
2024-7-16 13:34:45 Author: securityboulevard.com(查看原文) 阅读量:17 收藏
In a significant development for cybersecurity, a new vulnerability has been detected in OpenSSH, the widely-used suite for secure network communications. This flaw poses a serious risk, potentially allowing malicious actors to remote code execution on affected systems. Understanding and mitigating this OpenSSH vulnerability is essential for secure data transfers and remote server management globally. In this blog post, we’ll look into the details of the newly discovered risk, exploring its potential impact and providing actionable steps to safeguard your systems against this emerging threat.
Brief About OpenSSH Vulnerability (CVE-2024-6409)
A new vulnerability, CVE-2024-6409, has been discovered in select versions of the OpenSSH secure networking suite, which can potentially lead to remote code execution (RCE). CVE-2024-6409, with a CVSS score of 7.0, is caused by a race condition in the privsep child’s signal handling, differing from CVE-2024-6387 (RegreSSHion). The vulnerability affects OpenSSH versions 8.7p1 and 8.8p1 shipped with Red Hat Enterprise Linux 9. Security researcher Alexander Peslyak, also known as Solar Designer, discovered and reported the bug while reviewing CVE-2024-6387.
Although the immediate impact of CVE-2024-6409 is lower since the race condition and RCE potential are triggered in the privsep child process. An active exploit for CVE-2024-6387 has already been detected in the wild, targeting servers primarily located in China. Users and system administrators are advised to review their OpenSSH installations and apply the necessary patches or updates to mitigate the risk.
Impacted Versions and Specifics
The vulnerability affects OpenSSH versions 8.7 and 8.8, including their portable releases. A major concern stems from specific downstream patches, like Red Hat’s OpenSSH-7.6p1-audit.patch, which introduces additional code to cleanup_exit() and worsens the vulnerability. Unlike CVE-2024-6387, this race condition occurs within the privsep child process, which runs with reduced privileges. While this slightly mitigates the immediate impact, it still presents a significant threat.
Implications of the Vulnerability (CVE-2024-6409)
Despite the reduced privileges of the privsep child process, the risk of remote code execution (RCE) remains severe. Immediate patching of affected systems is crucial, with various distributions like Rocky Linux already releasing patches. Additionally, implementing security measures such as setting LoginGraceTime to 0 can help prevent exploitation. Enhancing monitoring for unusual activity, particularly related to authentication attempts and signal handling within the SSH is also essential.
Below infographic shows how a generic Remote code execution looks like, However, RCE attack flow could be changed according to the target vector.
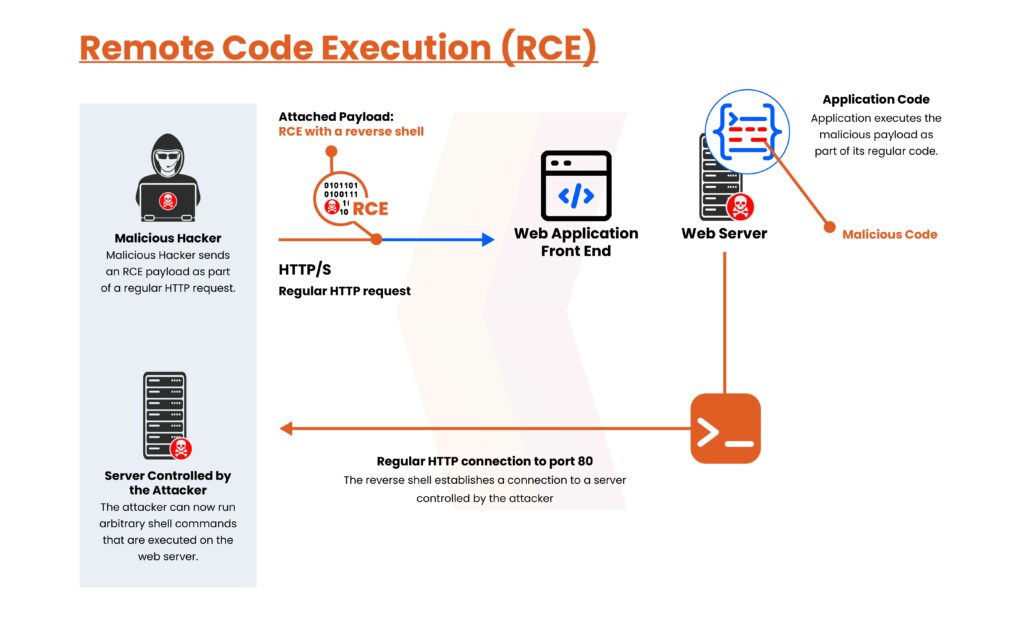
Immediate Steps to Mitigate Risk
Addressing the vulnerability in OpenSSH, which allows remote code execution on Linux systems, requires a targeted and multi-layered security approach. Here are some concise steps and strategic recommendations for enterprises to protect against this critical threat:
Patch Management
Addressing the vulnerability in OpenSSH, which allows remote code execution on Linux systems, requires a targeted and multi-layered security approach. Here are some concise steps and strategic recommendations for enterprises to protect against this critical threat:
Enhance Access Control
Restrict SSH access using network-based controls to reduce attack risks.
Network Segmentation and Intrusion Detection
Segment networks to limit unauthorized access and lateral movement within critical environments. Implement monitoring systems to detect and alert on unusual activities that may indicate exploitation attempts.
Examples of Known RCE Vulnerabilities
- CVE-2021-44228 (Log4Shell) in Apache Log4j 2.x, along with follow-up vulnerabilities CVE-2021-45046 and CVE-2021-45105 (a denial of service vulnerability), exemplifies an RCE in a non-web application. This vulnerability in Log4j, specifically in the JndiLookup class, does not require attacker authentication and affects multiple Log4j versions. Many popular applications and services, including Steam, Apple iCloud, and Minecraft, were initially found to be vulnerable.
- CVE-2021-1844 in Apple iOS, macOS, watchOS, and Safari is another example of an RCE in an operating system module. If a victim visits an attacker-controlled URL using a vulnerable device, the operating system will execute a malicious payload on that device.
- CVE-2020-17051 in Microsoft Windows NFSv3 demonstrates an RCE within an operating system module. Exploiting this vulnerability involves an attacker connecting to a susceptible NFS server and transmitting a payload for execution on the targeted endpoint.
- CVE-2019-8942 in WordPress 5.0.0 illustrates an RCE within a widely used web application. Exploiting this vulnerability allows an attacker to execute arbitrary code in WordPress by uploading an image file specially crafted to contain PHP code in its Exif metadata.
How to Prevent RCE Attacks?
To effectively prevent RCE vulnerabilities in web applications, it is essential to avoid using language functions and constructs that are vulnerable to RCE when handling untrusted data. For instance, functions like eval in PHP/JavaScript should be used cautiously or avoided altogether with user input.
If the eval function must be used with untrusted data, and there’s no alternative to achieve the application’s functionality, it’s crucial to acknowledge the inherent risk of susceptibility to remote code execution attacks. Despite rigorous input sanitization, attackers may still find avenues to exploit vulnerabilities. While avoiding RCE vulnerabilities entirely may be impossible, robust input/output validation and whitelist-based sanitization can minimize attack risks and impacts.
Kratikal has always recommended continuous monitoring to minimize any risk associated with remote code execution. Contact us for VAPT services to mitigate RCE attacks.
Book a Free Consultation with our Cyber Security Experts

Conclusion
Mitigating the impact of the newly identified OpenSSH vulnerability (CVE-2024-6409) and other RCE vulnerabilities requires a comprehensive and proactive approach. Immediate patching, stringent access controls, network segmentation, and robust input/output validation are crucial to reducing exploitation risk. Although eliminating RCE vulnerabilities entirely may be challenging, adopting a multi-layered security strategy and continuous monitoring can substantially minimize the threat. Kratikal’s continuous monitoring and VAPT services are designed to help organizations effectively address these vulnerabilities and strengthen their cybersecurity posture. Reach out to us for expert assistance in securing your systems against RCE attacks.
As a CERT-In empanelled organization, Kratikal is equipped to enhance your understanding of potential risks. Our manual and automated Vulnerability Assessment and Penetration Testing (VAPT) services proficiently discover, detect, and assess vulnerabilities within your IT infrastructure. Additionally, Kratikal provides comprehensive security auditing services to ensure compliance with various regulations, including ISO/IEC 27001, GDPR, PCI DSS, and more, assisting your business in adhering to legal requirements set forth by diverse governments.
Ref: https://thehackernews.com/2024/07/new-openssh-vulnerability-discovered.html
FAQs
- Is OpenSSH a vulnerability?
A critical vulnerability affecting millions of OpenSSH servers allows remote code execution, bypassing authentication safeguards. Discovered by the security research team at Qualys, the bug, known as regreSSHion (CVE-2024-6387), predominantly impacts Glibc-based Linux systems.
- What is OpenSSH used for?
OpenSSH is a free SSH protocol suite that encrypts network services, such as remote login and file transfers. Its source code is freely accessible on the internet, promoting code reuse and auditing.
The post Critical Vulnerability Discovered in OpenSSH Impacting Large User appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/critical-vulnerability-discovered-in-openssh-impacting-large-user/
如有侵权请联系:admin#unsafe.sh