2024-6-12 15:1:40 Author: www.threatfabric.com(查看原文) 阅读量:5 收藏
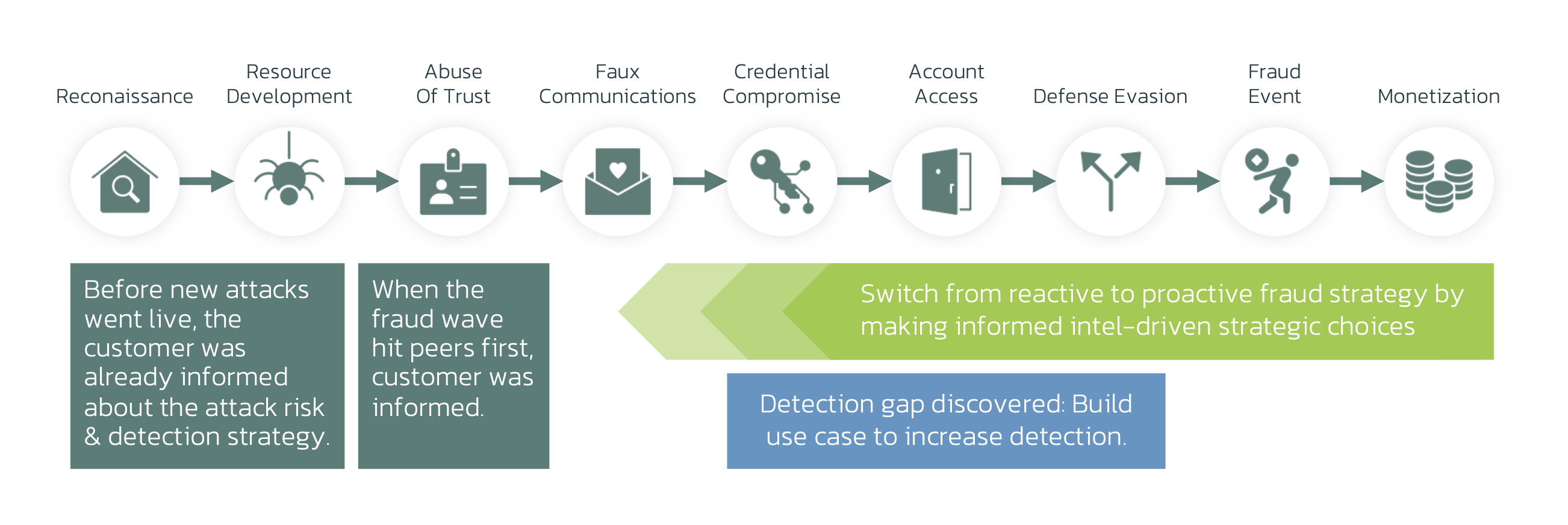
The scam is a combination of a romance scam and an investment scam. Often the investment opportunity is a crypto scam. Therefore, sometimes the name is used synonymously for romance, crypto, or investment scams. Initial contact processes vary, but building trust through romance is a large part of the criminal process. When enough of a relationship is built, an investment opportunity will arise. Additional confidence is built with realistic-looking websites or even investment apps. Over time, the victim’s investment seems to yield. It’s only when they cash out, that they find the entire thing was a scam – and their money is lost. This fifth episode, for that reason, has some resemblance to our earlier articles on “romance scams” and “investment scams”. Scam process steps: Our numbers show that Investment Scams have been on the rise in Q1 of 2024. Romance Fraud and Investment fraud combined is 26% of all fraud. The Fraud Kill-chain is a useful tool to identify detection opportunities and gaps. It allows anti-fraud teams to map capabilities to attacks and helps control a wide variety of fraud and scams. The Fraud Kill Chain mapping shares similarities with other scams: The early stages of the scam resemble Romance Fraud and the later stages with Investment scams. In many scam attempts, device use and the transaction will seem completely benign. To detect behavioral aspects, it’s key to have Customer Journey visibility: all interactions happening between login and transaction. Web and app adoption is increasing rapidly. This is why a detection stack should include customer journey visibility on any online channel: web, mobile, and app. Manipulation of behavior requires a different perspective. Behavioral Biometrics is the best technology available. It’s key to have multiple models: As scammers are raking in billions, anti-fraud teams are to perform the following checks: ThreatFabric helps banks and financials globally perform these analyses. If you’re interested in a detection readiness workshop contact us via the link below.This blog is part of a series where we provide tools to assess your fraud detection capabilities against the most prevalent fraud and scam types.
From malware campaigns to complex scams, we analyze TTPs, Fraud Kill Chain mappings, and detection gaps.
This fifth episode delves into one of the most manipulative scams: Pig Butchering. Combining romance and investment fraud elements, we explore how the Cyber-Fraud Kill Chain can identify detection opportunities and gaps.
Pig Butchering vs Cyber-Fraud Kill Chain
“Pig Butchering” is a horribly named scam. Sadly, the press and the industry have adopted the criminals’ vocabulary for this scam type, as it unfairly characterizes victims as animals being groomed for slaughter. For victims, the name might feel like an additional slap in the face.

About the Fraud Kill Chain
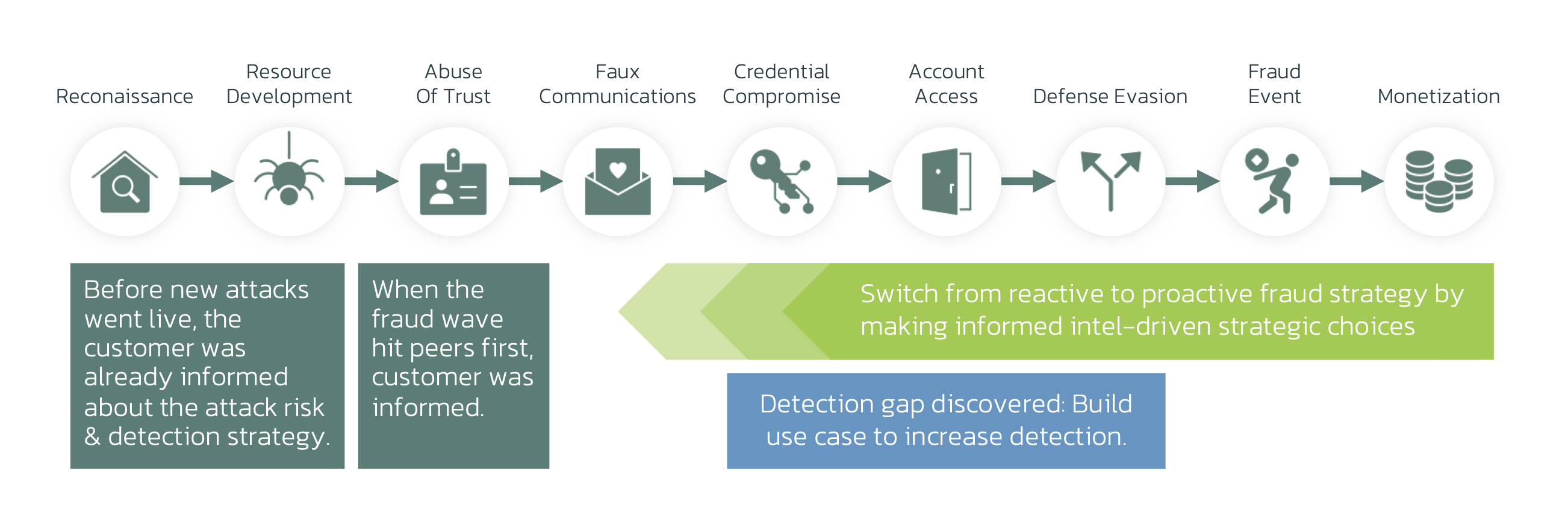
Pig Butchering vs Fraud Kill-Chain

Detection Gaps and Opportunities
Gap 1: Customer Journey Visibility
Gap 2. Web, Mobile, and App: multi-channel Visibility and Correlation
Gap 3. Behavioral Biometrics
Conclusion & Takeaways
Detection Readiness workshop
如有侵权请联系:admin#unsafe.sh