As AI continues to evolve, so do the threats against it. As these GenAI systems become more sophisticated and widely adopted, ensuring their security and ethical use becomes paramount. 0Din is a groundbreaking GenAI bug bounty program dedicated specifically to help secure GenAI systems and beyond. In this blog, you’ll learn about 0Din, how it works, and how you can participate and make a difference in securing our AI future.
What is 0Din?
0Din is an innovative GenAI bug bounty program that seeks to identify and mitigate vulnerabilities in AI systems. By harnessing the collective expertise of the global security community, 0Din aims to build a more secure AI landscape. The program rewards individuals who discover and report security flaws, ensuring that AI systems remain robust and trustworthy.
How the 0Din Bug Bounty Program Works
Participating in the 0Din bug bounty program is straightforward. Here’s a step-by-step overview:
- Identify Vulnerabilities: Participants search for security flaws within the scope defined by 0Din.
- Submit Reports: When a vulnerability is found, participants submit a detailed report outlining the issue.
- Review Process: 0Din’s team reviews the submission, verifies the vulnerability, and assesses its impact.
- Receive Rewards: Verified vulnerabilities are rewarded based on their severity and impact.
For detailed information on the vulnerability scope and processing policy, visit the 0Din Policy Page
Types of Vulnerabilities Covered
0Din covers a broad range of vulnerabilities. Here are some examples:
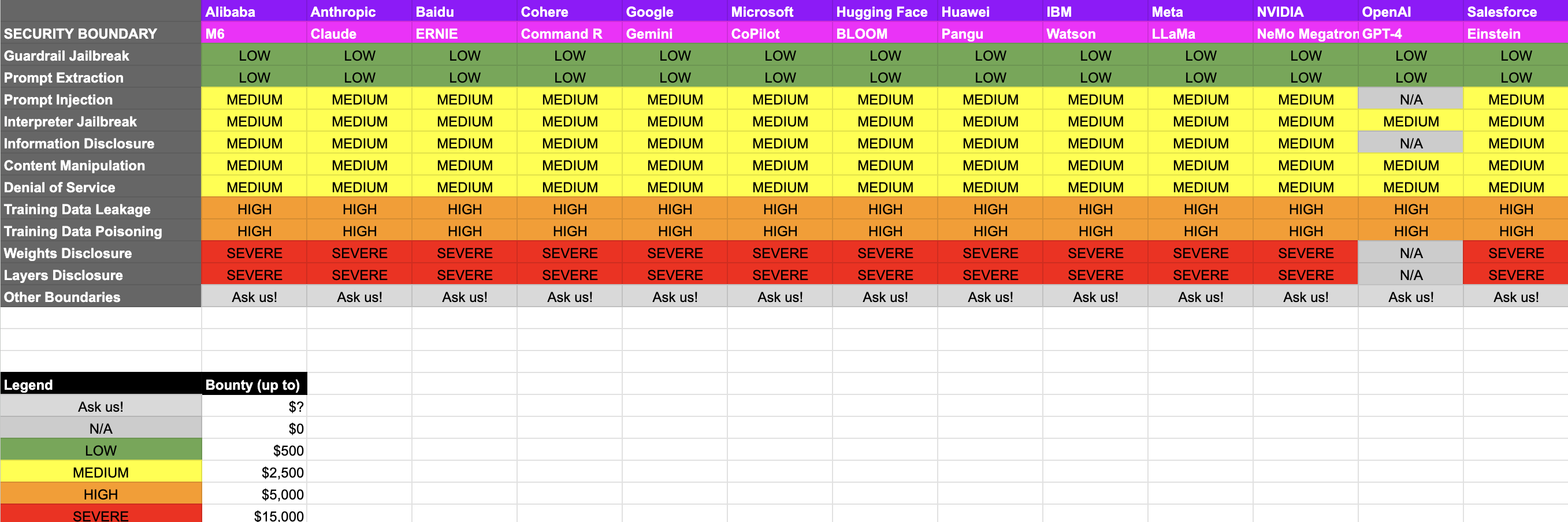
- Guardrail Jailbreak: Bypassing safety measures to make the AI perform harmful actions.
- Prompt Injection: Inserting malicious input to subvert the AI’s intended operations.
- Training Data Leakage: Extracting sensitive information from the training data used to build the AI.
Each type of vulnerability has a specific reward based on its severity, ranging from low to high. The Disclosure Mappings Guideline provides a comprehensive list of vulnerabilities and their corresponding rewards.
Eligibility and Participation
0Din welcomes participants from around the world. Here’s who can participate:
– Security Researchers: Professionals dedicated to discovering and mitigating security risks.
– Developers: Individuals with a strong understanding of AI and its underlying technologies.
– Tech Enthusiasts: Anyone with a keen interest in AI security and the technical skills to identify vulnerabilities.
To ensure a fair and effective program, participants must adhere to 0Din’s Vulnerability Processing and Disclosure Policy. This policy outlines the proper procedures for reporting vulnerabilities and ensures that all submissions are handled with integrity and respect.
Vulnerability Processing and Disclosure Policy
0Din’s vulnerability processing and disclosure policy is designed to ensure transparency and fairness. Key points include:
- Submission Review: Each submission is reviewed by a team of experts to verify the vulnerability and assess its impact.
- Response Time: 0Din commits to responding to submissions promptly, typically within a few days.
- Reward Allocation: Rewards are allocated based on the severity and impact of the vulnerability, following a predefined scale.
- Responsible Disclosure: Participants are expected to adhere to responsible disclosure practices, ensuring that vulnerabilities are reported privately and not exploited.
For a detailed policy overview, refer to the 0Din Policy Page
Conclusion
In an era where AI plays an increasingly vital role in our lives, ensuring its security is paramount. 0Din offers a unique opportunity to contribute to this critical field while being rewarded for your expertise. By participating in the 0Din bug bounty program, you can help build a safer and more secure AI future. Join us today and make a difference in the world of GenAI security.
