![]()
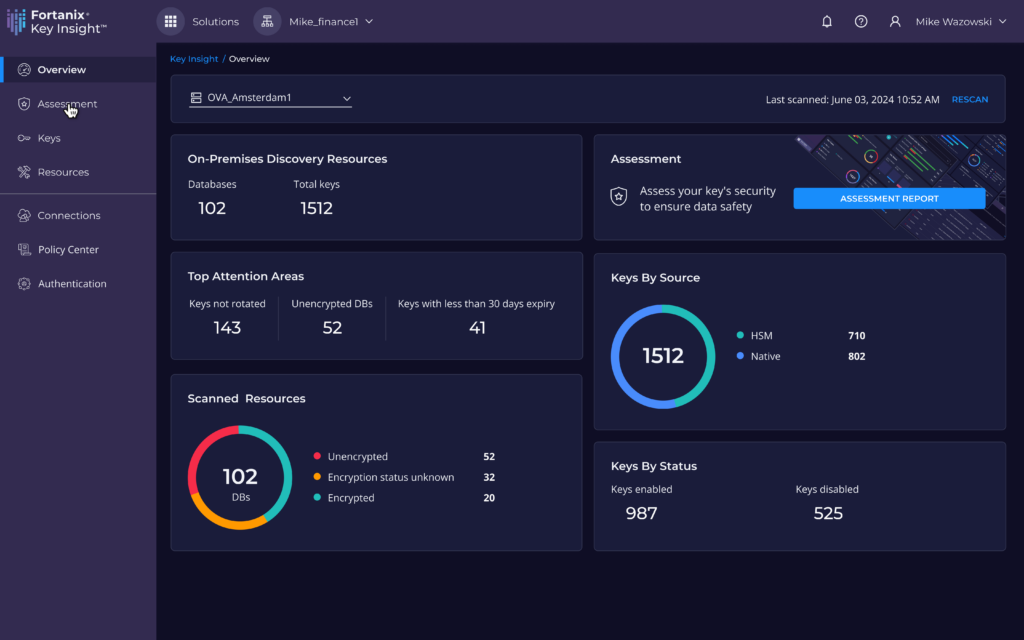
Fortanix today extended the reach of its ability to discover encryption keys to on-premises IT environments to enable organizations to more comprehensively manage risks.
Anuj Jaiswal, vice president of products at Fortanix, said this extension of the Key Insight platform the company provides will make it easier for organizations to manage encryption keys, that are today often distributed across a hybrid IT environment.
Key Insight runs on Fortanix Armor, a platform that makes use of confidential computing to ensure keys are always encrypted even while running in memory. The extension of Key Insight into on-premises IT environments makes it simpler for cybersecurity teams to better understand how well encryption is being applied across the entire organization, said Jaiswal.
If an issue is discovered cybersecurity teams can then centrally remediate cryptographic security posture via the Fortanix Armor platform, rather than having to manually fix each issue, he added.
That will prove to be crucial as advances in quantum computing are made there will soon come a day when organizations will need to discover all the encryption keys they have in place that these platforms might be able to break, noted Jaiswal. Given the effort required to replace all the types of encryption keys being employed, organizations are being advised to start that process now. Many nation-states are already collecting encrypted data in anticipation of being able to decrypt that data at some future date.
At the same time, organizations in the age of artificial intelligence (AI) are expected to apply encryption even more broadly to ensure sensitive data is not inadvertently shared with platforms that will use that data to train the next iteration of a model.
Encryption Keys and Updates
One of the challenges organizations typically encounter is encryption keys are usually configured when a platform is first deployed but seldom updated as changes are later made. It’s not uncommon for organizations to subsequently discover that privileges that were once granted to access encrypted data have never been updated until a compliance audit has failed.
Of course, cybercriminals can gain access to encrypted data by simply stealing the credentials of an end user who has been given access to that data. However, once the breach is discovered it becomes imperative to update the encryption keys that were granted as soon as possible. Today that process typically requires a significant amount of manual effort that requires more time than cybersecurity teams would prefer. Replacing encryption keys in the absence of a platform that automates that process also requires security operations teams to work closely with IT operation teams that often have other priorities.
There is no silver bullet with cybersecurity, but encryption is one of the best tools any cybersecurity team has. The primary reason it isn’t as widely employed as it might is that managing all the encryption keys needed has simply been too challenging for many organizations to effectively manage.
Recent Articles By Author