minute read

In March 2024, we discovered a campaign targeting individuals in Russia with previously unseen Android spyware we dubbed LianSpy. Our analysis indicates that the malware has been active since July 2021. This threat is equipped to capture screencasts, exfiltrate user files, and harvest call logs and app lists. The malicious actor behind LianSpy employs multiple evasive tactics, such as leveraging a Russian cloud service, Yandex Disk, for C2 communications. They also avoid having dedicated infrastructure, and employ a lot of other features to keep the spyware undiscovered. Some of these features suggest that LianSpy is most likely deployed through either an unknown vulnerability or direct physical access to the target phone.
Technical details
Initially, LianSpy determines if it is running as a system app, which automatically receives the permissions it needs. Otherwise, it requests permissions for screen overlay, notifications, background activity, contacts, call logs, etc. Once authorized, the spyware verifies it’s not running in a debugging environment. If the environment is free from debugger artifacts, LianSpy sets up its configuration with predefined values and stores this data as a collection of key-value pairs locally using SharedPreferences, an app data storage mechanism generally used for storing application settings. This configuration persists across device reboots and uses integer keys linked to specific spyware settings in SharedPreferences. A detailed list of configuration parameters, including descriptions and default values, is provided below.
| ID (key) | Description | Default value |
| 100 | Is first launch | false |
| 110 | Allow to run if connected to Wi-Fi | true |
| 111 | Allow to run if connected to mobile network | true |
| 113 | Threat actor’s Yandex ID | REDACTED |
| 115 | Threat actor’s Yandex Disk OAuth token | REDACTED |
| 121 | Collect list of installed applications on target device | true |
| 123 | Collect call logs | true |
| 124 | Collect contact list | true |
| 128 | Take screenshots as root with screencap binary | false |
| 136 | Capture screen via media projection API | true |
| 302 | Time interval between screenshots in milliseconds | 5000 (5s) |
| 308 | Time interval between data exfiltration tasks in milliseconds | 1200000 (20min) |
| 400 | Comma-separated list of apps (package name substrings) for screen capture via media projection API or taking screenshots with screencap binary | whatsapp, viber, skype, chrome, vkontakte, telegram, android.gm, gallery, thoughtcrime.securesms, facebook, tencent.mm, snapchat, icq, tencent.mobileqq, imoim, mailapp, instagram, kakao.talk, discord, chrome, internet, browser, dolphin, firefox, opera, safari, uc browser, maxthon, baidu, yandex |
| 420 | Unused | – |
| 450 | User ID | – |
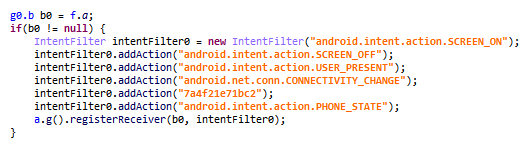
Once activated, the spyware hides its icon and registers a built-in broadcast receiver to receive intents from the system. This receiver triggers various malicious activities, such as screen capturing via the media projection API, taking screenshots as root, exfiltrating data, and updating its configuration.
To update the spyware configuration, LianSpy searches for a file matching the regular expression "^frame_.+\\.png$" on a threat actor’s Yandex Disk every 30 seconds. If found, the file is downloaded to the application’s internal data directory. The spyware then decrypts the overlay (data written after the end of the payload) in the downloaded file with a hardcoded AES key. Finally, the configuration updater searches the decrypted payload for a set of substrings, each substring modifying LianSpy’s configuration. A comprehensive list of available options can be found below.
| Substring (command name) | Description |
| *con+ | Enable contact list collection |
| *con- | Disable contact list collection |
| *clg+ | Enable call log collection |
| *clg- | Disable call log collection |
| *app+ | Enable collection of installed app list |
| *app- | Disable collection of installed app list |
| *rsr+ | Schedule taking screenshots |
| *rsr- | Stop taking screenshots |
| *nrs+ | Enable screen recording |
| *nrs- | Disable screen recording |
| *swl | Set new app list, stored right after command string, for screen recording |
| *wif+ | Allow to run if device is connected to Wi-Fi |
| *wif- | Prohibit from running if device is connected to Wi-Fi only |
| *mob+ | Allow to run if device is connected to mobile network |
| *mob- | Prohibit from running if device is connected to mobile network only |
| *sci | Set screen capture interval in milliseconds |
| *sbi | Set interval between data exfiltration tasks in milliseconds |
The collected victim’s data is stored encrypted in the SQL table Con001, which also contains the type of record (device information, contact list, call logs, etc.) and its SHA-256 hash. The data is encrypted using the following scheme:
- An AES key for data encryption is generated using secure pseudorandom number generator (PRNG). This approach thwarts timing-based attacks that could potentially be exploited by unauthorized parties.
- A hardcoded public RSA key embedded within the spyware encrypts the AES key.
This robust encryption scheme ensures that only a threat actor owning the corresponding private RSA key can decrypt stolen data.
Stealth features
LianSpy employs unconventional sophisticated evasion techniques to remain undetected.
- To blend in with legitimate applications, its variants masquerade as the Alipay app or a system service.
- Android 12 introduced the privacy indicators feature, which displays a status bar icon if sensitive data is being accessed, for example when the screen is being recorded. However, LianSpy developers have managed to bypass this protection by appending a cast value to the Android secure setting parameter icon_blacklist, which prevents notification icons from appearing in the status bar.
- To further conceal its activities, LianSpy hides notifications from background services it calls by leveraging the NotificationListenerService that processes status bar notifications and is able to suppress them. A list of key phrases used for removing a notification from the status bar can be found below.
running in the background
using battery
в фоновом режиме
использует батарею
используют батарею
- LianSpy can take screenshots using the screencap system command, typically employed for debugging, but accessible with root permissions. This command leaves no trace of screenshot capture, which allows attackers to stealthily capture screen content.
- It leverages legitimate cloud and pastebin services extensively, making malicious web activity from a compromised device virtually undetectable.
- It encrypts exfiltrated data using a robust encryption scheme. Victim identification remains impossible even if Yandex Disk credentials are compromised during APK analysis.
- LianSpy uses su binary with a modified name to gain root access. The malware samples we analyzed attempt to locate a mu binary in the default su directories. This indicates an effort to evade root detection on the victim’s device. Acquiring superuser rights with such a strong reliance on a modified binary suggests that the spyware was likely delivered through a previously unknown exploit or physical device access.
Infrastructure
LianSpy has no private infrastructure whatsoever. Instead, the threat actor leverages Yandex Disk for both exfiltrating stolen data and storing configuration commands. Victim data is uploaded into a separate Yandex Disk folder.
Other than configuration update job, LianSpy’s communication with its command-and-control (C2) server is unidirectional, with no incoming commands. The malware autonomously conducts update checks and data exfiltration based on its current configuration.
Yandex Disk credentials can be updated from a hardcoded pastebin URL, which may vary across different malware variants. A comprehensive list of these pastebin pages is provided in the IoC section.
Victims
Given that key phrases used to filter notifications are partially in Russian, and some of the default configurations of LianSpy variants include package names for messaging apps popular in Russia, we assume that this spyware targets users in that country. Our KSN telemetry corroborates this, indicating that Russian users have been victims of LianSpy attacks.
Conclusion
The newly discovered Android spyware we dubbed LianSpy exhibits several noteworthy capabilities. Beyond standard espionage tactics like harvesting call logs and app lists, it leverages root privileges for covert screen recording and evasion. Its reliance on a renamed su binary strongly suggests secondary infection following an initial compromise. Unlike financially motivated spyware, LianSpy’s focus on capturing instant message content indicates a targeted data-gathering operation.
By exclusively leveraging legitimate platforms like Yandex Disk and pastebin services for data exfiltration and C2 communication, the threat actor has complicated attribution. This novel Android threat exhibits no overlap with ongoing malware campaigns targeting Russian users, and we will maintain vigilant monitoring for related activities.
Indicators of Compromise
APK file hashes
084206ec8e6e5684a5acdcbd264d1a41
09088db5640381951e1b4449e930ff11
15222c61978f9133aa34b5972ce84e7e
1ccf5b723c38e30107d55040f10ce32a
22b013cfb95df6b4ba0d2d40dc4bddf4
23b9e5d4ab90506c6e9a42fa47164b84
36bc97ce040ada7142e4add4eb8cd3dd
38149658e5aba1942a6147b387f79d3f
3a4f780820043a8f855979d2c59f36f2
4c3e81bb8e972eef3c9511782f47bdea
5b16eb23a2f5a41063f3f09bc4ca47dd
69581e8113eaed791c2b90f13be0981a
707a593863d5ba9b2d87f0c8a6083f70
7de18a7dac0725d74c215330b8febd4e
842d600d5e5adb6ca425387f1616d6c4
86ea1be200219aca0dc985113747d5ea
86f7c39313500abfb12771e0a4f6d47a
8f47283f19514178ceb39e592324695a
966824d8c24f6f9d0f63b8db41f723b6
99d980a71a58c8ad631d0b229602bbe2
9f22d6bffda3e6def82bf08d0a03b880
a7142ad1b70581c8b232dc6cf934bda4
c449003de06ba5f092ee9a74a3c67e26
d46c5d134a4f9d3cd77b076eb8af28b3
d9e9655013d79c692269aeadcef35e68
da97092289b2a692789f7e322d7d5112
ec74283d40fd69c8efea8570aadd56dc
f13419565896c00f5e632346e5782be4
f37213a7ef3dc51683eec6c9a89e45af
f78eaca29e7e5b035dbcbabac29eb18d
fa3fecca077f0797e9223676d8a48391
fbc2c4226744c363e62fcfeaec1a47f1
Yandex Disk encrypted credential sources
hxxps://pastebin[.]com:443/raw/X4CuaV5L
hxxps://pastebin[.]com:443/raw/0t2c1Djz
hxxps://pastebin[.]com:443/raw/8YXyQtp9
hxxps://pastebin[.]com:443/raw/hm78BGe9
hxxps://pastebin[.]com:443/raw/R509SydV
hxxps://pastebin[.]com:443/raw/dXXcZDF7
hxxps://pastebin[.]com:443/raw/81GhQUjK
hxxps://pastebin[.]com:443/raw/2PmX7Bgd
hxxps://pastebin[.]com:443/raw/zsY6tZLb
hxxps://pastebin[.]com:443/raw/rzMhGiFp
hxxps://pastebin[.]com:443/raw/85DMiWdE
hxxps://pastebin[.]com:443/raw/nSZaB3hw
hxxps://pastebin[.]com:443/raw/Wppem8U5
hxxps://pastebin[.]com:443/raw/KRqNqNrT
hxxps://pastebin[.]com:443/raw/47uLyg6q
hxxps://pastebin[.]com:443/raw/tUQFWtVY
hxxps://pastebin[.]com:443/raw/AgBMX16r
hxxps://pastebin[.]com:443/raw/wSzsbXpg
hxxps://pastebin[.]com:443/raw/e0SqYu41
hxxps://pastebin[.]com:443/raw/ZBFe2b4z
hxxps://pastebin[.]com:443/raw/cbLWwCbR
hxxps://pastebin[.]com:443/raw/fxqART5r
hxxps://pastebin[.]com:443/raw/hiAYisG8
hxxps://pastebin[.]com:443/raw/459bbu4H
hxxps://pastebin[.]com:443/raw/7kxADNLm
hxxps://pastebin[.]com:443/raw/417svXuD
hxxps://pastebin[.]com:443/raw/w4j6jNBV
hxxps://pastebin[.]com:443/raw/9eQJ8uUd
hxxps://pastebin[.]com:443/raw/zy8BKYyg
hxxps://pastebin[.]com:443/raw/uc5Ft4z6