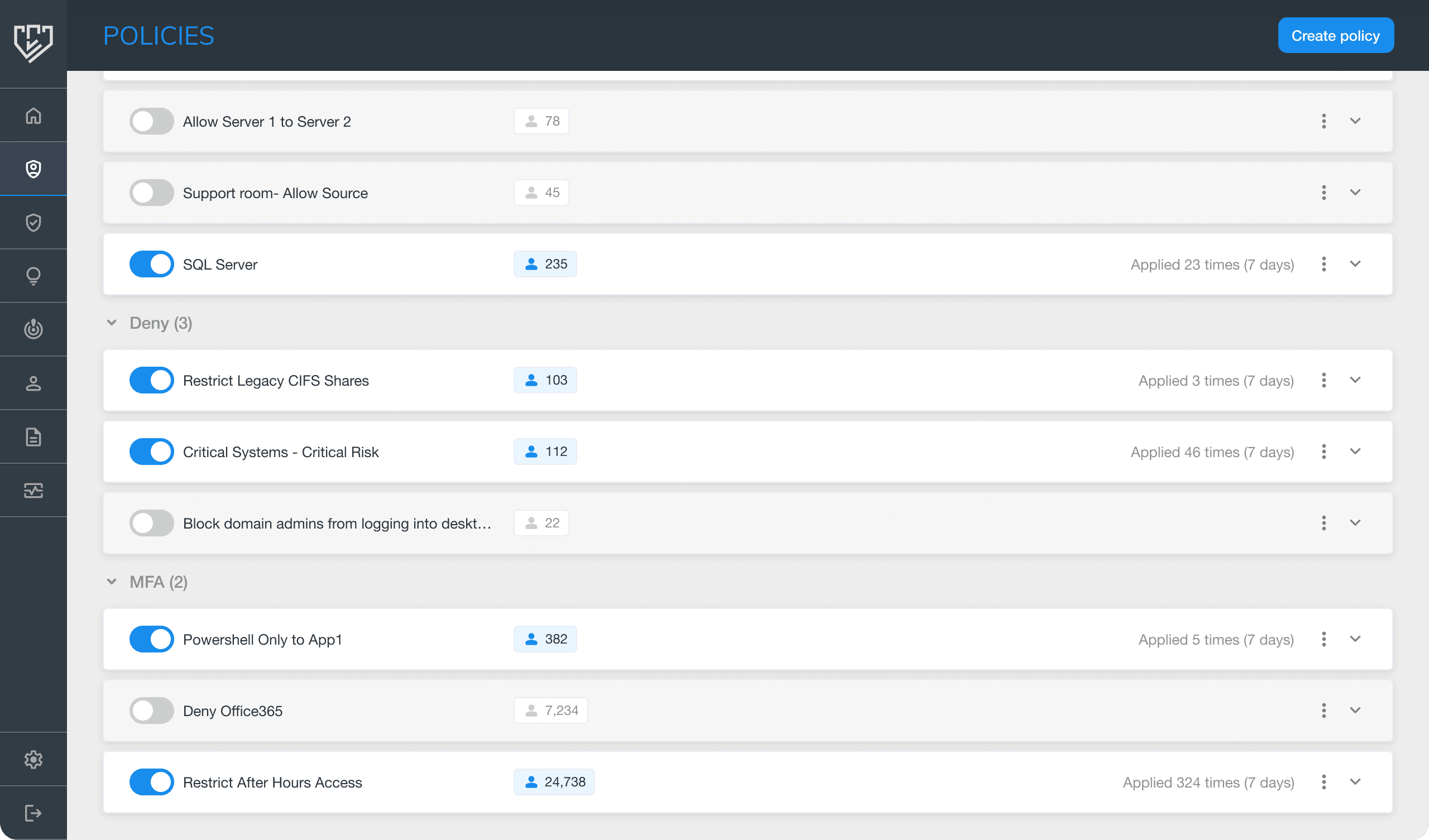
For example, Silverfort’s system can require MFA for each access request based on continuous analysis of user behavior, devices, locations, security events, and other risk factors. By doing so, access to ePHI can be properly managed and protected while ensuring that only authorized users will have access to sensitive patient information, as required under HIPAA.
Enforcing MFA Protection
To comply with HIPAA’s requirement of strong authentication, Silverfort can enforce MFA protection across all users and resources, on-prem and in the cloud. This applies to all authentication to identity providers (IdPs) including Active Directory and those that couldn’t be protected by MFA before, such as legacy applications, command-line access, databases, networking infrastructure, and many others. Silverfort’s strong authentication capabilities are achieved through access policies. Silverfort ensures no access is granted based on passwords alone, and users are required to authenticate through MFA to verify their identity.
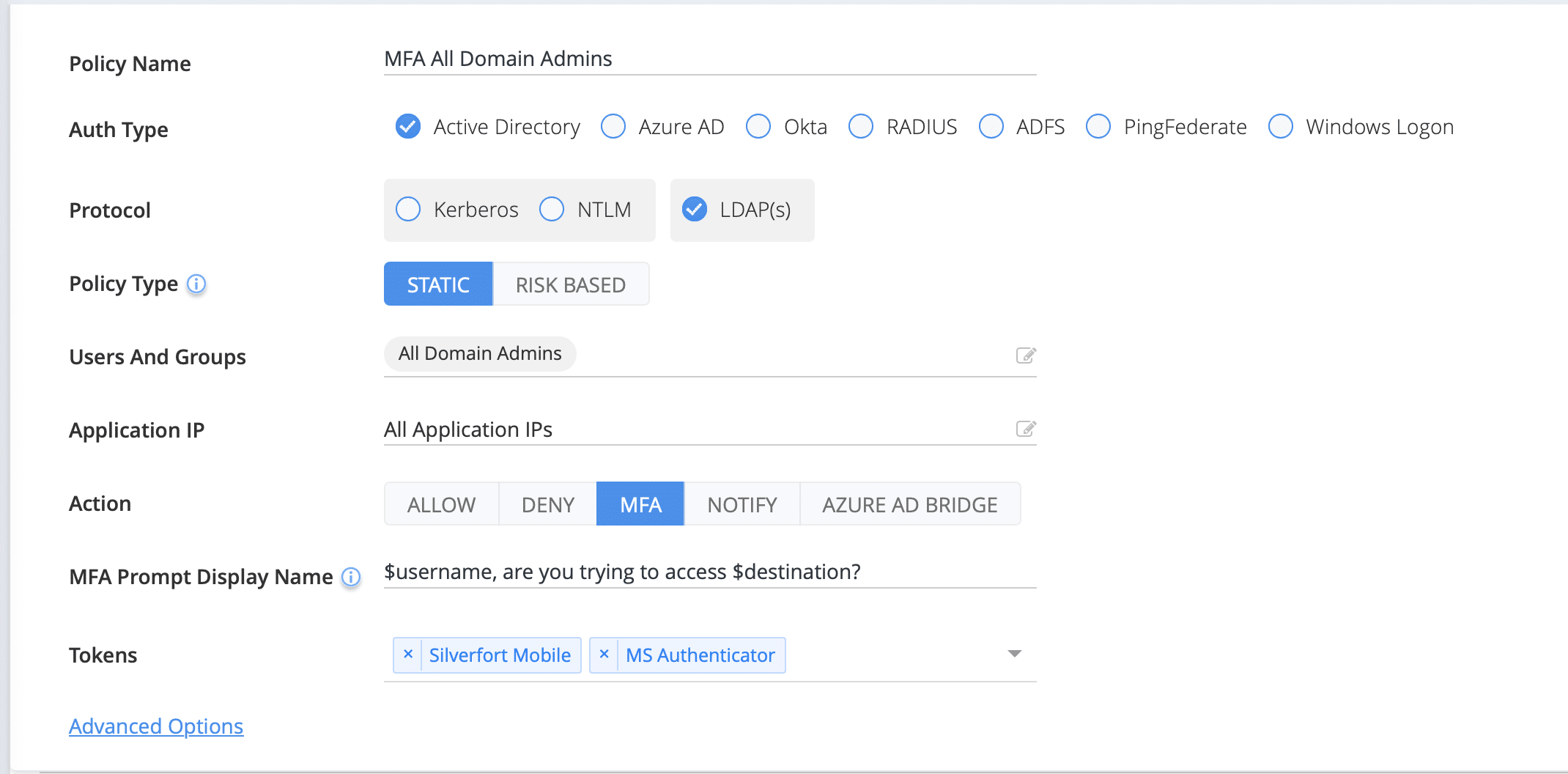
The strong authentication via MFA protection aligns with HIPAA requirements, which mandate that only authorized individuals should have access to ePHI. By requiring MFA for each access request, Silverfort ensures that access to ePHI is strictly monitored with the proper security controls, as required by the HIPAA regulations.
Want to learn more about how Silverfort can assist you in complying with HIPAA requirements? Schedule a call with one of our experts or fill out this form for a pricing quote.
The post Unlocking HIPAA Compliance: Navigating Access Control and MFA Guidelines appeared first on Silverfort.
*** This is a Security Bloggers Network syndicated blog from Silverfort Blog - Cyber Security News authored by Zev Brodsky. Read the original post at: https://www.silverfort.com/blog/unlocking-hipaa-compliance-navigating-access-control-and-mfa-guidelines/
如有侵权请联系:admin#unsafe.sh