2024-7-4 19:30:19 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Security professionals constantly battle to identify and patch vulnerabilities before attackers exploit them. But how do we measure the severity of these vulnerabilities? Enter the Common Vulnerability Scoring System (CVSS), a standardized method for assessing vulnerability risk. In this blog, we will dive into details about the CVSS score:
Table of Contents:
- What is a CVSS score?
- Understanding the Why: The Need for CVSS 4
- CVSS Metrics
- CVSS Base Metrics
- CVSS Temporal Metrics
- CVSS Environmental Metrics
- Is the CVSS score enough for vulnerability management?
- What to Use Alongside CVSS Scores?
- Take your Vulnerability Management to the Next Level
1. What is a CVSS score?
The Common Vulnerability Scoring System (CVSS) is a cornerstone of effective vulnerability management. CVSS empowers security professionals to prioritize remediation efforts and bolster overall cyber resilience by offering a standardized method for assessing vulnerability severity. This in-depth guide delves into the intricacies of CVSS, equipping you with the knowledge to leverage it for a more secure digital landscape.
Security analysts, vulnerability managers, and incident responders rely on CVSS scores to prioritize which vulnerabilities require the most urgent attention. This enables them to focus their efforts on patching or mitigating the most critical risks first, optimizing their security posture.
There are several places where you can check CVSS scores for vulnerabilities:
- National Vulnerability Database (NVD): National Vulnerability Database (NVD) | NIST (.gov)
- Vulnerability Scanner Reports
- CVE Details: Strobes Vulnerability Intelligence
CVSS assigns a numerical score (0.0-10.0) to each vulnerability, reflecting its potential impact on an organization’s security posture. Higher scores signify greater severity, demanding swifter mitigation strategies. Additionally, CVSS categorizes vulnerabilities into severity levels:
- Critical (9.0-10.0): Exploitable with devastating consequences. Immediate remediation is paramount.
- High (7.0-8.9): Significant potential for harm. Prioritize patching or implementing countermeasures.
- Medium (4.0-6.9): Moderate cause for concern. Address within a reasonable timeframe.
- Low (0.1-3.9): Minimal potential for exploitability. Mitigate when resources permit.
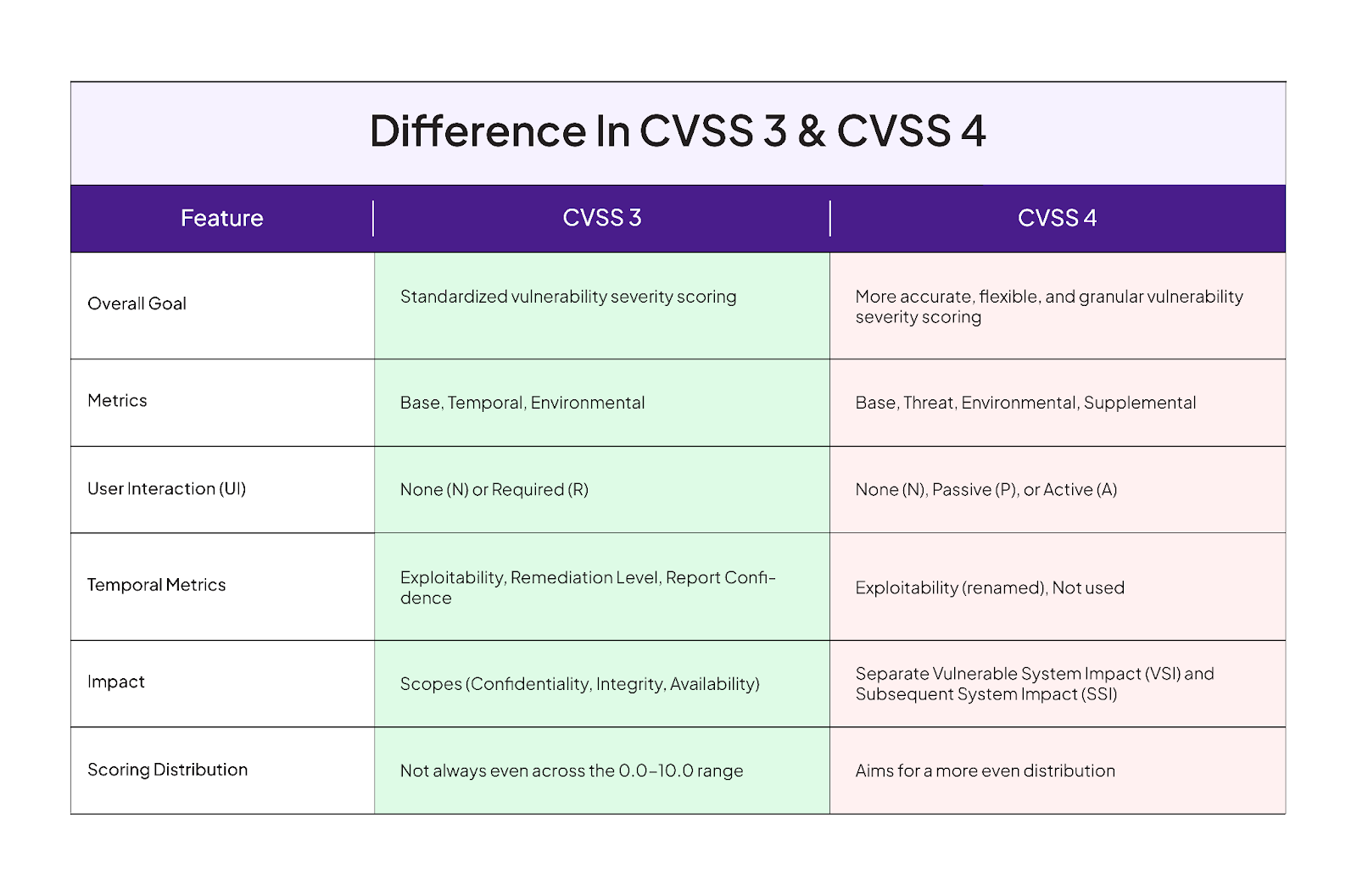
2. Understanding the Why: The Need for CVSS 4
While CVSS 3 has been the industry standard for over a decade, it wasn’t without its limitations. The new version addresses these shortcomings by offering:
- Increased Accuracy: CVSS 4 refines the scoring system to better reflect real-world risk based on new metrics like “Attack Requirements.”
- Enhanced Flexibility: The system is more adaptable to emerging threats, particularly in the realm of IoT and OT vulnerabilities.
- Granular Detail: CVSS 4 provides a more nuanced view of exploitability with options like “Passive” and “Active” user interaction.
Breaking Down the Key Changes
The most significant differences lie in the metrics used for scoring. Here’s a quick comparison:
- Metrics: CVSS 4 introduces new metrics like “Attack Requirements” and revamps others like “User Interaction” for better granularity. It also separates the impact scope into “Vulnerable System Impact” and “Subsequent System Impact” categories.
- Temporal vs. Threat Metrics: CVSS 3’s “Temporal Metrics” are renamed “Threat Metrics” in CVSS 4, with some streamlining.
- Scoring Distribution: CVSS 4 aims to achieve a more even distribution of scores across the 0.0 to 10.0 range, addressing a shortcoming of CVSS 3.
3. CVSS Metrics
These metrics form the bedrock of a CVSS score, dissecting the inherent properties of the vulnerability itself. Imagine them as a vulnerability’s DNA, independent of the specific environment or the latest exploit techniques. Here, we dig into three critical aspects:
4. CVSS Base Metrics
These metrics form the bedrock of a CVSS score, dissecting the inherent properties of the vulnerability itself. Imagine them as a vulnerability’s DNA, independent of the specific environment or the latest exploit techniques. Here, we delve into three critical aspects:
1. Exploitability
This metric quantifies the effort required for a malicious actor to successfully exploit the vulnerability. We meticulously evaluate the attack vector (e.g., network access required), attack complexity (ease of exploitation), and privileges required (attacker permissions needed). A vulnerability requiring minimal attacker effort and low privileges to exploit would naturally receive a higher score due to its inherent accessibility.
The Exploitability metrics within CVSS provide a detailed picture of the effort required for a malicious actor to successfully exploit a vulnerability. These metrics are crucial for understanding the immediate threat posed by a vulnerability. Let’s delve into each metric and its corresponding scoring system:
a. Attack Vector (AV):
This metric assesses the level of access an attacker needs to exploit the vulnerability. Here’s the breakdown of scoring and its implications:
- Network (AV:N): The vulnerability can be exploited remotely over a network. This signifies the highest level of exploitability as attackers don’t require physical access to the system. (Score: High)
- Adjacent (AV:A): The vulnerability can be exploited from a nearby system on the same network. This indicates a moderate level of exploitability as attackers require some level of network access. (Score: Medium)
- Local (AV:L): The vulnerability requires physical access to the system or local user privileges to exploit. This signifies a lower level of exploitability as attackers need direct access to the compromised machine. (Score: Low)
- Physical (AV:P): The vulnerability can only be exploited through physical access to the system. This represents the lowest level of exploitability as attackers need direct physical interaction with the machine. (Score: Low)
b. Attack Complexity (AC):
This metric evaluates the technical difficulty involved in exploiting the vulnerability. Here’s the scoring system and its implications:
- Low (AC:L): Exploiting the vulnerability requires minimal technical expertise or specific tools. This signifies a higher level of exploitability as even less skilled attackers might pose a threat. (Score: High)
- High (AC:H): Exploiting the vulnerability requires specialized skills or custom tools. This indicates a moderate level of exploitability as attackers need some level of technical proficiency. (Score: Medium)
c. Privileges Required (PR):
This metric assesses the level of access (privileges) an attacker needs to exploit the vulnerability. Here’s the scoring system and its implications:
- None (PR:N): No special privileges are required to exploit the vulnerability. This signifies the highest level of exploitability as even unprivileged users might be able to exploit it. (Score: High)
- Low (PR:L): User privileges are required, but they are typically assigned to standard user accounts. This indicates a moderate level of exploitability as attackers might need to compromise a user account first. (Score: Medium)
- High (PR:H): Privileged access (administrator or root) is required to exploit the vulnerability. This signifies a lower level of exploitability as attackers need to escalate privileges to exploit it. (Score: Low)
By analyzing these Exploitability metrics within CVSS, vulnerability analysts can gain valuable insights into the immediate threat posed by a vulnerability. This information, combined with other CVSS metrics and threat intelligence, empowers them to prioritize remediation efforts and bolster organizational security.
2. Impact
These metrics focus on the potential consequences of a successful exploit. Understanding the potential impact empowers security teams to prioritize vulnerabilities that pose the greatest risk to critical assets and data.
Here, we shift our focus to the potential consequences of a successful exploit. We assess the potential damage across three key areas: confidentiality (unauthorized information disclosure), integrity (data modification or destruction), and availability (denial of access to authorized users). A vulnerability that allows attackers to steal sensitive data (high confidentiality impact) or disrupt critical operations (high availability impact) would naturally warrant a higher score.
- Confidentiality (C): This metric evaluates the potential for unauthorized disclosure of information. Here’s the scoring system:
- High (C:H): A successful exploit could result in complete or significant disclosure of confidential information. (Score: High)
- Low (C:L): A successful exploit might result in disclosure of limited, low-impact information. (Score: Low)
- None (C:N): No potential for unauthorized disclosure of information. (Score: None)
- Integrity (I): This metric evaluates the potential for unauthorized modification or destruction of data. Here’s the scoring system:
- High (I:H): A successful exploit could result in complete or significant modification or destruction of data. (Score: High)
- Low (I:L): A successful exploit might result in limited, low-impact data modification or destruction. (Score: Low)
- None (I:N): No potential for unauthorized modification or destruction of data. (Score: None)
- Availability (A): This metric evaluates the potential for denial of access to authorized users. Here’s the scoring system:
- High (A:H): A successful exploit could result in complete or significant disruption of access to a system or resource. (Score: High)
- Low (A:L): A successful exploit might result in limited, low-impact disruption of access. (Score: Low)
- None (A:N): No potential for denial of access to a system or resource. (Score: None)
By analyzing both Exploitability and Impact metrics, vulnerability analysts gain a comprehensive understanding of the potential threat a vulnerability poses. This information, coupled with other CVSS metrics and threat intelligence, guides effective vulnerability management strategies, prioritizing the most critical vulnerabilities for remediation efforts.
3. Scope
The scope metric within CVSS plays a crucial role in understanding the potential ripple effects of a vulnerability. It goes beyond the initial point of compromise, analyzing whether a successful exploit can pave the way for attackers to move laterally within the network and compromise additional systems. This metric assesses the potential for attackers to leverage the vulnerability to gain unauthorized access to additional resources within the system or network.
a. Scoring System:
- Unchanged (S:U): A successful exploit has limited impact on the affected component itself. There’s no potential for attackers to use this vulnerability to gain control of other systems or resources within the environment. (Score: Low)
- Changed (S:C): A successful exploit can be leveraged by attackers to compromise additional resources within the same system or network. This signifies a broader potential impact as attackers can potentially escalate privileges and move laterally. (Score: High)
b. Implications of Scope:
- Higher Scope Score: A vulnerability with a “Changed” scope score signifies a greater potential for attackers to gain a foothold within the system and launch further attacks. This warrants a higher CVSS score due to the amplified risk.
Example:
- Imagine a vulnerability in a web application that allows attackers to steal user credentials (high impact). However, the vulnerability resides in a sandboxed environment, and attackers cannot use it to escape that environment or compromise other systems (unchanged scope). This would likely receive a lower CVSS score compared to the same vulnerability that allows attackers to pivot and compromise critical servers within the network (changed scope).
4. CVSS Temporal Metrics
CVSS Temporal Metrics focus on the time-dependent aspects of a vulnerability’s exploitability. These metrics help us understand how the risk associated with a vulnerability can change over time. Here’s a breakdown:
a. What they measure:
- Existence of Public Exploit Code: This is the biggest factor influencing a vulnerability’s exploitability over time. If publicly available exploit code exists, attackers don’t need to develop their own tools, making exploitation easier and more widespread.
- Exploit Maturity: The sophistication of exploit code also plays a role. A simple exploit script can be readily used by less skilled attackers, whereas a complex exploit might require more advanced skills. Both factors influence the overall risk.
b. Why they’re important:
- A vulnerability with readily available, easy-to-use exploit code poses a significantly greater threat compared to one with no publicly available exploit.
- Temporal metrics help us understand the current exploitability of a vulnerability, not just its inherent characteristics.
c. How they’re used:
- CVSS itself doesn’t assign specific scores for Temporal Metrics.
- Instead, it provides a framework for considering these factors when evaluating a vulnerability’s overall severity.
- Security professionals use their judgment and threat intelligence to assess the exploitability based on the availability and maturity of exploit code.
5. CVSS Environmental Metrics
Environmental Metrics go beyond the inherent characteristics of a vulnerability and consider your organization’s security posture. These metrics allow you to refine the CVSS score to better reflect the true risk within your own environment. Here’s a breakdown of the key factors:
- Affected Assets:
- The type of asset impacted by the vulnerability plays a crucial role. A vulnerability affecting critical infrastructure, like a server holding financial data, would naturally be more concerning than one impacting a low-impact system, like a printer.
- Data Sensitivity:
- The sensitivity of the data stored on the affected assets is another critical consideration. A vulnerability that exposes sensitive financial records would naturally warrant a higher score compared to one compromising less sensitive data, like employee email addresses.
- Existing Security Controls:
- We assess the presence and effectiveness of existing security controls that might mitigate the impact of the vulnerability. Intrusion detection systems, firewalls, and other controls can potentially lessen the severity of the vulnerability within your specific environment.
6. Is the CVSS score enough for vulnerability management?
The answer is straightforward: NO.
A CVSS score alone is not sufficient for effective vulnerability management. While CVSS offers a valuable standardized method for assessing vulnerability severity, it has limitations that necessitate a more comprehensive approach.
1. Strengths of CVSS Scores
- Standardized: CVSS provides a common language for communicating vulnerability severity. This allows easy comparison across different vulnerabilities and platforms (https://www.first.org/cvss/).
- Prioritization: CVSS scores can be a starting point for prioritizing remediation efforts, with higher scores indicating potentially greater risk.
- Communication: The standardized nature facilitates communication within security teams and with external stakeholders.
2. Limitations of CVSS Scores
- Doesn’t Account for Context: CVSS focuses on the inherent characteristics of a vulnerability, not the specific environment. It doesn’t consider factors like:
- Affected Assets: The type of asset impacted (critical server vs. printer) significantly influences risk.
- Data Sensitivity: The sensitivity of data stored on the affected asset plays a crucial role (e.g., financial data vs. employee email addresses).
- Existing Security Controls: Intrusion detection systems, firewalls, and other controls can mitigate the impact of a vulnerability.
- Doesn’t Reflect Exploitability: CVSS has Temporal Metrics for exploitability (existence of public exploits), but these aren’t directly incorporated into the base score (https://www.first.org/cvss/v3.1/use-design).
- Doesn’t Consider Business Impact: CVSS doesn’t factor in your organization’s risk tolerance or business priorities. A vulnerability with a high CVSS score might be less critical if it doesn’t impact core business functions.
7. What to Use Alongside CVSS Scores?
1. Environmental Metrics:
CVSS offers a framework for Environmental Metrics, which consider your specific security posture. These factors refine the CVSS score and reflect the true risk within your environment. Here’s a breakdown of key Environmental Metrics:
- Affected Assets: The type of asset impacted by the vulnerability plays a crucial role. A vulnerability affecting critical infrastructure, like a server holding financial data, would naturally be more concerning than one impacting a low-impact system, like a printer.
- Data Sensitivity: The sensitivity of the data stored on the affected assets is another critical consideration. A vulnerability that exposes sensitive financial records would naturally warrant a higher score compared to one compromising less sensitive data, like employee email addresses.
- Existing Security Controls: The presence and effectiveness of existing security controls, such as intrusion detection systems and firewalls, can potentially lessen the severity of the vulnerability within your specific environment.
2. Threat Intelligence:
Understanding the current threat landscape is crucial. Threat intelligence feeds provide insights into the likelihood of a vulnerability being actively exploited. This information, combined with CVSS scores, helps prioritize vulnerabilities based on the real-world risk they pose. Threat intelligence feeds can be obtained from security vendors or reputable organizations focused on cybersecurity, such as:
- MITRE ATT&CK
 : MITRE ATT&CK for Enterprise
: MITRE ATT&CK for Enterprise - Cybersecurity & Infrastructure Security Agency (CISA): CISA Known Exploited Vulnerabilities Catalog
3. Vulnerability Management Tools:
Many vulnerability management tools go beyond CVSS scores. These tools offer additional context that can be invaluable for prioritizing vulnerabilities. Here are some examples of what these tools might provide:
- Exploit Details: Information about the existence and sophistication of exploit code for the vulnerability.
- Remediation Recommendations: Guidance on how to address the vulnerability, including patches, workarounds, or configuration changes.
- Integration with Threat Intelligence: The ability to combine CVSS scores with threat intelligence data for a more comprehensive risk assessment.
8. Take your Vulnerability Management to the Next Level
While CVSS provides a strong foundation, for a truly proactive defense, consider exploring advanced vulnerability management solutions. The Strobes Vulnerability Intelligence platform offers a comprehensive archive of the latest vulnerabilities, exploits, and CVEs targeting specific platforms or applications (https://vi.strobes.co/). This empowers you to:
- Stay Ahead of the Curve: Strobes keeps you updated on the latest threats, ensuring your vulnerability management adapts to the evolving threat landscape.
- Gain Actionable Insights: Move beyond basic CVSS scores and access detailed exploit information to prioritize remediation efforts effectively.
- Simplify Workflows: The Strobes platform integrates seamlessly with your existing security tools, streamlining vulnerability management processes.
By using CVSS alongside these strategies, you can transform vulnerability management from a reactive scramble to a proactive defense. Remember, CVSS is your ally, but true security requires a multi-layered approach. The fight against cyber threats is a marathon, not a sprint, and CVSS equips you to run the race strategically. With advanced vulnerability management solutions like Strobes, you gain the endurance and insights needed to stay ahead of the curve.
The post CVSS Score: A Comprehensive Guide to Vulnerability Scoring appeared first on Strobes Security.
*** This is a Security Bloggers Network syndicated blog from Strobes Security authored by Alibha. Read the original post at: https://strobes.co/blog/cvss-score-a-comprehensive-guide-to-vulnerability-scoring/
如有侵权请联系:admin#unsafe.sh