2024-6-13 16:10:0 Author: ddanchev.blogspot.com(查看原文) 阅读量:3 收藏
Dear blog readers,
In this analysis I'll offer and provide an in-depth technical overview of the Internet-connected infrastructure behind the Maze Ransomware Group using public sources including the data leak broker who’s responsible for the Sonatrach Data Leak with the idea to assist the appropriate parties researchers and analysts on their way to properly attribute the leak to the cyber threat actor known as Maze Ransomware Group where the ultimate idea would be to prevent future network intrusions including to actually assist in attempting to take their Internet-connected infrastructure offline.
Although the group has publicly announced that it’s shutting down its operations its Internet-connected infrastructure remains online and operational.
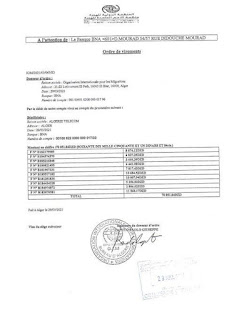
Sample screenshots:
Sample screenshots of the ISPs currently hosting the Maze Ransomware Group’s Internet-connected infrastructure include:
Sample personally identifiable email of the individual involved in the leak:
s0natrach[.]proton.me
Sample URLs for leaked information obtained from the leak:
hxxp://anonfiles[.]com/cbz9z225y4/Le_contr_le_de_gestion_pour_managers_zip
hxxp://easyupload[.]io/rps33q
hxxp://easyupload[.]io/ax8jh3
hxxp://easyupload[.]io/n443ev
hxxp://easyupload[.]io/dw9209
Sample domains known to have been involved in the campaign include:
hxxp://mazedecrypt[.]top
hxxp://mazenews[.]top
hxxp://newsmaze[.]top
hxxp://mazedecrypt[.]top
Related actionable intelligence and C&Cs on the Maze Ransomware Group:
hxxp://mazedecrypt[.]top - 35[.]205[.]61[.]67
Name servers used: ns1[.]csof[.]net
Dark Web Onion: aoacugmutagkwctu[.]onion
Sample Bitcoin Address: 3JGqKRWSsXQsnHWDpHXXNg7TJcubszJher
Related domains:
hxxp://munsys[.]icu
hxxp://deepletelyre[.]club
hxxp://gamsaymin[.]club
hxxp://hersendentp[.]club
hxxp://nistreecongl[.]club
hxxp://cllbguhxggwd[.]club
hxxp://cxwbtywohnimbat[.]biz
hxxp://xbknggwrsigwvqg[.]biz
hxxp://xyrcwgdibytikak[.]biz
hxxp://okxlqotixjlxbst[.]biz
hxxp://mazedecrypt[.]top
hxxp://avoirparticulierserv[.]xyz - 94[.]140[.]114[.]197 - 146[.]0[.]72[.]74
Sample malicious MD5s known to have been involved in the campaign include:
4e22ab46a8d5dc5fea6c41ea6fdc913b793a4e33df8f0bc1868b72b180c0e6e
067f1b8f1e0b2bfe286f5169e17834e8cf7f4266b8d97f28ea78995dc81b0e7b
1161b030293e58d15b6a6a814a61a6432cf2c98ce9d156986157b432f3ebcf78
153defee225de889d2ac66605f391f4aeaa8b867b4093c686941e64d0d245a57
195ef8cfabc2e877ebb1a60a19850c714fb0a477592b0a8d61d88f0f96be5de9
30b72e83d66cbe9e724c8e2b21179aecd4bcf68b2ec7895616807df380afab54
33afa2f1d53d5279b6fc87ce6834193fdd7e16e4b44e895aae4b9da00be0c502
4080402553e9a86e954c1d9b7d0bb059786f52aba4a179a5d00e219500c8f43d
5603a16cbf81d183d3ff4ffea5477af1a4be01321865f0978c0e128051ec0a82
58fe9776f33628fd965d1bcc442ec8dc5bfae0c648dcaec400f6090633484806
5c9b7224ffd2029b6ce7b82ea40d63b9d4e4f502169bc91de88b4ea577f52353
6878f7bd90434ac5a76ac2208a5198ce1a60ae20e8505fc110bd8e42b3657d13
6a22220c0fe5f578da11ce22945b63d93172b75452996defdc2ff48756bde6af
822a264191230f753546407a823c6993e1a83a83a75fa36071a874318893afb8
83f8ce81f71d6f0b1ddc6b4f3add7a5deef8367a29f59b564c9539d6653d1279
877c439da147bab8e2c32f03814e3973c22cbcd112d35bc2735b803ac9113da1
91514e6be3f581a77daa79e2a4905dcbdf6bdcc32ee0f713599a94d453a26fc1
9751ae55b105ad8ffe6fc5dc7aea60ad723b6df67a959aa2ea6f4fa640d20a71
9ad15385f04a6d8dd58b4390e32d876070e339eee6b8da586852d7467514d1b1
9be70b7fe15cd64aed5b1adc88c2d5270bce534d167c4a42d143ae0059c3da1c
b30bb0f35a904f67d3ac0082c59770836cc415dc5b7225be04e8d7c79bde73be
c040defb9c90074b489857f328d3e0040ac0ddab26cde132f17cccae7f1309cc
c11b964916457579a268a36e825857866680baf1830cd6e2d26d4e1e24dec91b
ea19736c8e89e871974aabdc0d52ad0f0948159d4cf41d2889f49448cbe5e705
ecd04ebbb3df053ce4efa2b73912fd4d086d1720f9b410235ee9c1e529ea52a2
F491fb72f106e879021b0bb1149c4678fb380c255d2ef11ac4e0897378793f49
fc611f9d09f645f31c4a77a27b6e6b1aec74db916d0712bef5bce052d12c971f
Related C&Cs known to be part of Maze Ransomware Group’s Internet-connected infrastructure include:
hxxp://104[.]168[.]198[.]208/wordupd[.]tmp
hxxp://104[.]168[.]215[.]54/wordupd[.]tmp
hxxp://104[.]168[.]174[.]32/wordupd_3[.]0[.]1[.]tmp
Related C&Cs known to be part of Maze Ransomware Group’s Internet-connected infrastructure include:
91[.]218[.]114[.]4
5[.]199[.]167[.]188
185[.]147[.]15[.]22
91[.]218[.]114[.]11
91[.]218[.]114[.]25
91[.]218[.]114[.]26
91[.]218[.]114[.]31
91[.]218[.]114[.]32
91[.]218[.]114[.]37
91[.]218[.]114[.]38
91[.]218[.]114[.]77
91[.]218[.]114[.]79
Related malicious MD5s known to have been involved in the campaign include:
19aaa6c900a5642941d4ebc309433e783befa4cccd1a5af8c86f6e257bf0a72e
6878f7bd90434ac5a76ac2208a5198ce1a60ae20e8505fc110bd8e42b3657d13
9ad15385f04a6d8dd58b4390e32d876070e339eee6b8da586852d7467514d1b1
b950db9229db2f37a7eb5368308de3aafcea0fd217c614daedb7f334292d801e
Related C&Cs known to be part of Maze Ransomware Group’s Internet-connected infrastructure include:
hxxp://91[.]218[.]114[.]4/nwjknpeevx[.]action?pw=g1y652l&kyn=21y3vvhh&dvr=5e&us=g25e3582a
hxxp://91[.]218[.]114[.]11/forum/siaib[.]jspx?v=h&xyna=0vip863&eul=xsn3q0
hxxp://91[.]218[.]114[.]26/view/ticket/pigut[.]jspx?o=664quo0s&fp=ot52
hxxp://91[.]218[.]114[.]25/xrr[.]jspx?ygad=r35e2cx&e=6as6ta
hxxp://91[.]218[.]114[.]4/j[.]php
hxxp://91[.]218[.]114[.]11/payout/view/fa[.]aspx?y=y&qbx=4&kws=n2&iuy=8k7
hxxp://91[.]218[.]114[.]25/lxh[.]asp?mtxm=l7&r=836wy5
hxxp://91[.]218[.]114[.]26/signin/ticket/eq[.]action?x=yk6rr&e=50b&q=327dr5&ofk=065cdp
hxxp://91[.]218[.]114[.]31/signin/rnmnnekca[.]jsp?kdn=6snl5&e=7a50cx4hyp
hxxp://91[.]218[.]114[.]31/forum/a[.]aspx?byx=56&bc=62t0h&u=75w6n6&sot=2v0l761or6
hxxp://91[.]218[.]114[.]32/withdrawal/checkout/l[.]do?nuny=qj6&sdv=45g2boyf5q&dnr=rh8lk31ed
hxxp://91[.]218[.]114[.]77/task/bxfbpx[.]jspx?nq=cge63
hxxp://91[.]218[.]114[.]38/account/payout/ujwkjhoui[.]shtml
hxxp://91[.]218[.]114[.]37/imrhhjitop[.]phtml?wto=344dsc84&sp=x&oml=c173s71u&iy=m3u2
hxxp://91[.]218[.]114[.]38/auth/login
hxxp://91[.]218[.]114[.]79/logout/hfwdmugdi[.]php?upaj=mj7g
hxxp://91[.]218[.]114[.]38/sepa/juel[.]php?ars=51qse4p3y&xjaq=r5o4t4dp
hxxp://91[.]218[.]114[.]32/fwno[.]cgi?yd=410&o=y7x5kx371&p=m3361672
hxxp://91[.]218[.]114[.]37/sepa/signout/mjsnm[.]aspx?r=7o47wri&rtew=uu8764ssy&bri=51gxx6k5&opms=72gy0a
hxxp://91[.]218[.]114[.]77/payout/analytics/lrkaaosp[.]do?y=62h&aq=3jq8k6&v=0svt
hxxp://91[.]218[.]114[.]79/create/dpcwk[.]php?u=28qy0dpmt&qwbh=k&f=g1ub5ei&ek=3ee
Related malicious domains known to be part of Maze Ransomware Group’s Internet-connected infrastructure include:
hxxp://mazedecrypt[.]top
hxxp://mazedecrypt[.]top
hxxp://mazenews[.]top
hxxp://newsmaze[.]top
Related C&Cs known to be part of Maze Ransomware Group’s Internet-connected infrastructure include:
91[.]218[.]114[.]11
91[.]218[.]114[.]25
91[.]218[.]114[.]26
91[.]218[.]114[.]31
91[.]218[.]114[.]32
91[.]218[.]114[.]37
91[.]218[.]114[.]38
91[.]218[.]114[.]4
91[.]218[.]114[.]77
91[.]218[.]114[.]79
hxxp://92[.]63[.]8[.]47
hxxp://92[.]63[.]32[.]2
hxxp://92[.]63[.]37[.]100
hxxp://92[.]63[.]194[.]20
hxxp://92[.]63[.]17[.]245
hxxp://92[.]63[.]32[.]55
hxxp://92[.]63[.]11[.]151
hxxp://92[.]63[.]194[.]3
hxxp://92[.]63[.]15[.]8
hxxp://92[.]63[.]29[.]137
hxxp://92[.]63[.]32[.]57
hxxp://92[.]63[.]15[.]56
hxxp://92[.]63[.]11[.]151
hxxp://92[.]63[.]32[.]52
hxxp://92[.]63[.]15[.]6
Related malicious MD5s known to be part of Maze Ransomware Group’s Internet-connected infrastructure include:
064058cf092063a5b69ed8fd2a1a04fe
0f841c6332c89eaa7cac14c9d5b1d35b
108a298b4ed5b4e77541061f32e55751
11308e450b1f17954f531122a56fae3b
15d7dd126391b0e7963c562a6cf3992c
21a563f958b73d453ad91e251b11855c
27c5ecbb94b84c315d56673a851b6cf9
2f78ff32cbb3c478865a88276248d419
335aba8d135cc2e66549080ec9e8c8b7
3bfcba2dd05e1c75f86c008f4d245f62
46b98ee908d08f15137e509e5e69db1b
5774f35d180c0702741a46d98190ff37
5df79164b6d0661277f11691121b1d53
658e9deec68cf5d33ee0779f54806cc2
65cf08ffaf12e47de8cd37098aac5b33
79d137d91be9819930eeb3876e4fbe79
8045b3d2d4a6084f14618b028710ce85
8205a1106ae91d0b0705992d61e84ab2
83b8d994b989f6cbeea3e1a5d68ca5d8
868d604146e7e5cb5995934b085846e3
87239ce48fc8196a5ab66d8562f48f26
89e1ddb8cc86c710ee068d6c6bf300f4
910aa49813ee4cc7e4fa0074db5e454a
9eb13d56c363df67490bcc2149229e4c
a0c5b4adbcd9eb6de9d32537b16c423b
a3a3495ae2fc83479baeaf1878e1ea84
b02be7a336dcc6635172e0d6ec24c554
b40a9eda37493425782bda4a3d9dad58
b4d6cb4e52bb525ebe43349076a240df
b6786f141148925010122819047d1882
b93616a1ea4f4a131cc0507e6c789f94
bd9838d84fd77205011e8b0c2bd711e0
be537a66d01c67076c8491b05866c894
bf2e43ff8542e73c1b27291e0df06afd
c3ce5e8075f506e396ee601f2757a2bd
d2dda72ff2fbbb89bd871c5fc21ee96a
d3eaab616883fcf51dcbdb4769dd86df
d552be44a11d831e874e05cadafe04b6
deebbea18401e8b5e83c410c6d3a8b4e
dfa4631ec2b8459b1041168b1b1d5105
e57ba11045a4b7bc30bd2d33498ef194
e69a8eb94f65480980deaf1ff5a431a6
ef95c48e750c1a3b1af8f5446fa04f54
f04d404d84be66e64a584d425844b926
f457bb5060543db3146291d8c9ad1001
f5ecda7dd8bb1c514f93c09cea8ae00d
f83cef2bf33a4d43e58b771e81af3ecc
fba4cbb7167176990d5a8d24e9505f71
Related C&Cs known to be part of Maze Ransomware Group’s Internet-connected infrastructure include:
91[.]218[.]114[.]11
91[.]218[.]114[.]25
91[.]218[.]114[.]26
91[.]218[.]114[.]31
91[.]218[.]114[.]32
91[.]218[.]114[.]37
91[.]218[.]114[.]38
91[.]218[.]114[.]4
91[.]218[.]114[.]77
91[.]218[.]114[.]79
92[.]63[.]11[.]151
92[.]63[.]15[.]6
92[.]63[.]15[.]8
92[.]63[.]17[.]245
92[.]63[.]194[.]20
92[.]63[.]194[.]3
92[.]63[.]29[.]137
92[.]63[.]32[.]2
92[.]63[.]32[.]52
92[.]63[.]32[.]55
92[.]63[.]32[.]57
92[.]63[.]37[.]100
92[.]63[.]8[.]47
Related C&Cs:
hxxp://104[.]168[.]174[.]32/wordupd_3[.]0[.]1[.]tmp
hxxp://104[.]168[.]198[.]208/wordupd[.]tmp
hxxp://104[.]168[.]201[.]35/dospizdos[.]tmp
hxxp://104[.]168[.]201[.]47/wordupd[.]tmp
hxxp://104[.]168[.]215[.]54/wordupd[.]tmp
hxxp://149[.]56[.]245[.]196/wordupd[.]tmp
hxxp://192[.]119[.]106[.]235/mswordupd[.]tmp
hxxp://192[.]119[.]106[.]235/officeupd[.]tmp
hxxp://192[.]99[.]172[.]143/winupd[.]tmp
hxxp://54[.]39[.]233[.]188/win163[.]65[.]tmp
hxxp://91[.]208[.]184[.]174:8079/windef[.]exe
hxxp://agenziainformazioni[.]icu/wordupd[.]tmp
hxxp://www[.]download-invoice[.]site/Invoice_29557473[.]exe
Related C&Cs known to be part of Maze Ransomware Group’s Internet-connected infrastructure include:
173[.]209[.]43[.]61
193[.]36[.]237[.]173
37[.]1[.]213[.]9
37[.]252[.]7[.]142
5[.]199[.]167[.]188
hxxp://checksoffice[.]me
hxxp://drivers[.]updatecenter[.]icu
hxxp://plaintsotherest[.]net
hxxp://thesawmeinrew[.]net
hxxp://updates[.]updatecenter[.]icu
hxxp://att-customer[.]com
hxxp://att-information[.]com
hxxp://att-newsroom[.]com
hxxp://att-plans[.]com
hxxp://bezahlen-1und1[.]icu
hxxp://bzst-info[.]icu
hxxp://bzst-inform[.]icu
hxxp://bzstinfo[.]icu
hxxp://bzstinform[.]icu
hxxp://canada-post[.]icu
hxxp://canadapost-delivery[.]icu
hxxp://canadapost-tracking[.]icu
hxxp://hilfe-center-1und1[.]icu
hxxp://hilfe-center-internetag[.]icu
hxxp://trackweb-canadapost[.]icu
Related personally identifiable email address accounts known to have been involved in the campaign include:
abusereceive[.]hitler.rocks
gladkoff1991[.]yandex.ru
Related C&Cs known to be part of Maze Ransomware Group’s Internet-connected infrastructure include:
hxxp://91[.]218[.]114[.]4
hxxp://91[.]218[.]114[.]11
hxxp://91[.]218[.]114[.]25
hxxp://91[.]218[.]114[.]26
hxxp://91[.]218[.]114[.]31
hxxp://91[.]218[.]114[.]32
hxxp://91[.]218[.]114[.]37
hxxp://91[.]218[.]114[.]38
hxxp://91[.]218[.]114[.]77
hxxp://91[.]218[.]114[.]79
hxxp://globalsign[.]icu
hxxp://ocspverisign[.]pw
hxxp://officecloud[.]top
92[.]63[.]8[.]47
92[.]63[.]3[.]2
92[.]63[.]37[.]100
92[.]63[.]194[.]20
92[.]63[.]17[.]245
92[.]63[.]32[.]55
92[.]63[.]11[.]151
92[.]63[.]194[.]3
92[.]63[.]15[.]8
92[.]63[.]29[.]137
92[.]63[.]32[.]57
92[.]63[.]15[.]56
92[.]63[.]11[.]151
92[.]63[.]32[.]52
92[.]63[.]15[.]6
91[.]218[.]114[.]11
91[.]218[.]114[.]25
91[.]218[.]114[.]26
91[.]218[.]114[.]31
91[.]218[.]114[.]32
91[.]218[.]114[.]37
91[.]218[.]114[.]38
91[.]218[.]114[.]4
91[.]218[.]114[.]77
91[.]218[.]114[.]79
Sample screenshots:
如有侵权请联系:admin#unsafe.sh















