2024-7-16 17:32:10 Author: isc.sans.edu(查看原文) 阅读量:6 收藏
Few weeks ago, I was asked by a customer to take a look at a phishing message which contained a link that one of their employees clicked on. The concern was whether the linked-to site was only a generic credential stealing web page or something targeted/potentially more dangerous. Luckily, it was only a run-of-the-mill phishing kit login page, nevertheless, the e-mail message itself turned out to be somewhat more interesting, since although it didn’t look like anything special, it did make it to the recipient’s inbox, instead of the e-mail quarantine where it should have ended up.
The reason for this probably was that the message in question contained what looked like a reply to a previous e-mail exchange. This might have made it appear more trustworthy to the spam/phishing detection mechanisms that were employed to scan it, since – as far as my understanding goes – automated spam/phishing detection mechanisms tend to consider messages with reply-chains to be somewhat more trustworthy than plain, unsolicited e-mails from unknown senders.
It should be mentioned that threat actors commonly use replies to legitimate messages in account takeover/BEC-style phishing attacks, however, in this case, the situation was somewhat different – the original (replied-to) message was from someone not associated with the targeted organization in any way. Use of this approach (i.e., “replying” to a message with no relevance to the recipient) can sometimes be seen in generic phishing, however, if someone receives an e-mail which contains a reply to a message from someone they have never even heard of, it doesn’t exactly make the message appear trustworthy… Which is where the slight twist, which was used in this message, comes in.
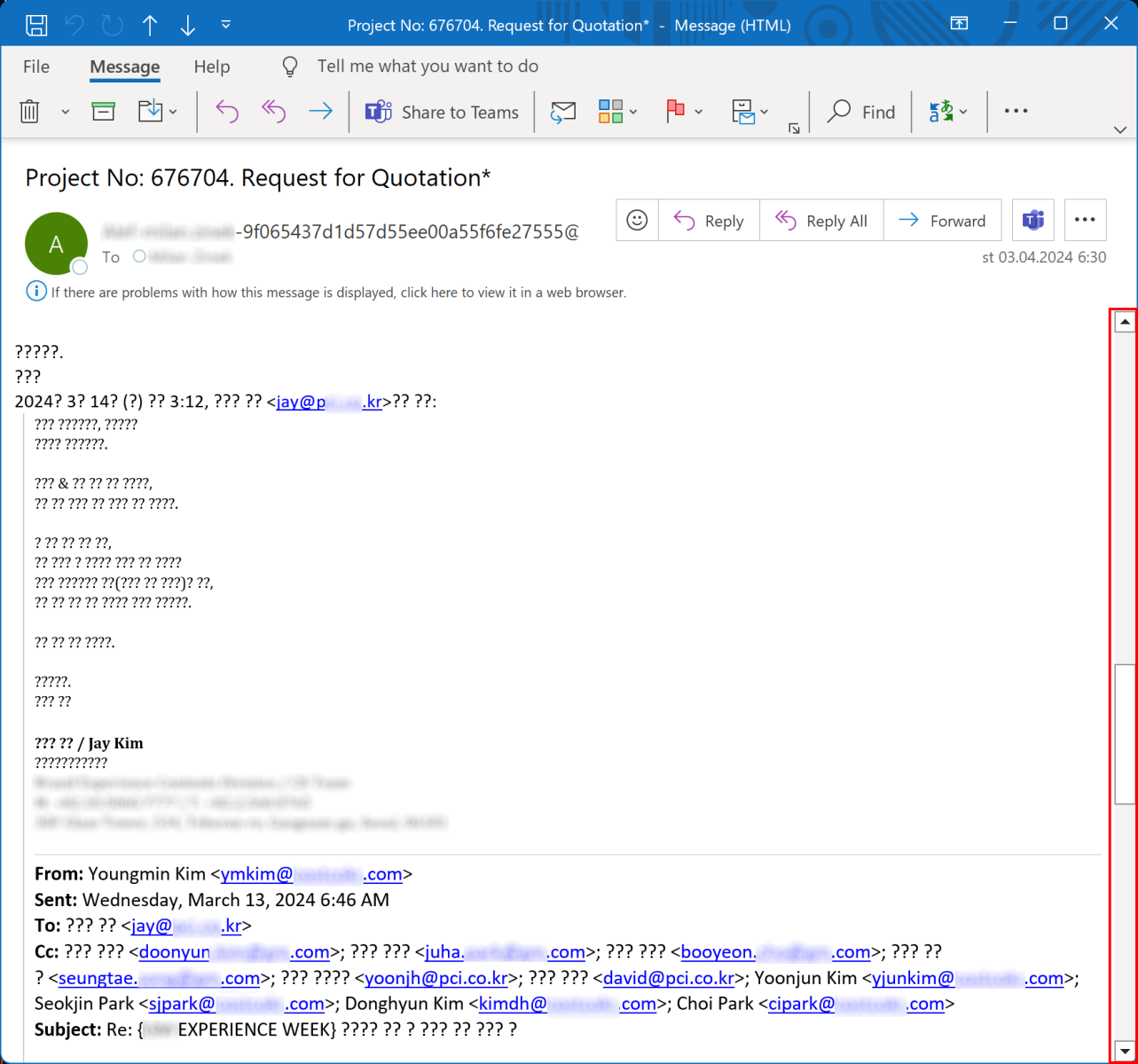
In the message, the ”reply” part was hidden from the recipient bellow a long list of empty paragraphs (well, paragraphs containing a non-breaking space). And although this technique is not new, since the aforementioned customer’s IT specialists weren’t aware of it, and a quick Google search failed to provide any write-ups of it, I thought it might be worthwhile to go over it here.
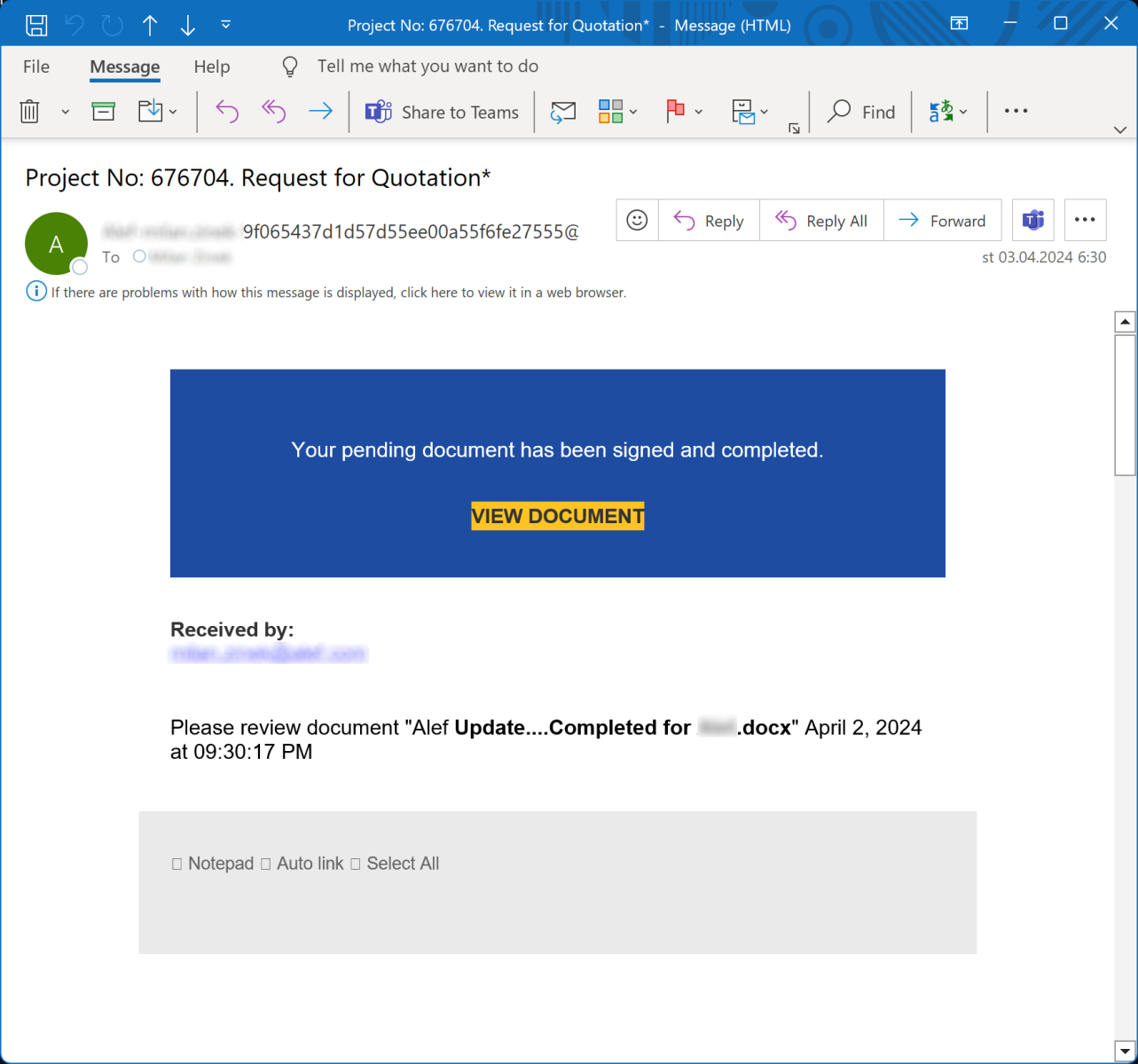
As the following example from my “phishing collection” shows, at first glance, an e-mail messages, in which this technique is used, would look quite normal, and a recipient might not notice anything suspicious (besides the overall “this is an obvious phishing” vibe).
Only if one noticed that the scrollbar on the right side of the window seems to indicate that there is (literally) much more to the message than it appears to be, would one probably discover the text of the original reply-chain... Which, in this instance, is hidden bellow 119 empty paragraphs.
Although the aforementioned technique is hardly the most common (or most dangerous) one when it comes to phishing, since it is being used “in the wild”, a short mention of it might make a good addition to any security awareness training (e.g., something along the lines of “if you see a large scrollbar next to the body of a short e-mail, it is a definite indicator that something is amiss”)…
-----------
Jan Kopriva
@jk0pr | LinkedIn
Nettles Consulting
如有侵权请联系:admin#unsafe.sh