
2024-6-14 21:0:0 Author: www.tenable.com(查看原文) 阅读量:14 收藏

Check out the NCSC’s call for software vendors to make their products more secure. Plus, why the Treasury Department is looking at how financial institutions are using AI. And the latest on the cybersecurity skills gap in the U.S. And much more!
Dive into six things that are top of mind for the week ending June 14.
1 - NCSC issues “code of practice” for software makers
Software vendors improve the security of their products.
That’s the goal of the U.K. National Cyber Security Centre’s new “Code of Practice for Software Vendors.” The document from the U.K.’s cybersecurity agency outlines a minimum baseline of secure development processes for software vendors.
Compliance with the “Code of Practice for Software Vendors” is voluntary for now “but further policy interventions to support its uptake and impact are currently being explored,” reads the NCSC blog “Raising the cyber resilience of software 'at scale.'”

The document is structured around four core principles software vendors should follow:
- Adopt secure design and development by, for example, establishing and following a secure development framework and understanding their software products’ components.
- Secure build environments to protect the software’s integrity and quality by, for example, preventing unauthorized access to the build environment.
- Ensure products remains secure after deployment by, for example, adopting a vulnerability disclosure process; detecting and managing vulnerabilities; and releasing timely updates and patches.
- Provide the necessary information to customers for effective risk and incident management.
The “Code of Practice for Software Vendors” also includes implementation guidance for its best practices and recommendations.
For more information about the security of commercial software products:
- “How To Prevent Software Vulnerabilities in Commercial Applications” (IT Pro Today)
- “Tenable Partners with CISA to Enhance Secure By Design Practices” (Tenable)
- “Principles and Approaches for Secure by Design Software” (CISA)
- “US government software suppliers must attest their solutions are secure” (Help Net Security)
2 - How are banks using AI? The U.S. gov’t wants to know
What obstacles to responsible use of artificial intelligence (AI) do financial institutions face? How is AI impacting their operations? And when banks use AI, how does that affect their consumer and corporate customers, as well as their investors and other third parties?
These are some of the questions the U.S. Treasury Department is seeking answers to. To that end, it has issued a formal request for information about how the financial services sector is using AI.

If you want to contribute to this fact-finding effort, check out the formal document titled “Request for Information on Uses, Opportunities, and Risks of Artificial Intelligence in the Financial Services Sector” and add your comment on the Regulations.gov website.
“Treasury is seeking a broad range of perspectives on this topic and is particularly interested in understanding how AI innovations can help promote a financial system that delivers inclusive and equitable access to financial services,” reads a Treasury Department statement.
For more information about AI usage trends in the financial services sector:
- “How Artificial Intelligence is Transforming the Financial Services Industry” (Deloitte)
- “Artificial Intelligence and Machine Learning in Financial Services” (U.S. Congressional Research Service)
- “Finding value in generative AI for financial services” (MIT Technology Review)
- “Digital ethics and banking: A strong AI strategy starts with customer trust” (Deloitte)
- “Managing Artificial Intelligence-Specific Cybersecurity Risks in the Financial Services Sector” (U.S. Treasury Department)
3 - Insurer: Cyber claims hit all-time high in 2023
Looking for insights about how the cyber insurance market is evolving? Data released by insurance broker Marsh McLennan offers interesting clues about this dynamic market.
For starters, the 1,800-plus claims submitted by its U.S. and Canadian customers in 2023 were a record for Marsh McLennan. Drivers included the growing sophistication of attacks, the exploitation of the MOVEit Transfer vulnerabilities, privacy-related claims and an increase in cyber insurance customers.
Unsurprisingly, ransomware remains top-of-mind for insurance companies and for their customers, although it accounted for under 20% of total claims. Ransomware concern centers on its potential for significant financial losses, reputation harm, lost sales, litigation costs, regulatory scrutiny and more, according to the insurer.
More interesting data points include:
- About 1 in 5 Marsh cyber customers filed a claim last year, a rate that’s remained consistent over the past five years.
- The hardest hit industries in 2023 were healthcare, communications, retail/wholesale, financial services and education.
- The median cost of breach responses was $160,000 and the average was $1 million
Also of note, the percentage of organizations paying ransoms remains on a downward trend.
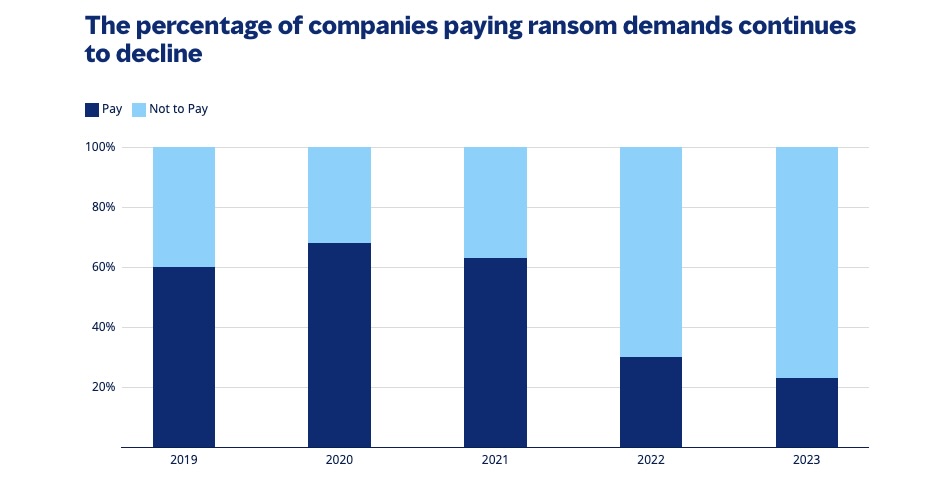
(Source: Marsh McLennan, June 2024)
Ultimately, it’s key for organizations to continually boost their cybersecurity strategy and controls.
“Organizations’ cyber resilience strategy should incorporate a view of cyber risk across the enterprise, including its potential economic and operational impact and taking account of cybersecurity at vendors and other third parties,” reads a Marsh McLennan statement.
To learn more about cyber insurance, check out these Tenable resources:
- “What Is Cyber Insurance?”
- “Shifting the Paradigm: Why the Cyber Insurance Industry Should Focus on Preventive Security” (blog)
- “How to Successfully Secure the Best Cyber Insurance Policy at the Best Price for Your Business” (on-demand webinar)
- “How To Obtain the Right Cybersecurity Insurance for Your Business” (blog)
- “A CISO, General Counsel & Underwriter Walk Into a Bar... Securing the Right Cyber Insurance for Your Business is No Joke” (on-demand webinar)
4 - Tenable takes pulse on GenAI app usage policies
With generative AI adoption on fire in the enterprise, Tenable took the opportunity to poll attendees at several of our webinars this month about this topic. Specifically, we asked them whether their organizations have crafted usage policies for generative AI applications. Check out the results!
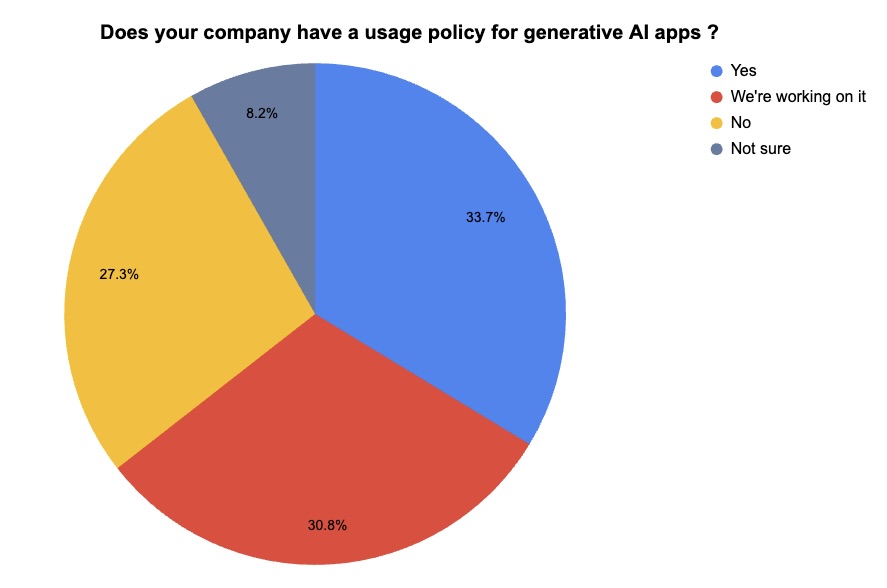
(377 webinar attendees polled by Tenable, June 2024)
For more information about this topic:
- “Cybersecurity Snapshot: 6 Best Practices for Implementing AI Securely and Ethically” (Tenable)
- “Key Considerations for Developing Organizational Generative AI Policies” (ISACA)
- “How to craft a generative AI security policy that works” (TechTarget)
- “Why and how to create corporate genAI policies” (Computerworld)
- “If you don’t already have a generative AI security policy, there’s no time to lose” (CSO)
5 - U.S. can only fill 85% of cyber jobs with current workforce
The U.S. needs more than 220,000 new cybersecurity pros to close its cyber talent gap. Currently, the U.S. has enough cyber workers to fill 85% of cybersecurity jobs.
That’s according to CyberSeek, which provides data about the cybersecurity job market. It’s a joint initiative between the National Institute of Standards and Technology’s NICE program; Lightcast; and CompTIA.
“Although demand for cybersecurity jobs is beginning to normalize to pre-pandemic levels, the longstanding cyber talent gap persists,” Will Markow, vice president of applied research at Lightcast, said in a CompTIA statement about the CyberSeek data.
To address the skills gap, employers should try training less experienced cybersecurity pros to perform advanced jobs, as well as consider candidates who have cybersecurity expertise but who only have a professional certification, according to CompTIA.
Other interesting insights include:
- Between May 2023 and April 2024, U.S. employers posted almost 470,000 cybersecurity jobs, down 29% from the same period the year prior. By comparison, job postings for all tech positions declined 37%.
- Currently, 1.2 million people hold cybersecurity jobs in the U.S., a number that’s been growing for years.
- Cybersecurity skills are evolving quickly as hackers craft new types of attacks.
For more information about the cyber skills shortage in the U.S. and globally:
- “Cybersecurity skills gap: Why it exists and how to address it” (TechTarget)
- “ISC2 Cybersecurity Workforce Study: Looking Deeper into the Workforce Gap” (ISC2)
- “Will the Cyber Skills Gap Continue to Grow in 2024?” (Infosecurity Magazine)
- “Bridging the Cyber Skills Gap” (World Economic Forum)
- “Key cybersecurity skills gap statistics you should be aware of” (Help Net Security)
6 - CIS updates Benchmarks for AWS, Google, Microsoft products
The Center for Internet Security has announced the latest batch of updates for its popular CIS Benchmarks, including new secure-configuration recommendations for Amazon Elastic Kubernetes Service, Google Container-Optimized OS and Microsoft SQL Server.
Specifically, these CIS Benchmarks were updated in May:
- CIS Amazon Elastic Kubernetes Service (EKS) Benchmark v1.5.0
- CIS Google Container-Optimized OS Benchmark v1.2.0
- CIS Google Workspace Foundations Benchmark v1.2.0
- CIS Microsoft SQL Server 2019 Benchmark v1.4.0
- CIS Microsoft Windows 10 EMS Gateway Benchmark v3.0.0
- CIS Microsoft Windows 11 Stand-alone Benchmark v3.0.0
- CIS Microsoft Windows Server 2019 Benchmark v3.0.1
- CIS Oracle Cloud Infrastructure Container Engine for Kubernetes (OKE) Benchmark v1.5.0
- CIS Palo Alto Firewall 10 Benchmark v1.2.0
- CIS Palo Alto Firewall 11 Benchmark v1.1.0

In addition, CIS released brand new Benchmarks for Apple’s macOS 12, macOS 13 and macOS 14 running in a cloud environment.
CIS Benchmarks are secure-configuration guidelines for hardening products against attacks. Currently, CIS offers more than 100 Benchmarks for 25-plus vendor product families. There are Benchmarks for cloud platforms; databases; desktop and server software; mobile devices; operating systems; and more.
To get more details, read the CIS blog “CIS Benchmarks June 2024 Update.” For more information about the CIS Benchmarks list, check out its home page, as well as:
- “Getting to Know the CIS Benchmarks” (CIS)
- “Security Via Consensus: Developing the CIS Benchmarks” (Dark Reading)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (Help Net Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)

Juan Perez
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
Related Articles
- Center for Internet Security (CIS)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- NIST
- Risk-based Vulnerability Management
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Try Tenable Web App Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
如有侵权请联系:admin#unsafe.sh