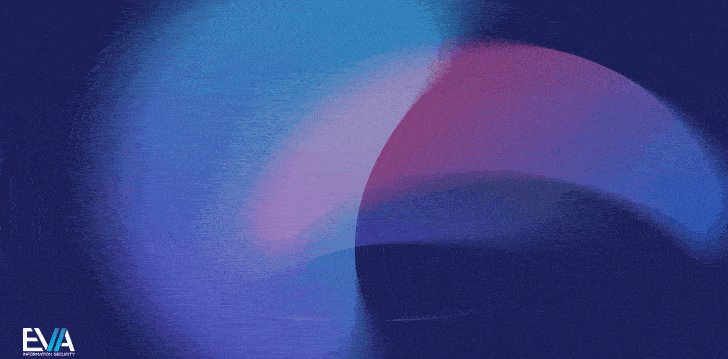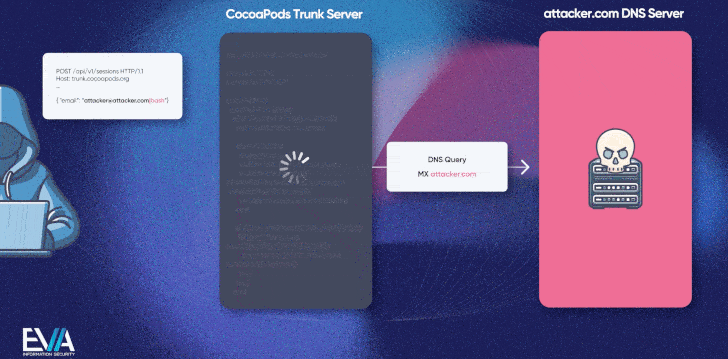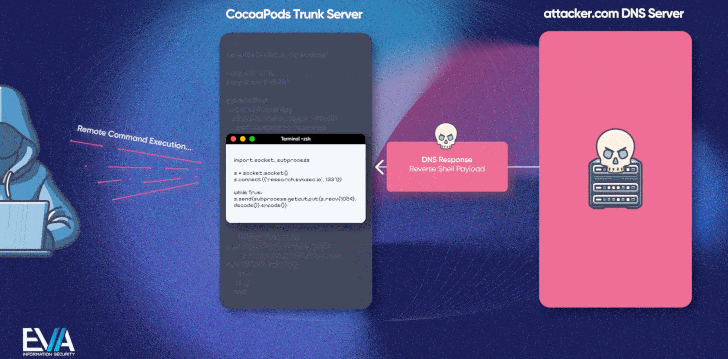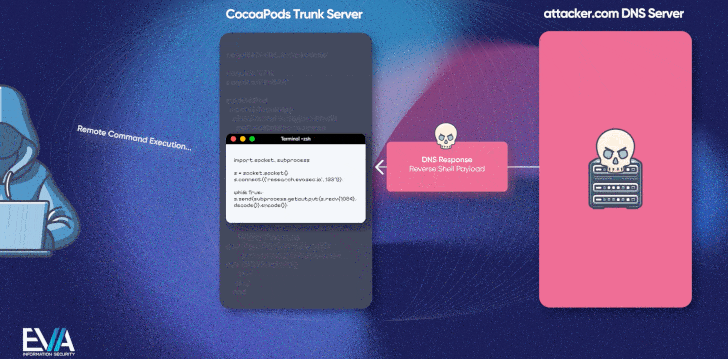A trio of security flaws has been uncovered in the CocoaPods dependency manager for Swift and Objective-C Cocoa projects that could be exploited to stage software supply chain attacks, putting downstream customers at severe risks.
The vulnerabilities allow "any malicious actor to claim ownership over thousands of unclaimed pods and insert malicious code into many of the most popular iOS and macOS applications," E.V.A Information Security researchers Reef Spektor and Eran Vaknin said in a report published today.
The Israeli application security firm said the three issues have since been patched by CocoaPods as of October 2023. It also resets all user sessions at the time in response to the disclosures.
One of the vulnerabilities is CVE-2024-38368 (CVSS score: 9.3), which makes it possible for an attacker to abuse the "Claim Your Pods" process and take control of a package, effectively allowing them to tamper with the source code and introduce malicious changes. However, this required that all prior maintainers have been removed from the project.
The roots of the problem go back to 2014, when a migration to the Trunk server left thousands of packages with unknown (or unclaimed) owners, permitting an attacker to use a public API for claiming pods and an email address that was available in the CocoaPods source code ("[email protected]") to take over control.
The second bug is even more critical (CVE-2024-38366, CVSS score: 10.0) and takes advantage of an insecure email verification workflow to run arbitrary code on the Trunk server, which could then be used to manipulate or replace the packages.
Also identified in the service is a second problem in the email address verification component (CVE-2024-38367, CVSS score: 8.2) that could entice a recipient into clicking on a seemingly-benign verification link, when, in reality, it reroutes the request to an attacker-controlled domain in order to gain access to a developer's session tokens.
Making matters worse, this can be upgraded into a zero-click account takeover attack by spoofing an HTTP header – i.e., modifying the X-Forwarded-Host header field – and taking advantage of misconfigured email security tools.

"We have found that almost every pod owner is registered with their organizational email on the Trunk server, which makes them vulnerable to our zero-click takeover vulnerability," the researchers said.
This is not the first time CocoaPods has come under the scanner. In March 2023, Checkmarx revealed that an abandoned sub-domain associated with the dependency manager ("cdn2.cocoapods[.]org") could have been hijacked by an adversary via GitHub Pages with an aim to host their payloads.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.