2024-8-5 23:50:44 Author: hackernoon.com(查看原文) 阅读量:13 收藏
If you're reading this article, you've probably heard of "multi-cloud," which involves connecting to more than one cloud provider. With the fast-paced shift, many organizations are moving towards multi-cloud deployments and moving away from traditional networks.
In this article, I will cover how you can establish the site-to-site VPN tunnel configuration between AWS Managed VPN and Google Cloud Platform (GCP) using the dynamic BGP routing protocol. This article will be helpful to those who are looking to incorporate multi-cloud architecture into a high-availability setup.
Prerequisite:
- Configure VPC network and its firewall rules on Google Cloud Platform side.
- Configure Virtual Private Cloud, subnets, and routing on AWS side.
Architecture:
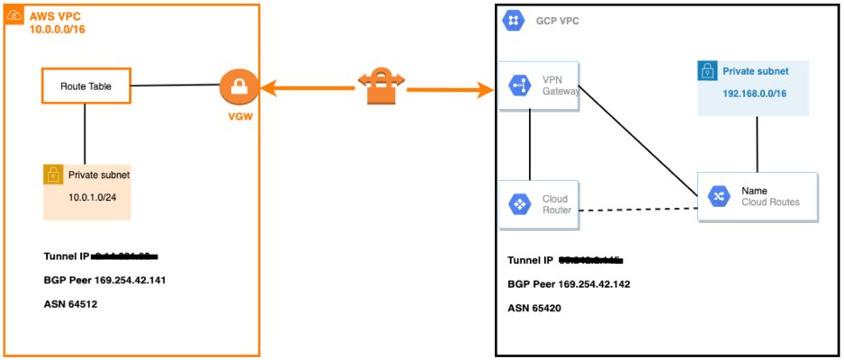
While this can be implemented programmatically on both ends, I chose to use the console since it better helps understand the process easily.
Configuration on GCP side:
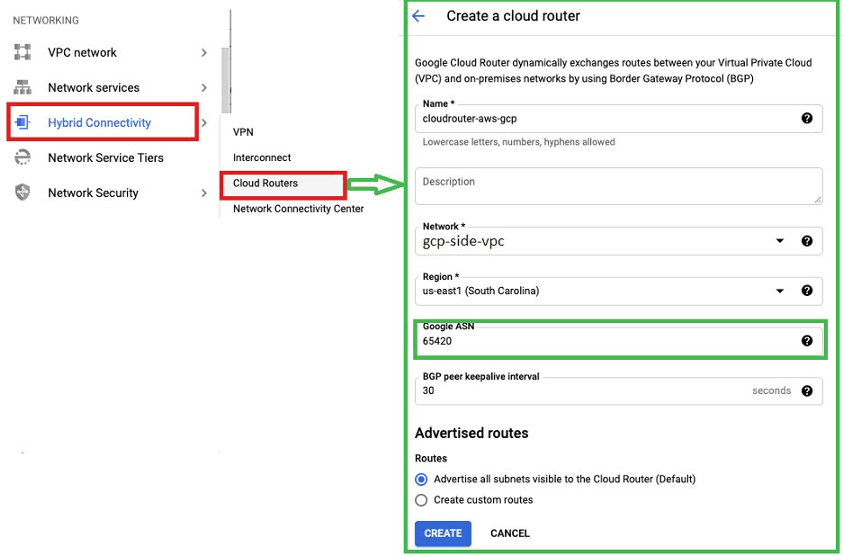
- Navigate to the “Hybrid connectivity” and create “Cloud router”.
- Navigate to the “Hybrid connectivity” and create “High-Availability VPN Gateway”.
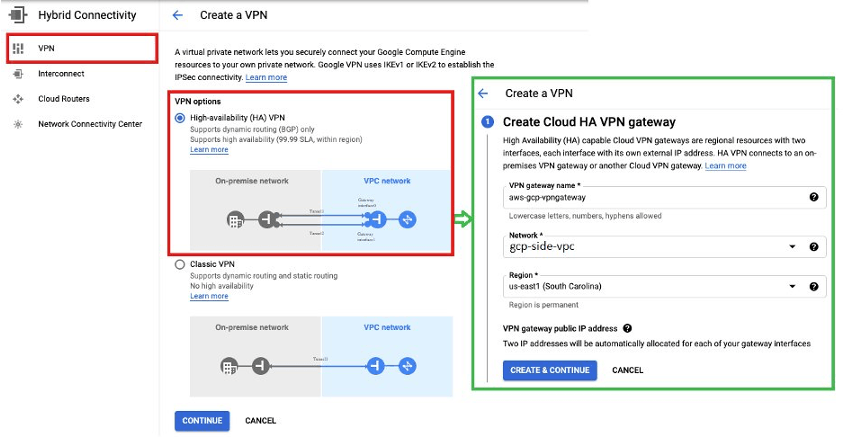
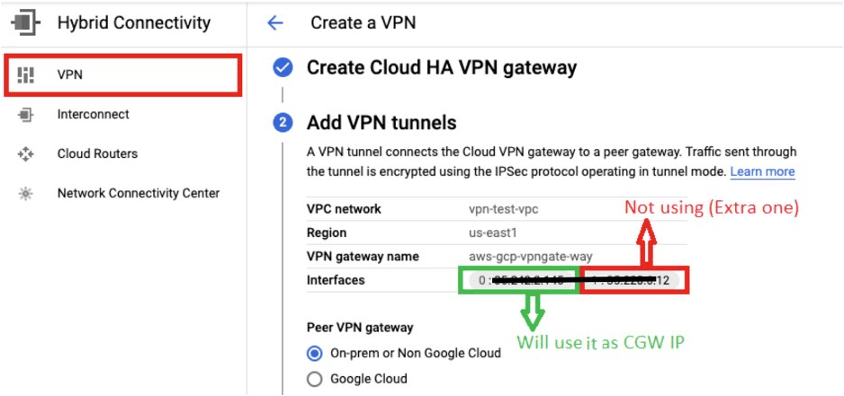
Once, High-Availability VPN Gateway is created, we get two interface IPs (check below screenshot) which we can use them as customer gateway IPs on AWS side. Here, I am using only one interface IP: 35.x.x.x (External IP) as I am configuring single VPN connection on AWS side.
Configuration on AWS side:
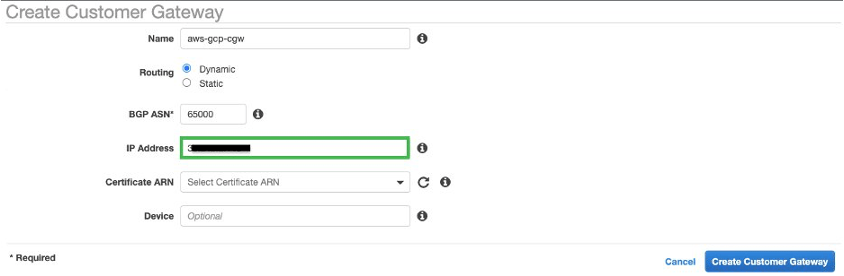
- Create a Customer Gateway in the AWS VPC console.
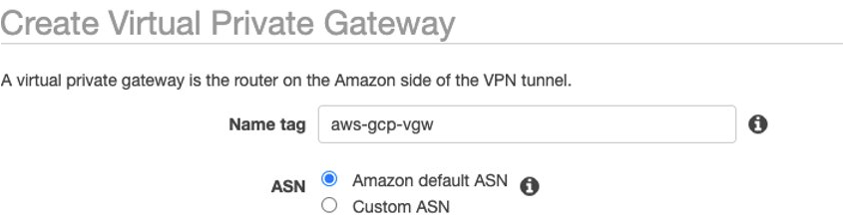
- Create a Virtual Private gateway in the AWS VPC console
-
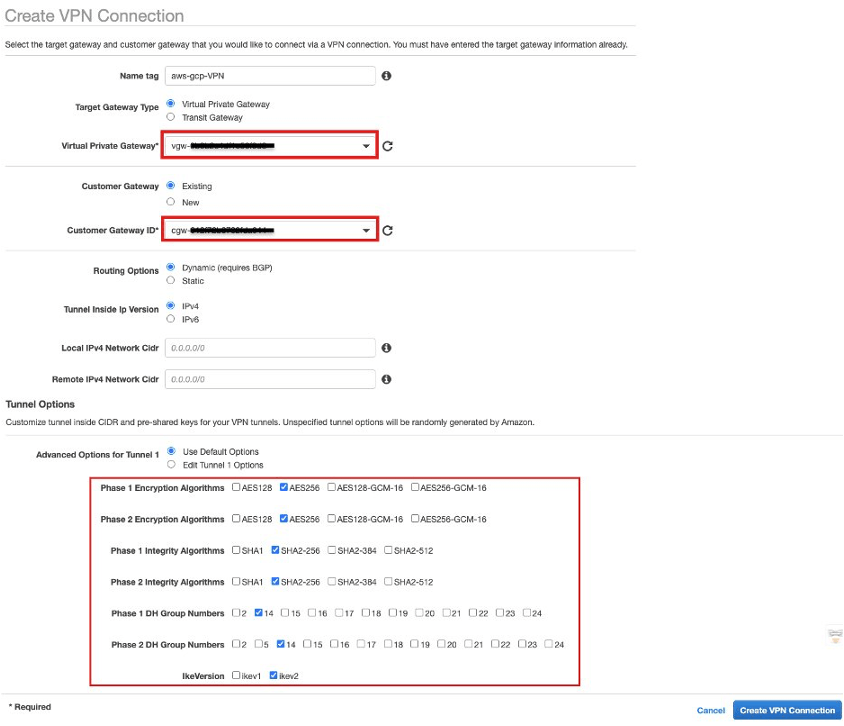
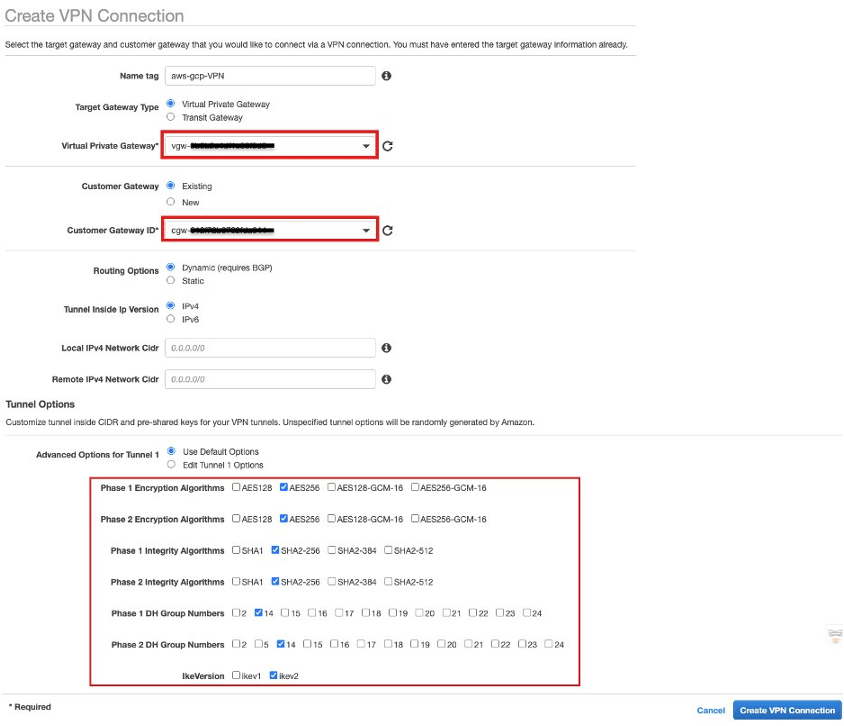
Create a site-to-site VPN connection in the AWS console by specifying the Customer gateway (created in step 3) and Virtual private gateway (Created in step 4).
Under “Advanced Options for Tunnel 1”, disabled ikev1 and enabled ikev2 with advanced encryption algorithms. Enabling advanced encryption algorithms is optional. You can disable some algorithms if you don’t want to us as I did in below screenshot.
- Download the generic VPN configuration file from AWS VPN console.
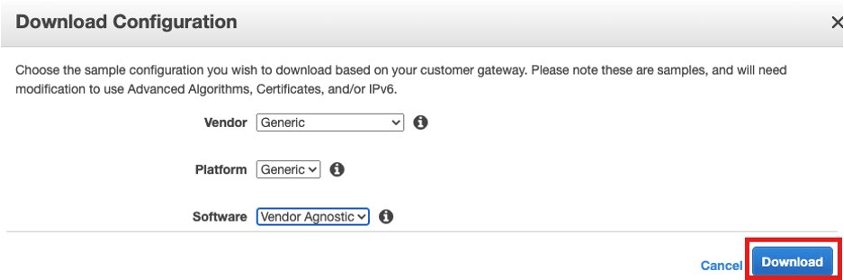
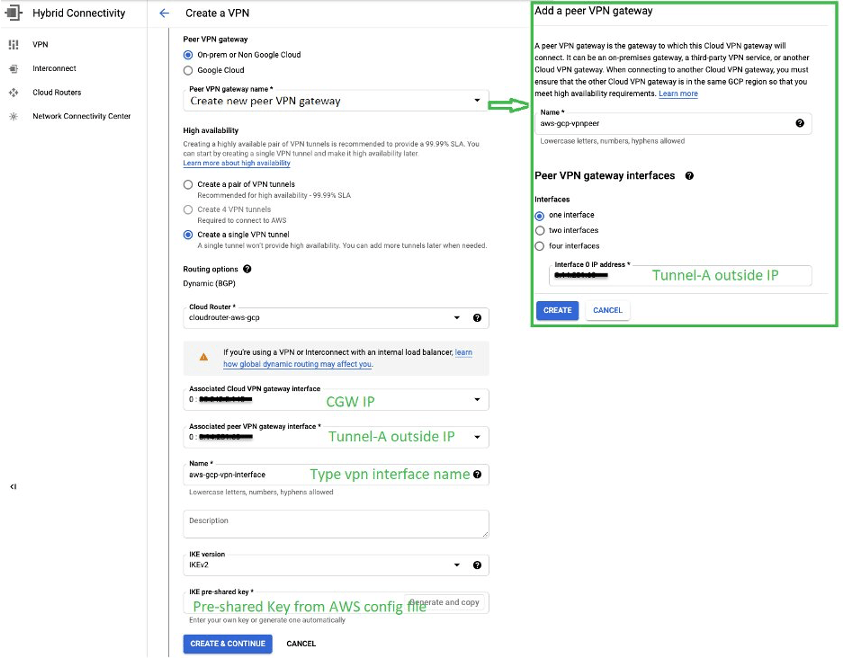
Return to GCP console and configure VPN Gateway using downloaded configuration file
- Configure VPN connection by creating a peer VPN Gateway on GCP Console
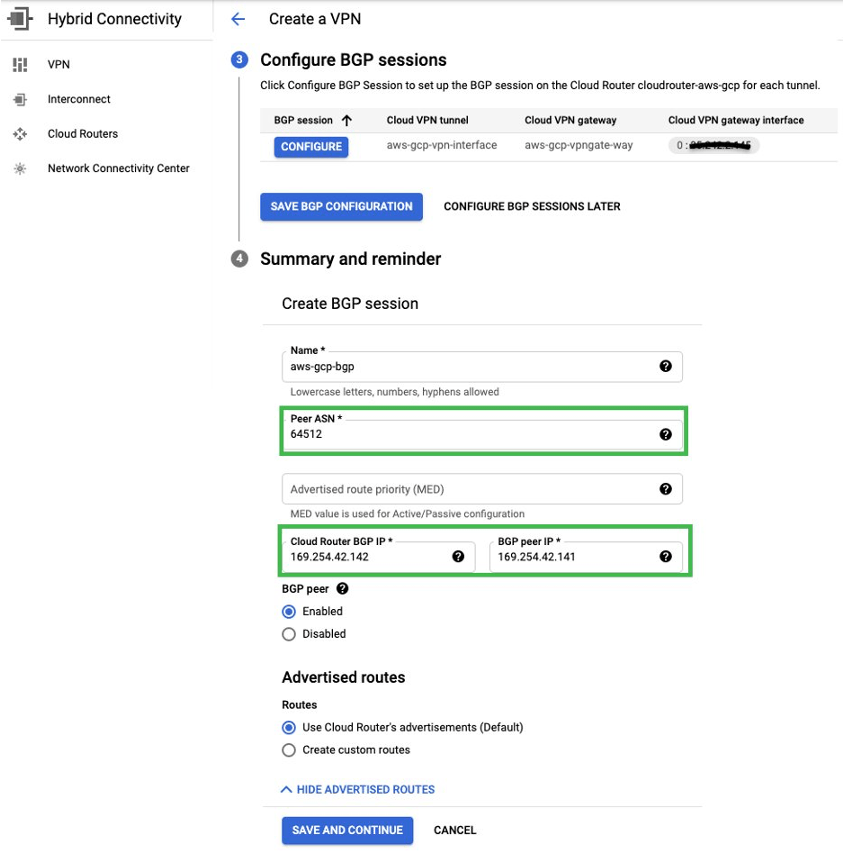
- Configure BGP on GCP side:
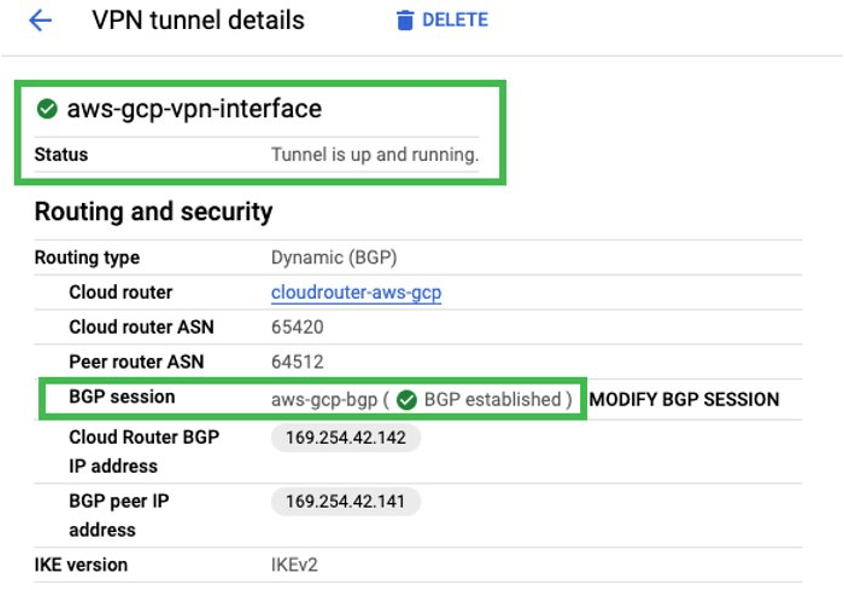
Tunnel and BGP status is UP on GCP side:
Tunnel and BGP UP on AWS Console:
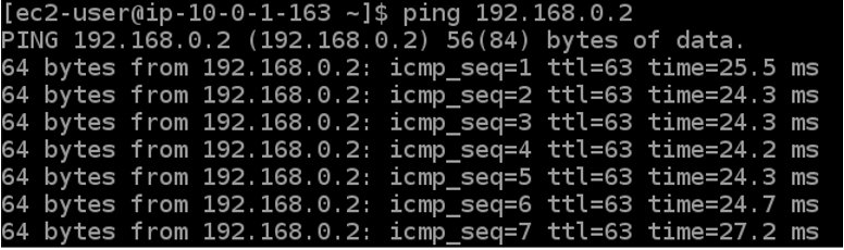
Ping test from GCP to AWS:
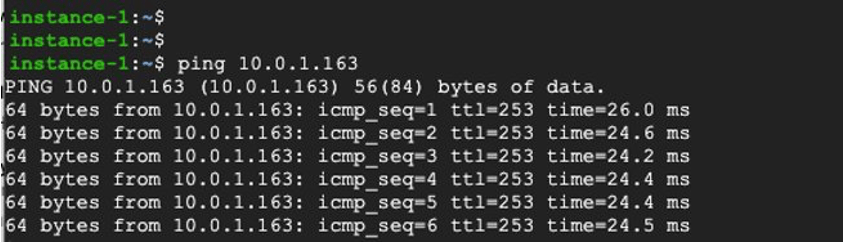
Ping test from AWS to GCP:

By following these steps, you can make your network more reliable and always available. Whether you’re new to multi-cloud setups or want to improve your current one, this guide will help you establish Site-to-Site VPN that will help you to achieve encrypted and secure connectivity between multi-cloud environment.
References:
[1] Getting started with AWS Site-to-Site VPN: https://docs.aws.amazon.com/vpn/latest/s2svpn/SetUpVPNConnections.html
[2] Connect HA VPN to AWS peer gateways: https://cloud.google.com/network-connectivity/docs/vpn/how-to/connect-ha-vpn-aws-peer-gateway
如有侵权请联系:admin#unsafe.sh