
2024-7-31 00:48:48 Author: securityboulevard.com(查看原文) 阅读量:9 收藏
Microsoft recently announced the deprecation of NTLM protocol for Windows client. This falls in line with Microsoft’s encouragement to move away from NTLM due to the security risks it introduces – and acts as a wakeup call that maintaining NTLM usage puts environments at high risk.
We cannot overlook the striking resemblance between today’s NTLM deprecation and Windows XP’s EOL a decade ago. In both cases, Microsoft ceased to support a legacy – yet extremely common – infrastructure that exposes its users to critical risks. In the case of XP, the risk was malicious remote code execution; with NTLM it’s credential access and subsequent lateral movement and ransomware spread.
This blog provides a summary of the potential identity threats NTLM introduces to organizations today and outlines a mitigation plan to ensure your environment remains resilient.
Did you know NTLM is alive and kicking?
While NTLM being ‘insecure’ is common knowledge, it is still heavily used in production environments. The Identity Underground Report, published in March 2024, disclosed that an alarming proportion of users, admins and service accounts still use NTLM for resource access:
64% of user accounts regularly use NTLM for resource access
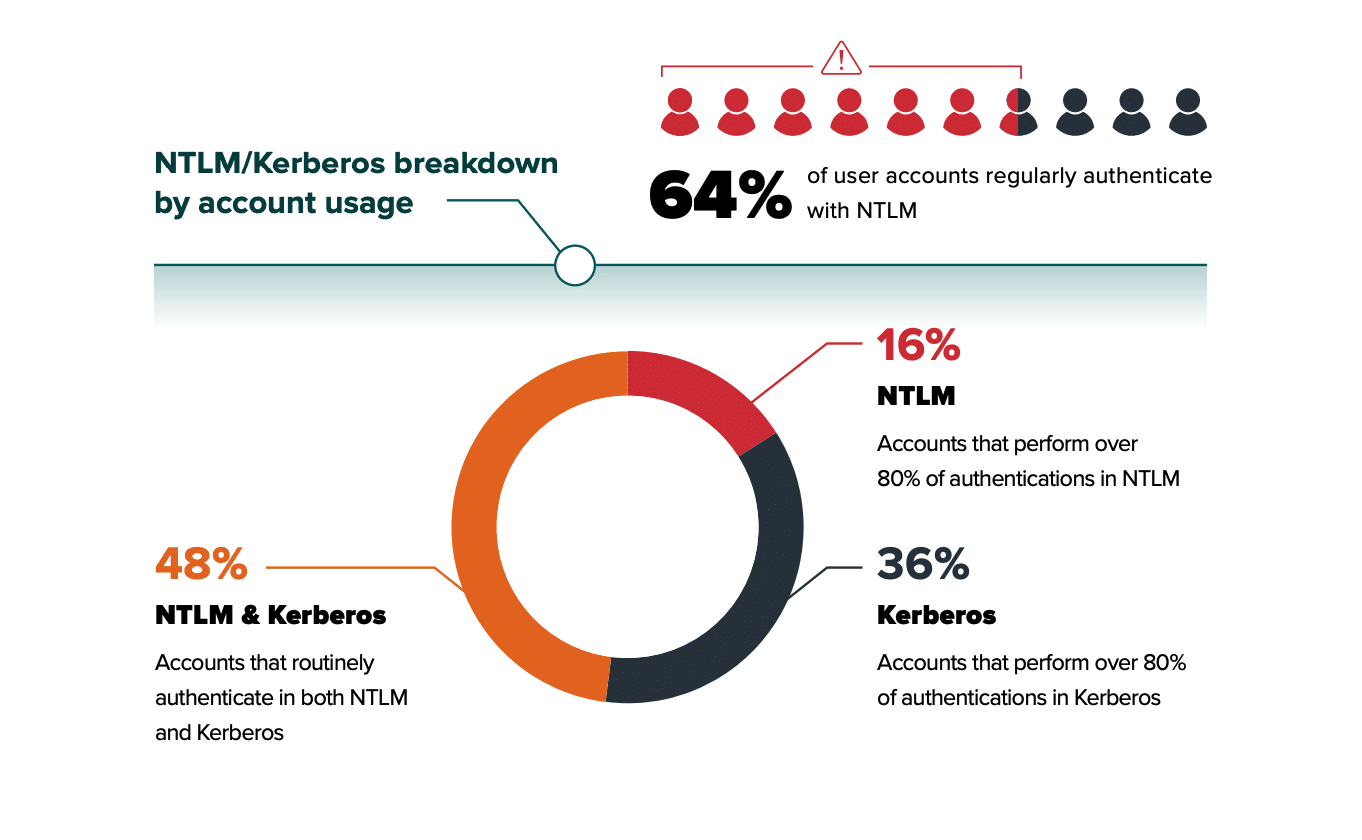
37% of administrator users regularly use NTLM for resource access
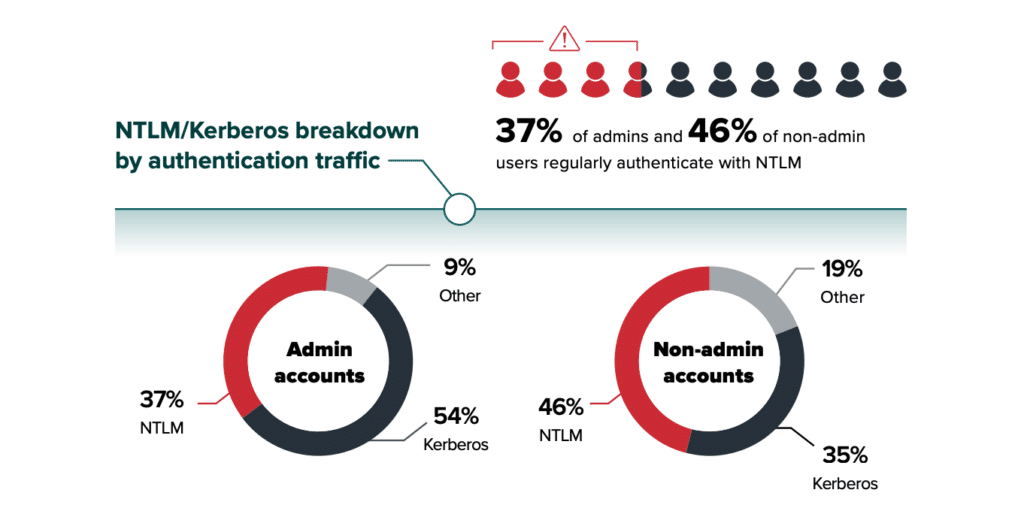
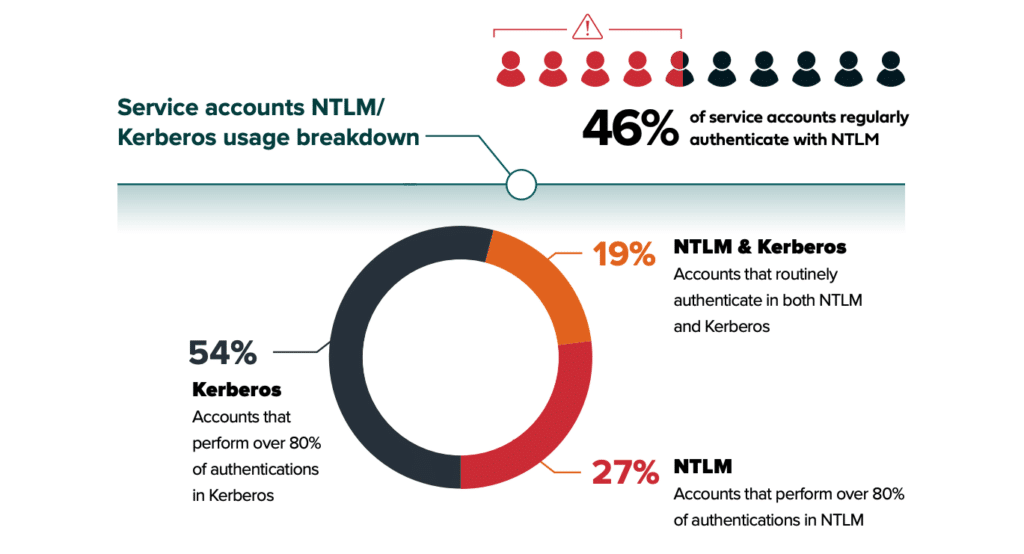
46% of service accounts regularly use NTLM for resource access
Did You Know NTLM Can Enable Mass Ransomware Spread?
But what is the actual risk of high NTLM usage?
NTLM security issues stem from the way it uses hashes instead of passwords. This eliminates sending the cleartext password over the wire, which is good. However, attackers can abuse this mechanism and use the NTLM hash itself as a password equivalent for malicious resource access.
Let’s map this NTLM abuse to MITRE ATT&CK framework terminology:
- Credential Access: attackers can employ a wide array of available tools to extract the NTLM either from its storage in machines’ memory or while it traverses the network between machines.
- Lateral movement: following the hash compromise, attackers can either use the hash itself or decrypt it offline to obtain the cleartext password. In the former case, they would use techniques such as Pass-the-Hash or NTLM relay. In the latter, they would simply use newly obtained passwords for malicious access.
The combination of credential access and lateral movement is the X-factor behind all the high-profile ransomware attacks organizations have experienced in recent years.
Knowledge Is Power: Ask the Following Questions to Understand and Resolve Your NTLM Risk Exposure
Gain insight into your environment’s NTLM exposure and mitigation capabilities by asking your identity security team the following questions:
Do we have visibility into actual NTLM usage in our environment?
This question focuses on the scope of your NTLM exposure across all users, admins, service accounts, and the resources where NTLM is used. The answer should be quantified as a percentage, like the one we’ve show above.
Can we limit NTLM usage to where it is absolutely necessary?
Next step is to see what you can do to minimize NTLM usage. The answer to this question should show the portion of your NTLM usage that cannot be eliminated (legacy apps are the most common example) and the portion that could be removed without any operational disruption.
Can we block lateral movement facilitated by NTLM in real time?
Here we should assume a breach has already happened. If NTLM is in place, there’s a solid chance that attackers would compromise passwords and attempt to perform malicious access. The answer to this question should list the security controls in place that can detect and block malicious access attempts using NTLM-related compromised credentials.
Conclusion: See, Know and Act to Mitigate NTLM Risks
Like with Windows XP, being proactive is the best approach to mitigate NTLM-driven risks. The three questions above are an outline for a proactive mitigation strategy, so can your identity and security teams provide solid answers to them? Of course, this would depend on the identity and security solutions you have in place. If you can’t find the answers or if they’re dissatisfying, immediate action is required to find the solution that can help. Anything shorter than that would leave you exposed.
Remember XP and the multiple attacks organizations experienced on a daily basis? That problem didn’t vanish by itself. NTLM will be no different.
The post NTLM Deprecation is Giving Us XP EOL Flashbacks: Are You Protected? appeared first on Silverfort.
*** This is a Security Bloggers Network syndicated blog from Silverfort Blog - Cyber Security News authored by Yiftach Keshet. Read the original post at: https://www.silverfort.com/blog/ntlm-deprecation-is-giving-us-xp-eol-flashbacks-are-you-protected/
如有侵权请联系:admin#unsafe.sh