2024-8-6 00:42:43 Author: securityaffairs.com(查看原文) 阅读量:7 收藏
Researchers warn of a new critical Apache OFBiz flaw

Researchers urge organizations using Apache OFBiz to address a critical bug, following reports of active exploitation of another flaw.
Experts urge organizations to address a new critical vulnerability, tracked as CVE-2024-38856, in Apache OFBiz. The vulnerability is an incorrect authorization issue in Apache OFBiz that impacts versions through 18.12.14, version 18.12.15 addressed the flaw.
“Unauthenticated endpoints could allow execution of screen rendering code of screens if some preconditions are met (such as when the screen definitions don’t explicitly check user’s permissions because they rely on the configuration of their endpoints).” reads the advisory.
The security researcher Hasib Vhora from SonicWall reported the vulnerability CVE-2024-38856 along with other security experts.
“The SonicWall Capture Labs threat research team has discovered a pre-authentication remote code execution vulnerability in Apache OFBiz being tracked as CVE-2024-38856 with a CVSS score of 9.8. This is the second major flaw SonicWall has discovered in Apache OFBiz in recent months, the first coming in December 2023.” wrote Vhora. “This time, a flaw in the override view functionality exposes critical endpoints to unauthenticated threat actors using a crafted request, paving the way for remote code execution. It affects Apache OFBiz versions up to 18.12.14, and users are strongly encouraged to upgrade their instances to version 18.12.15 or newer.”
The issue stems from a flaw in the authentication mechanism, which allows unauthenticated users to access features typically restricted to logged-in users, potentially leading to remote code execution.
Apache OFBiz is an open-source ERP system that helps businesses automate and integrate various processes such as accounting, HR, CRM, order management, manufacturing, and e-commerce. It is used by hundreds of companies worldwide, with 41% in the U.S., 19% in India, 7% in Germany, 6% in France, and 5% in the U.K. Notable users include United Airlines, Atlassian JIRA, Home Depot, and HP.
SonicWall is not aware of attacks in the wild exploiting this vulnerability, however it has developed IPS signature IPS:4455 to detect any active exploitation of this issue.
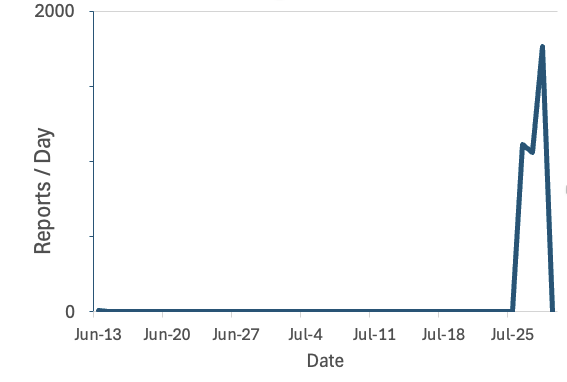
In May, researchers disclosed another vulnerability, a path traversal issue tracked as CVE-2024-32113, in the Apache OFBiz. The exploitation of this second vulnerability could lead to remote command execution.
Researchers from SANS recently observed a surge in the attacks targeting CVE-2024-32113.
“With the vulnerability announcement in May, we have been waiting for some scans to take advantage of the OFBiz vulnerability. Exploitation was trivial, and while the vulnerable and exposed population is small, this hasn’t stopped attackers in the past. But they are now at least experimenting and maybe adding the vulnerability to bots like Mirai variants.” reads the advisory published by SANS.
Researchers from threat intelligence firm GreyNoise also observed an exploitation attempt for this second vulnerability.
In December, SonicWall experts warned of another authentication bypass zero-day flaw, tracked as CVE-2023-51467, that affects Apache OfBiz.
An attacker can trigger the vulnerability to bypass authentication to achieve a simple Server-Side Request Forgery (SSRF).
In January, researchers from cybersecurity firm VulnCheck created a proof-of-concept (PoC) exploit code for the flaw.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Apache OFBiz)
如有侵权请联系:admin#unsafe.sh
