2024-8-8 01:0:9 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Firstly, we extend our thanks to Chris Fearnley and Gi7w0rm, two threat researchers who assisted us behind the scenes with our investigation into the 7777 (“Quad7”) botnet. Their insights were instrumental in confirming the findings mentioned in this blog post.

A “7777 botnet” was first referenced in public reporting in October 2023 by Gi7w0rm. At the time, it was described as a botnet with approximately 10,000 nodes, observed primarily in brute-force attacks against Microsoft Azure instances. These attacks were characterized by their low-volume nature, making them inherently difficult to detect, with only 2-3 login attempts made per week in some cases. While initial reports suggested VIP users were targeted by these attacks, more recent research by Sekoia indicated there was no clear targeting pattern in the attacks they observed.
The botnet takes its name from the fact it uniquely opens TCP port 7777 on compromised “zombie” routers. When scanned, the service on this port returns an xlogin: banner.
To date, various low-confidence attributions have linked Quad7 to both cybercrime and state-sponsored activities. However, little conclusive evidence in this area has been made public, leaving the true operators of the botnet shrouded in mystery.
In this blog post, we will examine the Quad7 botnet and the infrastructure used to control it in greater detail.
Key Findings
-
Identification of a potential expansion of the Quad7 threat operator’s modus operandi to include a second tranche of bots, characterized by an open port 63256.
-
The port 63256 botnet appears to be comprised mainly of infected Asus routers.
-
Identification of 12,783 active bots (comprising both 7777 and 63256) over the 30-day period ending 05 August 2024, likely to represent a proportion rather than the full extent of the botnet.
-
Identification of seven management IPs either currently active or last observed in the past 30 days. Four of the IPs align with recent research by Sekoia, with the remaining three previously unattributed.
Bot Hunting & Characterization
As disclosed by other researchers and alluded to above, Quad7 bots can be identified by querying for IP addresses with an open port 7777 displaying the xlogin: banner.
In Figure 1 below, we can see that over the past 30 days (at the time of writing), 7,038 devices were identifiable in this way.

Figure 1 – Quad7 Bots
Note, we have redacted some victim-related information from Figure 1 (and Figure 2 below).
This number (7,038) is lower than the approximately 10,000 nodes quoted in Gi7w0rm’s research from last October. There are two likely reasons for this discrepancy:
-
The initial findings may have been derived from a period longer than 30 days or from scan data collected at closer intervals, capturing routers that were only “online” for relatively short periods.
-
Since the public reporting of Quad7 emerged, users may have taken steps to clean infections or update vulnerable firmware to prevent their routers from being targeted.
Point 1 raises a more general issue about approximating the scale of botnets with scan data. It is important to remember that statistics derived in this way only represent a proportion of all available bots. This is due to various factors, the most significant being an "offline" device won't be picked up via this discovery method, even though it will likely continue to be a viable bot when it returns "online".
Whatever the case, nearly ten months later it is apparent that Quad7 remains active and retains a “healthy” number of bots, particularly if one of its primary use cases is low-volume brute force attacks.
Digging further into our result set, and based on the comprehensive tagging of IPs that we undertake to contextualize the data observed on our platforms, it was apparent that a significant proportion were likely Hikvision or TP-Link devices. This finding correlated with previous research on Quad7, such as this blog by VulnCheck, which examined the targeted hardware in more detail.
In Figure 2 below, we can see an example of this, with the highlighted host identified specifically as a TP-LINK WR841N router.

Figure 2 – Router Tag Example
Insights such as these, particularly specific router types, allow us to both understand and track how the botnet proliferates. Additionally, they enable Team Cymru and our customers to hunt for potentially vulnerable infrastructure in the hopes of pre-emptively disrupting future compromises.
We will expand on the subject of hardware identification in the next section..
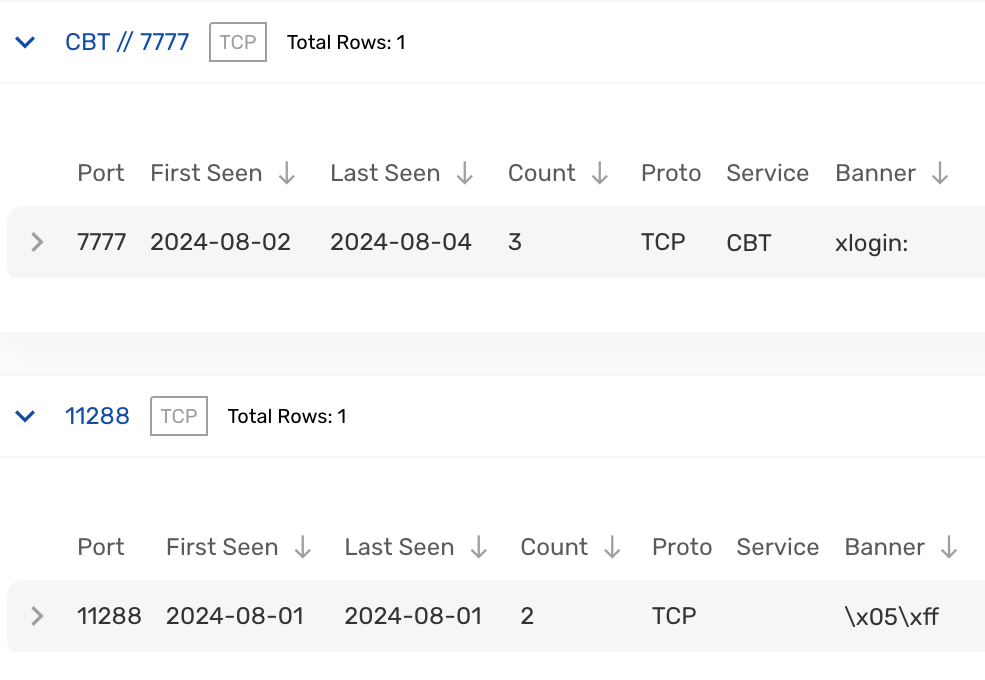
Eagle-eyed readers will also notice in Figures 1 and 2 that, in some cases, port 11288 was also observed open on hosts enrolled in the Quad7 botnet.
This is not a novel finding; previous research into Quad7 identified that a SOCKS5 proxy service was configured to operate on this port in some cases. The research by Sekoia narrowed this activity down to an open-source SOCKS5 proxy server developed by GitHub user bhhbazinga. Of possible note, this user lists their location as Hangzhou, China.
Sekoia found that TCP/11288 was used by the threat operators to proxy communications to third-party servers for the purpose of brute-forcing attacks. Specifically, they observed connections to login.microsoftonline[.]com, indicating that these attacks were targeted at Microsoft 365 accounts.
This process is simplified in Figure 3 below.

Figure 3 – SOCKS5 Proxy Use Case
By repeating the technique illustrated in Figure 1, we can sanity-check our findings by hunting for hosts with an open port 11288. Based on data from numerous hosts identified through hunting for an open port 7777, we found that a common banner (\x05\xff) was also displayed in cases where port 11288 was open. Figure 4, below, shows an example of this.

Figure 4 – Open Ports Information
The 63256 Botnet
Our next finding raises identity issues for the “7777 botnet.” We have observed a potential expansion of the threat operator’s activities, adding over 5,000 “zombie” devices in the process.
First, let’s play a game of “spot the difference”, comparing Figure 5 below to Figure 4 above.

Figure 5 – The Same Open Ports Information, But Different
The banner information is almost identical, but the observed open ports have switched. When we combined a hunt for these banners on port 7777 (xlogin:) and port 63256 (alogin:), a total of 12,783 hosts were identified.
So, in a way, we take back what we said about there being fewer “zombie” devices now compared to October 2023.
When looking at tagging data for the 63256 botnet, we found that a significant proportion of the hosts were likely operating ASUS routers. This marks another change in technique. As previously referenced, Quad7 activity had focused on the compromise of TP-LINK routers. The delineation appears to be as follows:
-
7777 botnet (xlogin): TP-LINK routers and various IP-camera types
-
63256 botnet (alogin): ASUS routers
NetFlow Analysis
Having established a substantial pool of recent analytical leads in the form of hosts likely enrolled in the Quad7 botnet (or botnets), we can now start to examine supporting NetFlow data. In this case, we are seeking to establish common peer IPs and further indications of management activity.
In total, seven such IPs were identified with high confidence following our analysis of associated NetFlow data. Figure 6 below presents the observed relationships in the form of a chart.

Figure 6 – Infrastructure Diagram
The seven IPs were assigned to three distinct providers: HOSTWINDS, HVC-AS, and M247. Four of these IPs were referenced in Sekoia’s research, which this analysis now builds upon.
IP 151.236.20.185 continues to be the only IP to communicate with the bots on remote port 7777, which we now know is a service used to provide the threat operators with a remote shell on the compromised device. This IP, therefore, remains of heightened interest due to its apparent elevated role.
The remaining six IPs communicated with the bots on remote port 11288. These connections are likely indicative of attack activity being proxied towards intended targets, as in the Microsoft 365 case referenced above.
IP 151.236.20.211 also provides a clear link to the 63256 botnet infrastructure, communicating with remote IPs over ports 63256 and 63260. This finding increases our confidence that the two bot infrastructures are linked, while also remaining siloed. To date, we have not observed any activity indicative of the 63256 botnet being utilized in offensive activities.
Conclusion
The Quad7 botnet continues to pose a significant threat, demonstrating both resilience and adaptability, even if its potential is currently unknown or unreached. Despite public reporting and efforts to mitigate its impact, the botnet remains active with a substantial number of compromised devices. Our investigation has not only confirmed the continued presence of the original 7777 botnet but also identified an expansion in the threat actor's operations, with the addition of the 63256 botnet predominantly affecting ASUS routers.
The identification of seven management IPs and their communication patterns provides valuable insights into the botnet's infrastructure and operational methods. The linkage between the 7777 and 63256 botnets, while maintaining what appears to be a distinct operational silo, further underscores the evolving tactics of the threat operators behind Quad7.
Our investigations of this infrastructure continue, and we remain focused on further understanding the targeting choices of the threat operators and any leads which may point towards an attribution. We will return at an appropriate time to provide further updates on our findings.
Recommendations
-
Maintain Up-to-Date Firmware: Users should ensure their devices have the latest firmware updates to prevent their routers from being compromised and enlisted in malicious activities.
-
Implement Robust Security Practices: Adopting strong security measures is crucial. This includes using strong, unique passwords, disabling unused services, and regularly monitoring network activity to detect any suspicious behavior.
-
Continued Vigilance and Proactive Measures: Security teams must stay vigilant and proactive. By understanding the specific hardware targeted and the communication channels utilized by botnets like Quad7, they can better defend against potential compromises.
-
Collaboration and Information Sharing: It is vital for researchers and security professionals to collaborate and share information. This collective effort is essential in the ongoing battle against botnets.
-
Utilize Advanced Tracking Tools: Users of Pure Signal Recon and Scout can track Quad7 activity by querying the IPs shared in the IOC section below or by performing advanced queries that combine the open ports characteristics discussed in this blog post.
Indicators of Compromise
The below IPs were all observed in communications with compromised hosts, inbound traffic from these IPs is indicative of enrolment in either the 7777 or the 63256 botnet.
Observed in traffic to remote ports 7777 and 11288:
151.236.20.185
Observed in traffic to remote ports 11288, 63256, and 63260:
151.236.20.211
Observed in traffic to remote port 11288:
104.168.152.139
142.11.205.164
23.227.196.73
23.254.201.175
23.254.209.118
*** This is a Security Bloggers Network syndicated blog from Team Cymru authored by S2 Research Team. Read the original post at: https://www.team-cymru.com/post/botnet-7777-are-you-betting-on-a-compromised-router
如有侵权请联系:admin#unsafe.sh