
In cryptography and cybersecurity, choosing a password hashing algorithm is crucial for protecting user credentials and sensitive data. This article compares four prominent password hashing algorithms: Argon2, bcrypt, scrypt, and PBKDF2. We'll explore their strengths, weaknesses, use cases, and prospects to help inform decisions on which algorithm to use in various scenarios.
Password Hashing Algorithms
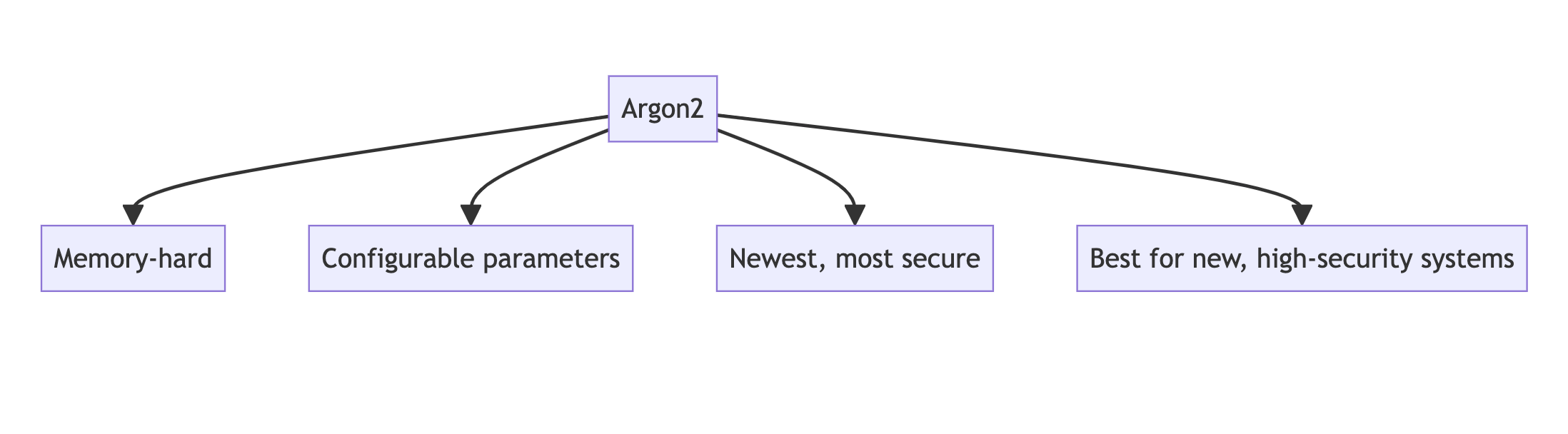
Argon2
Argon2 is the winner of the Password Hashing Competition held between 2013 and 2015. It was designed to be a state-of-the-art memory-hard function, resistant to various types of attacks.
Key Features:
- Memory-hard, making it resistant to GPU and ASIC attacks
- Configurable memory, time, and parallelism parameters
- Three variants: Argon2d, Argon2i, and Argon2id
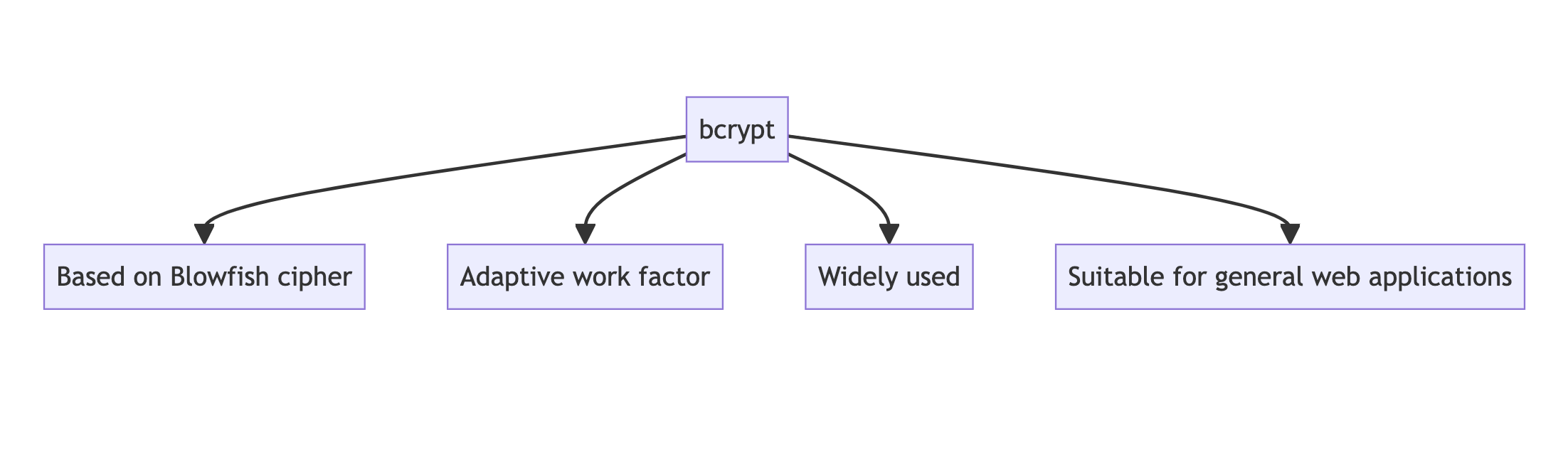
bcrypt
Developed in 1999 by Niels Provos and David Mazières, bcrypt is based on the Blowfish cipher and is widely used for password hashing.
Key Features:
- Adaptive function with a work factor that can be increased over time
- Built-in salt to protect against rainbow table attacks
- Relatively slow, which is beneficial for password-hashing
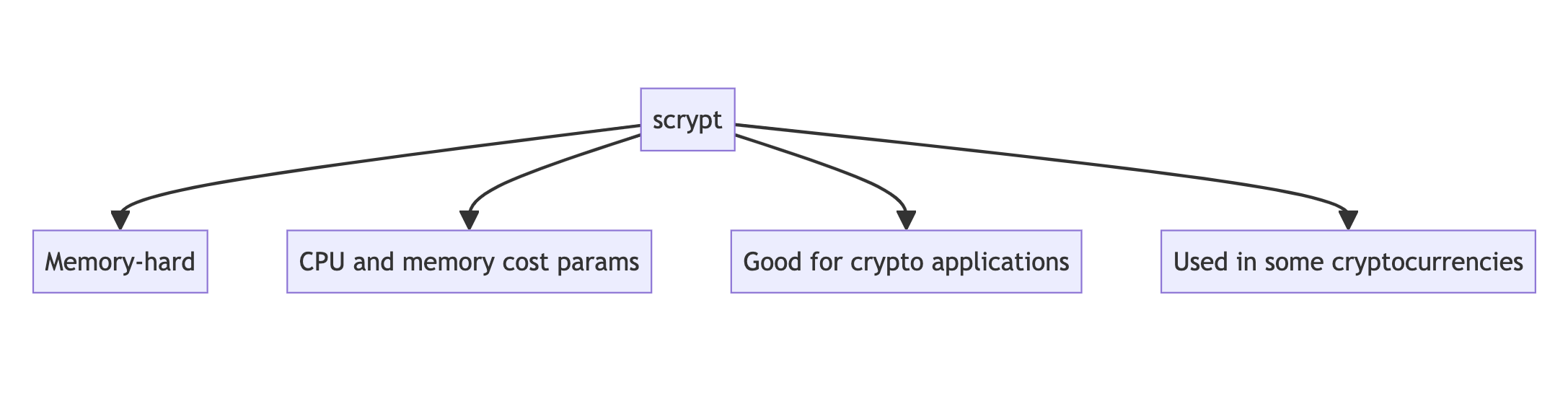
scrypt
Created by Colin Percival in 2009, scrypt was designed to be memory-hard and resistant to large-scale custom hardware attacks.
Key Features:
- Memory-hard, requiring significant amounts of RAM
- Configurable CPU and memory cost parameters
- Designed to be more secure against hardware brute-force attacks than PBKDF2
PBKDF2
Password-Based Key Derivation Function 2 (PBKDF2) is part of RSA Laboratories' Public-Key Cryptography Standards (PKCS) series. It's widely used and considered a standard in many applications.
Key Features:
- Applies a pseudorandom function to the input password along with a salt
- Uses key stretching through iteration count
- It can be used with various underlying cryptographic hash functions (e.g., SHA-256)
Comparative Analysis
Security
- Argon2: Considered the most secure among the four, especially against GPU and ASIC attacks. Its memory hardness and configurability make it highly resistant to various attack vectors.
- bcrypt: Still considered secure, but potentially vulnerable to FPGA attacks. Its fixed memory usage (4KB) is a limitation compared to more modern algorithms.
- scrypt: Very secure due to its memory-hardness, but slightly less so than Argon2. It's particularly strong against hardware-based attacks.
- PBKDF2: The least secure of the four, especially against GPU and ASIC attacks. However, it's still considered safe when used with a high iteration count.
Performance and Resource Usage
- Argon2: Highly configurable, allowing for balanced CPU and memory usage. Can be optimized for different hardware environments.
- bcrypt: Consistent performance across different hardware due to fixed memory usage. Generally slower than PBKDF2 but faster than scrypt.
- scrypt: High memory usage, which can be a limitation in resource-constrained environments. Slower than bcrypt and PBKDF2.
- PBKDF2: Fastest of the four, but this is a drawback for password hashing. Low memory usage makes it vulnerable to parallel attacks.
Flexibility and Implementation
- Argon2: Highly flexible with three variants and configurable parameters. However, being newer, it may have less widespread library support.
- bcrypt: Simple to implement and widely supported in various programming languages and frameworks.
- scrypt: Moderately complex to implement correctly. Has good library support but not as ubiquitous as bcrypt or PBKDF2.
- PBKDF2: Very flexible and widely supported. Can be used with different underlying hash functions.
Use Cases
Argon2
- Best for high-security applications where memory-hardness is crucial
- Ideal for password hashing in new systems with modern hardware
- Recommended for cryptocurrency systems due to its resistance to GPU attacks
bcrypt
- Suitable for general-purpose password hashing in web applications
- Good choice for systems that need a battle-tested, widely supported algorithm
- Appropriate for legacy systems that can't easily migrate to newer algorithms
scrypt
- Excellent for systems requiring strong protection against hardware-based attacks
- Suitable for cryptocurrency applications (e.g., used in Litecoin)
- Good for high-security systems with sufficient memory resources
PBKDF2
- Still suitable for key derivation functions in various cryptographic protocols
- Useful in resource-constrained environments where memory-hardness isn't critical
- Appropriate for systems requiring FIPS compliance
Future Prospects
- Argon2: Likely to see increased adoption as the new standard for password hashing. Its flexibility and security make it well-positioned for future cryptographic needs.
- bcrypt: Will continue to be widely used due to its established presence and simplicity. However, it may gradually be replaced by Argon2 in high-security applications.
- scrypt: Will remain relevant, especially in cryptocurrency and other memory-hard applications. However, it may lose ground to Argon2 in general use cases.
- PBKDF2: Due to its widespread implementation and FIPS compliance, PBKDF2 will continue to be used, but it's likely to be phased out in favor of more secure alternatives for password hashing.
Conclusion
While all four algorithms are currently considered secure when properly implemented, Argon2 stands out as the most future-proof and safe option, especially for new systems. bcrypt remains a solid choice for general-purpose use, particularly in established systems. scrypt offers strong security against hardware attacks but at the cost of higher resource usage. PBKDF2, while still widely used, is generally considered the least secure option for password hashing among these four.
The choice of algorithm should be based on specific security requirements, available resources, and the nature of potential threats. In most cases, migrating to or implementing Argon2 is recommended for optimal security. However, proper implementation and parameter selection are crucial regardless of the chosen algorithm.
As the field of cryptography evolves, it's essential to stay informed about new developments and potential vulnerabilities in these algorithms. Regular security audits and updates to cryptographic practices remain vital for maintaining robust security in any system.
*** This is a Security Bloggers Network syndicated blog from Meet the Tech Entrepreneur, Cybersecurity Author, and Researcher authored by Deepak Gupta - Tech Entrepreneur, Cybersecurity Author. Read the original post at: https://guptadeepak.com/comparative-analysis-of-password-hashing-algorithms-argon2-bcrypt-scrypt-and-pbkdf2/
