2024-6-5 07:42:20 Author: hackernoon.com(查看原文) 阅读量:2 收藏
Have you ever wondered what happens to stolen data when it goes to the Dark web? Or how does someone purchase stolen data? or maybe the inner workings of currency when a purchase is made? In today's interconnected world, the theft of data has become an increasingly prevalent issue, with cybercriminals constantly seeking new ways to exploit vulnerabilities and accelerate gains.
In "From Hack to Sale: The Journey of Stolen Data," we will journey into the world of cybercrime, tracing the path that stolen data takes from its initial breach to its sale on the dark web.
The Breach
Stolen data begins its journey at the breach stage. The breach stage is where a cybercriminal accesses the company’s network and steals the company’s data. The breach stage can be attributed to many factors such as:
- An unpatched vulnerability that gets exploited.
- Stolen credentials bought on the dark web.
- Access to devices without Multi-Factor Authentication (MFA).
- Phishing attacks and much more.
Reconnaissance for Data to Steal
After a cybercriminal has access to the company’s network, they will need to scan/locate sensitive data to exfiltrate. Always keep in mind that once a cybercriminal has access to a network, they do not know where they are currently positioned. They will need to run a series of network commands and scanning tools to locate data to sell. This is achieved through various methods:
Executing various network reconnaissance/user enumeration commands to reveal access the current user possesses.

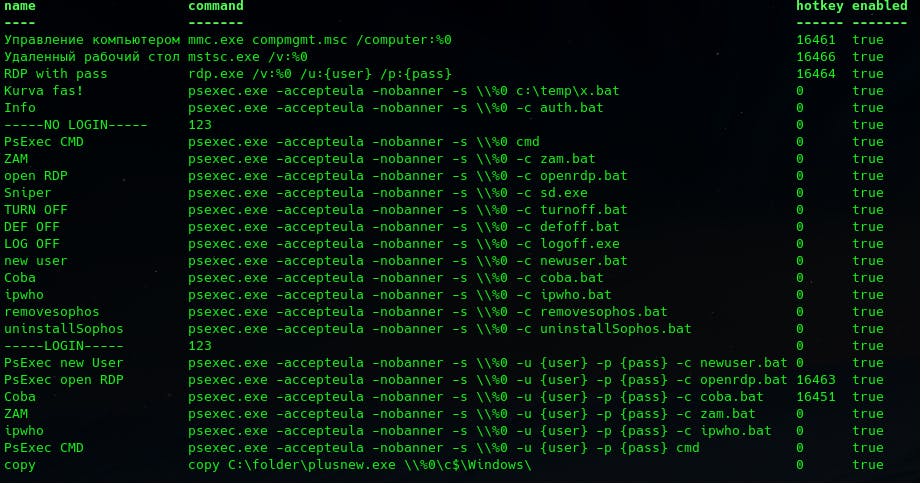
After these first commands, the threat actor employs tools such as Netscan to perform network discovery and network enumeration. SoftPerfect Network Scanner, also known as NetScan, is a multifunctional network scanning tool that detects devices and open ports on a network, identifies file shares, provides IP configuration details, integrates security features, has an intuitive graphical user interface, enables report generation and data export, supports SNMP protocol and offers scripting options for automating network scanning tasks.

Once the cybercriminal has enumerated write-access network shares, they will start browsing remote file shares via a web browser for sensitive information or other means to identify sensitive information. Remember, once a cybercriminal identifies a write-access share, they still need to locate files to exfiltrate during the attack.

The last stage after collecting all sensitive files is exfiltration. Data exfiltration occurs in various ways and through multiple attack methods. Exfiltration most typically occurs over the internet or on a corporate network. The techniques cyber criminals use to exfiltrate data from organizations’ networks and systems are becoming increasingly sophisticated, which helps them avoid detection.
These include anonymizing connections to servers, Domain Name System (DNS), Hypertext Transfer Protocol (HTTP), Hypertext Transfer Protocol Secure (HTTPS) tunneling, direct Internet Protocol (IP) addresses, fileless attacks, and remote code execution. Common data exfiltration cyberattack techniques include the following:
- Rclone - Open-source tool that can legitimately be used to manage content in the cloud but has been seen being abused by ransomware actors to exfiltrate data from victim machines. For an example of how Rclone may be used, see the case study below.
-
AnyDesk: A legitimate remote desktop application. By installing it, attackers can obtain remote access to computers on a network. Malicious usage of AnyDesk is now a well-known TTP and, in some cases, attackers will attempt to avoid raising suspicions by renaming the AnyDesk executable to something that may appear more innocuous, a technique known as masquerading.
-
Cobalt Strike: An off-the-shelf tool that can be used to execute commands, inject other processes, elevate current processes, impersonate other processes, and upload and download files. It ostensibly has legitimate uses as a penetration-testing tool but is invariably exploited by malicious actors. Cobalt Strikes has been used for data exfiltration, with attackers leveraging Cobalt Strike's Beacon payload to establish covert communication channels with compromised systems, allowing them to exfiltrate sensitive data stealthily.
The tool's ability to mimic normal network traffic and blend in with legitimate activity enables attackers to surreptitiously transfer valuable information from compromised networks.
-
ScreenConnect: A remote desktop application tool by ConnectWise, used to enable remote access to computers.
-
Atera: Legitimate remote monitoring and access software. It and similar tools are often used by attackers to obtain remote access to computers on a network.
- Chisel: Chisel is an open-source proxy tool. It was designed to create encrypted, tunneled connections, commonly used in network security testing and penetration testing scenarios. However, it has been abused during ransomware attacks to create tunnels to attacker-controlled infrastructure as part of data exfiltration activities. It creates a TCP/UDP tunnel that is transported over HTTP and secured via SSH.
- PowerShell: Microsoft scripting tool that can be used to run commands, download payloads, traverse compromised networks, and carry out reconnaissance. In several ransomware attacks, the attackers have executed specific commands in order to facilitate data exfiltration, including the use of the Compress-Archive cmdlet:
During the exfiltration stage, the cybercriminal will need to have a file storage location to store the stolen data before they sell it on the dark web marketplace. Once they are finished exfiltrating the data, they will move to the dark web marketplace to sell the data. There are numerous file storage locations a cybercriminal can use, but I will list a few below. Cybercriminals will also store the stolen data on their server if there are issues finding a location.

The Dark Web Marketplace
Despite what you might think, cybercriminals do not store the stolen data on the dark web marketplaces. It is used as a sales medium between the seller and the buyer. After the cybercriminal has moved the data to the determined file storage location, they will go online to one of many dark web marketplaces to sell the data.
This is also usually followed by the cybercriminal claiming the breach and alerting the company that they will need to pay to get their data back or they will sell it to the highest bidder. Below is an example of a data breach made public recently.

Once the cybercriminal has made the breach public, they will sell the data in the sellers’ market section of the marketplace. Before they can actually sell the data, they must abide by the rules of the marketplace unless they become banned. Below is an example of the marketplace rules for selling data.


Selling Data to the Highest Bidder
Selling stolen data is a complex process for many reasons, and most of them pertain to authenticity and trust. The buyer has to believe that the data is authentic and trust the seller. There are news articles that discuss such issues of cybercriminals stating they have stolen data but in actuality, they do not.
According to blackbird.ai, one such breach was Sony. Sony has endured numerous verified high-profile security incidents, such as the massive 2011 PlayStation Network hack that leaked 77 million user data. This denigrated public opinion of their security operations and trust in the company’s ability to handle customers’ personal identifying information.
The damage a cyberattack can exhibit was exacerbated on September 25th, 2023, when a threat actor collective called Ransomed.VC claimed on a dark web forum to have breached Sony’s systems. They threatened to release the stolen data on September 28th, contingent upon paying an undisclosed ransom.
Sony launched an investigation but revealed these claims were exaggerated, signifying that the incident appeared to be a clout-chasing hoax. Despite the discredited claims, the brand suffered reputational and financial damage. Social media narratives had already formed, and many validated these assertions due to Sony’s prior history.
To sell the data, the seller needs to create a selling profile and list the demands for transactions and the method of payment. This usually involves the type of bitcoin of choice or payment process such as “Middleman through escrow” which we will discuss later on in the article.

One item to remember, especially for companies that believe they can buy back their data. Some cybercriminals will only sell certain data to other members that have a known reputation and appear trustworthy. This means the person who wants to buy the data must have a high rank in the forum and be known to other members. If you are a company trying to buy back data and you are not known or have rank, you will not be able to buy it back.

Buying Stolen Data
Once the buyer has reached out to the seller and a deal has been struck, the deal will move to the transaction stage. This usually involves the currency of choice and the use of middleman escrow service. Most of the transactions involve “Monero” bitcoin. Monero is a popular altcoin based on the crypto note protocol that is recognized as the most anonymous cryptocoin available at present. The seller will then ask to use the middleman escrow service through the forum.
According to socradar.io, “the middleman takes data and money and then checks whether what parties provided satisfies the other side’s criteria, and you guessed it right! The middleman does that in exchange for a commission. The usual deal in the market is that the buyer pays for the commission. Nevertheless, is the system safe?

No. There is no way to understand or prevent if a middleman stores the data or seizes the money. On the other hand, these middlemen usually are someone who has a good reputation on the dark web. Considering that people have been there just by their nicknames, having a good reputation is the only virtue one can have anonymously.
Therefore, none of the middlemen usually attempt to do such a thing because they are paid for what they do. It’s also worth mentioning that losing your reputation has much more severe consequences compared to the average transaction amounts on the market and that to build a reputation, one must be a well-known threat actor who has been selling or buying data on the market for a while. So, it is a long and costly process.”
When the escrow process is complete and the currency has been exchanged, the cybercriminal will give the buyer a link or directions to download the stolen data. An example would be a link to Mega.io or some other cloud storage locations mentioned previously in this article.
Cybercriminals have been known to use several services or pay for legitimate services to store data. They will also host a separate server to house the data if they run into issues. Below is a screenshot of a conversation where cybercriminals were having issues storing stolen data.

Final Thoughts.
Understanding the buying and selling process of stolen data is an advantage to the cybersecurity community. It gives a perspective that is widely missed due to fear or misunderstanding. By knowing how to buy or sell stolen data, you will have the ability to make tough business decisions about stolen data. Decisions that can decide the future of your company or even your future.
Anytime you must go to the dark web to inquire or purchase data that belongs to you or your company, always remember you are at the mercy of the marketplace and the cybercriminal who stole your data in the first place. There is no honor among thieves and paying a ransom is never a guarantee.
如有侵权请联系:admin#unsafe.sh