2024-7-3 18:17:6 Author: blog.sekoia.io(查看原文) 阅读量:10 收藏
This blogpost is part of a series of articles covering our vision of cybersecurity and analyzing the benefits of SOC platforms for modern organizations. Take a look at the previous article on efficiency-driven SOC operations here.
At Sekoia.io, the integration of the MITRE ATT&CK framework into our Security Operations Center (SOC) platform is a cornerstone of our approach to cybersecurity. The ATT&CK framework serves as a comprehensive knowledge base of cyber adversary behavior and a taxonomy for adversarial actions across their lifecycle. It consists of two main parts: ATT&CK for Enterprise, which covers behaviors against enterprise IT networks and cloud environments, and ATT&CK for Mobile, focusing on behaviors against mobile devices. By meticulously evaluating this framework, we ensure that our defenses are not only comprehensive but also relevant to our clients’ unique needs. This method offers substantial benefits, providing a broad perspective on potential threats while aligning with industry standards. Let’s see why and how.
What is the MITRE ATT&CK framework?
The MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework is a comprehensive matrix that catalogs the tactics and techniques employed by cyber adversaries. It was originally developed by the U.S. Department of Homeland Security in collaboration with the MITRE Corporation in 2015 as an open reference standard to help all defenders improve their security postures against modern adversaries in cyberspace. Indeed, this framework is pivotal for threat modeling and enhancing security defenses, enabling organizations to understand the security risks linked to specific threats and refine their detection and prevention strategies. On the official MITRE ATT&CK Framework page, you’ll find this extensive matrix.

The top horizontal columns of the matrix outline various Tactics, beginning with Initial Access, Execution, Persistence, among others. Each tactic is linked to documented techniques, which are derived from observations of different Adversary Groups, as shared by cybersecurity researchers in threat intelligence reports.
The MITRE ATT&CK framework serves multiple purposes, including:
- Enhancing existing detection technologies within an organization.
- Assessing an organization’s visibility against potential attacks.
- Strengthening the organization’s current threat intelligence capabilities.
- Facilitating adversary simulations between Red and Blue Teams to identify weaknesses.
- Advancing the maturity of an organization’s Threat Hunting Program.
It’s essential to understand that the tactics and techniques documented in the MITRE ATT&CK matrix represent knowledge that is widely recognized within the cybersecurity community. There might be other tactics and techniques not yet documented. As such, the ATT&CK matrix continually evolves, incorporating new tactics and techniques over time.
The primary goal of the MITRE ATT&CK framework is to deepen the understanding of adversaries’ characteristics and actions, including the tactics, techniques, and tools they use. This insight helps stakeholders and system owners improve their awareness and enhance their protection and detection mechanisms. Moreover, MITRE aims to establish a standardized taxonomy for identifying and labeling threat actors based on their operational methods, fostering better information sharing between communities and organizations.
Implementing ATT&CK in Sekoia.io’s SOC Platform
At Sekoia.io, we leverage the ATT&CK framework in several key ways. Our journey begins with exclusive threat intelligence, systematically modeling adversary tactics, techniques, and procedures (TTPs) using ATT&CK. This comprehensive modeling helps us understand and anticipate adversary behaviors, enhancing our defensive strategies.

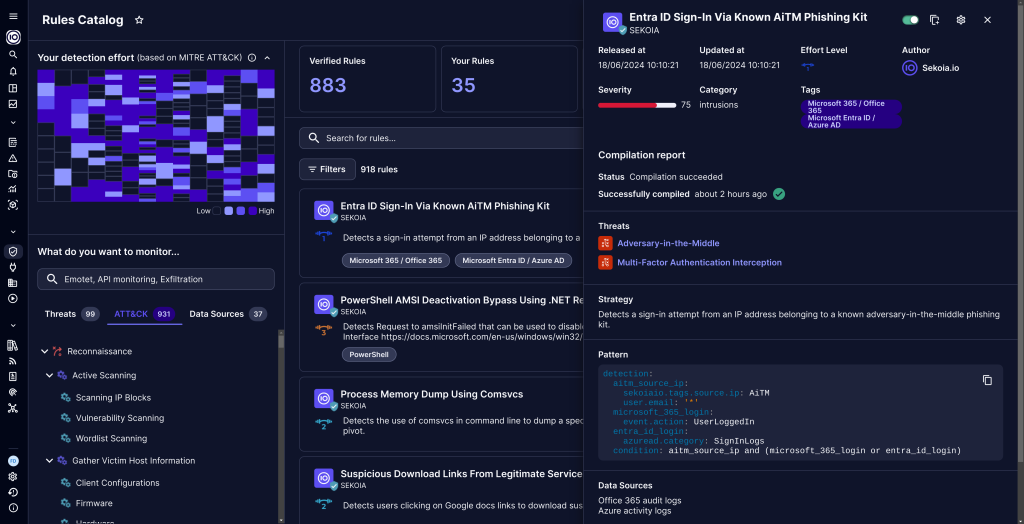
One of the standout features of our implementation is the ATT&CK mapping over our SIGMA rules. Our rule catalogue, which includes approximately 900 detections at the date of writing this article, is meticulously mapped to specific techniques. This mapping is key for a threat-centric understanding of our customers attack surface detection. It allows us to filter rules based on TTPs and identify coverage gaps within the ATT&CK matrix, providing a clear overview of both our strengths and areas needing improvement.

Additionally, each data source—or intake, in Sekoia.io terminology—is mapped to the ATT&CK framework. These mappings are publicly available on our GitHub repository and directly in our documentation, ensuring up-to-date views in the ATT&CK Navigator. By documenting how collected data contributes to detection, our customers and partners gain a deeper appreciation of the comprehensive coverage our integrated security technologies provide, enhancing their return on investment.
Enlarge the image with a single click
Looking Forward
With this foundation, bridging the gap between raw threat intelligence and the detection of adversaries using ATT&CK Techniques as pivots, e.g. leveraging the TTPs modeling, we now are eager to explore compounded coverage across customer security stack. One of our key objectives moving forward is to provide a comprehensive view of how various data sources contribute to the overall security posture. This endeavor aims to optimize the collection-to-value noise ratio, ensuring that the data gathered is both relevant and actionable.
This comprehensive view will help drive the optimization of the security stack itself and guide investments, enabling our clients to rationalize their return on investment over time across different security solutions. While this presents a challenge, it is crucial for maximizing the efficiency and effectiveness of the security measures in place.
By focusing on these goals, we aim to enhance our clients’ ability to detect, understand, and respond to threats more effectively.
Acknowledging Challenges
While the ATT&CK framework is a powerful tool, it is not without its challenges. One inherent limitation is that ATT&CK describes only known techniques, which means it may not account for emerging threats that have not yet been documented. Despite this limitation, ATT&CK remains a valuable tool for abstracting over the raw data traditionally used by threat intelligence-driven defenders.
Recognizing these constraints, we have invested in parallel efforts to detect unknown threats using machine learning models that identify signals amidst the noise. This additional detection layer enhances our platform by providing the capability to uncover novel threats that may otherwise go unnoticed.
A sole focus on MITRE coverage can also lead to a false sense of security, as relying exclusively on known techniques may neglect emerging threats. Additionally, striving for complete coverage can be resource-intensive, potentially detracting from other critical security needs. Balancing these aspects is essential to maintaining a robust defense posture.
Wrapping up
The integration of the MITRE ATT&CK framework into Sekoia.io’s SOC platform exemplifies our commitment to providing robust, relevant, and comprehensive security solutions. We will continue to unveil insights on how we develop around the framework in upcoming articles.
We are always eager to hear from the community about what they find useful and how we can accelerate the provision of tools for their daily needs within our SOC platform. By continuously refining our approach, incorporating advanced machine learning techniques, and addressing inherent challenges, we ensure that our clients are well-equipped to face the ever-evolving landscape of cyber threats.
You can check out other blogposts :
Fabien Dombard Chief eXperience Officer
如有侵权请联系:admin#unsafe.sh
