2024-8-6 14:24:3 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
“Shadow IT” isn’t just a catchy term; it goes beyond official procedures. It also shows unmet employee tech needs and perceived problems in company processes. What’s worse is that shadow IT can make your system more vulnerable to attacks, put compliance at risk, and lead to scattered and poor IT operations. The risk isn’t just in what you don’t know, but also in what you think you know but don’t.
Experts predict that shadow resources will be the target of between one-third and one-half of successful cyberattacks this year, based on figures from Gartner and Spin Technologies. Given that a data breach in the U.S. costs $4.2 million on average, it’s essential to tackle the risks linked to shadow IT. In this blog, we’ll dig into the intricacies of shadow IT and the insights you can gain from watching employee actions that could transform your cybersecurity approach.
What is Shadow IT?
Shadow IT is about using hardware or software without the approval of the company’s IT department or security team. It includes activities with products, services, and solutions that don’t follow the company’s rules for security, compliance, and data governance. In simple terms, it means going around company guidelines and picking up technology on your own.
What drives the prevalence of shadow IT in many organizations today? The fast rise of public cloud technologies has a big impact on the growth of shadow IT. The public cloud has turned once futuristic ideas into real things making it easy to access services and solutions from any device with just a few clicks. The handiness and ease of use of the public cloud are hard to beat letting people get to their files from anywhere without trouble. People can set up cloud-hosted solutions and services fast, often in just a few minutes.
Services like Google Drive, OneDrive, Dropbox, Box, and other cloud platforms need just an email address to create an account, and they offer free options. This simplicity draws in employees who want the handiness and freedom to access certain data from any device wherever they are. But this handiness also brings possible issues when it comes to managing the risks of shadow IT.
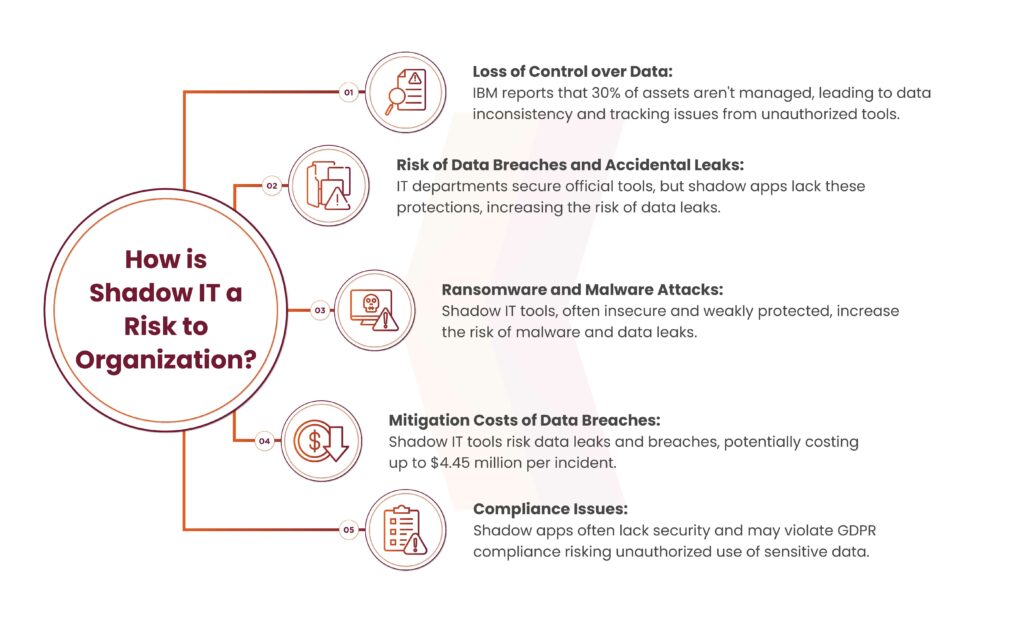
How is Shadow IT a Risk to Organizations?
According to a Cisco study, 80% of employees use shadow applications. They often choose these tools based on personal preferences or to expedite task completion. Below is the list of risks associated with Shadow IT :
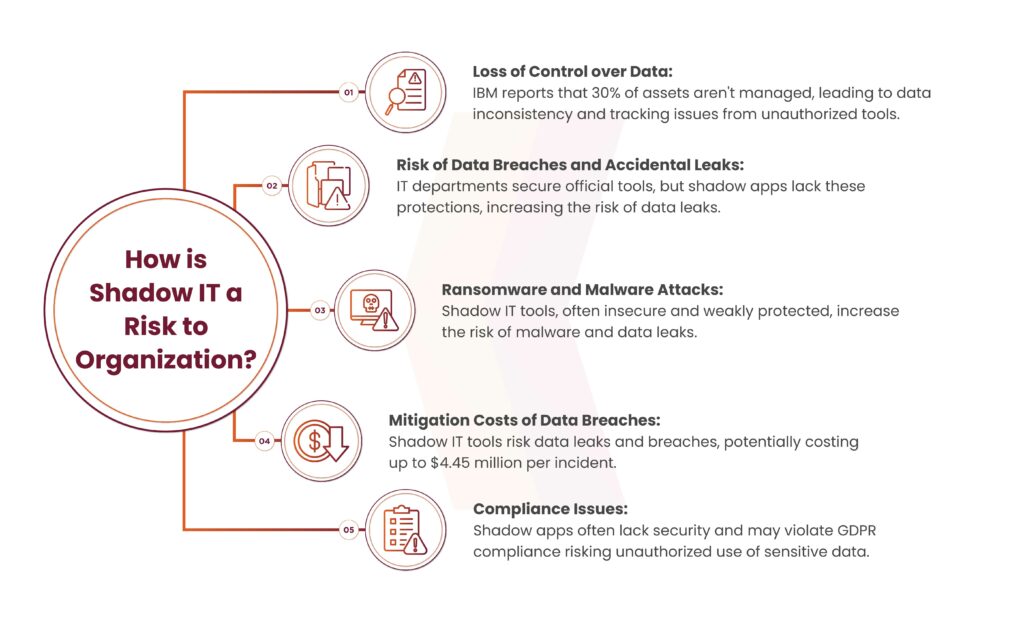
Loss of Control Over Data
IBM reports show that 30% of an organization’s assets are not part of formal asset management programs. Business data can become dispersed across various platforms when tools and applications are used without authorization. This can lead to data inconsistency because there’s no single oversight.
Also when employees share information or talk through their devices, organizations find it hard to keep track of the data. Companies often fail to back up or store this data according to their policies. As a result, if an employee quits or gets fired, the organization might not be able to locate or control the data.
Risk of Data Breaches and Accidental Leaks
An organization’s IT department puts in place tight security measures, encrypts data, and controls user rights for the tools, tech, and apps it manages. On the flip side, shadow apps don’t have the company’s security shields or proper controls, which means they’re more likely to leak data when it’s stored or sent.
Employees and higher-ups might not know about updates, settings, or key security controls. This can lead to sensitive info being kept and sent through shadow devices and apps.
Ransomware and Malware Attacks
Using shadow IT tools increases the organization’s risk of experiencing malware and ransomware attacks. These tools often lack good security practices because the organization’s cybersecurity solutions don’t cover them.
A Gartner study shows that one in three successful cyberattacks goes after data kept on shadow devices. On top of that, shadow tools often have weak passwords, which makes organizations more likely to face malware attacks, data leaks, and breaches. For instance, a Cequence Security study found that out of 16.7 billion malicious requests, 5 billion (or 31%) targeted shadow APIs.
Mitigation Costs of Data Breaches
Shadow IT tools pose a risk of sensitive data ending up in unauthorized apps. Many shadow apps let users share, store, and work together on files, which can lead to data leaks and breaches. These breaches can cost a lot, often resulting in big fines and penalties. For instance, an IBM report showed that the global average cost of a data breach in 2023 was $4.45 million. If a company traces a data breach back to shadow IT, it might face regulatory fallout.
What’s more, shadow IT apps work without the company keeping an eye on them. This means data leaks can go unnoticed for a long time, which makes them more expensive to fix. enough, staff often use shadow IT to save money and work better. However, the costs of breaking rules and dealing with data leaks can be huge.
Compliance and Security Concerns
Shadow apps often lack good security measures, which can lead to people using an organization’s sensitive data without permission. Also, using cloud storage devices that aren’t approved can result in data being kept in different places breaking data residency rules. Standards like the General Data Protection Regulation (GDPR) need tight controls to handle personal data, and shadow apps might not have the right data security measures in place.
Book a Free Consultation with our Cyber Security Experts

Preventive Measures to Mitigate Shadow IT Risk
Ways to get rid of shadow IT centers on tackling staff’s unapproved use of IT tools and apps often stems from employees wanting to work faster and easier, but it can bring big risks, like weak security and rule-breaking. To fight these problems, companies should implement a full SaaS control plan. This plan should enforce rules, teach employees, and use a SaaS Management Platform (SMP) to see and manage software use better. Key steps include setting up a standard software list, monitoring costs, and getting IT and business teams to work together. This helps make sure tech needs match company goals. By taking these steps, firms can cut down on shadow IT while helping staff use approved tools well.
How can Kratikal help you Prevent Shadow IT?
Businesses that need to follow data protection laws, like the GDPR, must be able to keep an eye on and control how data gets handled and passed around. Employees may violate company rules when they use unauthorized tools to handle sensitive information. This can lead to big penalties and fines.
Kratikal has solutions to help companies deal with shadow IT. We offer tools that spot both allowed and unauthorized systems and services in use. Cloud Access Security Broker (CASB) services boost security for cloud apps with features like access control, data loss prevention, and browser isolation. By creating an environment of open talk and understanding, Kratikal helps companies set up a safe space to discuss and approve needed tools. This cuts down the risk of data leaks and makes sure companies follow data protection rules.
- Is shadow IT a threat?
Yes, shadow IT poses a significant threat to your cloud environment. When your IT security team is unaware of the existence of an application that has access to your data, they cannot assess the associated risks or respond promptly in the event of a cyber incident.
- Why do employees use shadow IT?
Employees typically turn to shadow IT when they have difficulties using sanctioned tools or processes, leading them to use unofficial methods to finish their tasks.
The post How to Secure Your Organization from Shadow IT? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/how-to-secure-your-organization-from-shadow-it/
如有侵权请联系:admin#unsafe.sh