2024-6-13 23:45:0 Author: ddanchev.blogspot.com(查看原文) 阅读量:11 收藏
Dear blog readers,
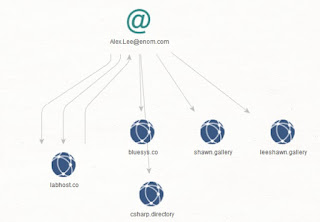
In this analysis I'll provide actionable intelligence on the LabHost phishing as a service cybercrime enterprise.
Sample URLs known to have been involved in the campaign include:
hxxp://labhost[.]cc
hxxp://labhost[.]co
hxxp://labhost[.]xyz - Email: zztopd[.]rambler.ru
hxxp://labhost[.]ru
hxxp://lab-host[.]ru
Related domains known to have been registered using [email protected]:
hxxp://russiancloud[.]xyz
hxxp://onelab[.]xyz
hxxp://onebio[.]xyz
hxxp://inforussia[.]xyz
hxxp://labservice[.]xyz
hxxp://labcentral[.]xyz
hxxp://gorussian[.]xyz
hxxp://ecoserver[.]xyz
hxxp://iotmed[.]xyz
hxxp://ecolenta[.]xyz
hxxp://fedlab[.]xyz
hxxp://fedinfo[.]xyz
hxxp://fedhost[.]xyz
hxxp://freerussia[.]xyz
hxxp://federalpost[.]xyz
hxxp://federalnet[.]xyz
hxxp://federalinfo[.]xyz
hxxp://federalhost[.]xyz
hxxp://murietta[.]ru
hxxp://federalcloud[.]xyz
hxxp://medcloud[.]xyz
hxxp://5koleso[.]xyz
hxxp://webrussia[.]xyz
hxxp://redmachine[.]xyz
hxxp://russianweb[.]xyz
hxxp://ru-linux[.]xyz
hxxp://medlenta[.]xyz
hxxp://mybiocloud[.]xyz
hxxp://medithink[.]xyz
hxxp://red-square[.]xyz
hxxp://invitrolab[.]xyz
hxxp://federalweb[.]xyz
hxxp://fedserver[.]xyz
hxxp://biocasino[.]xyz
hxxp://biosms[.]xyz
hxxp://fednet[.]xyz
hxxp://biodroid[.]xyz
hxxp://bioserver[.]xyz
hxxp://bioportal[.]xyz
hxxp://biolive[.]xyz
hxxp://biolenta[.]xyz
hxxp://biohost[.]xyz
hxxp://kindzadza[.]xyz
hxxp://gomama[.]xyz
hxxp://redsquare[.]xyz
hxxp://liveinternet[.]xyz
hxxp://rulinux[.]xyz
hxxp://papa-mama[.]xyz
hxxp://onbio[.]xyz
hxxp://astra77[.]xyz
Sample responding IPs:
34[.]98[.]99[.]30
91[.]215[.]43[.]219
185[.]156[.]42[.]4
158[.]69[.]138[.]108
194[.]28[.]86[.]146
23[.]111[.]174[.]83
23[.]111[.]137[.]182
91[.]195[.]240[.]117
170[.]178[.]183[.]18
103[.]224[.]212[.]219
199[.]115[.]116[.]43
103[.]224[.]182[.]250
5[.]79[.]79[.]212
103[.]224[.]212[.]210
91[.]214[.]124[.]221
81[.]171[.]22[.]6
185[.]178[.]208[.]34
194[.]58[.]112[.]165
91[.]215[.]43[.]156
104[.]21[.]65[.]189
172[.]67[.]191[.]126
172[.]67[.]30[.]242
104[.]22[.]11[.]98
104[.]22[.]10[.]98
172[.]67[.]165[.]61
198[.]105[.]254[.]11
104[.]21[.]73[.]181
69[.]64[.]155[.]178
52[.]87[.]81[.]7
108[.]61[.]211[.]100
52[.]72[.]115[.]242
45[.]76[.]92[.]34
8[.]5[.]1[.]32
34[.]120[.]137[.]41
37[.]140[.]192[.]148
37[.]140[.]192[.]254
如有侵权请联系:admin#unsafe.sh

