Two releases of 2024 are already behind us, but we’re not slowing down! We hope you’ve enjoyed the features delivered in recent months, including QR codes extraction from PDF files, URL extraction from OneNote documents, support for STIX 2.1 in Analysis Reports, as well as our continuous enhancements and research to Signature & Detection. You can read about the latest Detection Highlights here.
Now, without further ado, let’s dive into our latest achievements of the 2024.3.0 release.
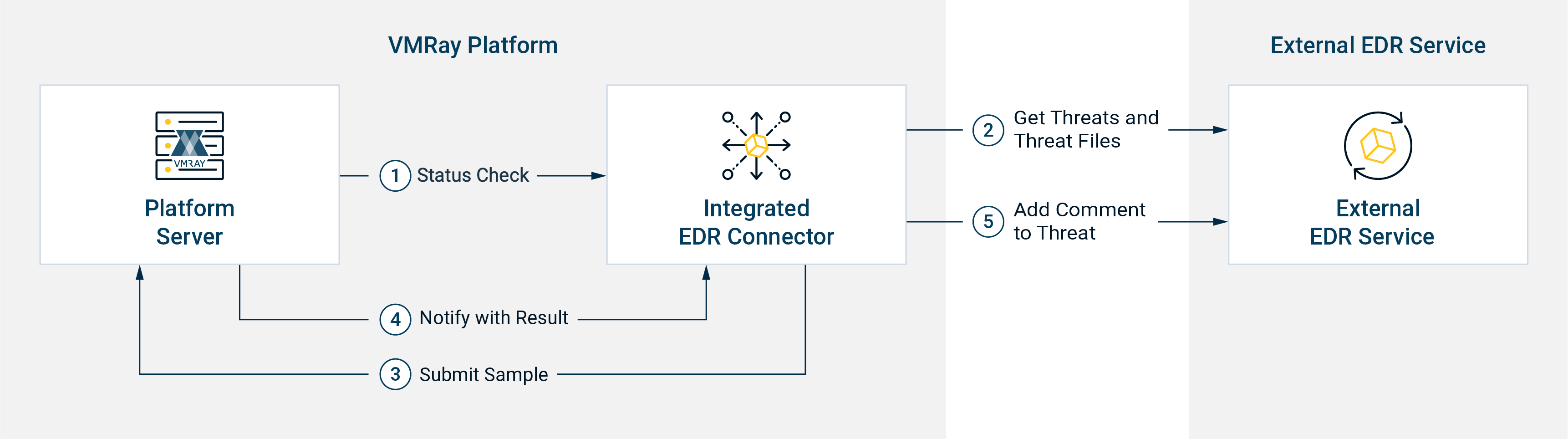
We’re thrilled to announce the MVP release of our integrated SentinelOne connector! This latest development makes integrating with SentinelOne through the VMRay Platform settings page in the Console easier than ever.
The integrated SentinelOne EDR connector, now built directly into the VMRay Platform, streamlines the integration process. Setting up this connector involves minimal configuration steps within the VMRay Console. Simply navigate to the dedicated EDR Integrated Connectors configuration tab in the Console’s Settings and fill in the necessary fields. With just a few clicks, you can configure the system to automatically detect and submit incidents from SentinelOne to our Platform, enabling detailed incident enrichment with notes containing: Threat Classifications, Indicators of Compromise, VMRay Threat Identifiers, and more. This feature is supported in both our TotalInsight and FinalVerdict products.
What are the key advantages of integrated connectors?
- Effortless Integration – no need for time-consuming integration, maintenance, or troubleshooting, as the process is automated.
- Reduced Manual Work – significantly decreases manual maintenance tasks for security teams.
- Automated Incident Submission – the integrated EDR connector automatically picks up incidents from the integrated product, in this case – SentinelOne, and submits them to the Platform, eliminating the need for manual sample submission.
The problem we’re solving:
Existing integrations often rely on middleware that needs to be hosted and managed by our customers. Our new integrated SentinelOne connector addresses several challenges that customers prefer to avoid, such as:
- Hosting – Setting up and maintaining servers or cloud instances for the middleware.
- Learning – Investing time and resources in learning how to operate the middleware.
- Installation – Going through complex installation processes that can be prone to errors.
- Configuration – Dealing with intricate configuration settings that require expertise.
- Maintenance – Regularly updating and patching the middleware to ensure it stays functional and secure.
- Troubleshooting – Resolving issues and bugs that may arise during operation.
With VMRay’s integrated EDR connectors, these challenges are eliminated. The integration process is simplified, reducing the workload on IT and security teams and allowing them to focus on more critical tasks. By embedding the connectors directly within the VMRay Platform, we provide an efficient way to enhance your security operations without the overhead associated with traditional middleware solutions.
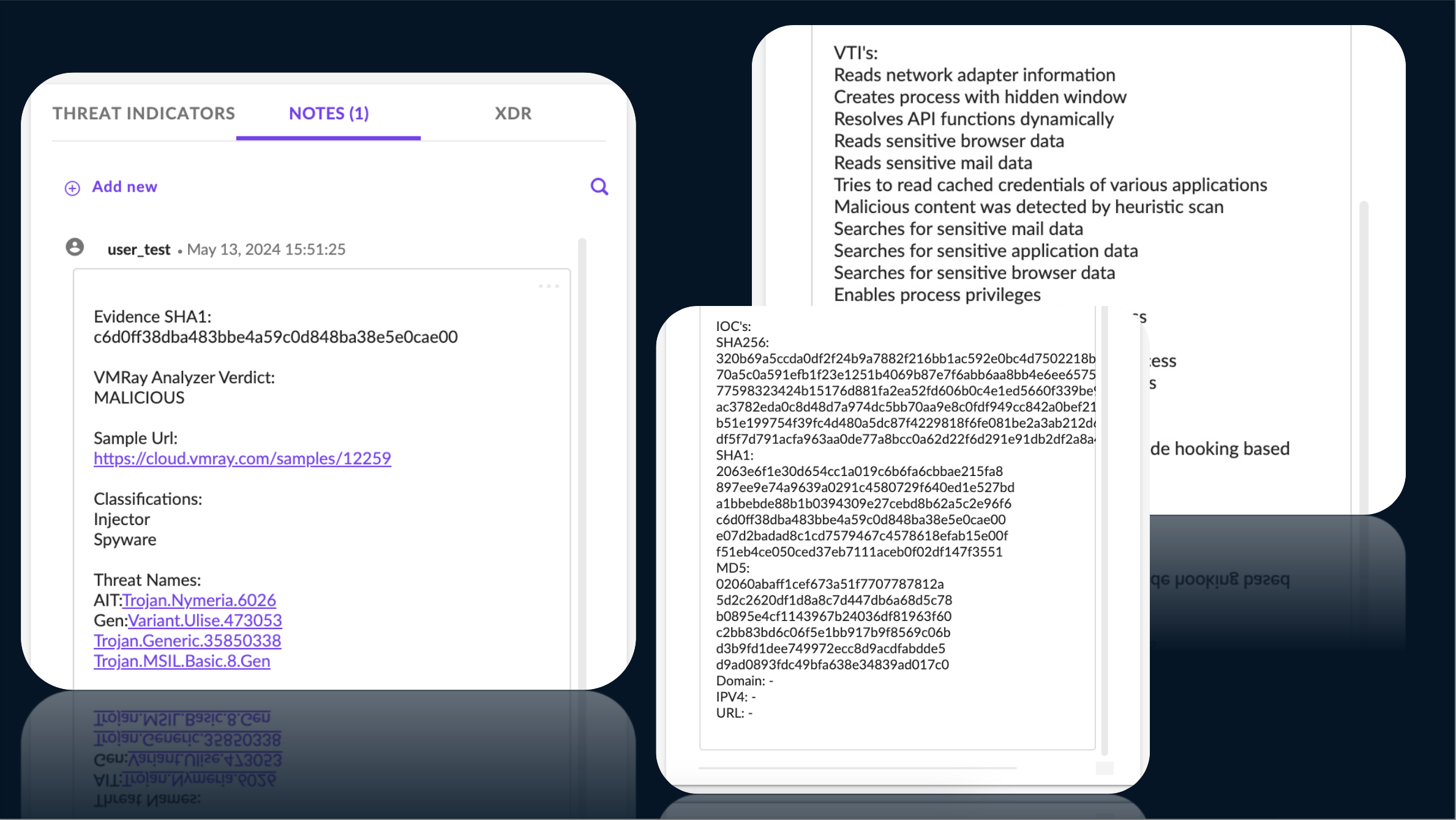
Our customers use MITRE ATT&CK® mapping for a couple of different use cases as they provide a standardized framework for understanding and communicating about cyber threats. This framework helps security professionals identify and anticipate adversary tactics and techniques, enhancing their defense strategies. Organizations use it for threat modeling, incident response, and to improve security measures. To align with the evolving landscape of cyber threats and enterprise techniques, we announce our support for MITRE ATT&CK® v14.1. This update ensures that you have access to the latest adversary tactics and techniques. You’ll discover the updated MITRE ATT&CK® framework integrated into:
- Summary.json v2 Report (supporting MITRE ATT&CK® v4 and v14.1)
- STIX 2.1 Report (supporting MITRE ATT&CK® v14.1)
Why is it important to stay up to date with updated versions of MITRE ATT&CK® framework for threat analysis and detection solutions? Here are a few answers:
- Alignment with industry standards – The MITRE ATT&CK® framework is widely recognized and used across the cybersecurity industry as a comprehensive knowledge base of adversary tactics and techniques. By staying current with the latest version, security teams can ensure that their sandbox environments are aligned with industry standards and best practices.
- Enhanced detection capabilities – New versions of the MITRE ATT&CK® framework often include updates based on emerging threats, attack techniques, and trends observed in the wild. By incorporating these updates, companies can enhance their detection capabilities and better simulate real-world attack scenarios.
- Improved Threat Intelligence – The MITRE ATT&CK® framework provides detailed information about tactics, techniques, and procedures (TTPs) used by threat actors. By staying up to date, security teams can leverage the latest threat intelligence to improve their understanding of potential threats and better defend against them.
Source: https://medium.com/mitre-attack/attack-v14-fa473603f86b
FinalVerdict users now get additional analysis types
We are happy to announce that with this latest release, FinalVerdict users can now benefit from comprehensive analysis of macOS and Linux malware samples. This enhancement significantly broadens the capabilities of our Platform for FinalVerdict users, ensuring robust protection across multiple operating systems.
One of the key concerns that we wanted to address with this addition is the fact that the popularity of Linux and UNIX-like operating systems has grown, and so has the attention from malicious actors seeking to exploit vulnerabilities. The increasing adoption of these systems in various industries has made them lucrative targets for cyberattacks. To learn more about the rising threats targeting Linux, check out our recent blog post: Guarding the Gates: The Growing Abundance of Linux Malware.

Out of sight, out of mind!
We know it’s not a monumental change, but we’re confident it will make a difference! Starting now, DeepResponse users will no longer see the Automation Dashboard, which wasn’t available for their product anyway. This small tweak will reduce any unnecessary confusion and streamline the user experience, ensuring that DeepResponse users can focus on the features that matter most to them.
We do hope you will greatly benefit from what our development teams’ work has to offer. From the seamless integration of the SentinelOne EDR connector into our Platform to the updates on MITRE ATT&CK®, and even the subtle yet impactful improvements across our individual products, there’s a lot to explore.
Going forward, we will be on the lookout for potential enhancements for our On Premises customers’ experience. Stay ahead for updates including an upgraded host system and improved VM management. And speaking of updates, expect some Wind(ows) change in the analysis environment support!
As we march through 2024, there are still two more releases on the horizon, promising valuable updates by the end of August. In the meantime, enjoy the warmth of summer and the upcoming holiday weeks. Stay tuned as we continue this journey together!
如有侵权请联系:admin#unsafe.sh