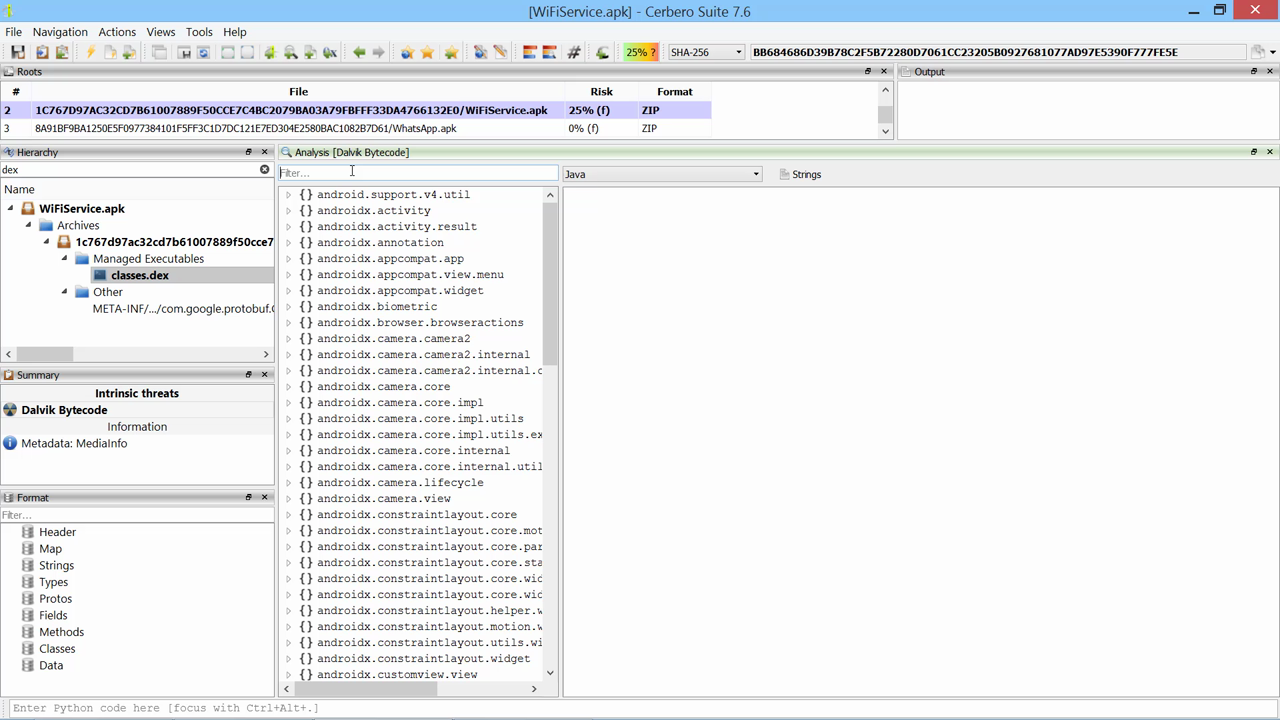
We’re excited to release the DEX Decompiler package for all licenses of Cerbero Suite: this package is capable of decompiling Android DEX files from their bytecode back to Java.
Once you have installed the package, you can access the decompiler from the bytecode view.
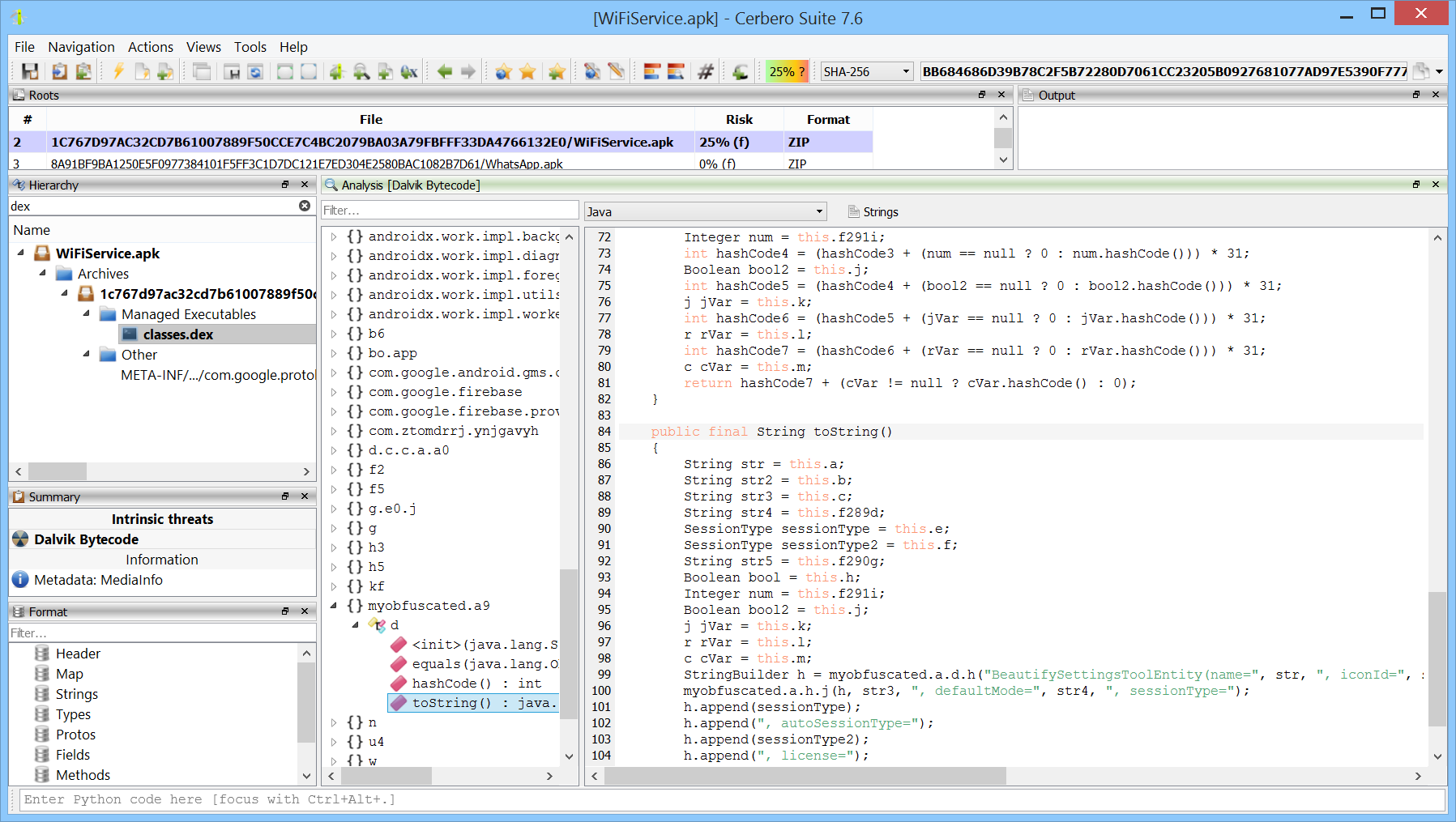
The interface provides a quick filter to show only matching namespaces, classes, and methods.
To switch between the bytecode and the decompiler, you can use the combo box at the top.
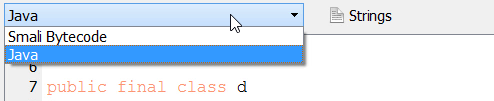
Alternatively, and even more conveniently, you can use the ‘Tab’ key to toggle between the bytecode and the decompiler, which will bring you directly from the Java code to the corresponding bytecode and vice versa.
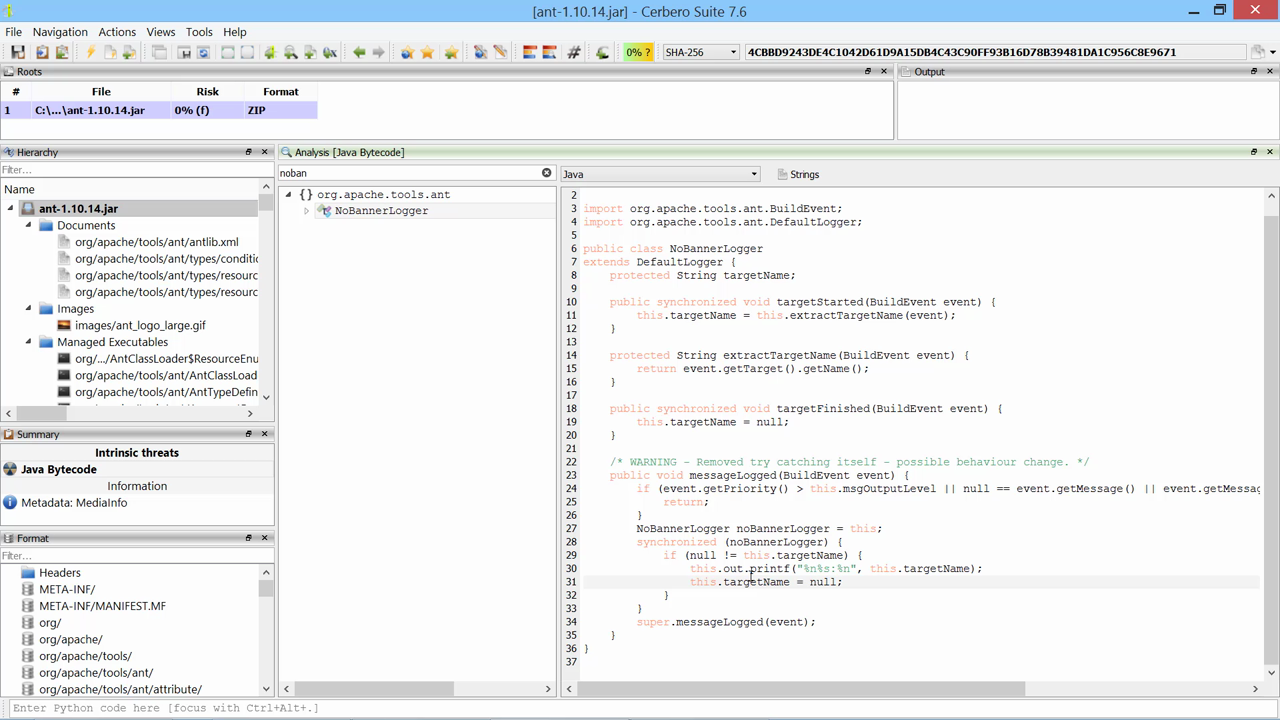
You can navigate the code both when viewing the bytecode and the decompiled output. The ‘Esc’ key will bring you back to the previous position, just like in the Carbon disassembly view.
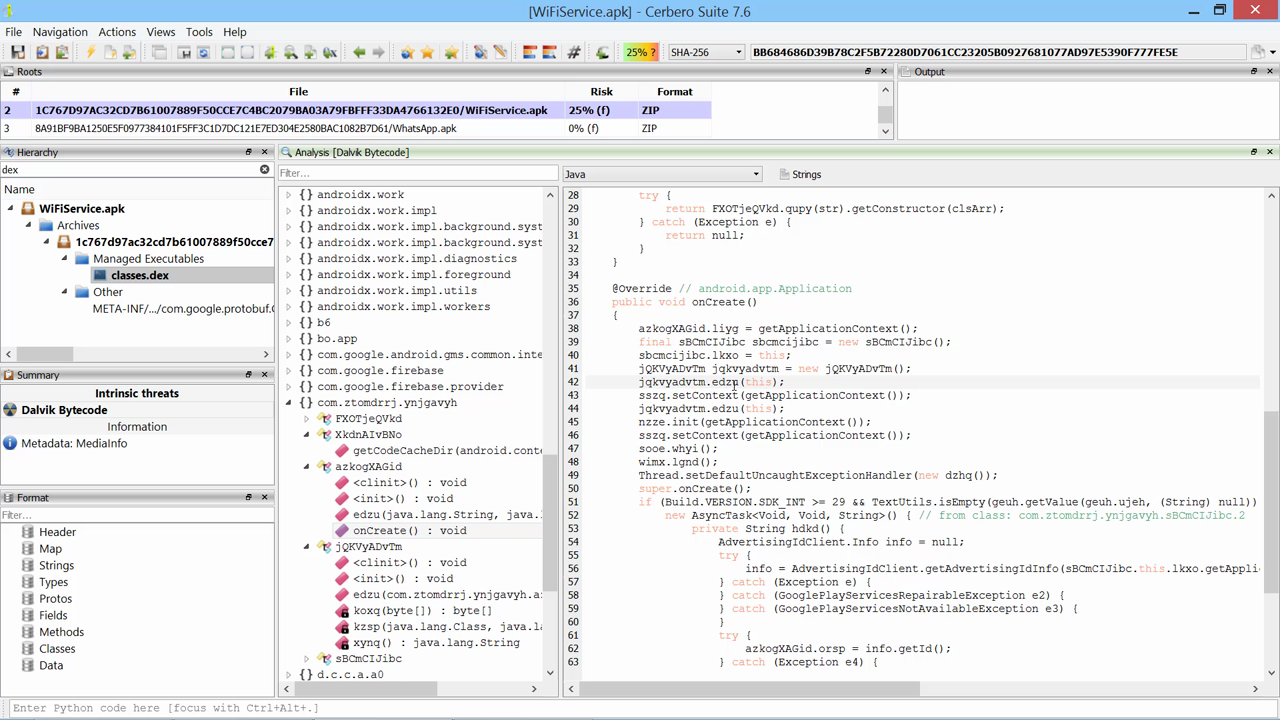
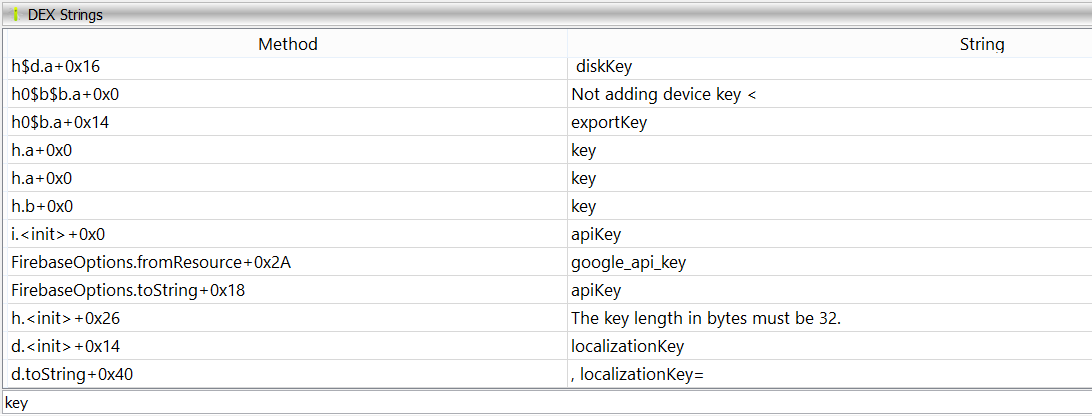
The ‘Strings’ button displays all referenced strings in the code, showing which class and method reference them. It also allows you to jump to the location where they are referenced, both in the bytecode and in the decompiled output.
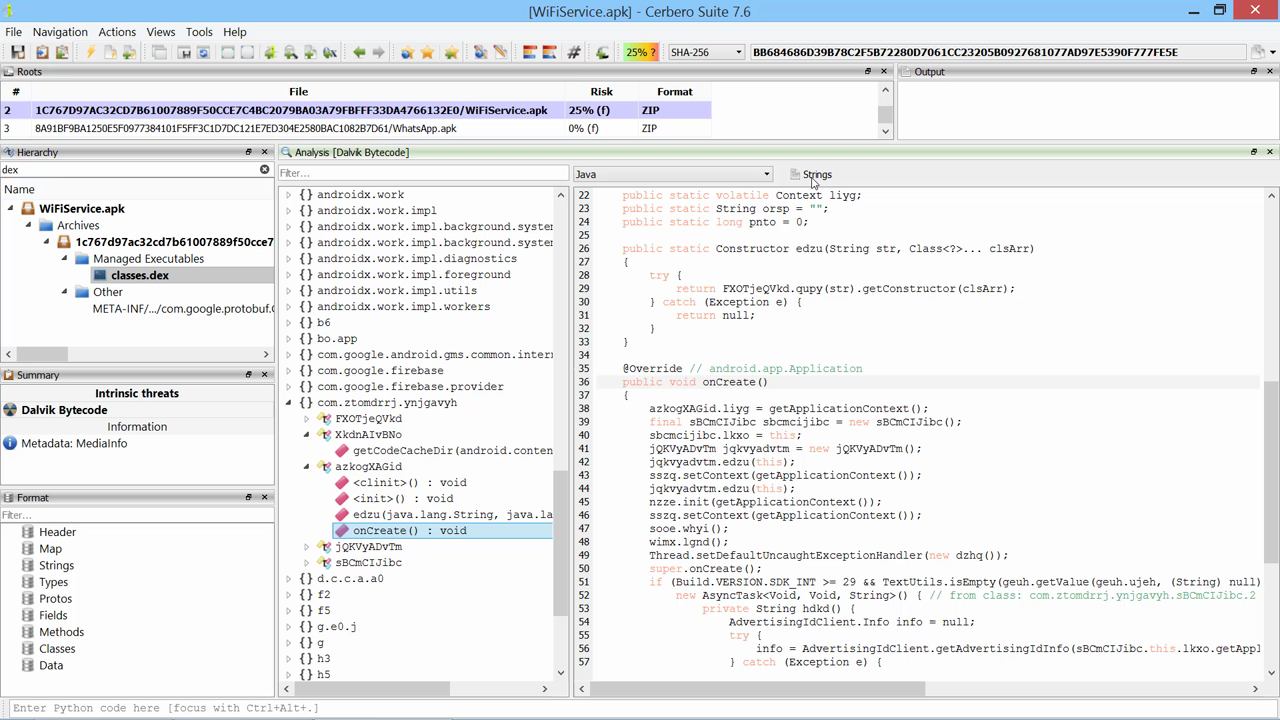
Additionally, the strings view features a filter to quickly find strings of interest.
The package is exposed to the SDK. The following code snippet demonstrates how to decompile a class in a DEX file:
from Pkg.DEXDecompiler import *
def main():
dec = DEXDecompiler()
dec.init("path/to/classes.dex")
# we specify the name of the class to decompile
text, _ = dec.decompile("com.android.providers.applications.ApplicationsAdapter")
if text != None:
print(text)
We hope that this package will be useful to our users, whether they are in IT security or digital forensics. By providing a package for decompiling Android DEX files, we aim to simplify and accelerate their day-to-day tasks.