2024-7-17 00:0:0 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
“Consumers and businesses alike expect that cars and other products they purchase from reputable providers will not carry risk of harm. The same should be true of technology products … Cyber-intrusions are a symptom rather than a cause of the continued vulnerability of U.S. technology.”
~ CISA Director Jen Easterly in a Foreign Affairs article in 2023
In most industries, we as consumers can generally trust the products that we purchase are safe and tested. Third-parties such as Underwriters Laboratories (UL) inspect, test, and certify everything from batteries to beauty products. The National Highway Traffic Safety Administration (NHTSA) publishes crash test ratings for passenger vehicles.
But when it comes to IT products such as PCs, servers, network hardware, software products, we are unsurprised when security vulnerabilities are routinely discovered. These defects put organizations at risk, especially with the ransomware epidemic continuing to grow.
Why is it that companies spend so many resources patching and mitigating the risk of vulnerabilities—yet it seems like the bad guys are still able to breach defenses? The incentives for developing and shipping complex technology often outweigh the safety concerns. What is needed are strong economic incentives where consumers expect that IT products are developed and shipped with adequate security measures in place and make purchasing decisions based on the evidence of these measures. That’s the basis for CISA’s Secure by Design initiative.
Government efforts to increase IT product security
U.S. politicians and regulators such as the Securities and Exchange Commission are stepping up cybersecurity requirements for companies, but are not currently interested in cybersecurity requirements for manufacturers of IT products. Apart from U.S. Food and Drug Administration requirements for medical device manufacturers, the U.S. government is largely content with working in the background to improve digital supply chain security and creating awareness. Of note are publications such as NIST 800-161 (Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations) and the forthcoming NIST Cyber Security Framework 2.0. The U.S. Office of Management and Budget (OMB) also requires vendors selling to federal agencies to attest that they are following NIST Secure Software Development Framework (SSDF) practices. CISA also asks manufacturers to voluntarily eliminate specific classes of vulnerabilities, such as OS command injection in network devices, and to sign the Secure by Design Pledge.
On the consumer front, the Federal Communications Commission (FCC) plans to roll out a new U.S. Cyber Trust Mark label for consumer IoT devices later this year. According to FCC Chairwoman Jessica Rosenworcel, “Just like the ‘Energy Star’ logo helps consumers know what devices are energy efficient, the Cyber Trust Mark will help consumers make more informed purchasing decisions about device privacy and security.”

Gartner’s digital supply chain security guidance
In October 2023, Gartner published a helpful report, Mitigate Enterprise Software Supply Chain Security Risks, that advises organizations to follow the example of U.S. government agencies in asking for SSDF attestation. Software defects are a supply chain problem, according to Dale Gardner, author of the report. “Despite a dramatic rise in software supply chain attacks, security assessments are not performed as a part of vendor risk management or procurement activities. This leaves organizations vulnerable to attacks,” he writes.
The report advises security leaders to partner with legal counsel, procurement, and line of business managers to perform security assessments of IT products. This goes beyond the analysis performed by traditional third-party risk management tools, which provide overall vendor risk metrics but do not provide information about the security of the actual products being sold. Organizations should make use of third-party audits and certifications, such as SOC and ISO 27001.
Market forces can improve IT product security
In 1959, Volvo was granted a patent for the three-point seat belt but then made it available to competitors for free, helping to save hundreds of thousands of lives. Volvo became known as a manufacturer that prioritized safety—a key marketing point. Imagine in the future technology and infrastructure providers differentiating themselves based on the security of their products. For this to truly take hold, customers should be able to differentiate products they use in their infrastructure based on their safety and risk.

We as an industry can change the incentives where IT product security is a competitive advantage. Security, IT, and procurement teams can work together to not only ask their vendors for SBOMs and attestations, but also evaluate IT products based on their safety.
The industry needs independent third-party testing of external technology products for organizations to make informed purchase decisions, similar to how NHTSA crash test ratings influence passenger vehicle buying behaviors.
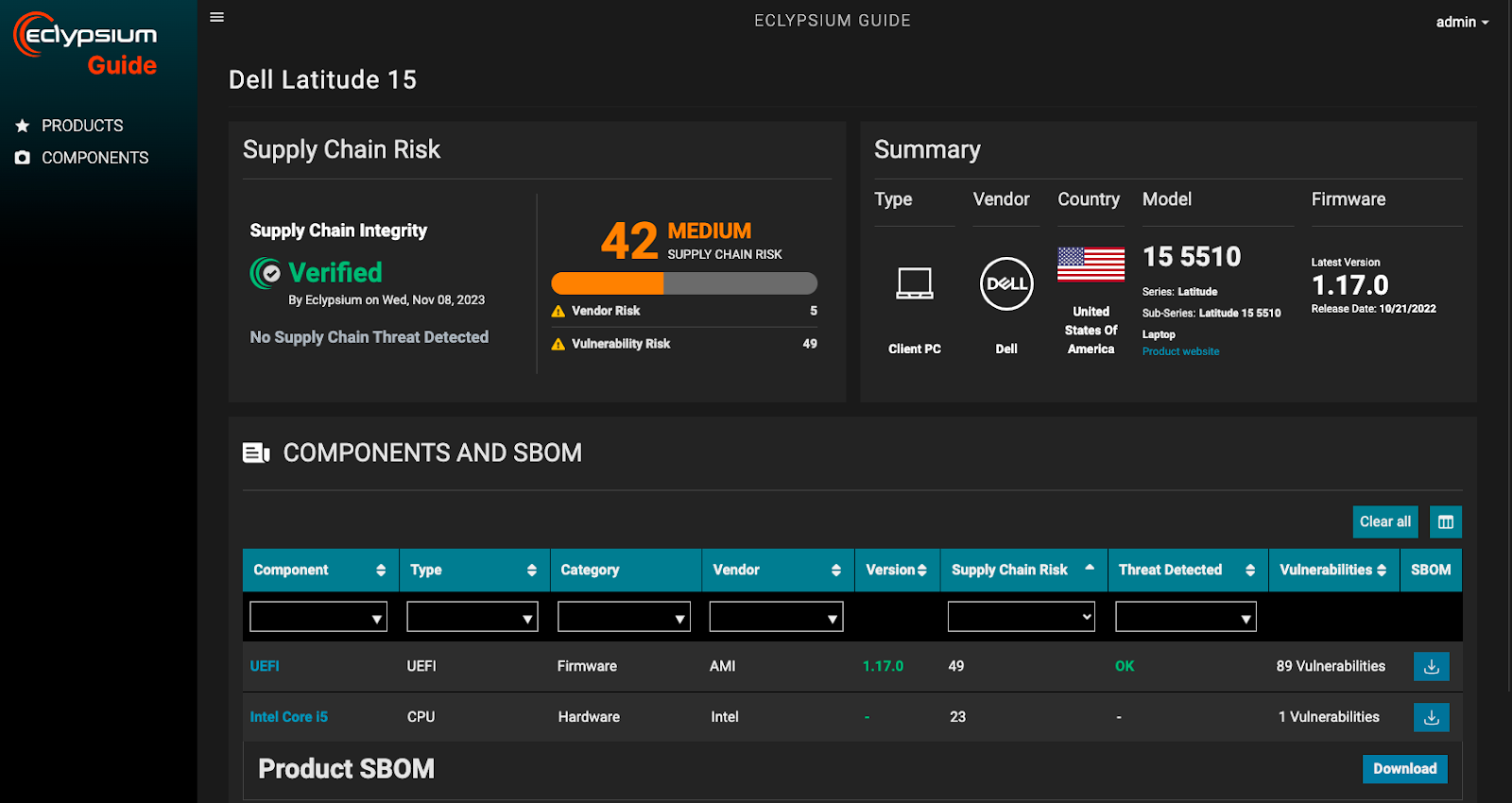
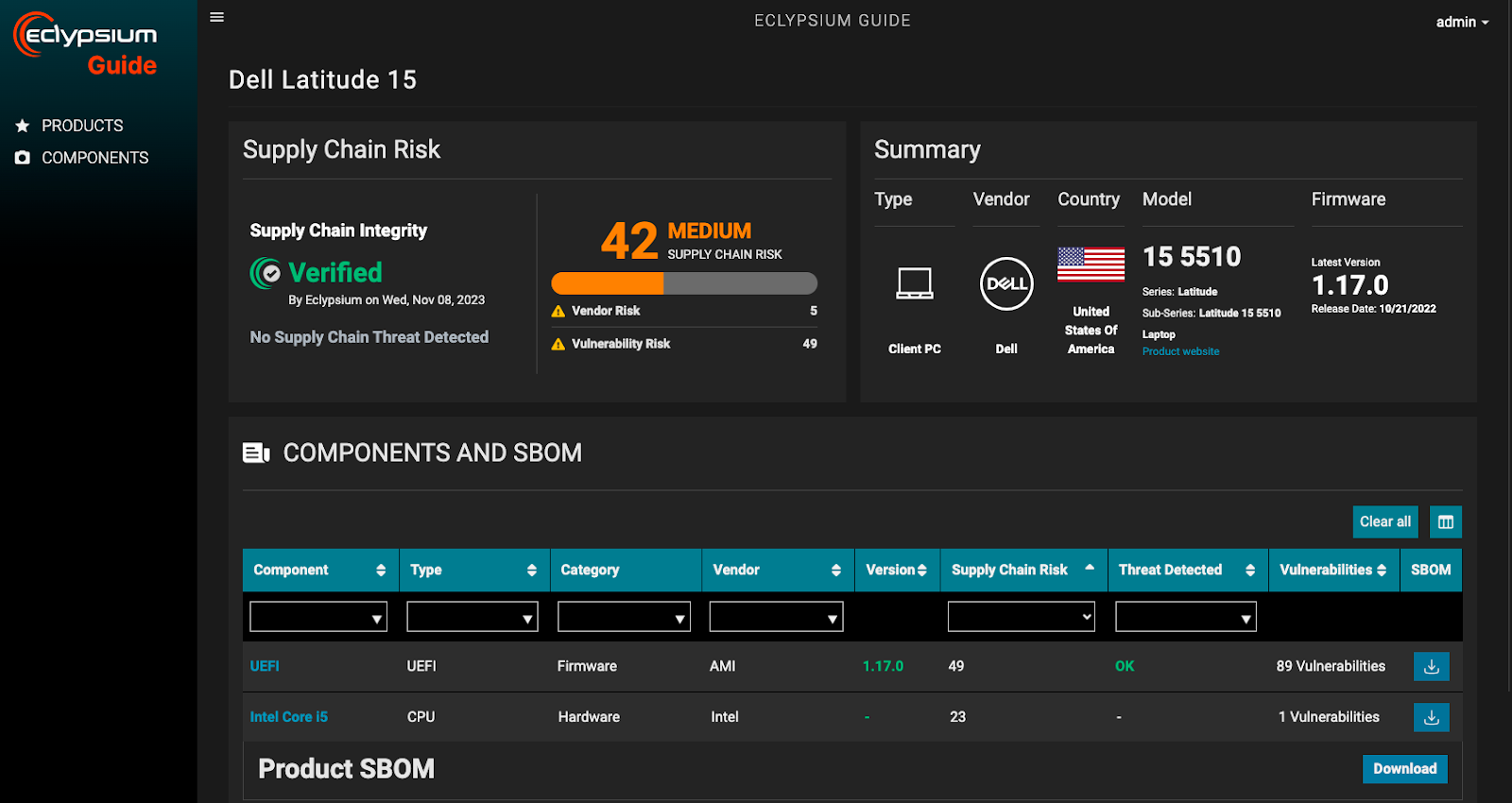
Supply chain intelligence provides transparency into IT product risk
We launched the Eclypsium Guide to Supply Chain Security to provide the transparency needed for IT buyers to make risk-informed decisions. With supply chain intelligence from the Eclypsium Guide, IT security and GRC teams can give their procurement counterparts criteria to start factoring IT product safety into their evaluation calculus. In addition to features, performance, and cost, procurement teams will be able to compare the relative IT product safety of product models. In a similar way, vendor risk management evaluations will be able to look at the actual safety of the products that are in question, which is arguably equally or more important than a vendor “scorecard” that looks at external security posture.
Software defects are a supply chain security issue. IT doesn’t have a vulnerability management problem, it has a supply chain security problem. Eclypsium is dedicated to working with the entire IT infrastructure ecosystem to harden the supply chain with both supply chain intelligence and supply chain security monitoring in production.
Take a tour of the Eclypsium Guide.
The post It Shouldn’t Take an Act of Congress to Make IT Products Secure appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise.
*** This is a Security Bloggers Network syndicated blog from Eclypsium | Supply Chain Security for the Modern Enterprise authored by Chris Garland. Read the original post at: https://eclypsium.com/blog/it-shouldnt-take-an-act-of-congress-to-make-it-products-secure/
如有侵权请联系:admin#unsafe.sh