
2024-8-9 21:0:46 Author: www.sentinelone.com(查看原文) 阅读量:5 收藏
The Good | $39M From Mass-Scale BEC Scam Recovered & Crypto Wallet Used by Cybercriminals Seized
This week, international law enforcement efforts made major recoveries in business email compromise (BEC) scams and took down a notorious cryptocurrency platform used by threat actors.
INTERPOL’s global stop-payment system, I-GRIP, successfully recovered over $41 million stolen in a business email compromise (BEC) scam targeting a Singaporean company – the largest recovery of its kind so far. In BEC scams, cybercriminals trick companies into redirecting legitimate payments to attacker-controlled bank accounts. In this case, a Singaporean firm wired $42.3 million to what they believed was their supplier’s new account, only to realize the scam after.
INTERPOL then coordinated with Timor Leste authorities to recover $39 million and arrest seven suspects. The operation points to the growing threat of BEC scams, which according to the FBI, cost businesses $2.9 billion last year alone. Since its 2022 launch, I-GRIP has helped recover over $500 million from fraud and cybercrime worldwide.
U.S. and German law enforcement seized the domain of Cryptonator, a cryptocurrency wallet platform allegedly used for illicit activities by ransomware gangs and darknet marketplaces. Roman Boss, Cryptonator’s operator, has been indicted for money laundering and operating an unlicensed money service. Launched in 2014, Cryptonator enabled users to store and exchange cryptocurrencies but failed to implement anti-money laundering controls, allowing anonymous transactions. Cryptonator’s lax security allowed widespread criminal use, undermining regulatory safeguards.

The DoJ claims Cryptonator facilitated over $235 million in illicit transactions linked to darknet markets, scams, hacks, and other illegal activities. The platform’s primary domain has been seized, and authorities are seeking penalties against Boss, including asset seizure and damage relief.
The Bad | French Cultural Institution Hit By Cyberattack As Olympic Games Carry On
With just a few days left in the Paris 2024 Olympic games, the Grand Palais Réunion des musées nationaux (RMN) reported a cyberattack on their computer systems. The incident was identified as a ransomware attack, with cybercriminals encrypting critical data and demanding a ransom to be paid in cryptocurrency. The Grand Palais is responsible for managing several cultural sites across the country and played host to this year’s fencing and taekwondo events.

Though the attack caused some operational disruptions, particularly affecting bookstores and boutiques at other museums within the RMN network, a solution was quickly implemented, allowing affected shops to operate independently. The Grand Palais stated that it remains unaffected with no interruptions to its activities, however, there is evidence that the data stolen in the attack was caused by credentials stolen by infostealer malware. The institution is currently working with the French cybersecurity task force, ANSSI, the National Commission on Informatics and Liberty (CNIL), and the Ministry of Culture to investigate the attack.
While no cyber threat groups have come forward to claim the attack yet, Olympic-linked cultural institutions remain vulnerable despite extensive cybersecurity measures implemented by French authorities prior to the games. Experts had warned of potential cyber threats during the Paris Olympics, particularly from nation-state actors and their use of AI-based tools to craft sophisticated scams.
The month before the games commenced, researchers noted spiked increases in domains using Olympics-linked keywords and designed specifically to scam hopeful ticket buyers. The attack this past weekend serves as a reminder of the ongoing risks facing large-scale and highly publicized global events like the Olympics.
The Ugly | Chinese Threat Group Breach ISPs to Spread Malware Via Software Updates
A PRC-backed threat actor known as Evasive Panda (aka Bronze Highland, Daggerfly, and StormBamboo), was revealed this week to have compromised an internet service provider (ISP) in mid-2023 to deliver malicious software updates to targeted companies. Active since at least 2012, Evasive Panda has used backdoors like MgBot and Nightdoor to conduct cyber espionage, recently expanding its arsenal to include macOS malware called MACMA, which was first seen in 2021.
Threat researchers explained that Evasive Panda worked by poisoning DNS queries at the ISP level to redirect software update requests and deliver malware via insecure HTTP mechanisms. The attack specifically exploited weak update processes that lacked proper integrity checks, allowing the delivery of MgBot or MACMA, depending on the victim’s operating system. One instance involved deploying a Google Chrome extension on a macOS device that exfiltrated browser cookies to an attacker-controlled Google Drive account.
The attack chain shows how the threat actor was able to intercept and manipulate DNS requests and replace them with malicious IP addresses to compromise software update mechanisms. This technique was confirmed to be an adversary-in-the-middle (AitM) attack rather than a supply chain compromise, as initially speculated. The level of sophistication seen in this campaign was also observed between MACMA and another multi-platform malware called Gimmick that is linked to the Chinese threat cluster Storm Cloud targeting organizations across Asia.
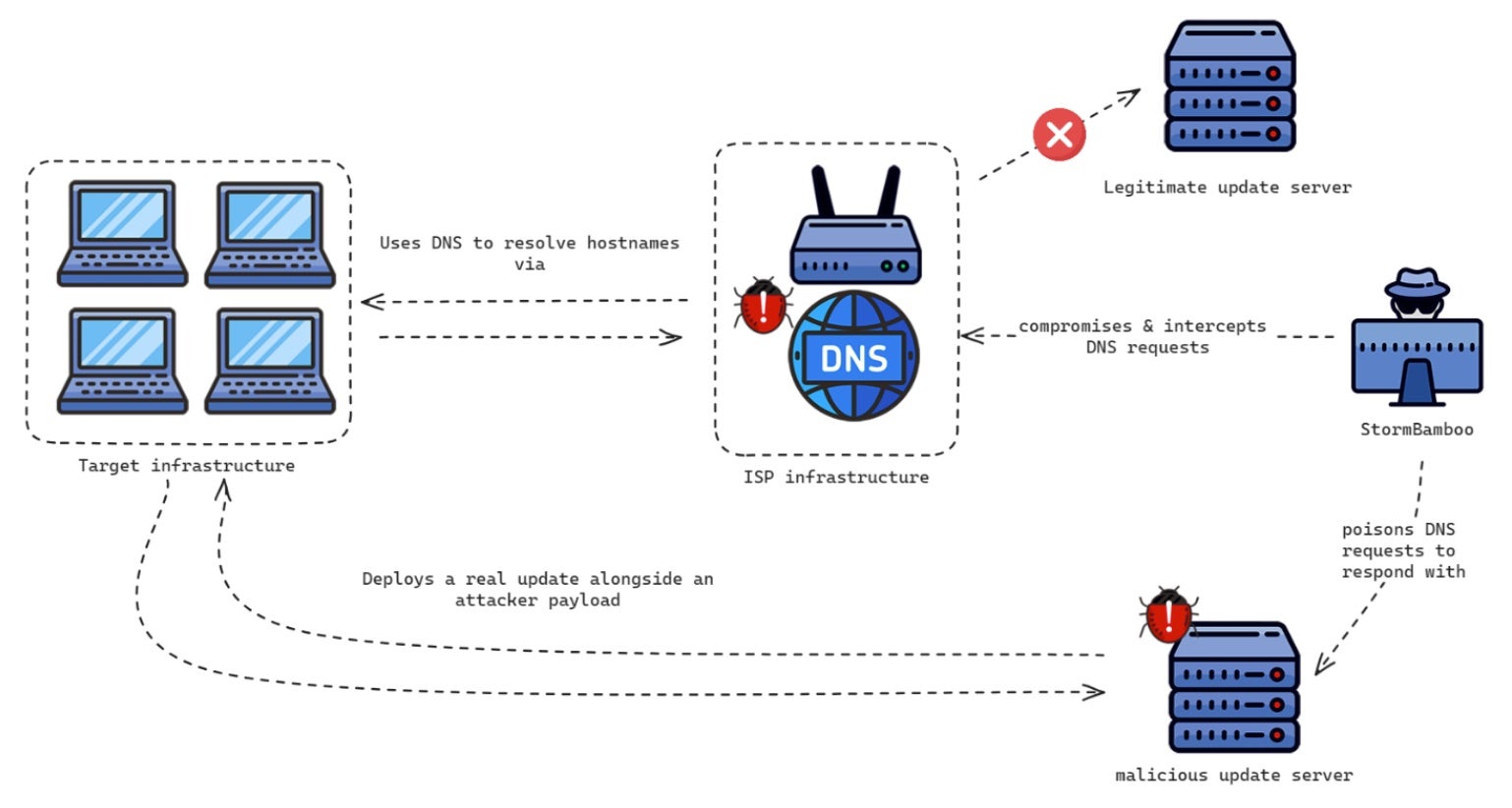
These findings underscore the critical need for stronger cybersecurity measures to protect against such advanced threats, particularly in light of the group’s demonstrated capacity to exploit vulnerabilities at the ISP level.
如有侵权请联系:admin#unsafe.sh