2024-7-23 21:0:0 Author: securityboulevard.com(查看原文) 阅读量:7 收藏
Automated anti-phishing techniques are revolutionizing how individuals and organizations defend against the ongoing and evolving threat of phishing attacks. Phishing, a type of cybersecurity attack that involves sending emails that appear to be from reputable sources to extract personal information or deploy malicious software, remains a prevalent threat that every organization must address.
It’s important to understand the innovative approaches that are reshaping the landscape of anti-phishing methods and how security automation is the best way to defend your organization against them.
What is Anti-Phishing?
Anti-phishing refers to measures and technologies designed to protect against phishing attacks, like email and mobile phishing, spear phishing and whaling attacks. Anti-phishing involves techniques to detect and respond to unauthorized attempts to access personal data, such as passwords and credit card numbers, aiming to enhance online security and safeguard users and prevent financial fraud.
The Role of Automation in Anti-Phishing
Automated anti-phishing techniques offer a dynamic solution by quickly identifying, analyzing, and neutralizing threats. These systems do this by employing advanced algorithms and machine learning models to learn from new tactics, ensuring continuous, up-to-date protection.
The four core automated anti-phishing techniques include:
1. Email Filtering
Email filtering acts as your frontline defense against phishing attacks. Through automated operations, every incoming email undergoes a thorough analysis to detect any suspicious content. This includes malicious links, problematic attachments, or deceptive text patterns designed to mimic legitimate communication. By immediately identifying and filtering out these potentially harmful messages, security automation prevents them from ever reaching the user’s inbox, significantly reducing the risk of security threats within your organization.
2. URL Analysis
Security automation solutions are designed to meticulously scan URLs in real time, effectively detecting and preventing access to sites identified as phishing attempts or exhibiting suspicious behaviors. Through this rigorous analysis, they can accurately identify abnormal domain names or the use of misleading subdomains, ensuring enhanced protection.
3. Threat Intelligence Sharing:
Implementing security automation allows collaboration across networks, sharing threat intelligence and indicators of compromise (IoCs). This collective defense mechanism enhances the protection of all participants by rapidly disseminating knowledge about emerging phishing schemes. Moreover, the autonomous integration enables each participant to better anticipate and defend against potential cyberattacks, ensuring a more secure and resilient digital environment for everyone involved.
4. Machine Learning Models
These models are trained on large datasets of phishing and legitimate emails to identify subtle patterns and anomalies that indicate phishing attempts. By analyzing these vast collections of email data in real-time, the models learn to distinguish between harmless messages and those crafted with malicious intent, thereby continuously improving their ability to identify potential incidents.
Advantages of Automated Anti-Phishing Solutions
Now that we know how security automation supports anti-phishing techniques, let’s explain the benefits:
- Scalability: Automated systems can handle vast quantities of data, protecting against thousands of phishing attempts in real time.
- Increase efficiency: With hundreds of false positives, human error, and alert fatigue can develop over time. Automation significantly reduces the time needed to identify and neutralize threats, minimizing potential damage.
- Improve incident response: On average, manually triaging an attack takes around 30 minutes. Automation improves phishing mean time to response (MTTR) by rapidly sifting through the noise of false positives.
- Prevent SOC analyst burnout: Analysts within your SecOps can become overwhelmed with alerts. By automating phishing use cases, analysts can save valuable time by only addressing genuine threats.
- Adaptability: Through continuous learning, these systems adapt to new and evolving phishing techniques faster than your human SecOps team. Their ability to constantly update their knowledge base allows them to stay one step ahead, ensuring a higher level of digital security.
- Comprehensive protection: By integrating various tools, use cases, and approaches, automated anti-phishing offers a multi-layered defense strategy.
Anti-Phishing Training Within Your Organization
While security automation and AI are instrumental, human SOC analysts will always remain key to maintaining an organization’s overall cybersecurity posture. To stay prepared for inevitable attacks, organizations can engage their employees in anti-phishing training by:
- Simulating phishing attacks: Organizations can conduct mock phishing attacks to test employees’ awareness and response. This can help identify vulnerabilities faster and improve employees’ ability to recognize phishing attempts.
- Running tailored training programs: Training programs that use industry-specific examples and educate employees anti phishing best practices relevant to their specific work environment can be crucial in preventing attacks.
- Showcasing real-life examples: Using actual phishing cases, such as the scam seen in the 0katapus campaign, to show employees what attempts could look like and how to spot them.
- Mobile phishing awareness: Mandate courses that cover vulnerabilities specific to mobile devices and SMS phishing (smishing), teaching employees to recognize and avoid these types of scams.
- Improving reporting mechanisms: Automated reporting on threats and training employees on how to process the data efficiently, allows for quicker incident response and potential shifts in strategy to prevent future events.
Prevent Phishing by Automating Anti-Phishing with Swimlane Turbine
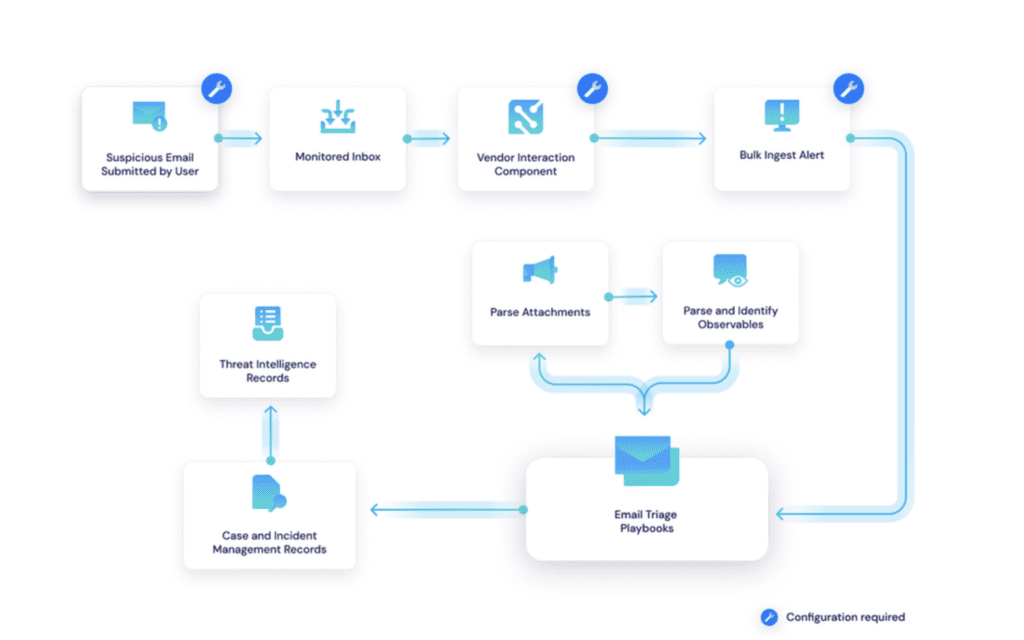
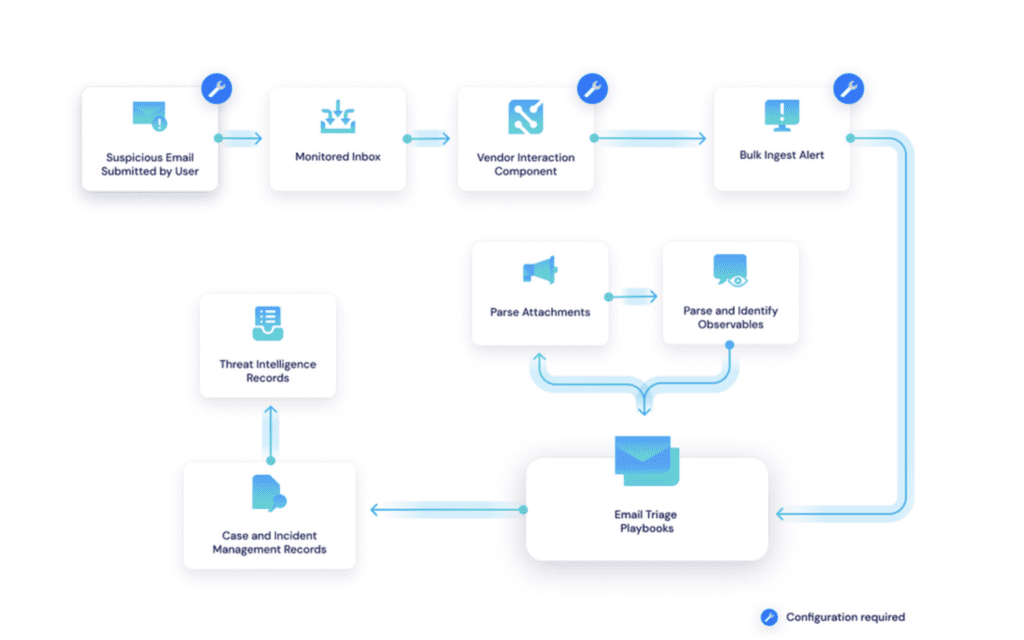
Anti-phishing solutions need to be innovative and adaptable to the evolving digital landscape. Swimlane Turbine saves hours of work when it comes to phishing triage. Our AI-enhanced security automation platform has an out-of-the-box solution for automating anti-phishing techniques. The Swimlane phishing solution works with any email detection platform to ingest, enrich, triage, and report on phishing related cases and incidents. This workflow diagram provides an overview of how the Swimlane Turbine automates anti-phishing techniques. Visit Swimlane Marketplace to learn more or browse email detection connectors.
Request a demo
If you haven’t had the chance to explore Swimlane Turbine yet, request a demo.
如有侵权请联系:admin#unsafe.sh