2024-7-23 16:12:31 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
Rezonate has extended the reach of its platform for managing access to infrastructure to include the credentials that are used by humans alongside the identities of machines and software components that organizations need to track to ensure zero-trust security.
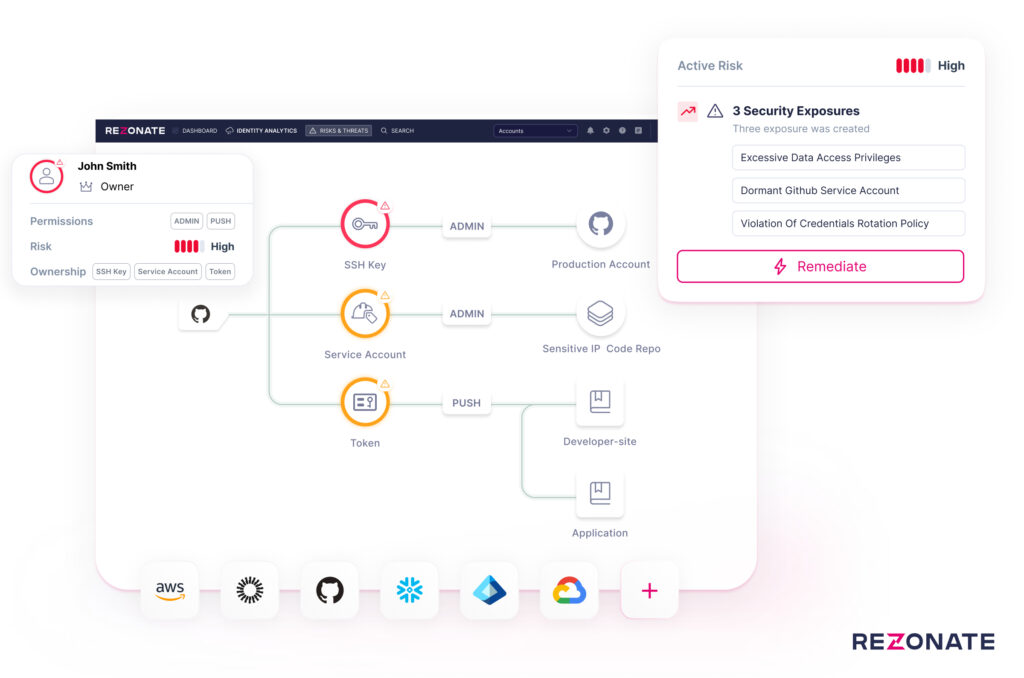
Company CEO Roy Akerman said a unified approach to managing human and non-human identities such as keys to access application programming interfaces (APIs) or tokens will make it simpler for organizations to achieve that goal at a lower total cost.
The Rezonate platform is already being used to manage non-human identities that cybercriminals have been targeting to gain illicit access to, for example, cloud infrastructure. At the same time, however, cybercriminals have been stealing credentials to gain access to IT resources by impersonating, for example, a trusted member of an IT staff.
Rather than trying to mitigate those attack vectors using separate platforms, Rezonate now makes it possible to centrally address both types of threats in a way that visualizes the entire attack path, including their authorization and authentication graphs, security controls, access conditions and behavioral profiles.
That’s critical because the number of inter-dependencies that exist between different types of identities makes it challenging to determine how attacks that are increasing in sophistication are being executed, said Akerman. Organizations need to understand how these inter-dependencies might be exploited on an end-to-end basis to compromise an IT environment if they hope to more proactively defend themselves, he added.
Additionally, cybersecurity and IT operations teams can in real-time surface permissions, entitlements and the services being accessed to combat a threat as it is evolving, or to simply streamline an audit.
Begin With Identity Management
It’s not clear how far down the path toward implementing zero-trust IT policies but it’s clear that journey starts with identity management. The challenge is organizations don’t always realize that for every single human identity, there are orders of magnitude more machine and software identities that need to be correlated and secured.
Ultimately, zero-trust IT will spur greater convergence across security and IT operations workflows because it’s generally the latter that grants access to both humans and machines. The challenge has been the lack of visibility cybersecurity teams have into these workflows, which is especially critical any time there is a breach. Cybersecurity teams at the very least should be creating a list of all the types of identities there are and the privileges that have been granted to them.
In the meantime, cybersecurity teams should assume that until proven otherwise every identity being used to access IT resources is suspicious. Even after an identity is verified, however, no one should take for granted that identity will not be compromised later. Cybercriminals, as of late, are more patient than ever. They are likely to “live off the land” for extended periods after they gain access to an IT environment before initiating any malicious action as part of their efforts to evade detection. The challenge and the opportunity now is to identify any anomalous behavior as soon as it starts to occur.
Recent Articles By Author
如有侵权请联系:admin#unsafe.sh
