2024-7-5 21:0:7 Author: www.sentinelone.com(查看原文) 阅读量:6 收藏
The Good | International Joint Operation Takes Down Over 600 IP Addresses Abusing Cobalt Strike Tool
Hundreds of IP addresses abusing Cobalt Strike have been shut down in a joint effort involving law enforcement across several nations. Codenamed “Morpheus”, the joint operation resulted in flagging 690 IP addresses and domains used to infiltrate victim networks. So far, 593 of them have been taken offline.
The servers flagged in Operation Morpheus used old, unlicensed versions of Cobalt Strike – a popular penetration testing tool used by red teams to simulate cyberattacks in order to evaluate the security posture of a network. Over the years, cracked, stolen, or reverse-engineered versions of the tool have made their way into the hands of malicious actors, enabling them to carry out a host of complex and damaging attacks.
Although the tool is legitimate and designed for threat emulation exercises and supporting offensive security operations, Cobalt Strike continues to be a double-edged sword being widely exploited and gaining a reputation on the dark web as a ‘go-to’ network intrusion tool. Illicit versions of Cobalt Strike, often accompanied by free training guides and tutorial videos, have lowered the barrier for entry into cybercrime, allowing criminals with limited funds or technical expertise to launch sophisticated attacks.
The success of Operation Morpheus is the result of collaboration between the United Kingdom’s National Crime Agency, authorities from Australia, Canada, Germany, the Netherlands, Poland, the United States, and various industry partners providing analytical and forensic support.
While acting as a virtual command post for the three-year-long operation, Europol confirmed that over 730 pieces of cyber threat intelligence and close to 1.2 million IoCs were shared between all participating parties. International disruptions like Operation Morpheus are critically effective in removing the tools and services that underpin cybercriminal infrastructure online.
Great effort! 25% drop in total active servers based on the data in @only_scans. https://t.co/9CpMEtTdoS pic.twitter.com/2hGwR2X5Q7
— Silas Cutler // p1nk (@silascutler) July 3, 2024
The Bad | Novel Ransomware Operator ‘Brain Cipher’ Disrupts Indonesian Data Centers
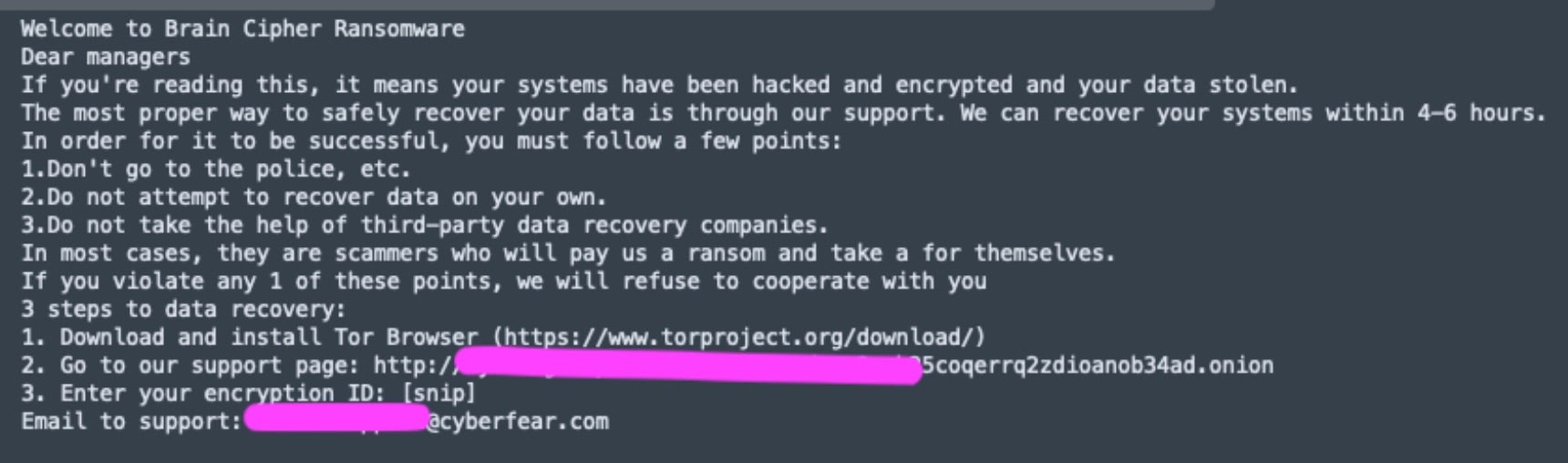
A new ransomware operation called Brain Cipher is gaining notoriety after targeting Indonesia’s temporary National Data Center (PDNS), designed to securely store government servers for online services and host sensitive data. In the recent attack, core services such as immigration, passport control, and event permitting were disrupted in over 200 government agencies. After encrypting the servers, Brain Cipher was reported to have demanded $8 million in Monero cryptocurrency for a decryptor and to prevent stolen data from being made public.
Brain Cipher was launched in early June and is being observed in attacks on critical industries and organizations worldwide. Since its debut onto the ransomware scene, the ransomware has been uploaded to malware-sharing sites, which show the payloads being based on LockBit 3.0. Threat actors behind Brain Cipher operations have also begun linking a data leak site to their ransom demands, indicating that exfiltrated data will likely be used in double and triple extortion attacks going forward.
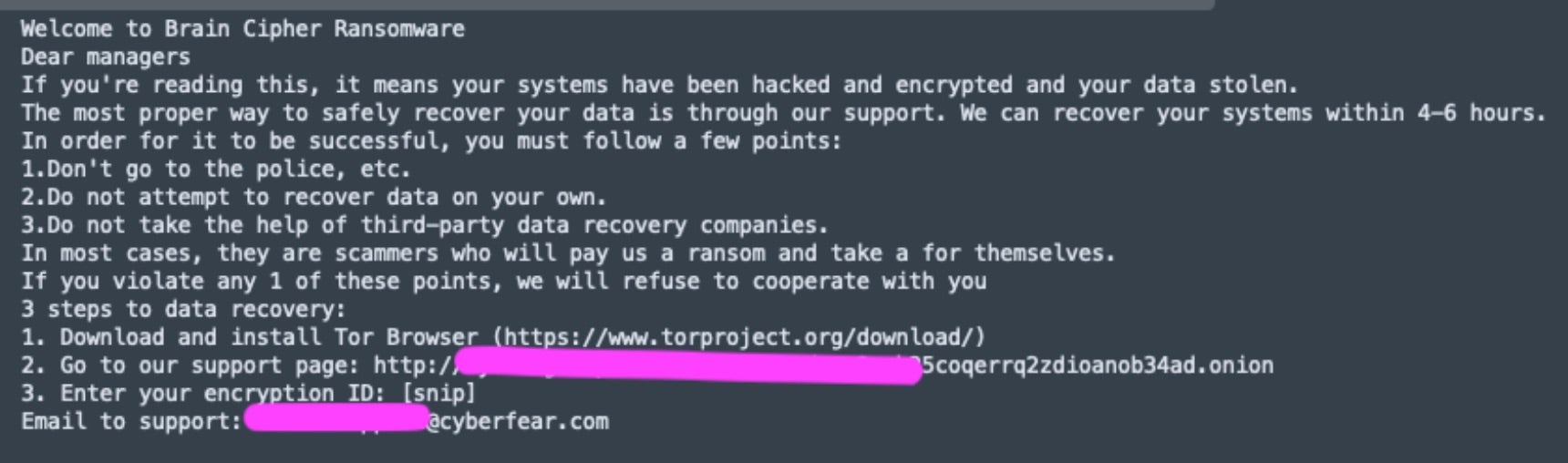
While technical functionality of Brain Cipher payloads is identical to those observed across all output from the leaked LockBit 3.0/LockBit Black builders, the operators have made minor changes such as adding an extension to encrypted files and also encrypting the file name itself. The ransomware also creates ransom notes in the format of [extension].README.txt, briefly describing the attack, making threats, and linking to Tor negotiation and data leak sites. Each victim has a unique encryption ID for the negotiation site, which includes a chat system for communication with the attackers.
SentinelOne customers are automatically protected from malicious activities associated with Brain Cipher. See how the Singularity Platform detects and protects against this novel ransomware.
The Ugly | Transparent Tribe Updates CapraRAT Spyware to Target Modern Android OS Users
A months-long campaign spreading malware-laden apps continues to embed spyware into popular video browsing platforms. In a new report by SentinelLabs, researchers detail Pakistani state-backed threat actor Transparent Tribe’s recent efforts to update its spyware to better suit the modern Android devices of their victims.
Transparent Tribe has been active since at least 2016. The outfit often uses social engineering-based tactics such as spear phishing and watering hole attacks to deliver both Windows and Android spyware. Latest observations show a continuation of its CapraTube campaign, first identified by SentinelLabs in September 2023. CapraTube initially used CapraRAT weaponized Android applications (APKs) to target YouTube users. Now, the actor has expanded the campaign to further target mobile gamers, weapons enthusiasts, and TikTok users by maximizing their spyware’s compatibility with both older and modern versions of the Android OS.
The four newest versions of CapraRAT use WebView to launch URLs to YouTube or mobile gaming site CrazyGames[.]com. CapraRAT then secretly accesses locations, SMS messages, contacts, and call logs while also taking screenshots and recording audio and video. These updates to CapraRAT show the removal of certain permissions, indicating a shift towards using the spyware as a surveillance tool rather than a backdoor. The focus on newer Android versions aligns with their higher value targets: individuals in the Indian government or military who are unlikely to use older devices.
While the updates to CapraRAT code is minimal, these kinds of incremental changes within long-running campaigns highlight how malware operators focus on making their tools more reliable and stable. Implementing mobile device management (MDM), strict application allowlisting, MFA, and robust endpoint protection ensures organizations are protected against campaigns similar to CapraTube.
如有侵权请联系:admin#unsafe.sh