2024-7-23 23:0:58 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
As the digital world continues to evolve, so do the methods used by malicious actors to exploit vulnerabilities in software systems. To stay ahead of such threats and comply with regulatory requirements, it is essential to provide security and developer teams with a Software Composition Analysis (SCA) solution that offers automatic vulnerability detection and remediation.
Launched at the beginning of the year, GitGuardian SCA is the latest addition to the GitGuardian code security platform. We are constantly updating its capabilities and performance to match the latest threats and the needs of our users.
Explore how GitGuardian's Software Composition Analysis has evolved since the beginning of 2024 to protect your software supply chain against the most recent attack vectors.
Why SCA has never been so relevant
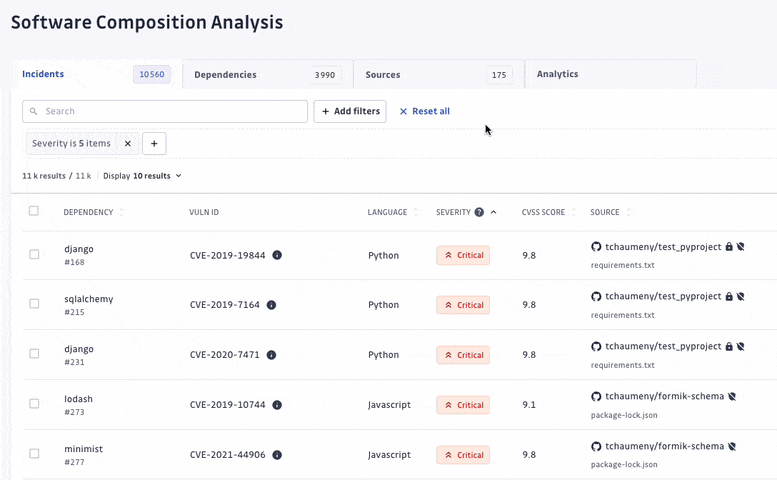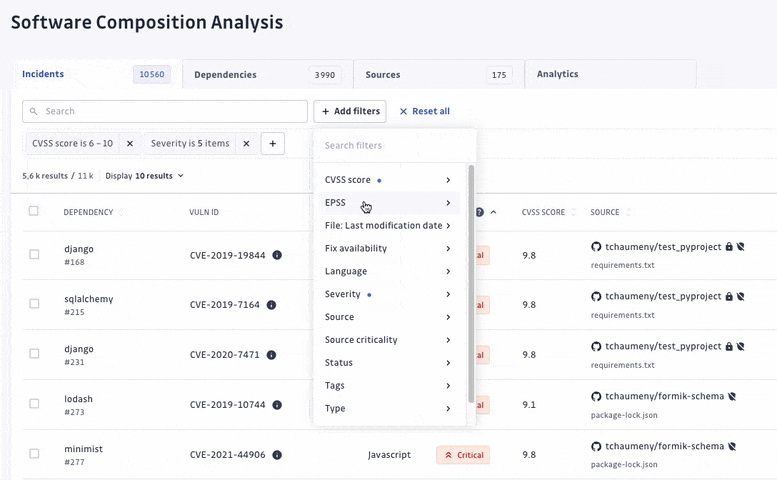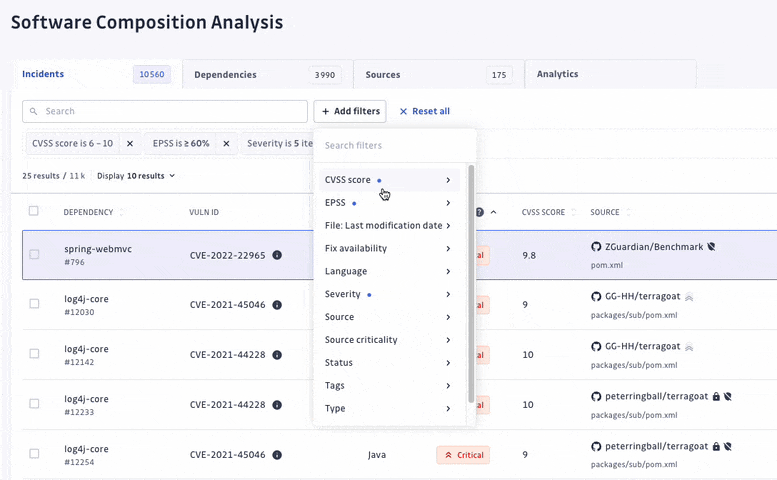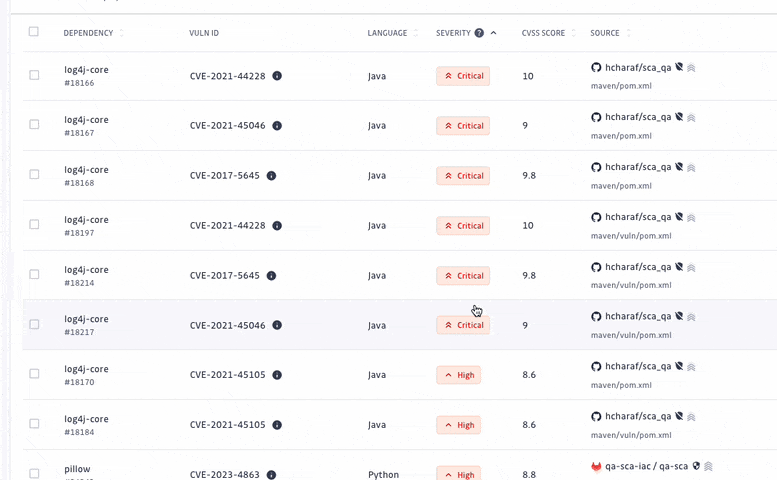
By analyzing software components and dependencies, GitGuardian SCA helps organizations identify and mitigate risks posed by open-source and third-party components. SCA enables security engineers to swiftly identify all applications with unsafe dependencies, consider the context to automatically prioritize incidents by severity, and prompt developers to fix them.
Capitalizing on some of GitGuardian's platform's strengths, GitGuardian SCA is specifically designed for use in fast-paced DevSecOps environments, leveraging cross-team collaboration, incident visibility, and business context.
Beyond software vulnerabilities, the security of your solution is at risk from open-source licenses that could lead to unintended consequences for your code base and organization.
SCA minimizes the threats to your intellectual property by identifying licenses in both your direct and transitive dependencies.
In light of the latest legal regulations on software, such as the directives of US Executive Order 14028 and the EU Cyber Resilience Act, software vendors are required to be more transparent about the risks in their software solutions. GitGuardian SCA allows you to assess and communicate such risks by building a comprehensive Software Bill of Materials (SBOM) of your application's open-source and third-party components, along with their nested dependencies.
Developers frequently use pre-existing code components developed and validated by the open-source community when building projects. This helps save time and resources, but it also means that, on average, 80% of their code base is borrowed from others. That's why it's crucial to automatically scan and detect vulnerabilities in open-source components and third-party libraries.
We have recently expanded the list of supported development ecosystems by adding the .NET framework and NuGet, the official package registry maintained by Microsoft, which is widely used in the .NET community. GitGuardian SCA now covers all the most used programming languages and their associated dependency managers.
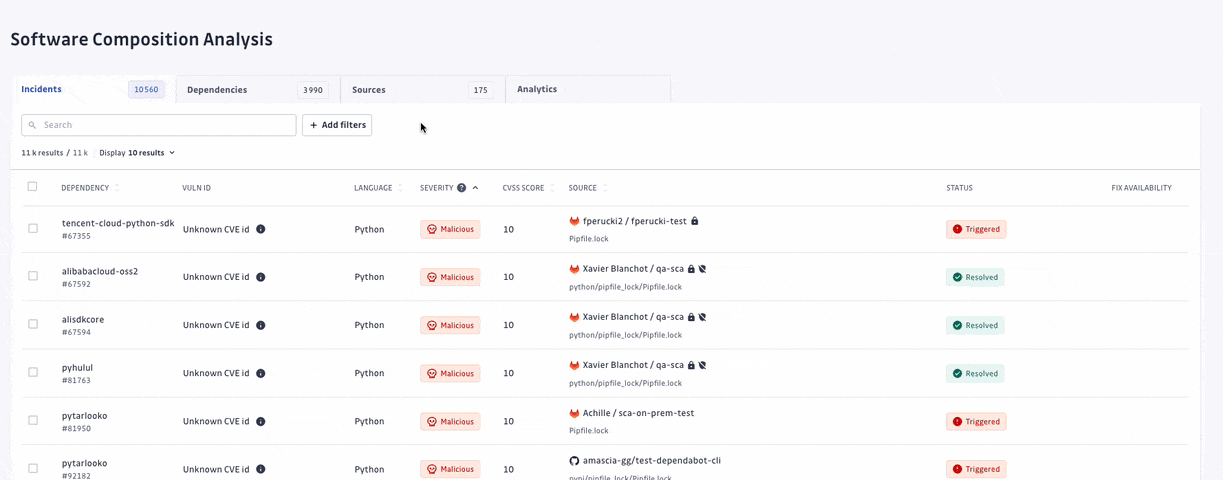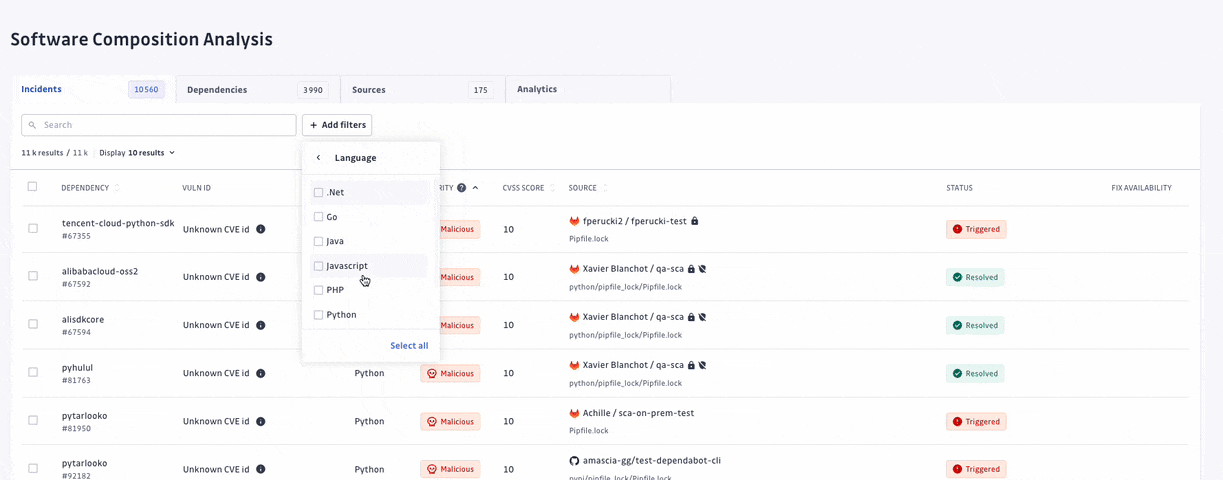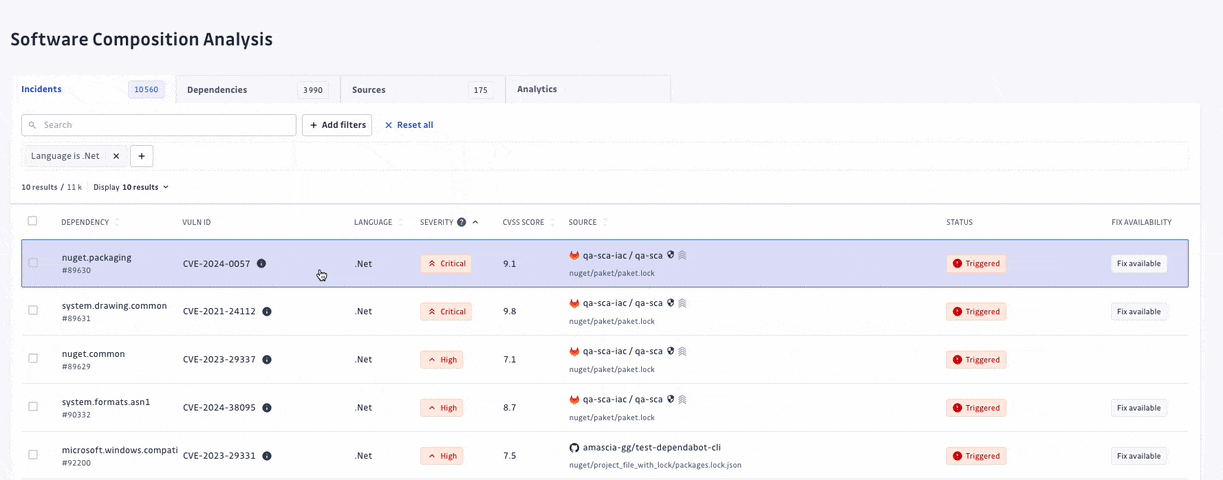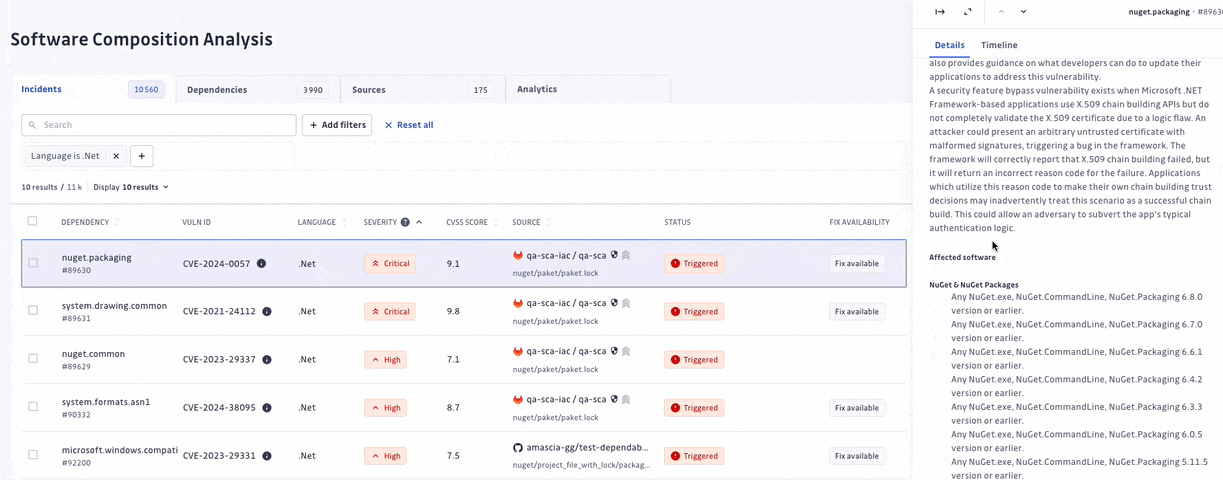
At GitGuardian, we believe that detection without remediation is just noise. Therefore, we have upgraded our prioritization system, allowing security teams to focus their efforts on prioritizing and addressing the most critical vulnerabilities amidst a sea of elements to triage.
We have turned off the scan of archived repositories by default to limit raised incidents to actual threats only. Moreover, we have introduced additional dimensions to let every organization customize what a critical incident means to them. For each incident, we added its EPSS score on top of its CVSS, provided its source criticality (to assess and assign a level of importance to your monitored sources, shared with our Secrets Detection platform), and finally added source activity metrics.
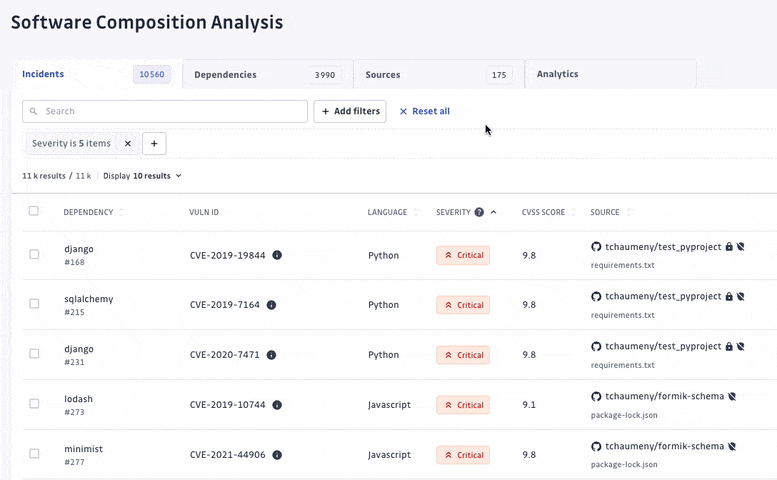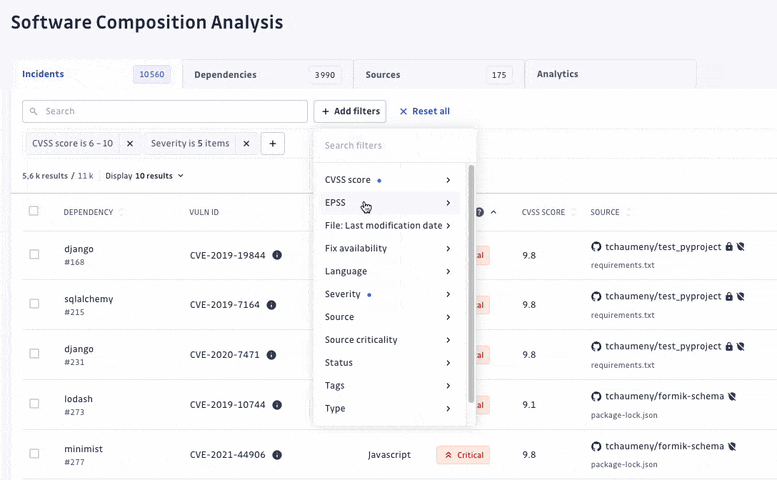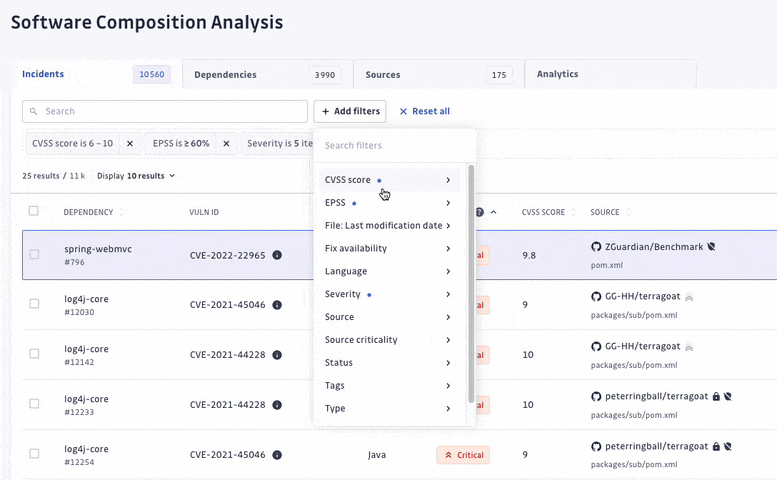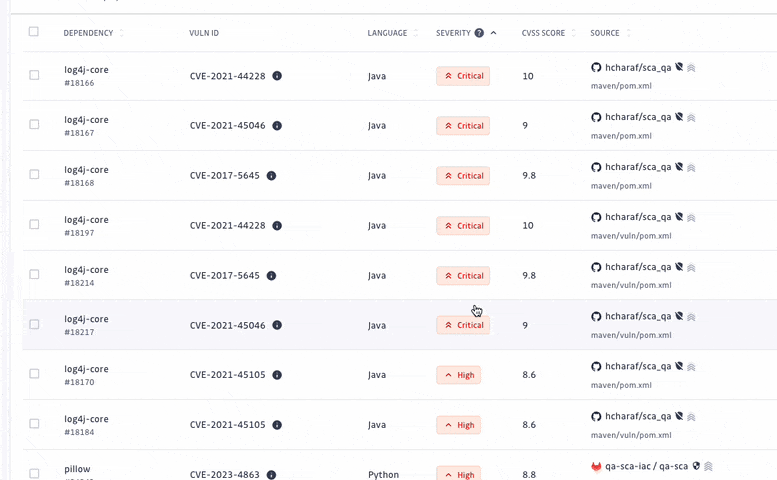
With detection and remediation as the cornerstones of its approach, GitGuardian SCA allows teams to find and fix vulnerabilities following a clear prioritization and investigation process.
Fighting against new attack vectors
Every part of the software supply chain, from external dependencies to internal processes, is a potential entry point for threats.
Recent research indicates a significant surge in attacks targeting code, tools, open-source components, and development workflows in areas where organizations lack visibility and protection. These attacks are becoming more sophisticated, necessitating specific preventive measures to safeguard your infrastructure.
One of the recent attack vectors that has emerged is dependency confusion. It occurs when a software project relies on both private and public package repositories. Attackers may register public packages with names identical to those of privately owned software dependencies. By taking advantage of the package managers' resolution algorithm, they aim to trick systems into unintentionally downloading the malicious public package instead of the secure, privately owned one.
GitGuardian SCA identifies vulnerable packages prone to dependency confusion attacks and provides guidance on preventing such attacks.
Over recent years, typosquatting has become a widespread practice, mainly because attackers could easily get started with it, there were few effective countermeasures to prevent it, and it has a large blast radius, as it targets popular package registries such as PyPI or npm. Typosquatting is one form of malicious package attacks.
Malicious package attacks are broader. Attackers create harmful packages to steal secrets or data, escalate privileges, or install backdoors. They expect developers to use these packages through different ruses, such as typosquatting or compromising legitimate accounts.
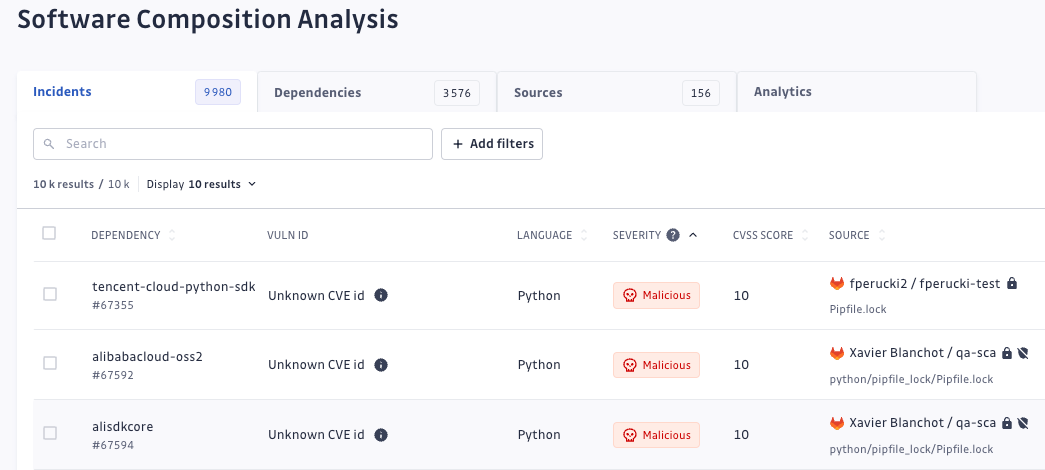
GitGuardian SCA identifies and prioritizes these attacks to allow users to remedy them effectively. While these incidents occur infrequently, they are designed to be highly harmful and are most likely already exploited, meaning they have already affected the developer's ecosystem from which we were able to detect that dependency. In such cases, our users should react quickly to mitigate the breach.
SCA everywhere
Matching the capabilities of our Secrets security solutions, GitGuardian can be accessed either through its online dashboard and APIs, through self-hosting for organizations operating in highly regulated industries, or with strict data privacy policies.
With the self-hosted deployment model, our users retain complete control over their data. This allows them to manage data privacy, security, and compliance according to their organization's needs and regulations. Our self-hosted service is designed to scale with business needs. Users can easily customize their infrastructure to accommodate growth, adjusting resources as necessary to meet increasing demands.
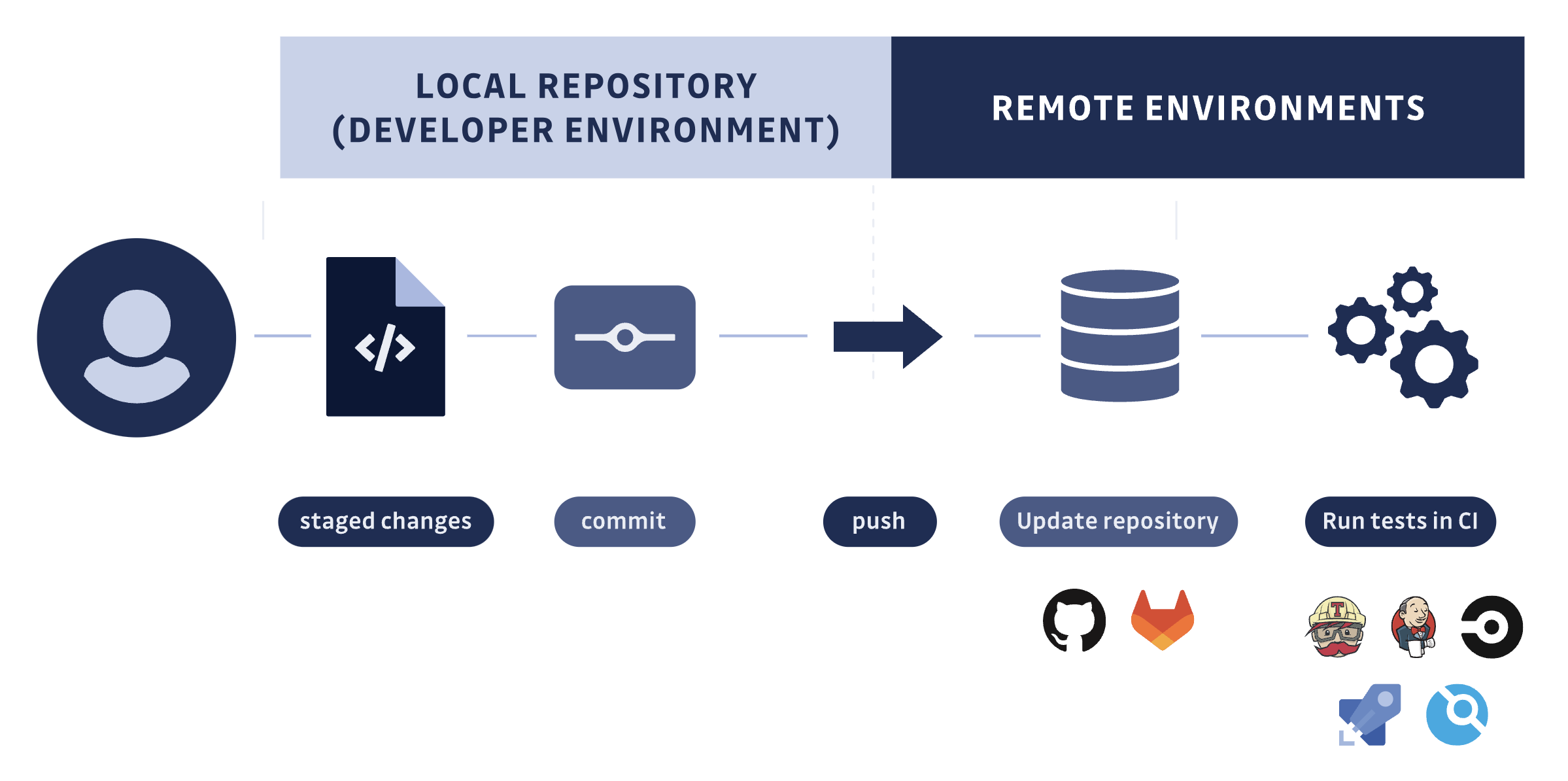
SCA vulnerability detection can be enforced at every step of the Software Development Lifecycle (SDLC) through ggshield, GitGuardian CLI. Safeguarding your repositories with ggshield scans is a proactive step towards securing your software supply chain and applications. It enables you to detect and address vulnerabilities early in your development process, lowering your security exposure in the long run.
Assess your security posture
After successfully defending against advanced attacks in the SDLC and addressing any vulnerabilities in your dependencies, evaluating your security efforts is essential. GitGuardian SCA analytics lets you monitor your attack surface in real-time for new vulnerabilities or vulnerable dependencies. You can track the progress of remediating triggered incidents and identify bottlenecks, such as the most used vulnerable dependencies.
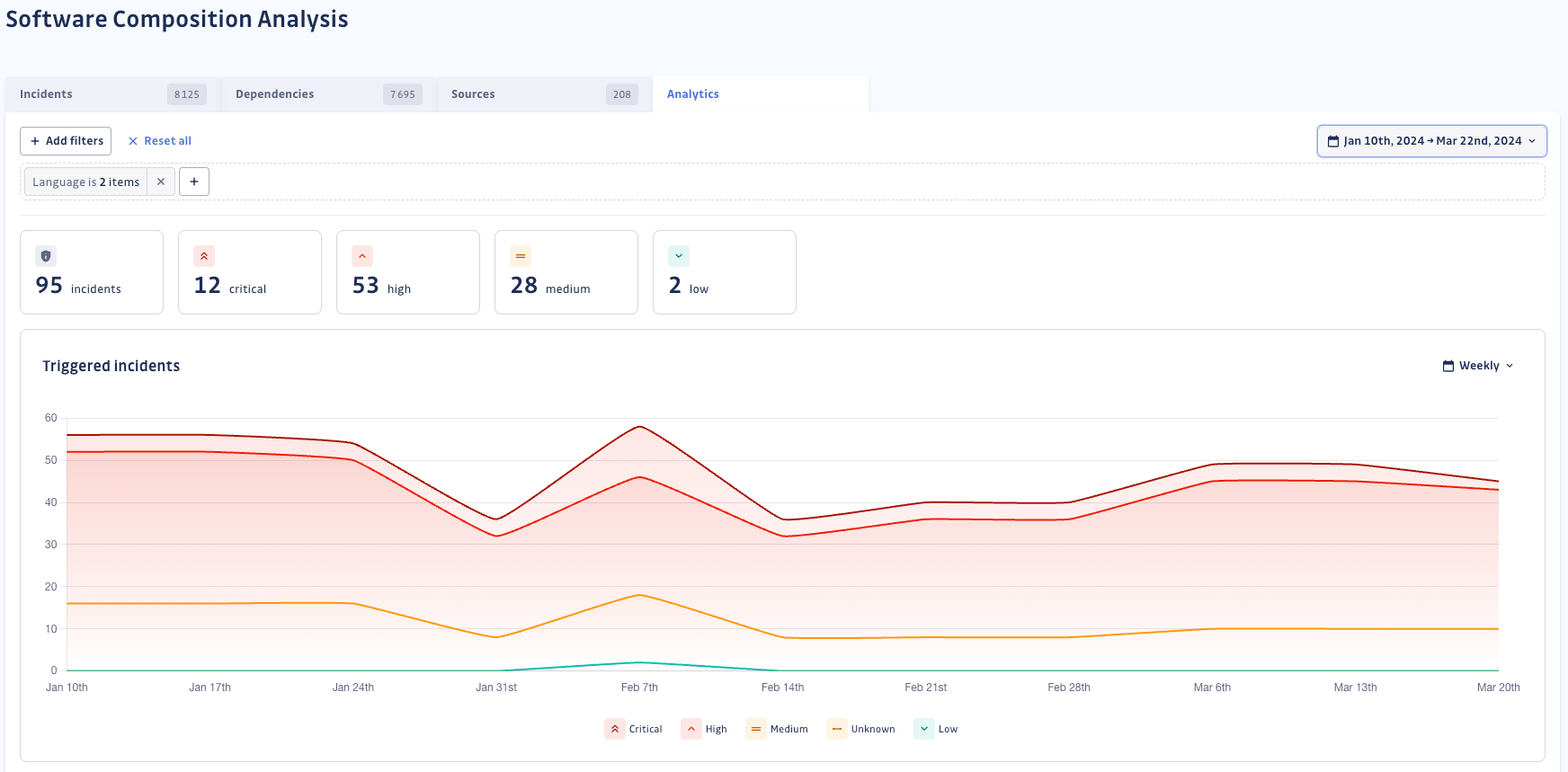
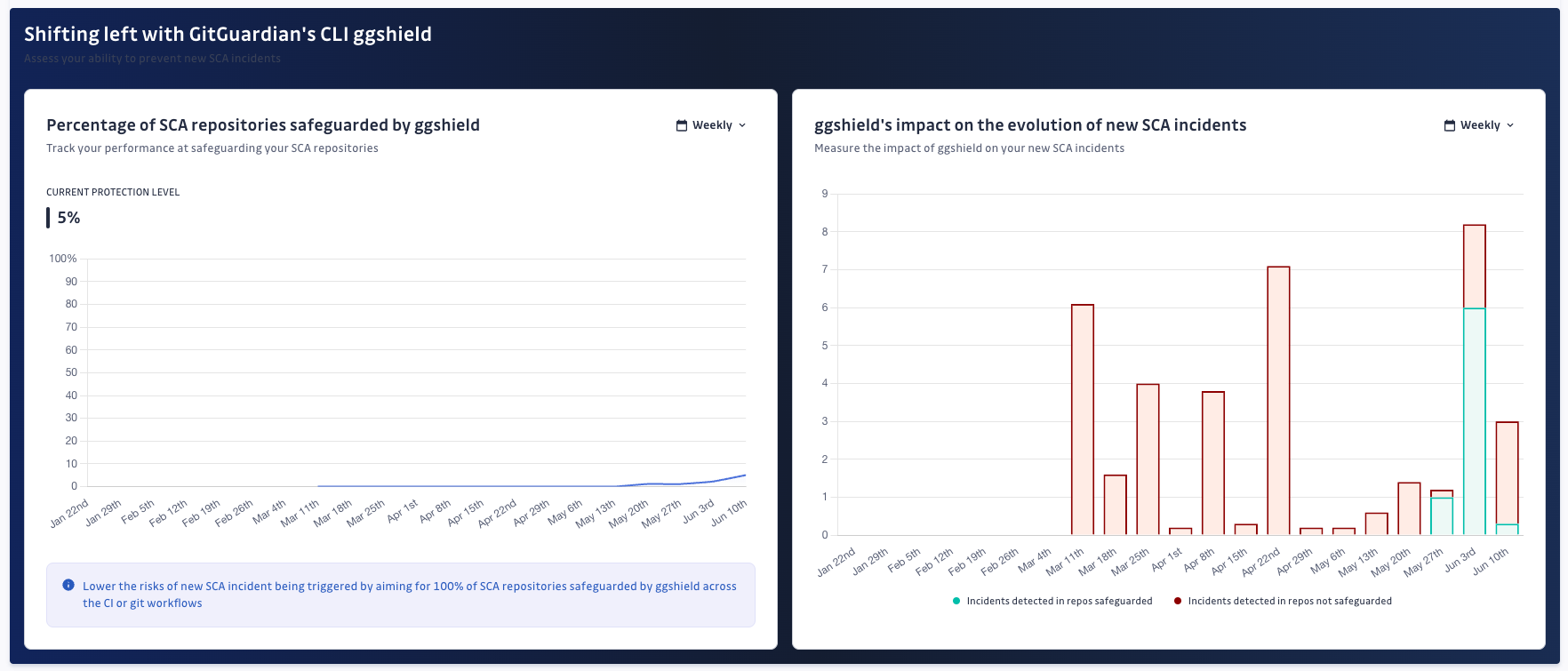
We have recently implemented shift-left analytics related to the advantages of preventing vulnerabilities with ggshield. This allows security teams to evaluate and demonstrate the benefits of adopting the shift-left approach, and their efforts to promote it. By pinpointing any remaining bottlenecks in their CI/CD process, they can make more informed decisions.
Conclusion
Ensuring the security of the software supply chain requires continuous adaptation. The technical teams at GitGuardian are committed to offering SCA users the best protection and experience. We constantly monitor new CVEs and explore the most effective ways to safeguard our users. Keep an eye on our blog for our CVE of the month reviews.
As attackers become increasingly creative with their software supply chain attacks, such as leveraging AI to trick users into downloading malicious packages, we are implementing additional safeguards for our users. Our next focus is on introducing automated fix pull requests to help users remediate issues more quickly. We also aim to explore how reachability can help users better understand the most vulnerable parts of their SDLC.
*** This is a Security Bloggers Network syndicated blog from GitGuardian Blog - Code Security for the DevOps generation authored by Ferdinand Boas. Read the original post at: https://blog.gitguardian.com/sca-defending-users-against-cyber-threats/
如有侵权请联系:admin#unsafe.sh