Introduction
Code reuse is very frequent in malware, especially for those parts of the sample that are complex to develop or hard to write with an essentially different alternative code. By tracking both source code and object code, we efficiently detect new malware and track the evolution of existing malware in-the-wild.
Diamorphine is a well-known Linux kernel rootkit that supports different Linux kernel versions (2.6.x, 3.x, 4.x, 5.x and 6.x) and processor architectures (x86, x86_64 and ARM64). Briefly stated, when loaded, the module becomes invisible and hides all the files and folders starting with the magic prefix chosen by the attacker at compilation time. After that, the threat actor can interact with Diamorphine by sending signals allowing the following operations: hide/unhide arbitrary processes, hide/unhide the kernel module, and elevate privileges to become root.
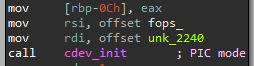
In early March 2024, we found a new Diamorphine variant undetected in-the-wild. After obtaining the sample, I examined the .modinfo section and noticed that it fakes the legitimate x_tables Netfilter module and was compiled for a specific kernel version (Kernel 5.19.17).
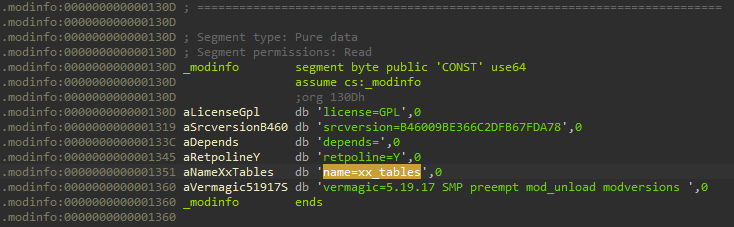
By listing the functions with Radare2, we can notice that the sample under analysis consisted of Diamorphine kernel rootkit (i.ex. module_hide, hacked_kill, get_syscall_table_bf, find_task, is_invisible, and module_show). But we can see also additional functions in the module (a, b, c, d, e, f, and setup) indicating that the sample was weaponized with more payloads.
Since Diamorphine is a well-known and open-source Linux kernel rootkit, this blog post is focused on the new features that were implemented:
- Stop Diamorphine by sending a message to the exposed device: xx_tables.
- Execute arbitrary operating system commands via magic packets.
Inserting the kernel rootkit
To insert this Diamorphine variant, we need a Linux operating system with the kernel version 5.19.17. We can find the appropriate Linux distro by using Radare2 too. Based on the compiler, we can see that Ubuntu 22.04 is a good candidate for this.
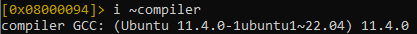
In fact, I found a person on Internet who used Ubuntu Jammy for this, and the version of the symbols of this specific Diamorphine source code partially matches the version of the symbols of the new Diamorphine variant that we found in VirusTotal (i.ex. module_layout don’t matches the version, but unregister_kprobe matches it).
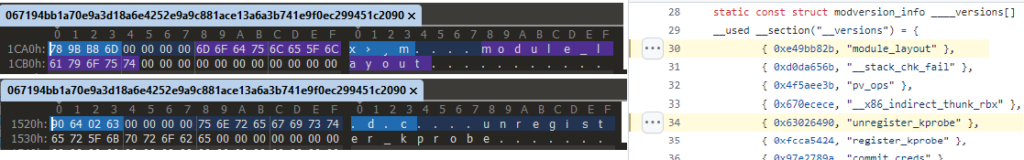
Therefore, the kernel rootkit can be inserted in an Ubuntu Jammy distro having the appropriate version of the symbols (see the Module.symvers file of the kernel where the Diamorphine variant will be inserted into).
XX_Tables: The device that the rootkit creates for user mode to kernel mode communication
Impersonating the X_Tables module of Netfiler is a clever idea because, this way, registering Netfilter hooks doesn’t raise suspicions, since interacting with Netfilter is an expected behaviour.
At the init_module function, the rootkit creates a device named xx_tables for communicating user mode space with the kernel mode rootkit.
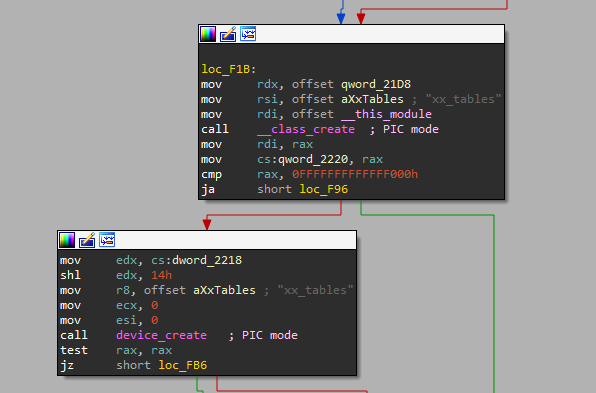
Following the everything is a file idea, the character device structure initialization function receives the file operations structure exposing the operations implemented and handled by the xx_tables device. The “g” function that appears in the file_operations structure is responsible for handling the dev_write operation.
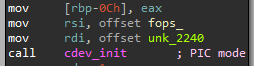
Handling the dev_write operation: The “g” function.
We can see that the function reads the commands from user mode space via xx_tables device. The memory is copied from the device using the API _copy_from_user.
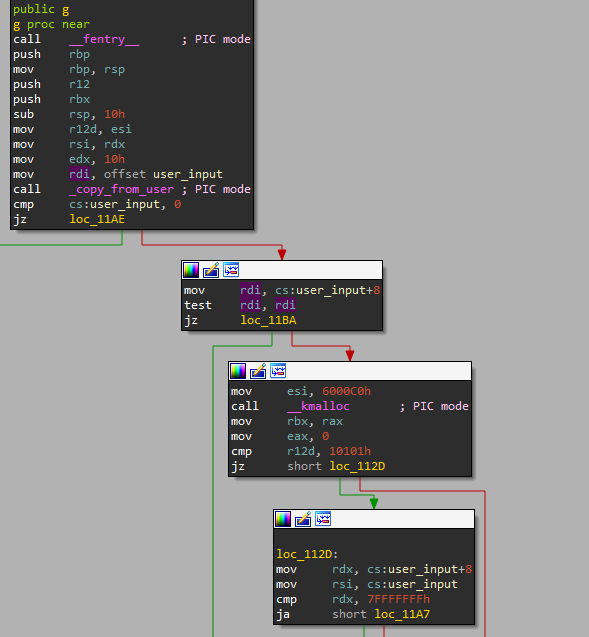
For safety reasons, the rootkit checks that the data sent from user mode space is not empty. Such data structure contains two fields: The length of the data, and a pointer to the data itself.
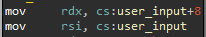
Finally, if the input sent from user mode space is the string “exit“, it calls to the exit_ function of the rootkit which restores the system, frees the resources and unloads the kernel module from memory.
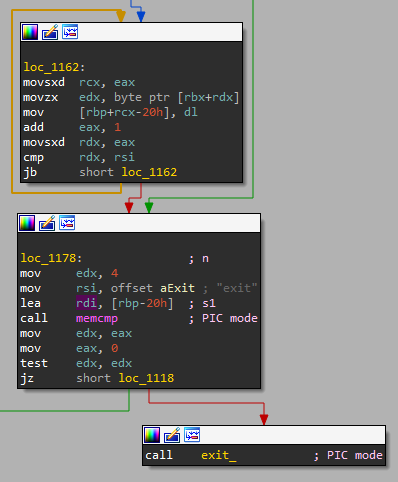
The exit_ function
The exit_ function properly restores the system and unloads the rootkit from the kernel memory. It performs the following actions:
- It destroys the device created by the rootkit.
- It destroys the struct class that was used for creating the device.
- Deletes the cdev (character device) that was created.
- Unregisters the chrdev_region.
- Unregisters the Netfilter hooks implementing the “magic packets“.
- Finally, it replaces the pointers with the original functions in the system_calls table.
The magic packets
The new Diamorphine rootkit implements “magic packets” supporting both: IPv4 and IPv6. Since the Protocol Family is set to NFPROTO_INET).
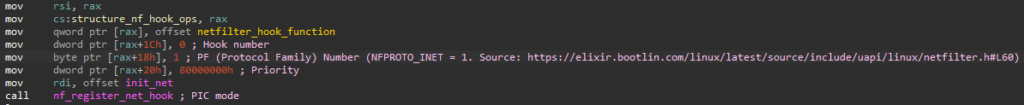
The netfilter_hook_function relies in nested calls to a, b, c, d, e and f, functions for handling the magic packets. The magic packet requirements include containing the values “whitehat” and “2023_mn” encrypted with the XOR key: 0x64.
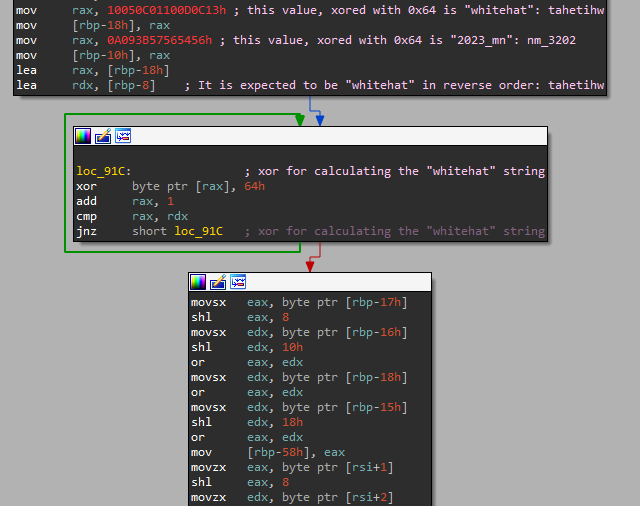
If the packet fits the requirements the arbitrary command is extracted from it and executed into the infected computer.
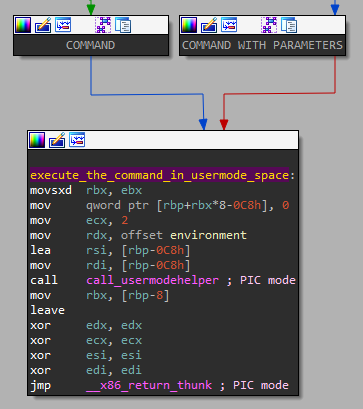
The hooks in the syscalls table
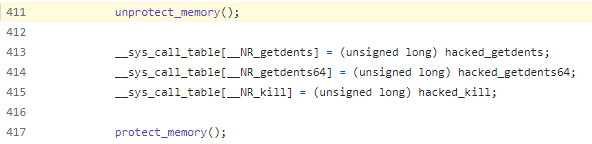
This is the original Diamorphine rootkit implementation of the syscalls hooking:
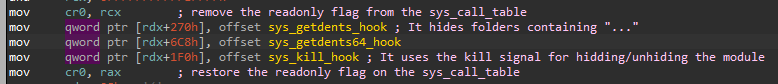
Even if the code is exactly the same in the new Diamorphine variant, it is important to highlight that it is configured to hide the files and folders containing the string: “…”.
Conclusions
We frequently discover new Linux kernel rootkits implementing magic packets that are undetected in-the-wild (i.ex. Syslogk, AntiUnhide, Chicken, etc.) and will continue collaborating and working together for providing the highest level of protection to our customers.
In this new in-the-wild version of Diamorphine, the threat actors added the device functionality allowing to unload the rootkit kernel module from memory and the magic packets functionality enabling the arbitrary commands execution in the infected system.
How to prevent infection and stay safe online
- Keep your systems up to date.
- Be sure that your Internet connection is safe to use (i.ex. Virtual Private Network).
- Avoid downloading/executing files from untrusted sources.
- Exercise the Principle of Least Privilege (PoLP). In the case of Linux, please, do not execute actions making use of the root account if it is not strictly necessary.
- Use a strong cyber safety solution such as Norton, Avast, Avira or AVG to make sure you are protected against these types of malwares.
New Diamorphine variant
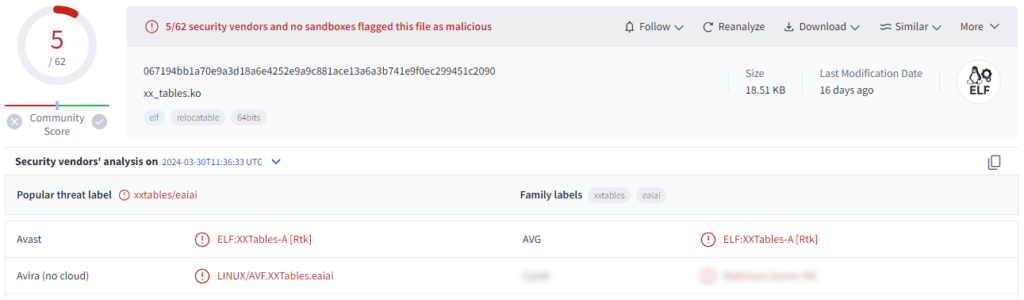
067194bb1a70e9a3d18a6e4252e9a9c881ace13a6a3b741e9f0ec299451c2090
IoC repository
The Diamorphine Linux kernel rootkit IoCs, the Yara hunting rule and the VirusTotal query are in our IoC repository.