
2024-8-13 13:45:15 Author: securityboulevard.com(查看原文) 阅读量:1 收藏
SSL, or Secure Sockets Layer, is a protocol designed to encrypt, secure, and authenticate communications over the Internet. While SSL has been succeeded by a more recent protocol known as TLS (Transport Layer Security), the term “SSL” is still widely used to describe this technology. SSL/TLS primarily secures the communication between a client and a server, but it is also used to protect email, VoIP, and other types of communication over unsecured networks. In this blog, we will explore the recent incident on SSL/TLS certificates were revoked and it’s impact.
How Does SSL/TLS Certificates Work?
Here are the key principles to understand in order to grasp how SSL/TLS operates:
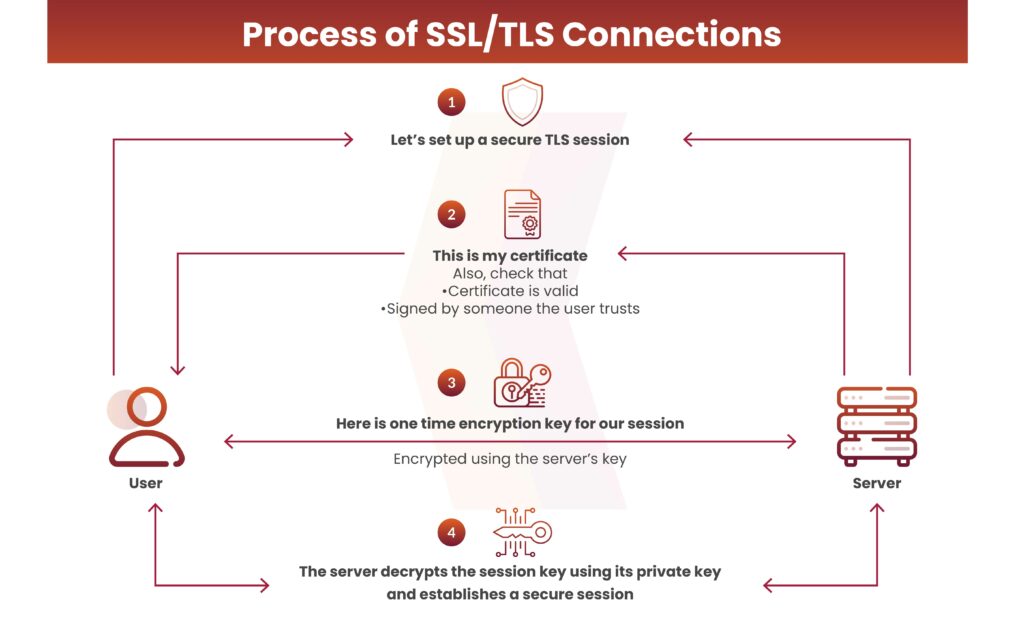
- Secure communication starts with a TLS handshake, during which the two parties establish a secure connection and exchange their public keys.
- During the TLS handshake, the two parties create session keys, which are then used to encrypt and decrypt all communications that follow the handshake.
- Each new session employs a unique set of session keys for encrypting communications.
- TLS verifies that the server side, or the website the user is engaging with, is genuinely who it claims to be.
- TLS ensures that data remains unchanged by including a message authentication code (MAC) with transmissions.
Weakness of SSL/TLS Certificates
Certificate store poisoning happens when hackers sneak into your device’s digital certificates often through malware, and plant a root certificate. This lets them pretend to be websites by sending fake responses to your requests. Putting a root certificate on your personal devices can be dangerous. It might allow others to access your stuff if the device is public or given to you by someone you don’t trust. Also, TLS certification depends on how safe Certificate Authorities (CAs) are. If CAs get hacked – like what happened with Comodo and DigiNotar in 2011 hackers can make fake certificates. Mistakes by CAs, when they make certificates, can give attackers a chance to cause trouble when you’re on shaky internet connections. Even though these risks exist, you can still trust CAs. But you need to be careful to keep the risks as low as possible.
Brief About Why SSL/TLS Certificates Were Revoked?
DigiCert has announced a mass revocation of over 83,000 SSL/TLS certificates starting 3rd August due to non-compliance with domain control verification. This action will impact around 6,800 customers, causing significant concern across the cybersecurity community. The revocation is expected to prompt urgent responses from various sectors, including critical infrastructure, as they take precautionary measures to address the potential risks associated with the revoked certificates.
One of the approved validation methods by the Certification Authority Browser Forum (CABF) requires customers to add a DNS CNAME record with a random value provided by the certificate authority, such as DigiCert. The company discovered that in some cases, the required underscore prefix was missing, making the validation non-compliant. According to CABF rules, these certificates must be revoked within 24 hours. However, the organization has delayed some revocations under exceptional circumstances to avoid disrupting critical services, with a final deadline set for August 3 at 19:30 UTC.
The Root Cause
In its root cause analysis, DigiCert identified several process failures during the creation of a new service-based system. Unlike the old system, where the required underscore was automatically added, the new architecture omitted this feature and the necessary checks. The omission went unnoticed during cross-functional reviews and regression testing, which were not scoped to detect this specific issue. The problem was discovered only after a customer inquiry, highlighting a lapse in DigiCert’s QA process, leading to significant disruptions for businesses dependent on the affected certificates.
Book a Free Consultation with our Cyber Security Experts

Mitigation Measures of the Incident
The company has enhanced its support services for affected customers, offering swift replacement of impacted services. The company is also providing resources and detailed guidance to help customers complete the process efficiently, minimizing downtime and maintaining the security of digital communications.
As the organization addresses the issue, affected customers must ensure that certificates are securely and promptly replaced. The company has reassured users of its commitment to security and transparency, vowing to learn from this incident and strengthen its systems against future threats.
Corrective Actions Taken
The company swiftly addressed the flaw and outlined steps to prevent future issues. It consolidated and reviewed all random value generators, simplifying the user experience by automating the generation of correct formats. Compliance team members are now embedded in all Certificate Authority (CA) and Registration Authority (RA) sprint teams and the company is expanding its test coverage to include compliance-based automated tests. Later this year, DigiCert plans to open source DCV for community review.
However, Info-Tech Research Group’s Chagnon criticized DigiCert, stating that the company’s issue has burdened customers with production outages due to certificate revocations caused by the problem. Connolly acknowledged that human errors in design and maintenance can impact infrastructure, highlighting the significant effects when such systems fail.
Conclusion
The recent incident involving DigiCert’s mass revocation of SSL/TLS certificates underscores critical vulnerabilities in certificate management and validation processes. While DigiCert has acted swiftly to mitigate the impact by enhancing support services and taking steps to prevent future issues, the situation highlights the importance of robust QA processes and adherence to compliance standards. Despite the company’s efforts to address the flaw and reassure customers, the incident has caused significant disruptions, illustrating the broader implications of weaknesses in digital security infrastructure. As the cybersecurity community continues to adapt, ongoing vigilance and proactive measures will be essential to safeguard against similar issues in the future.
As a CERT-In empanelled organization, Kratikal is equipped to enhance your understanding of potential risks. Our manual and automated Vulnerability Assessment and Penetration Testing (VAPT) services proficiently discover, detect, and assess vulnerabilities within your IT infrastructure. Additionally, Kratikal provides comprehensive security auditing services to ensure compliance with various regulations, including ISO/IEC 27001, GDPR, PCI DSS, and more, assisting your business in adhering to legal requirements set forth by diverse governments.
FAQs
- Why is SSL/TLS required?
SSL/TLS certificates improve SEO security. That’s why most major browsers require TLS/SSL certificates.
- What is the benefit of SSL?
One of the primary advantages of SSL certificates for websites is their ability to enhance data security. By utilizing cryptography, they ensure secure connections between the browser and server, safeguarding data during transmission.
The post An Overview: Why are SSL/TLS Certificates Getting Revoked? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/an-overview-why-are-ssl-tls-certificates-getting-revoked/
如有侵权请联系:admin#unsafe.sh