― If it sounds too good to be true, it probably is.
As digital currencies have rapidly grown, so have cryptocurrency scams, presenting significant risks to crypto investors and users. These scams often attract individuals with promises of high returns or use sophisticated schemes to defraud even the most cautious. Understanding these scams is crucial for protecting potential victims and safely navigating the evolving cryptocurrency scene. With the advent of artificial intelligence (AI) and deepfake technology, scams exploiting famous personalities and major events have significantly increased since these technologies enable the creation of realistic but fake videos. Consequently, dozens of scams try to leverage the popularity and credibility of celebrities or significant events to deceive as many people as possible.
Scammers use various media to distribute fake pages and videos. By using different platforms, they can reach a large audience and increase the probability of attracting more people with fraudulent content. The first documented medium used by scammers for this purpose was X, at the time Twitter, in 2018. Specifically, scammers took over three popular and verified Twitter accounts of British fashion retailer Matalan, film distributor Pathe UK, and US publisher Pantheon Books. The attackers used Elon Musk’s name and likeness to promote a fraud ad via Tweets. [1]. Since at least 2019, hackers have also been hijacking high-profile YouTube channels to broadcast cryptocurrency scams.
In an effort to combat these hijacks, Google has spent considerable time researching techniques used by hackers-for-hire that were used to compromise thousands of YouTube creators. Nevertheless, this has not completely stopped scammers, who still manage to hijack accounts from time to time [2, 3]. The issue gained enough importance to attract the interest of other researchers, motivating several scientific publications that tried to address the issue of crypto scams on various platforms, starting from the aforementioned YouTube and Twitter and including other platforms that have gained prominence in recent years, such as TikTok, Telegram, and WhatsApp [4-9].
It is to no one’s surprise that these sources describe very similar modus operandi and associated techniques across all these platforms. The deepfakes utilizing AI are naturally becoming key instruments in crypto scam campaigns. In recent years, there has been an increasing incidence of one specific scam based on giveaway events announced by abused events and well-known personalities. The group we dubbed CryptoCore has become famous for its sophisticated tactics and successful exploitation of unsuspecting victims. This scam group and its giveaway campaigns leverage deepfake technology, hijacked YouTube accounts, and professionally designed websites to deceive users into sending their cryptocurrencies to the scammers’ wallets.
This report delves into the intricacies of the CryptoCore group’s scam and analyses their modus operandi. We will describe key exploited events, including hijacked YouTube accounts and deepfake videos, alongside a technical analysis of the fraudulent sites. One purpose of this study is to present a fundamental analysis – and key statistics – of fraudulent wallets that have received profits in the millions of dollars, as well as provide statistical data on detections, showing how victims are lured into suspicious websites and ultimately end up crypto scam victims.
By gathering information and insights on the CryptoCore group’s operations and giveaway scams to better understand how they operate and how they manipulate victims, we hope to help counter their operations and protect the digital world.
Table of Content
- Modus Operandi
- Reconstructing the Scammers’ Operation
- Crypto Wallet Analysis
- Hijacked YouTube Accounts
- Video Policy & Providers’ Safeguards
- Abused Events
- Use of Deepfake Videos
- Technical Analysis
- Detections
- Conclusion
Modus Operandi
The primary attack vector relies on a simple exploitation of trust in established brands and famous individuals as well as the interest in major cultural and political events. The most common method is convincing a potential victim that messages or events published online are official communication from a trusted social media account or event page, thereby piggybacking on the trust associated with the chosen brand, person, or event. This initial vector usually directs the victim to a fake website that promises quick and easy profits. To pressure the victim even more, they often use limited time “giveaway” offers that urge the person to complete a quick action. Otherwise, they will allegedly lose the opportunity for a quick profit.
The initial attack vector most commonly manifests as events where famous people invest a certain sum of money to raise awareness about an allegedly promising cryptocurrency that targets new cryptocurrency users. They often try to add further confusion and make the distinction more difficult by associating themselves with actual events, usually related to technology, such as space flights or fake seminars focused on cryptocurrencies.
The success of the CryptoCore group is driven by their extensive preparation before an abused event, sophisticated infrastructure, and ability to expose fraudulent content to as many people as possible via popular social platforms.
Before publishing malicious content, usually a video with a QR code linking to a fraudulent website, attackers must set up an environment for sharing their content, which, if successful, will lead victims to the fake page. They need to hijack an account with many subscribers/followers. Documented cases of successful hacks on YouTube users with large follower bases usually begin through phishing or malware in emails; the malware can then steal the session or credentials. The phishing email might inform the account holder, for instance, about changes in YouTube’s terms or propose cooperation in advertising on the account holder’s YouTube account [2]. A similar approach is used for account holders on other popular social platforms.
The attackers prepare deepfake content in advance and wait for an opportunity that can attract a larger audience. On the day of the event, they modify the account by changing the background and description and adding fake content to enhance authenticity. Finally, they wait for victims to search for the official event. Given the high number of subscribers of the hijacked account, there is a high probability that the search results will predominantly show fake content. Keywords related to the targeted events, combined with a large number of followers/subscribers, place hijacked accounts in the top search results.
Once the victim is convinced that this is a unique event, they are redirected to the fraud website, which is highly professional-looking including “technical support” available via online chat. Additionally, the instructions, rules of the “unique event”, and crypto wallets are present on the website, including a fake transaction system to make the page appear more legitimate. The catch is that – if the victims send the money – there is no way to retrieve it back.
Reconstructing the Scammers’ Operation
Based on the assessed modus operandi, we see strong indications of a large and complex scam operation using a vast array of techniques and scam methods. Their techniques utilize several key tools essential to their campaigns’ success.
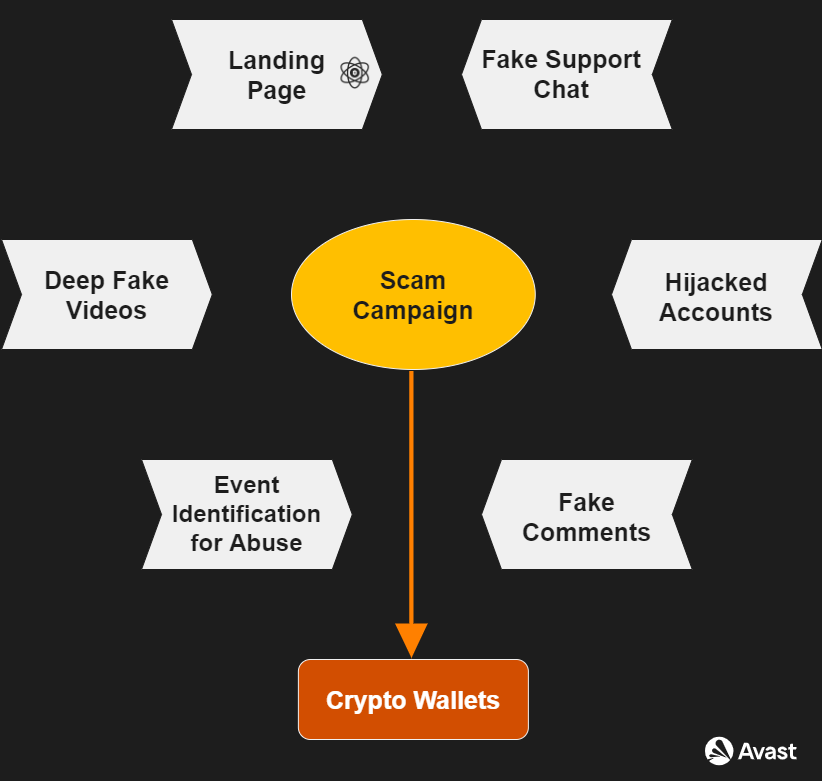
The first step is to attract the largest audience and potential victims. To do this, the group identifies significant events that will be widely publicized and accompanied by live broadcasts. The second step is creating a deepfake video mimicking official event video and abusing the events via embedded QR codes that lead to fraudulent websites. Technical analysis proves these scam websites are generated using the same patterns and framework.
Once the fake videos and websites are ready, the attackers distribute them using compromised accounts from popular platforms, especially YouTube. Therefore, another crucial part of the operation is procuring these compromised accounts because accounts with many subscribers increase the probability of attracting victims. In addition, fake comments also supplement the distribution of the abused event. Finally, the successful campaign results in collecting cryptocurrency wallets with fraudulently obtained crypto coins.
Search Engines
We have figured out how victims are led to fake videos or hijacked accounts; it is a crucial part of the scammers’ operation because it is primarily designed to be multiplatform. The initial phase is observed mainly on desktop platforms, while the landing page is directed towards smart devices via QR codes.
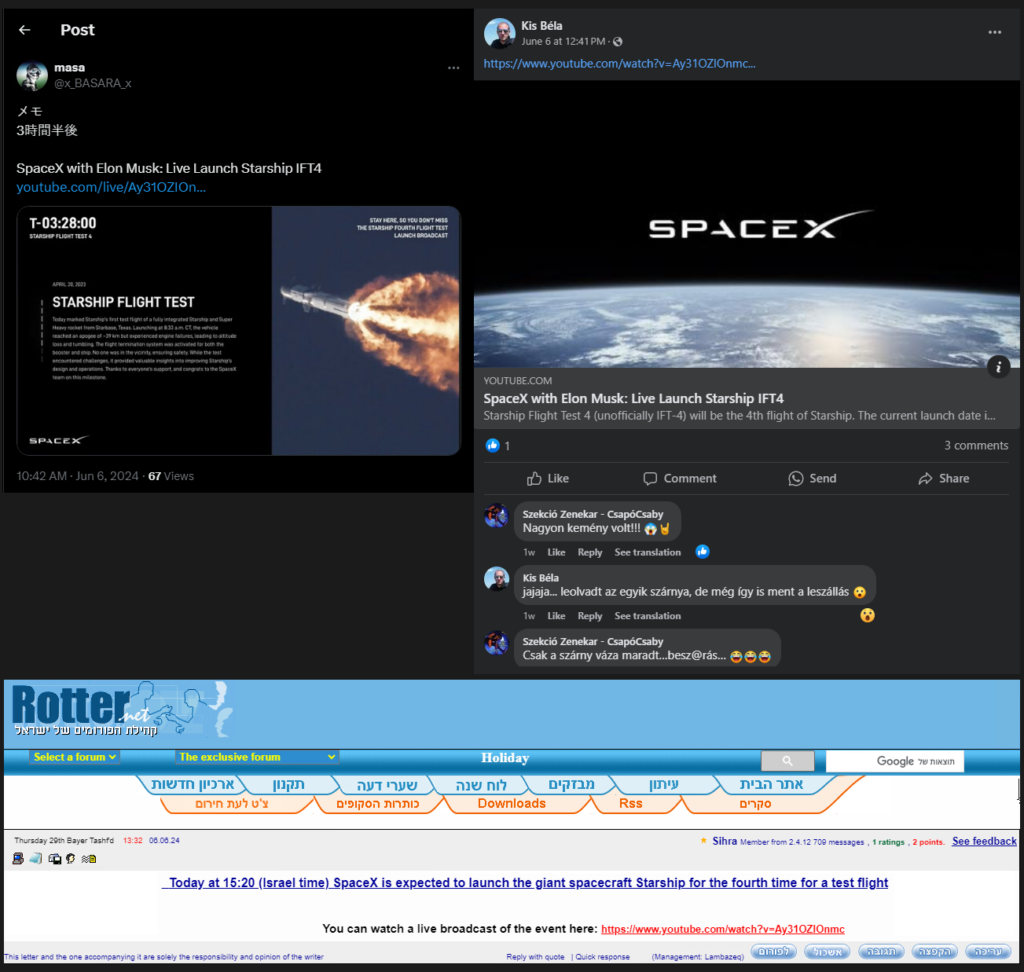
Most victims reach the fraudulent videos by searching for keywords related to the exploited events in popular search engines, such as “spacex starship launch 4“, “starship flight test“, and “start starship“. Another direct access point is searching for keywords directly on YouTube, such as “eclipse 2024 totality“, “integrated flight test four“, and “spaceship“. In addition to direct searches, we have observed fake or misused comments on various forums and posts on platforms X, Facebook, and Twitch. See examples below.
CryptoProject in Scammer Operations
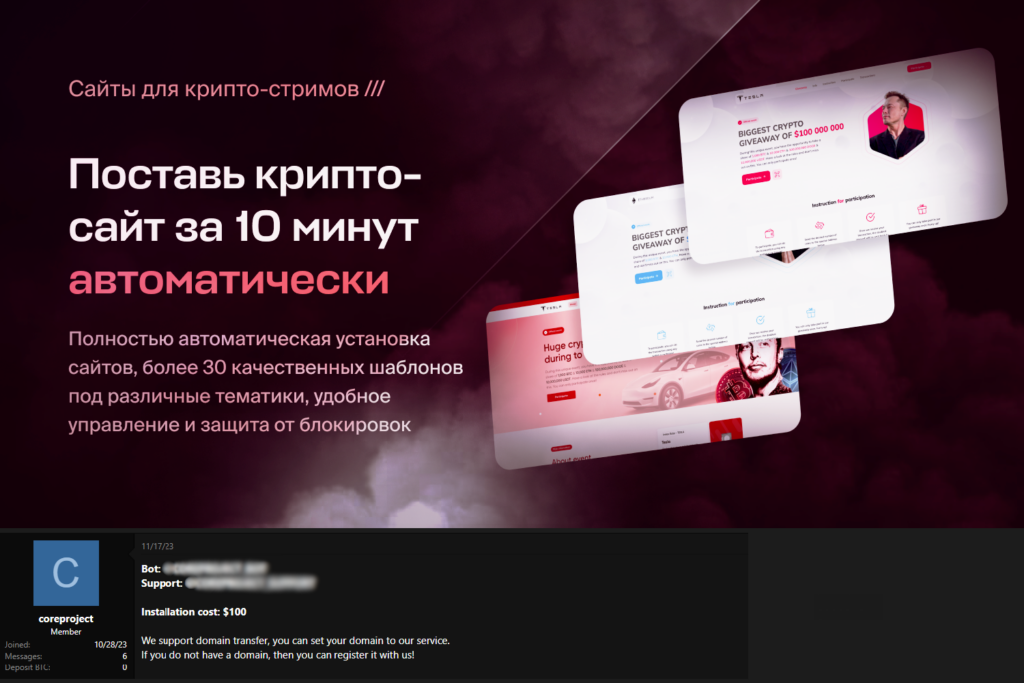
We have named the scammer group after the framework used to generate the landing pages – CryptoCore. However, the campaigns might be the result of collaboration between several independent cybercriminal groups, possibly through subcontracting.
Landing pages are created using a framework advertised on various hacker forums under the brand CryptoProject. The developers offer deployment on personal domains for approximately $100 and even showcase examples of the giveaway campaigns that we have been monitoring, as illustrated in the images below. Orders for specific pages can be placed via their dedicated Telegram bot.
Interestingly, deepfake videos and even stolen accounts or comments can be procured in a similar way. That means that all the necessary tools are available as a service. This leads to the natural question of whether the whole scam campaign can be procured via a service and the client only needs to supply crypto wallets (basically Scam-as-a-Service), or rather, this is the work of a single group potentially subcontracting parts of its campaign.
Regardless, we can assert with high confidence that landing pages are created using a framework that is available as a service, presumably we could probably extend this assessment even to its parts, such as deepfake videos, hijacked accounts, and fake comments. Further research is needed to reveal more details about other links, especially on the fraudulent crypto wallets, which could rule out one of these options.
Crypto Wallet Analysis
Over a six-month timeframe analysis, we found hundreds of crypto wallets with millions of dollars in turnover. However, it is essential to note that adding up all incoming transactions for each wallet is insufficient to determine the final value because it is necessary to deduct outgoing transactions in BTC from the same wallet. We also recorded large transactions unrelated to any giveaway campaigns, presumably representing transfers between the scammers’ wallets. Nevertheless, the wallets evidently belong to the attackers and not to a middleman. Therefore, the following statistical data on crypto wallets is not exact but provides a basic overview of the approximate range of revenues generated from the group’s illegal activities.
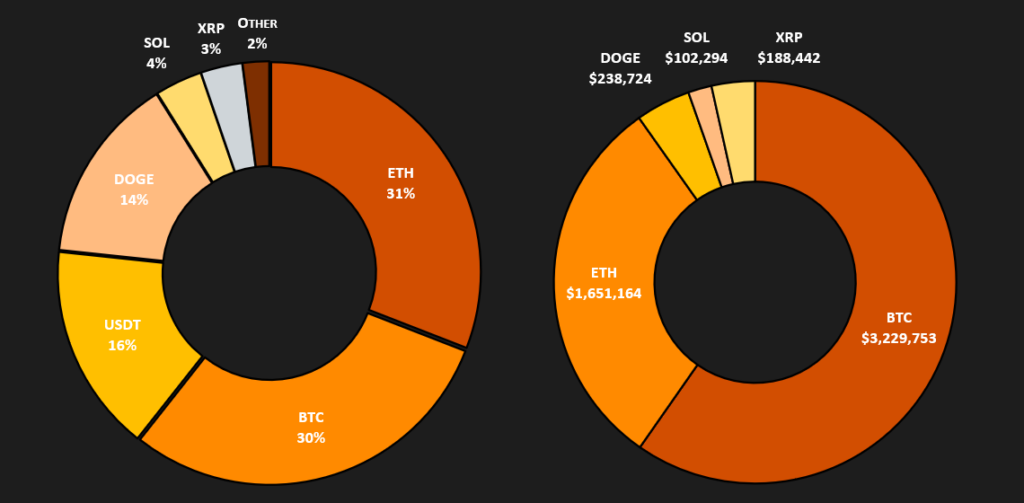
In total, we detected 1200 crypto wallets, with the most frequently used currencies being Ethereum, Bitcoin, Tether, and Dogecoin, as shown in the graph below.
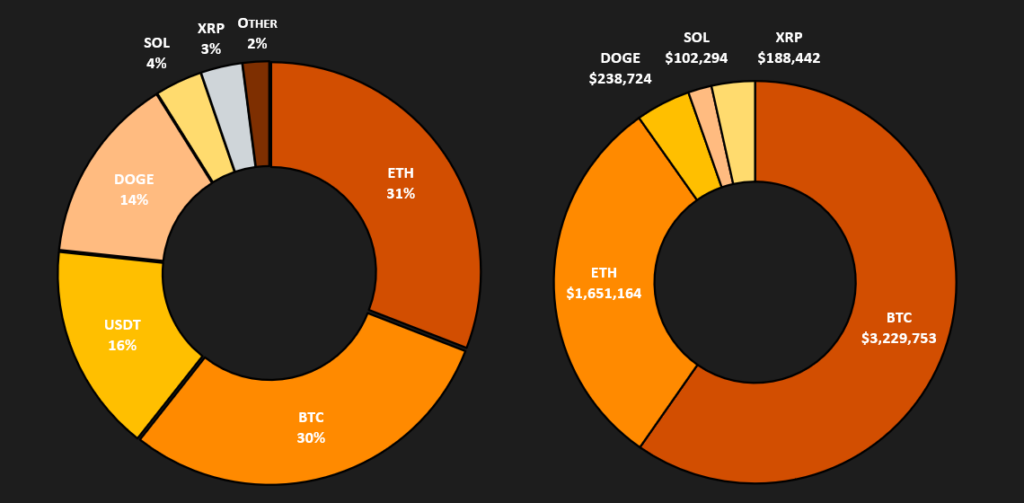
These wallets had a turnover of approximately $5,400,000. The table below summarizes the transaction details for each wallet. In absolute values, Bitcoin wallets represent the largest share of the total turnover due to Bitcoin’s high value, with Ethereum wallets coming in second. The complete list of collected crypto wallets can be found in the IoC section below.
| Wallet | Value |
| BTC | $ 3,229,752 |
| ETH | $ 1,651,163 |
| DOGE | $ 238,724 |
| SOL | $ 102,294 |
| XRP | $ 188,441 |
| $ 5,410,377 |
Hijacked YouTube Accounts
Since YouTube remains the most popular video-sharing platform with billions of users worldwide, scammers actively exploit its authentication mechanisms. Previous analyses and blog posts have recorded hundreds of suspicious accounts. The most hijacked accounts can be accounted for by two cases, one with 19 million subscribers and another with nearly 12 million [4, 10]. During our observations, accounts with 5 million subscribers were not uncommon. Such high subscriber counts allowed scammers to appear in the top 10 search results.
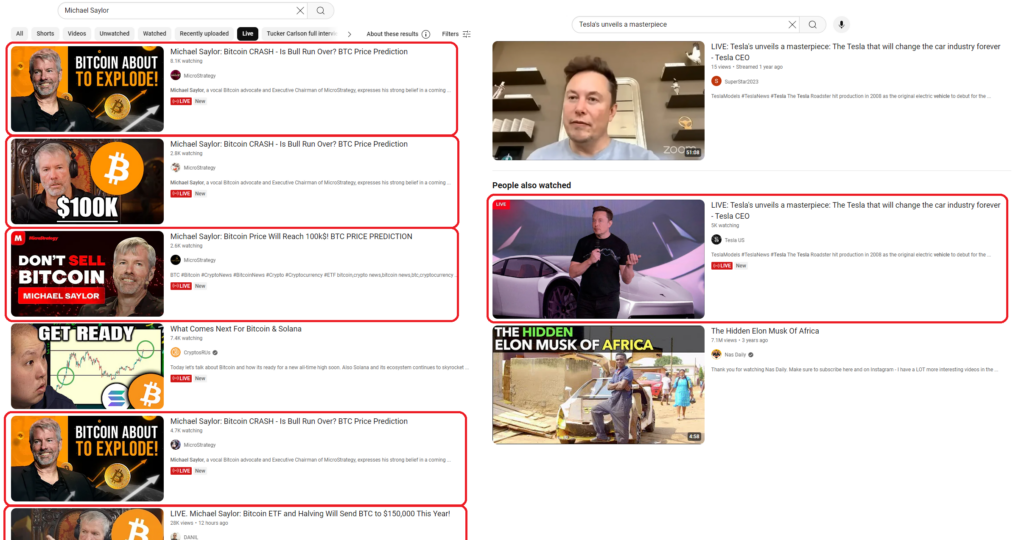
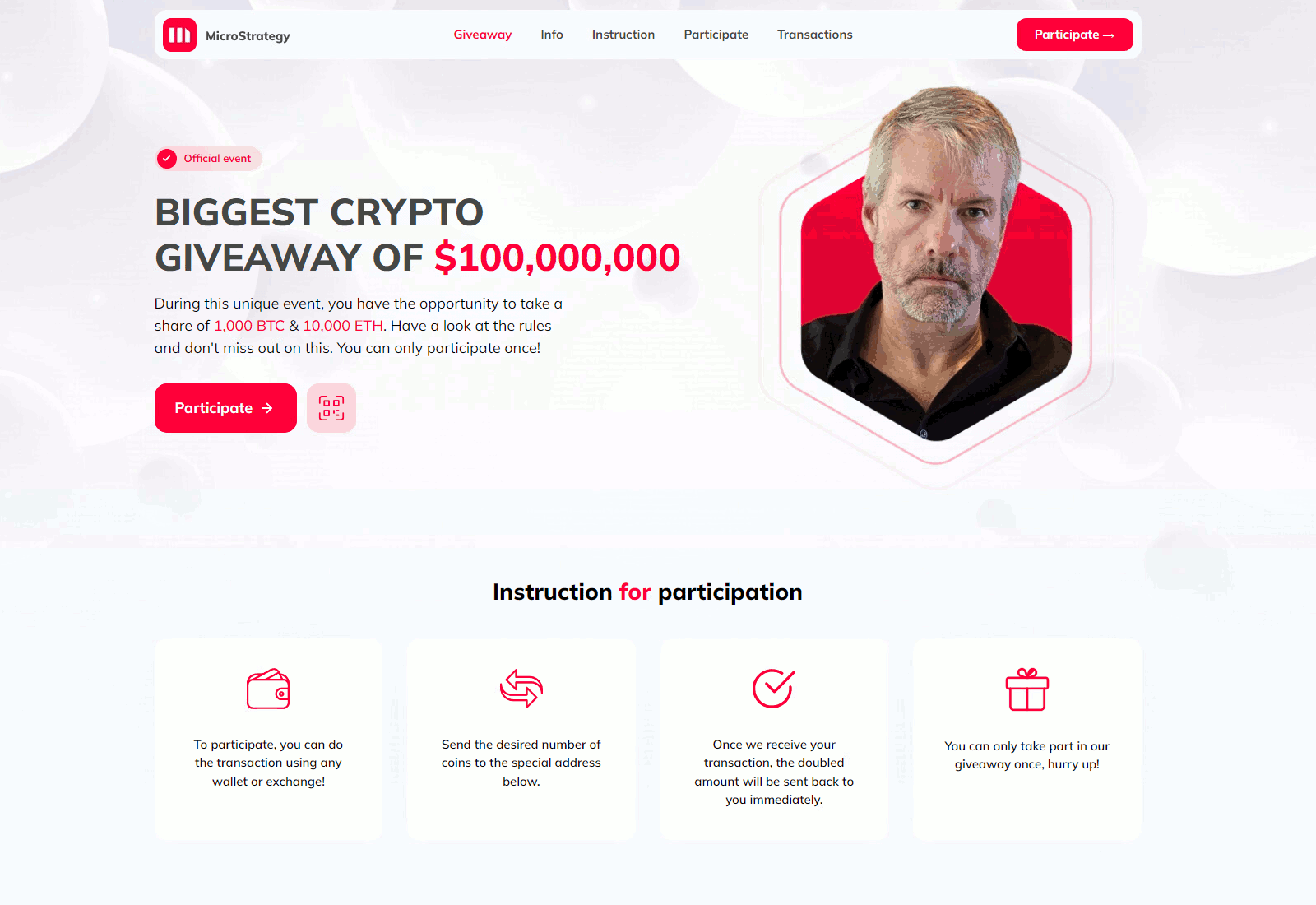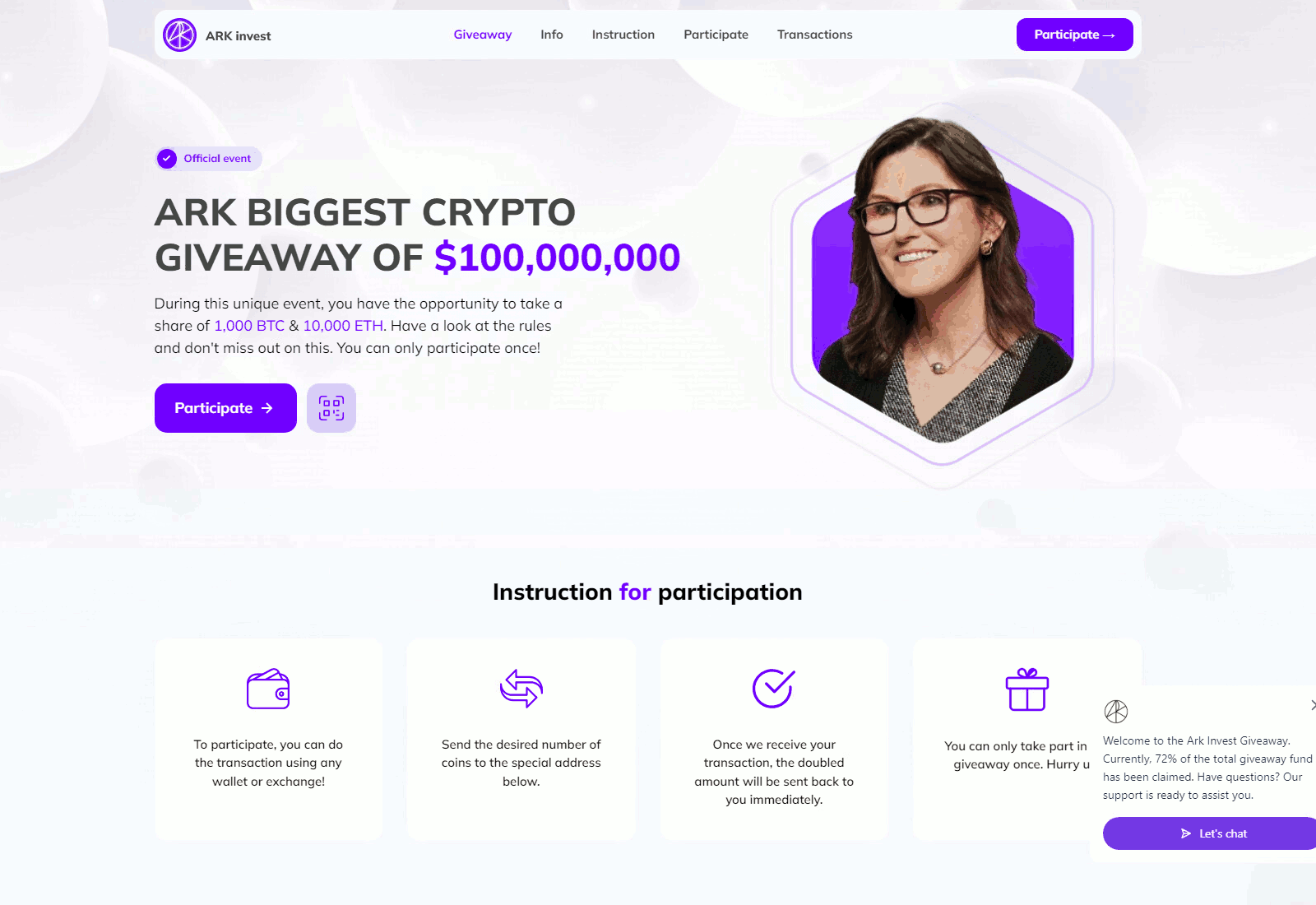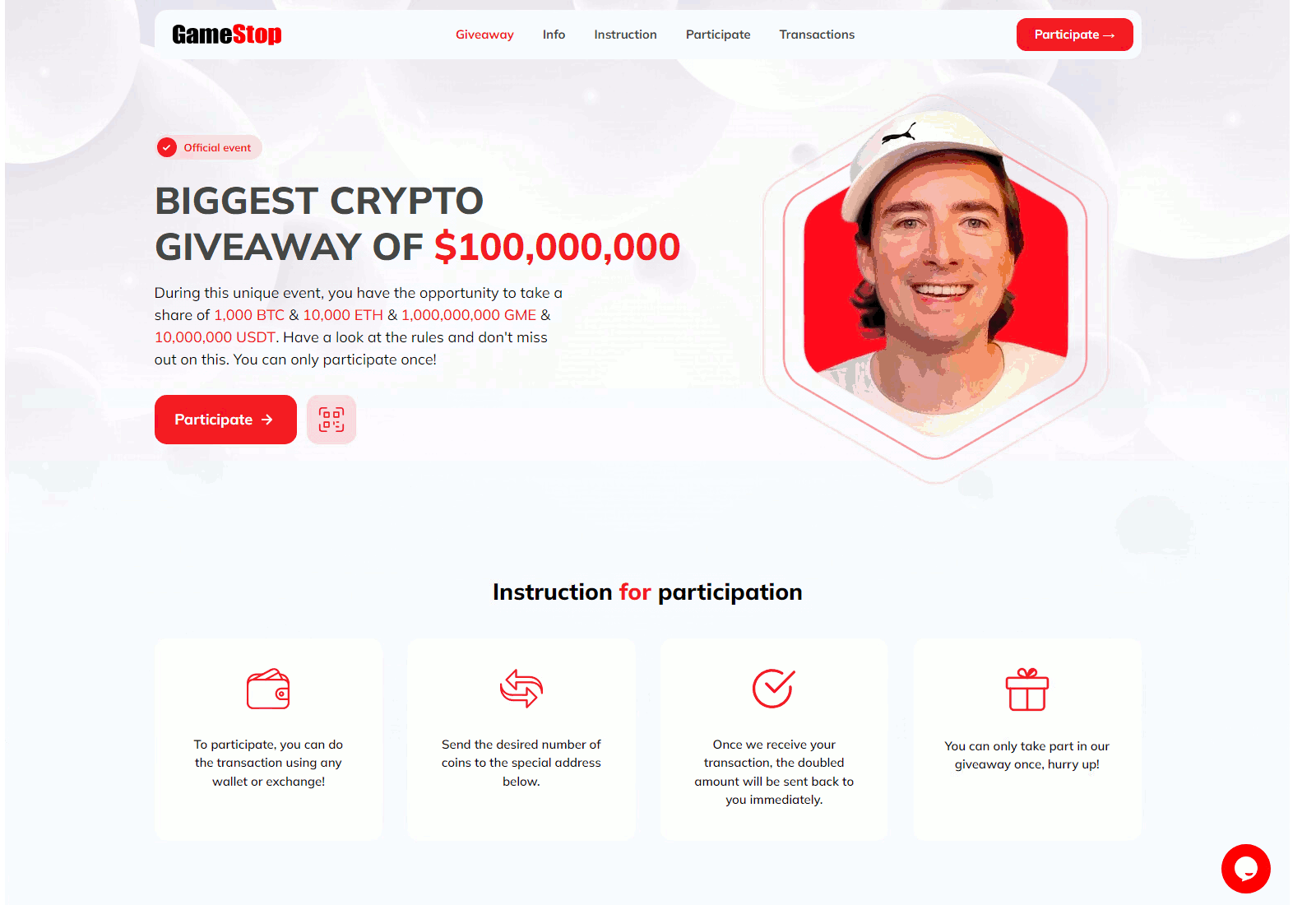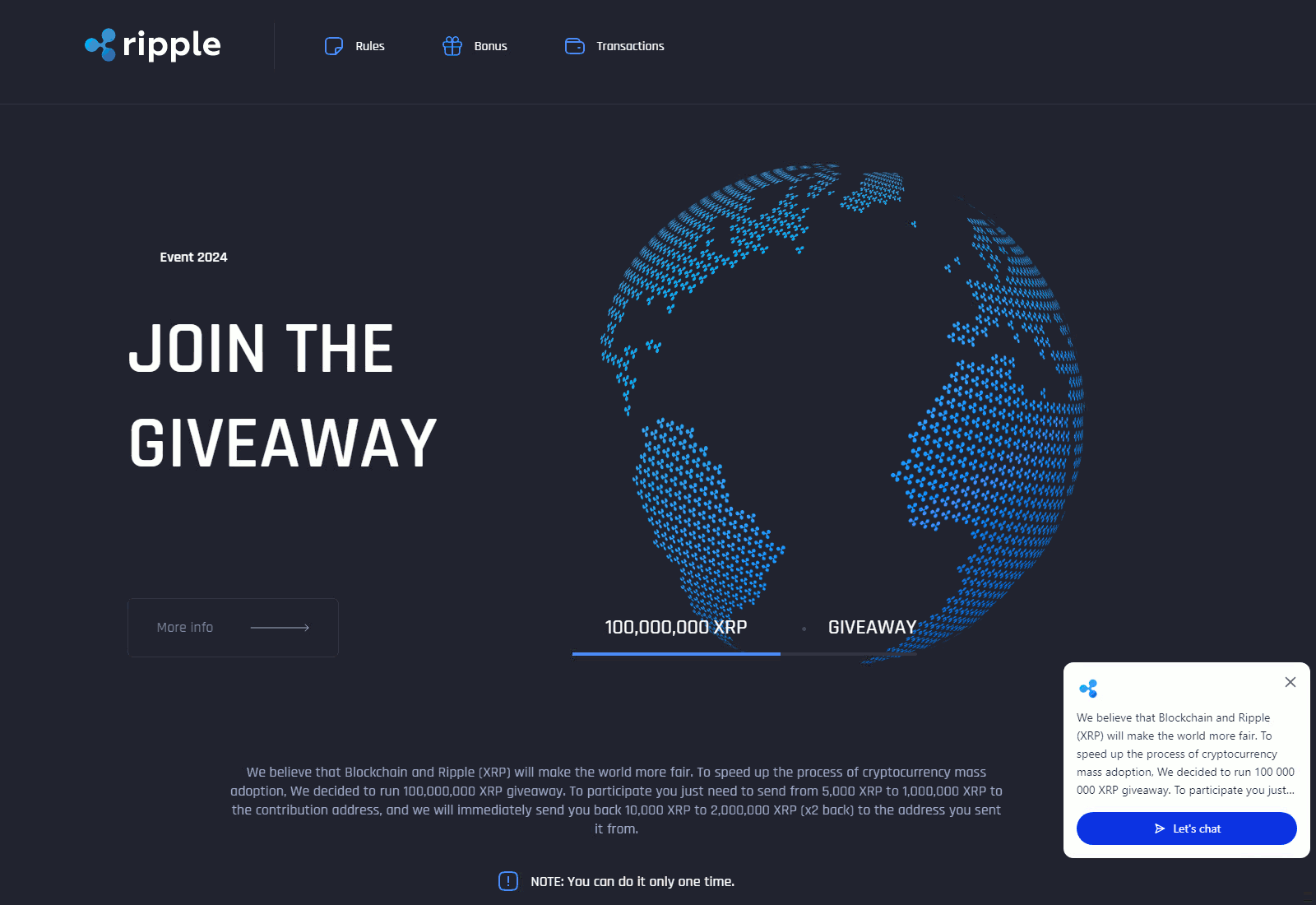
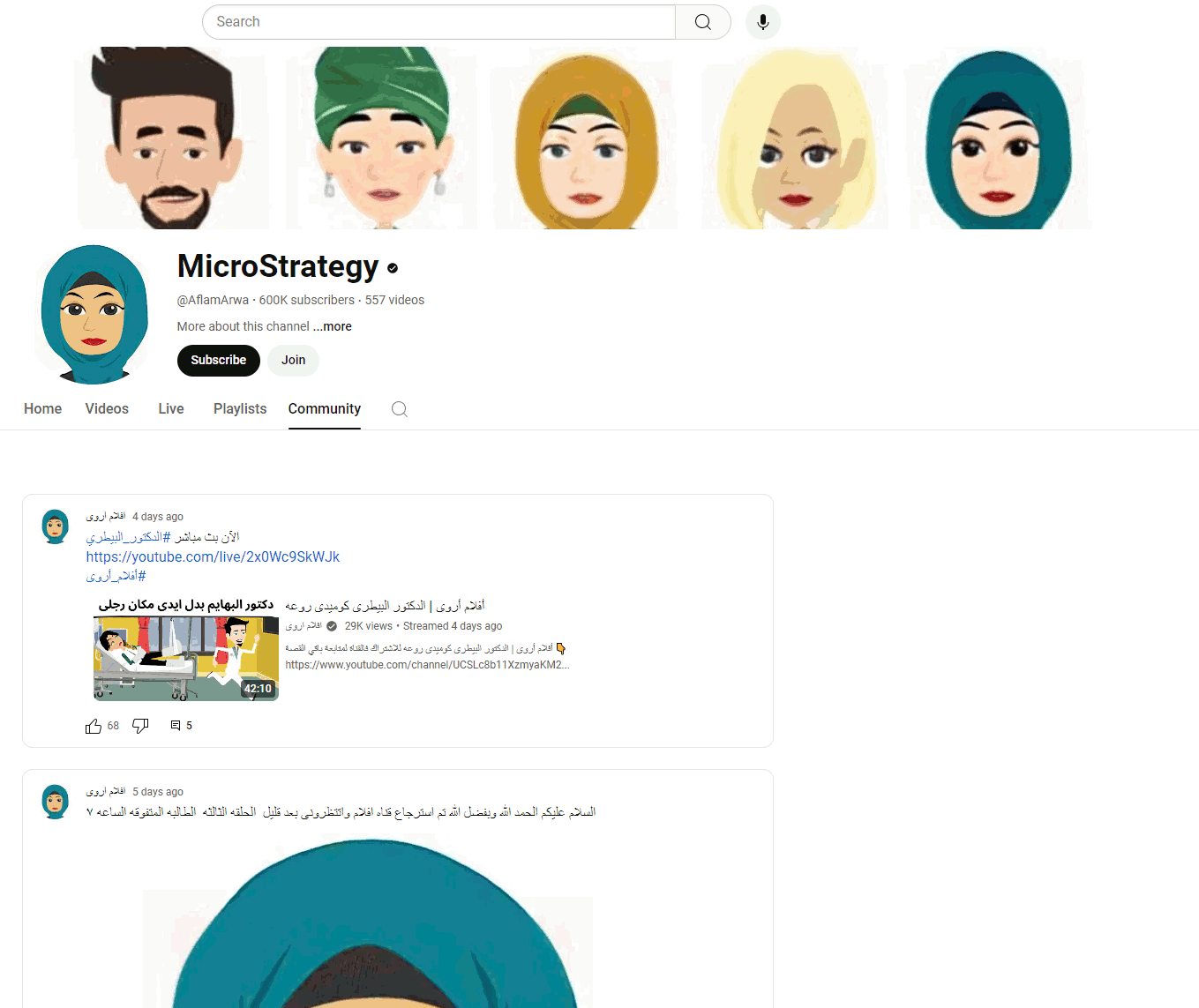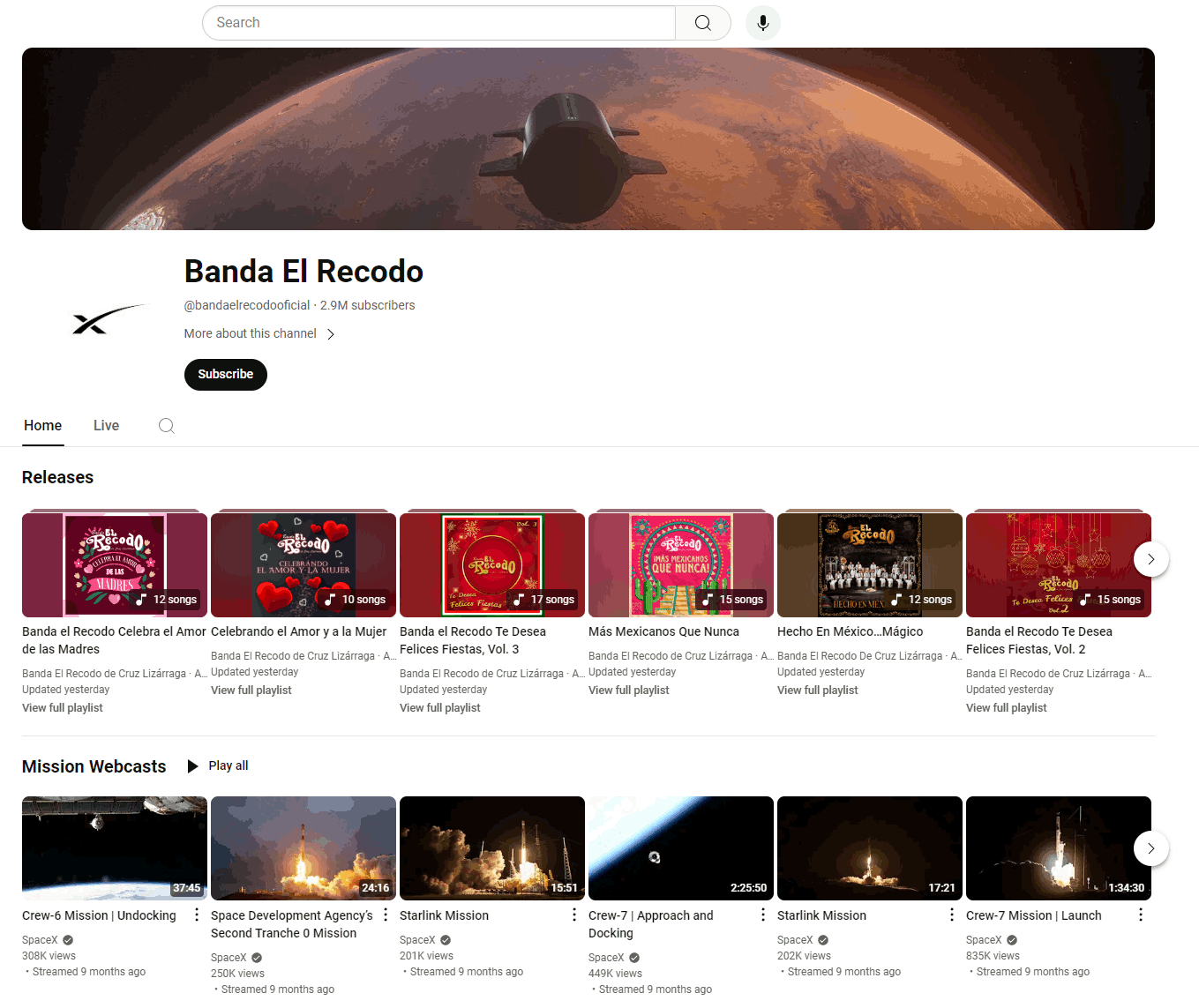
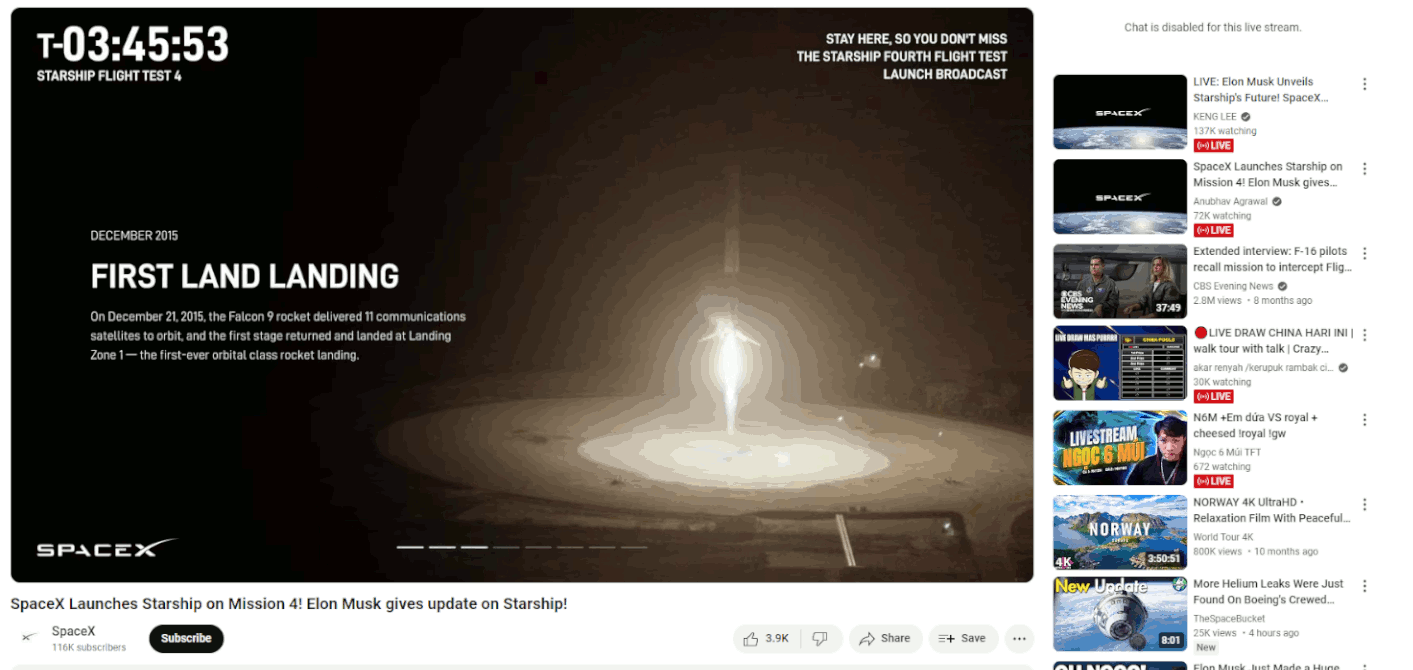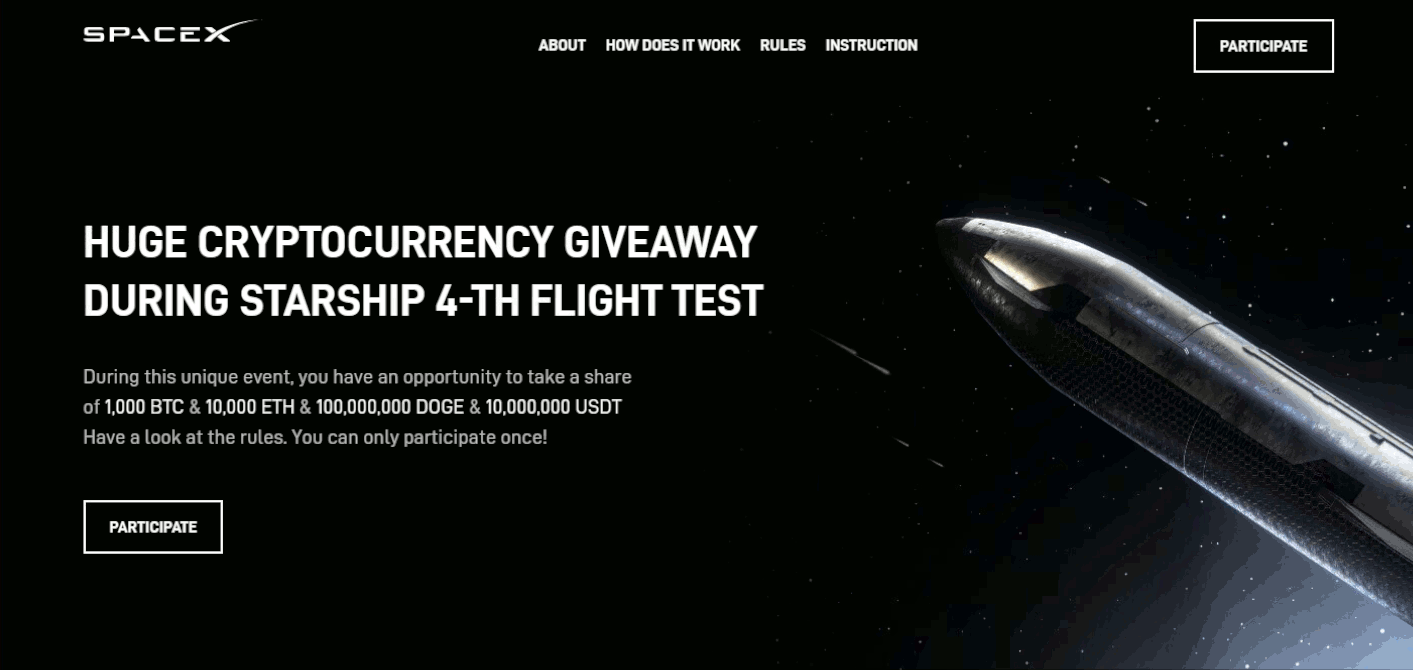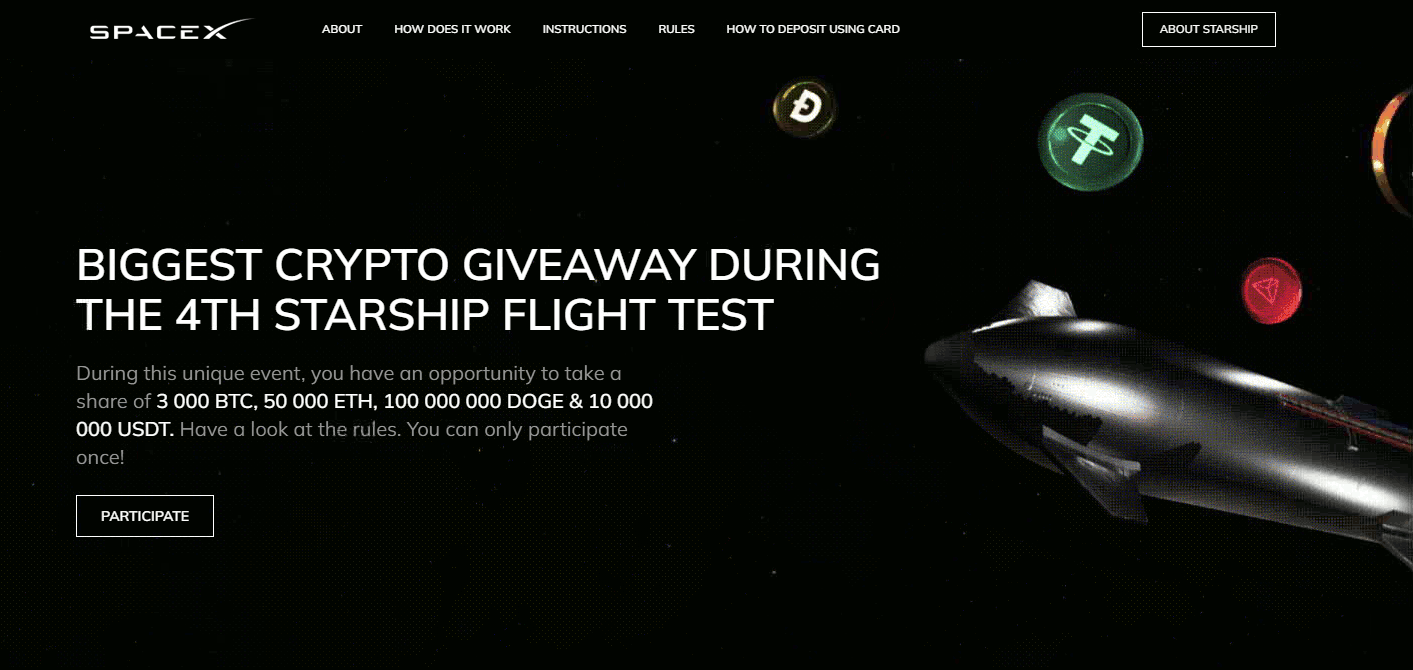
While the channels evade YouTube’s detections (and subsequent blocking), they are thematically adjusted to suit the current campaign’s needs. One channel might have channel names like MicroStrategy, Tesla, SpaceX, Ripple, etc. Typically, the background image, channel name, description, and alias (e.g., @RippleXRP24, @MicroStrategys) are changed, often relying on typo-squatting to confuse victims. Attackers also switch the original owner’s videos to private and upload their own content, consequently making the account look as credible as possible, even with verified status and a large subscriber base.
It is evident that these are massive attacks on YouTube accounts with high subscriber counts. If scammers are not targeting a specific event, we observe several hijacked accounts daily, usually themed as MicroStrategy or XRP. However, on the day of a significant global event such as the SpaceX launch, the number of active stolen accounts can rise to dozens.
Individual accounts are blocked or removed by YouTube for violating rules, but not in most cases. Moreover, many misused accounts can only be parked, and some remain active for the next promising event. Therefore, the parked accounts can be used in multiple CryptoCore campaigns before they are blocked. Victims often report that proving account ownership to YouTube is very difficult. Moreover, accounts can be blocked or permanently deleted, including all content. Given the large number of subscribers, the result is a significant loss for the victims, as they have built their profiles over many years.
As mentioned in modus operandi, the accounts are stolen through phishing or malware spread via emails. Previous studies have considered that attackers are shifting away from Gmail to other email providers, primarily using email.cz, seznam.cz, post.cz, and aol.com [2]. One documented case involved cookie theft, giving the attacker access to the account without needing the username, password, or two-factor authentication [11]. In addition, it is also possible that attackers purchase credentials on the dark web.
Hijacked YouTube Account Statistic
We do not aim to provide a complete statistical analysis of YouTube accounts due to the limited scope of analyzed accounts. However, more than 20% of hijacked accounts in our sample had over a million subscribers. The largest shares, approximately 36%, were accounts with 100K to 500K subscribers. So, the vast majority of stolen accounts have a huge number of followers, especially when we consider that MicroStrategy’s official YouTube account has “only” 39.1K subscribers.
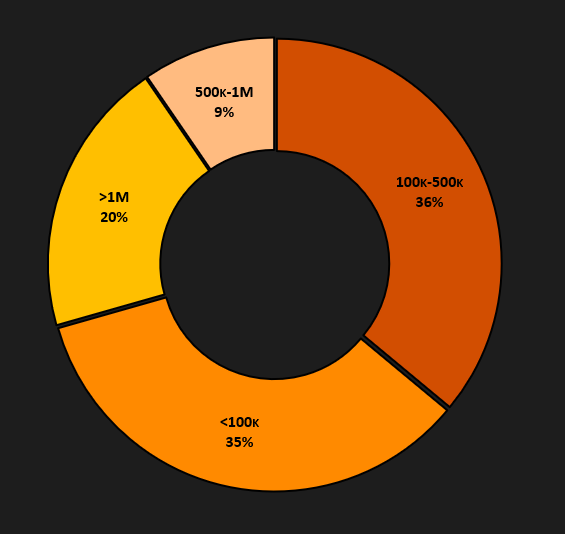
Such high subscriber numbers can be beneficial by boosting search results, resulting in both increased visibility as well as credibility. Regarding topics, most accounts tried to associate themselves with SpaceX events, with the second most popular being MicroStrategy which has been a CryptoCore staple for quite some time. The third significant topic is Ripple. However, we must consider noise in the statistics, as the content may change over time, and a single account can cover multiple topics. To illustrate the scale, the number of viewers for live streams of deepfake videos often reaches into the hundreds of thousands.
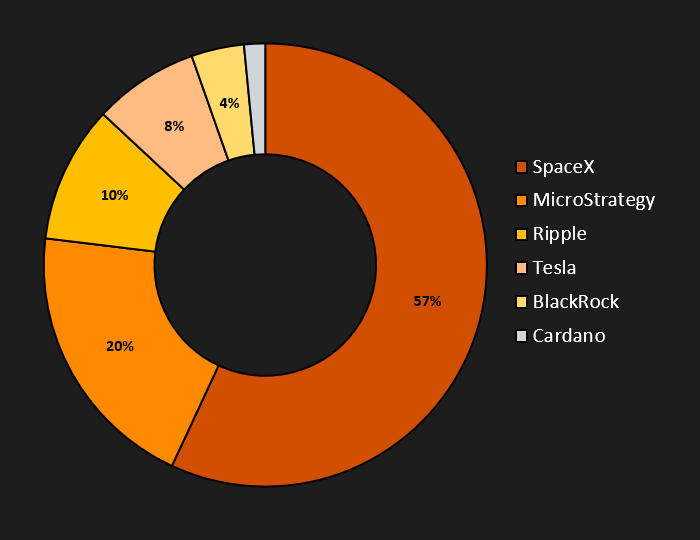
Hijacked YouTube Examples
We witnessed many modifications made to hijacked accounts during this research. The method of manipulation remains consistent, so we will provide one specific example of how the attackers operate and misuse the compromised accounts.
The prime example involves an abused YouTube account with many subscribers (1.46M), fortunately with a happy ending. This account was compromised on May 20, 2024, and rebuilt into an “official” MicroStrategy channel, including modification of the background image and description and uploading videos from MicroStrategy’s official website. The victim’s original videos were hidden or selected as private.
If someone searched for the keyword “MicroStrategy”, the hijacked account appeared second in the result list. However, the channel’s original name remained in the search list despite being renamed. The video contained a well-known deepfake video with a QR code leading to the very familiar fake page. Interestingly, one of the original posts from the victim’s YouTube channel remained on the Community tab; see the animation below. Additionally, we utilized this error to communicate with the support team, as documented in Case 2: Suspicious YouTube Channel. Finally, the hijacked account was terminated the next day.

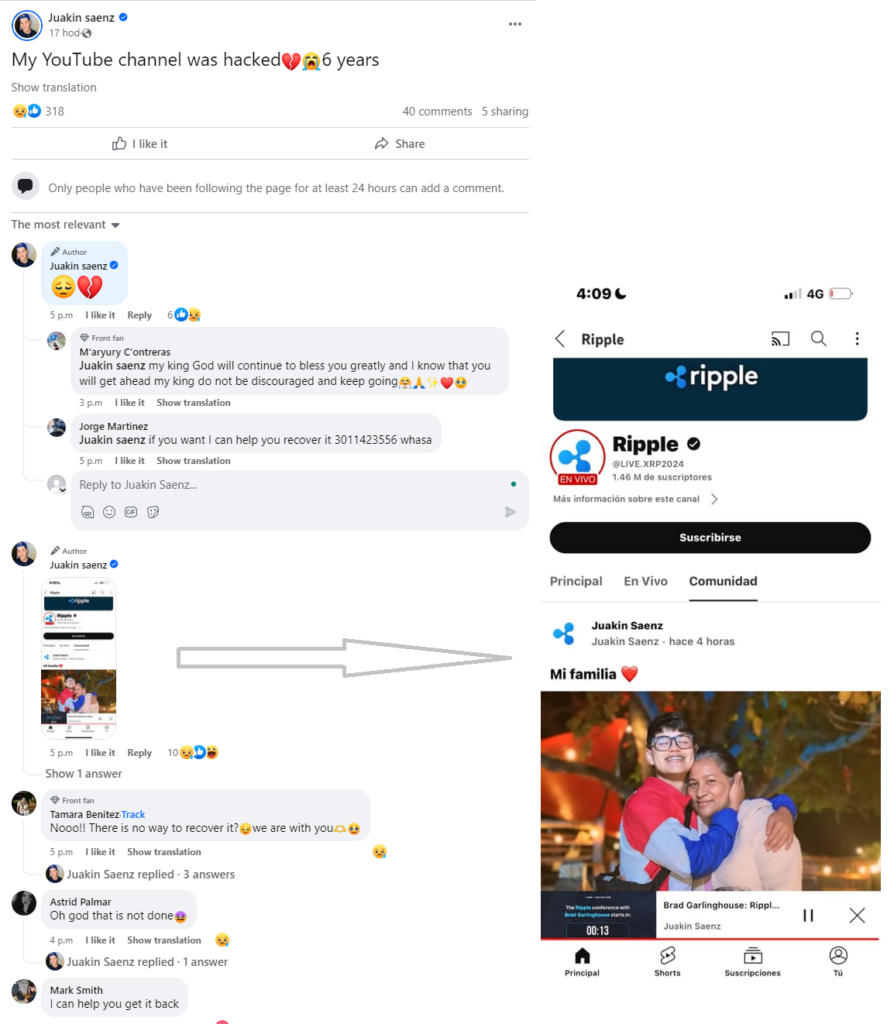
In this case, we have also noticed that the victim had other social media platforms where he announced to this audience that his YouTube account had been compromised and used to spread MicroStrategy and Ripple-related spam. This indicates that the account was live long enough after being hijacked to spread multiple campaigns before YouTube took it down.
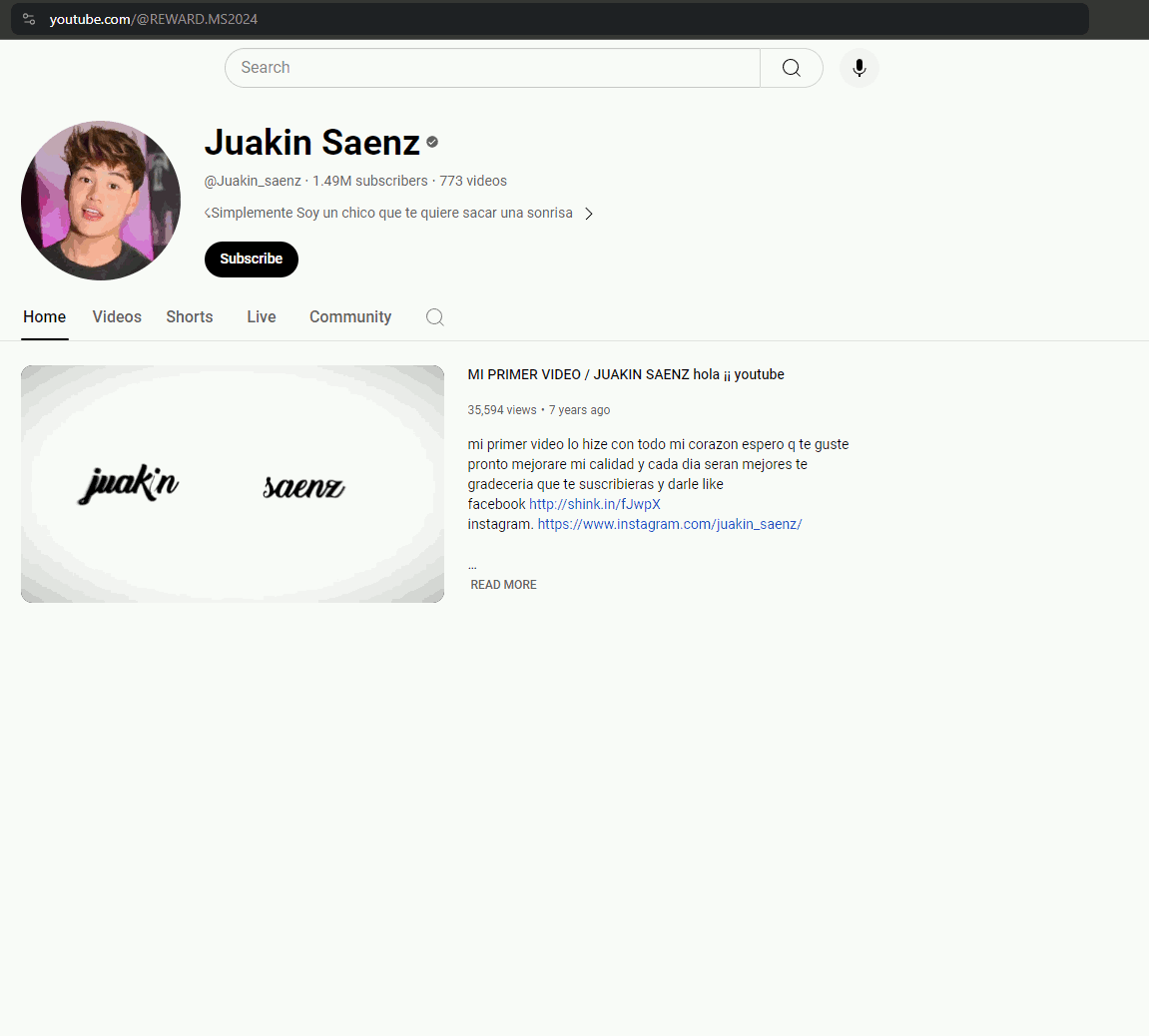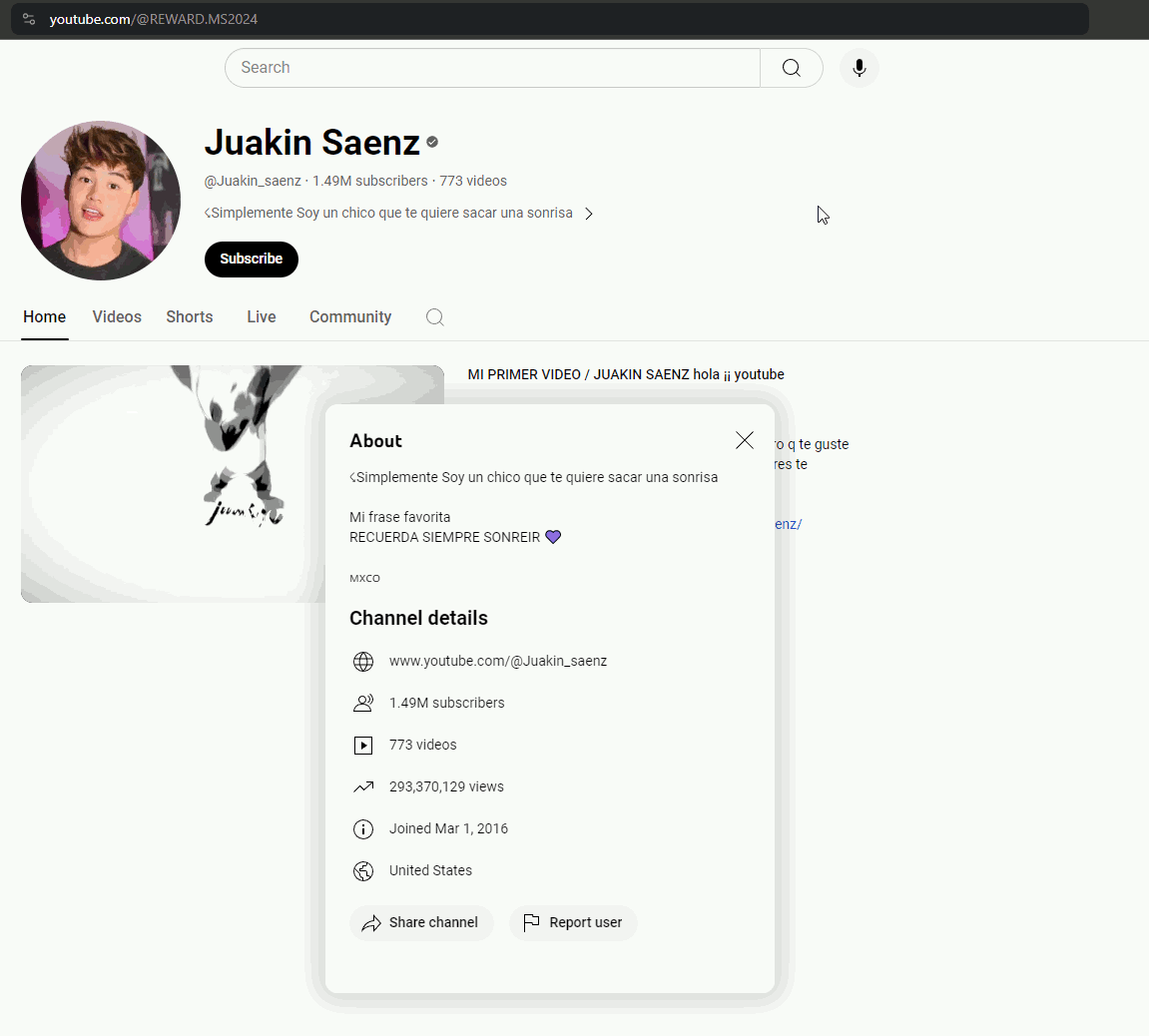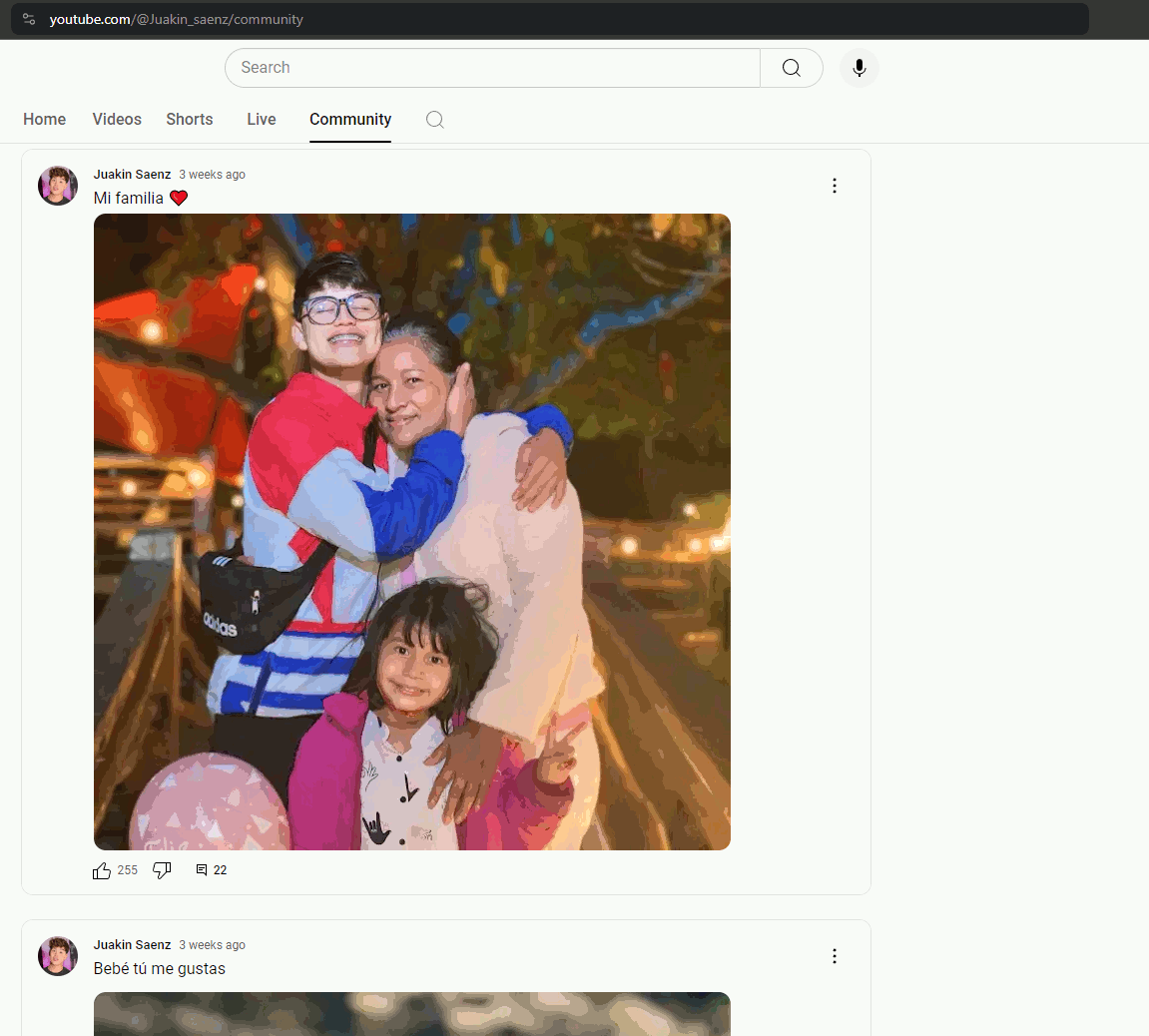
After some time, the account was returned to its owner. However, the alias to the hijacked account is still active. So, the link @REWARD.MS2024 still directs to the victim’s YouTube account.
Since attackers abuse accounts with a large audience and they want to retain access to it for as long as possible, they try to hide their activity to avoid being detected by the rightful owner of the account. Whenever they end a campaign, which usually lasts a few hours, they attempt to restore the account to the previous state. Nevertheless, they are not always diligent in these efforts, and they may miss some details such as channel name or background image.
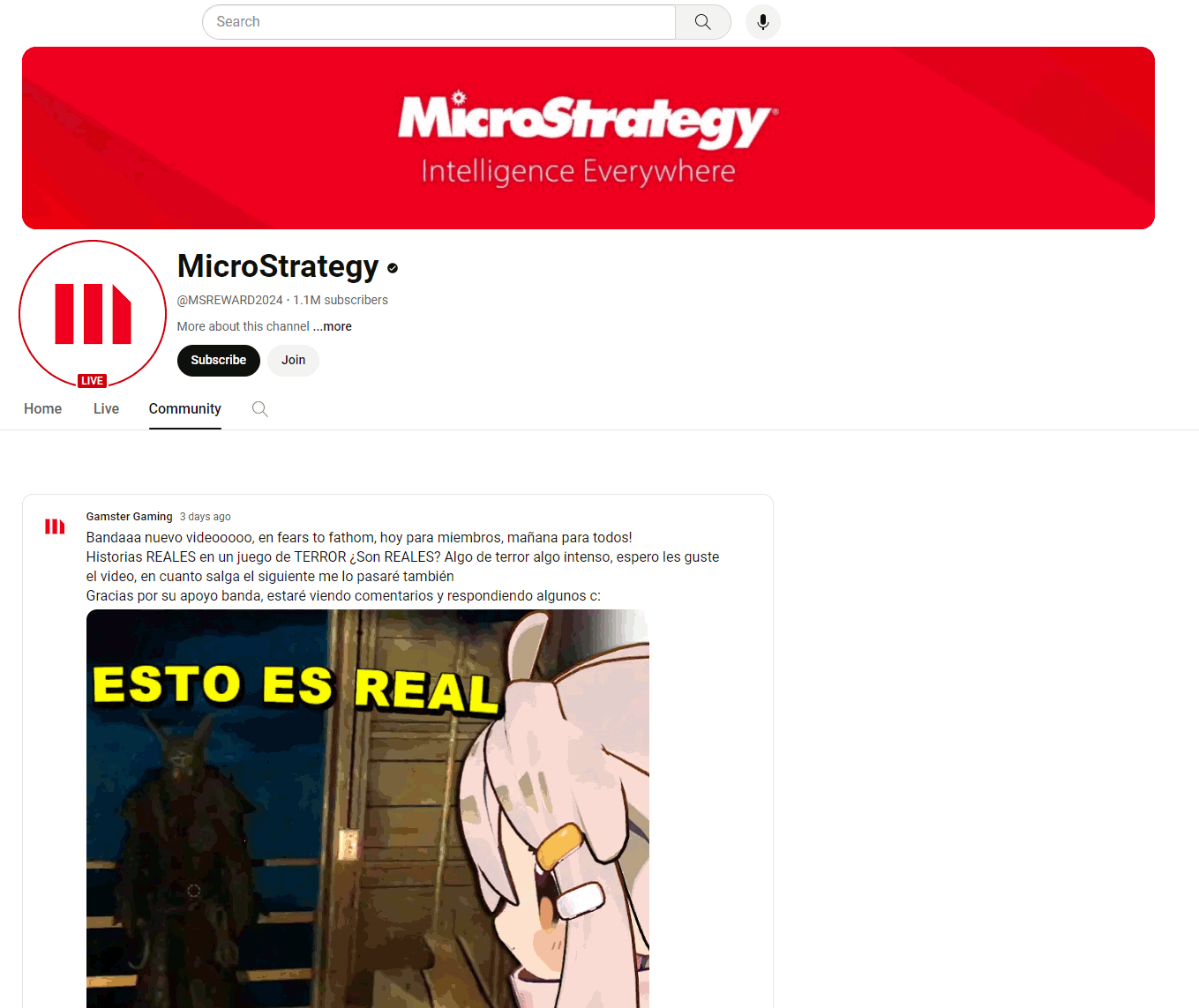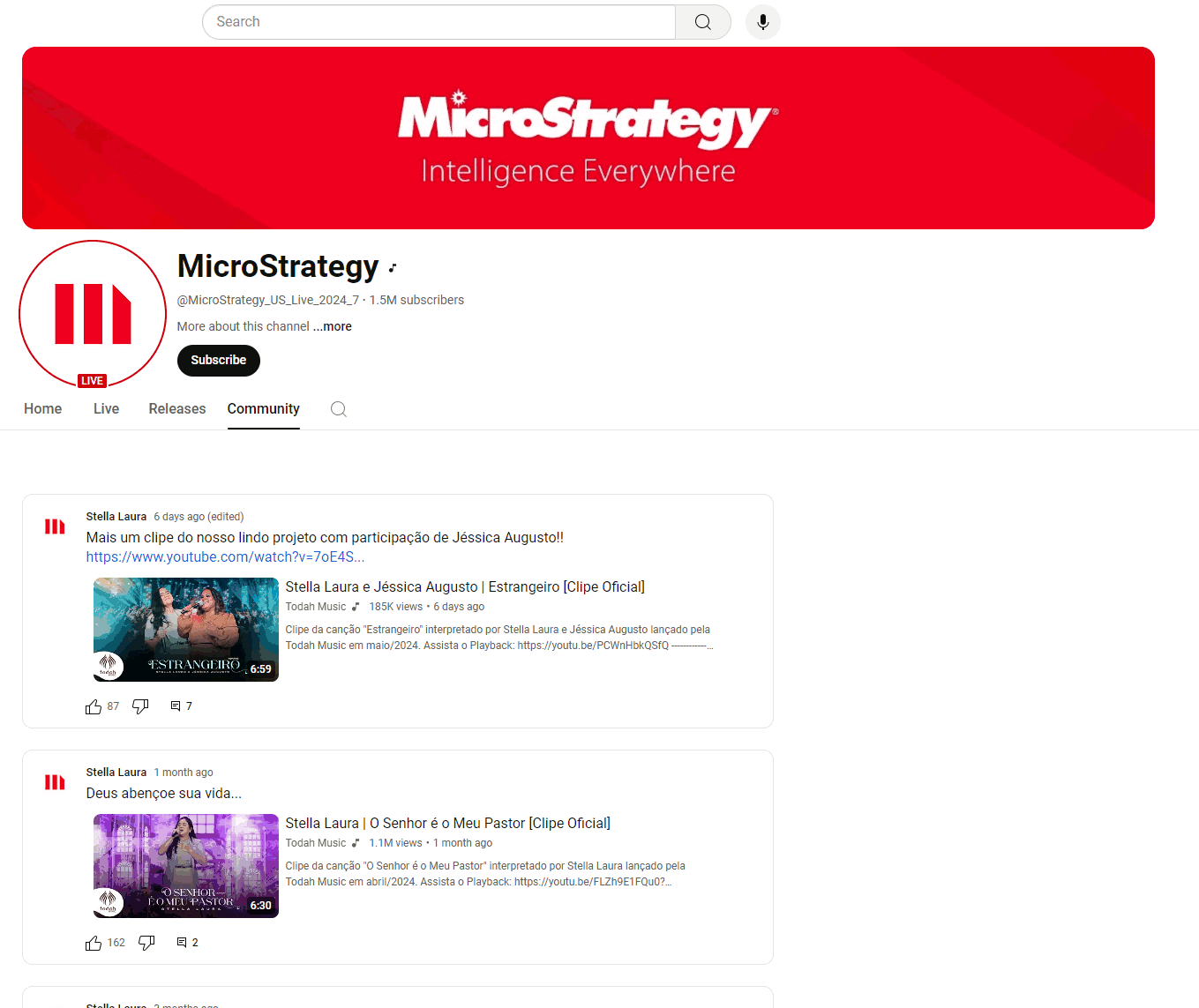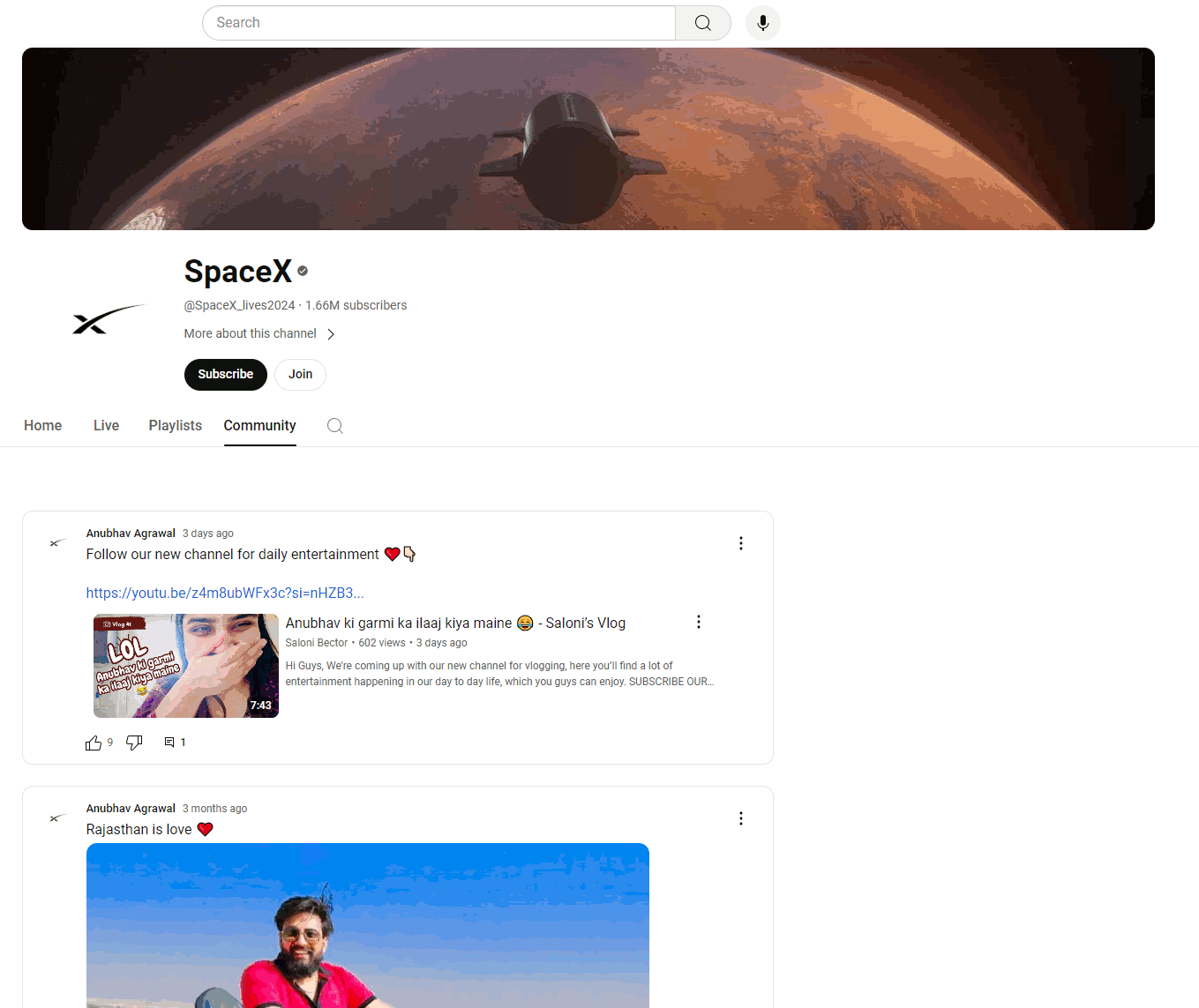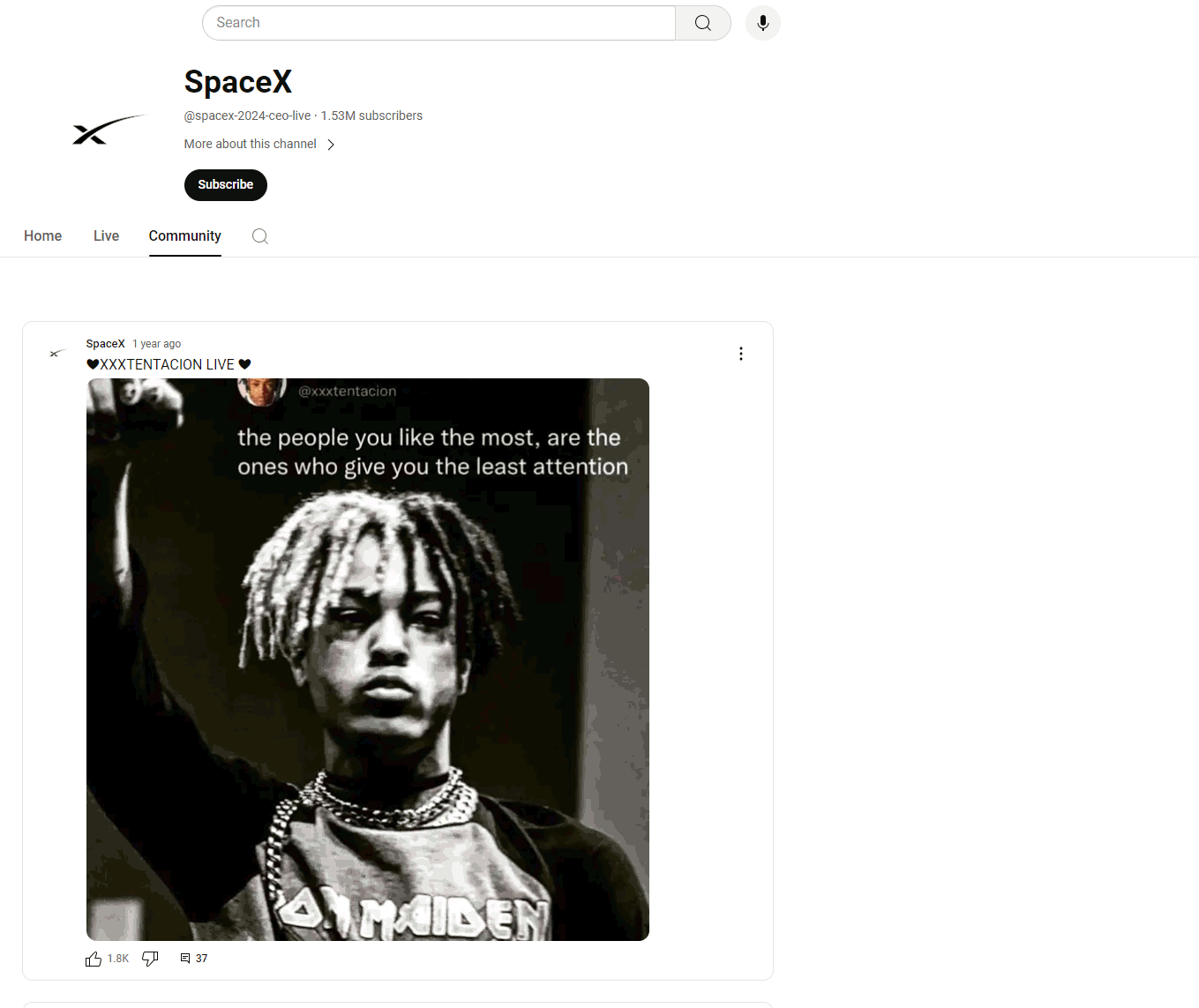
A common sign of stolen accounts is the community tab, which, despite the masking of the hijacked account, contains posts from the original owners.
Video Policy & Providers’ Safeguards
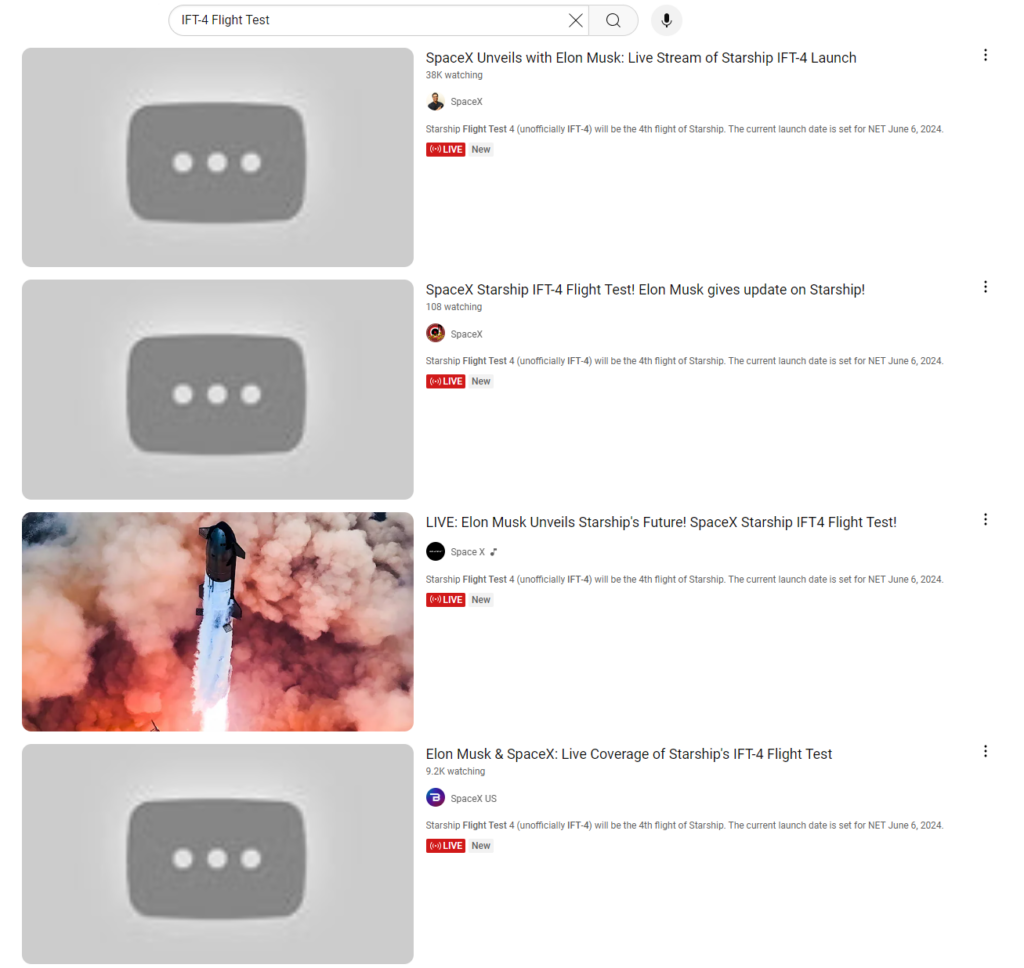
YouTube does define rules and policies for accounts and content visibility, but the effectiveness of its automated scam detection is insufficient. Despite the CryptoCore scam being a longstanding issue known to Google [2], there is no noticeable decrease in scam activities. Instead, major media events (e.g., SpaceX flight tests) are continually exploited with similar patterns that could be automatically detected. Although YouTube has mechanisms to block inappropriate content and accounts, these mechanisms often take more time and effort to respond. YouTube videos and accounts are typically blocked based on user reports, requiring substantial user intervention to trigger the blocking action. Consequently, the hijacked accounts with scam videos were not removed till a few days after the abuse event, as the figure below demonstrates.
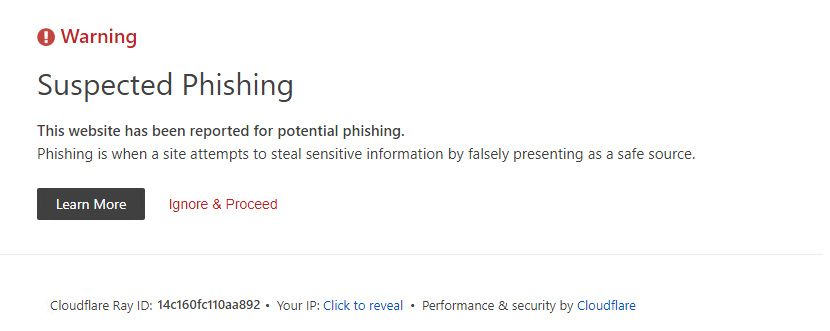
Cloudflare sometimes displays warnings about suspicious content, but this is rare and used primarily for long-running domains. Therefore, we see small proactive activity at the infrastructure level of providers, although the landing pages are generated using the same CryptoCore framework with static artifacts that can be easily identified and blocked.
Abused Events
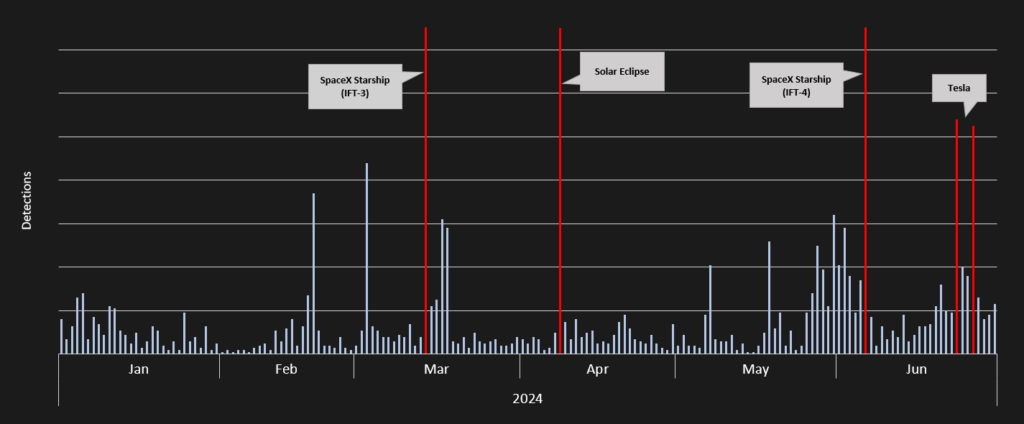
As described above, the attackers are exploiting various events to attract as many victims as possible. We recorded five significant events during the observed period.
At the beginning of January, Michael Saylor, the executive chairman of MicroStrategy, started selling company shares worth $216 million [12]. Attackers used this event to flood the internet with fake videos claiming Michael Saylor was giving away $100,000,000. This event was continuously misused throughout 2024.
Another significant peak occurred on March 14, 2024, when the SpaceX event during the SpaceX Starship integrated flight test (IFT-3) [13] was exploited. This period saw the highest number of detections.
In mid-March, a fake campaign ran after Reuters released information about a contract in which SpaceX allegedly built a network of hundreds of spy satellites [14].
Another notable peak was on April 8, 2024, during the solar eclipse, when SpaceX’s name was once again abused in a CryptoCore campaign.
The last major campaign occurred on June 6, 2024, during the SpaceX Starship integrated flight test (IFT-4) [15]. Nearly 50 hijacked YouTube accounts were used during this several-day campaign. During this campaign, we identified 84 crypto wallets with 500 transactions with a total value of $1.413M.
Additionally, there are sometimes small campaigns that misuse events of elections or tech companies. The examples below illustrate the landing pages for the WWDC24 Apple developer conference and the “giveaway” of Donald Trump.
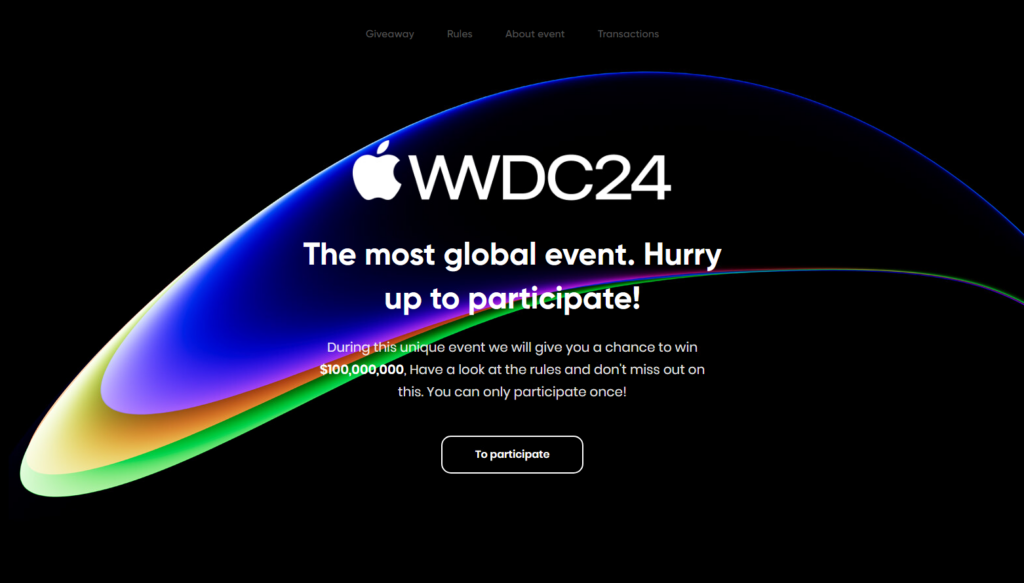
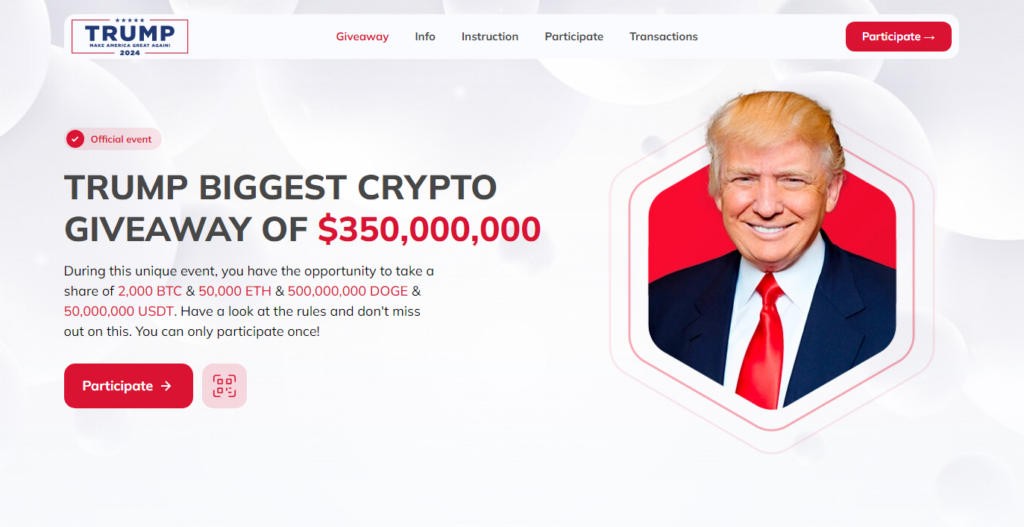
Use of Deepfake Videos
CryptoCore campaigns are complementing YouTube accounts with deepfakes videos. These videos abuse official footage from well-known events, personalities, or companies. For instance, in the case of SpaceX and Elon Musk, we have observed the misuse of videos from events such as the SpaceX All Hands 2024, the Starship Flight Test, and the Starship Update from 2022. For Michael Saylor’s campaigns, the exploited videos feature titles such as “Bitcoin is Digital Energy with Michael Saylor”, “10 Rules for Life with Michael Saylor”, and “The Nature of Energy with Michael Saylor”. Other personalities targeted include Larry Fink (CEO of BlackRock), Vitalik Buterin (programmer and co-founder of Ethereum), and Bradley Garlinghouse (CEO of Ripple Labs).
The compilation of deepfake videos below illustrates the modus operandi and its common theme: a well-known personality talks about a unique chance to double your investment. The videos use fake voices and, in some cases, advanced deepfake techniques like lip-syncing. Typically, these videos are looped every 12 minutes, often preceded by, for example, a countdown for a rocket launch or the start of an online broadcast.

Furthermore, some videos are pre-recorded and published as live streams. For instance, we have seen fresh accounts hosting a video that is about three hours in length, then marked as private, but later, the same content appeared as a live stream on the same account. Sometimes, we have seen captured live streams with added scam-related elements, such as a specific background or a QR code inside the video stream.
During the last major crypto campaign, we noted advancements in the usage of deepfake technology. The videos now feature detailed shots of personalities with high-quality lip-syncing, which can easily deceive viewers into believing they are watching an official statement. Additionally, they use parts of the original background, such as large screens, to seamlessly display information related to the scam.
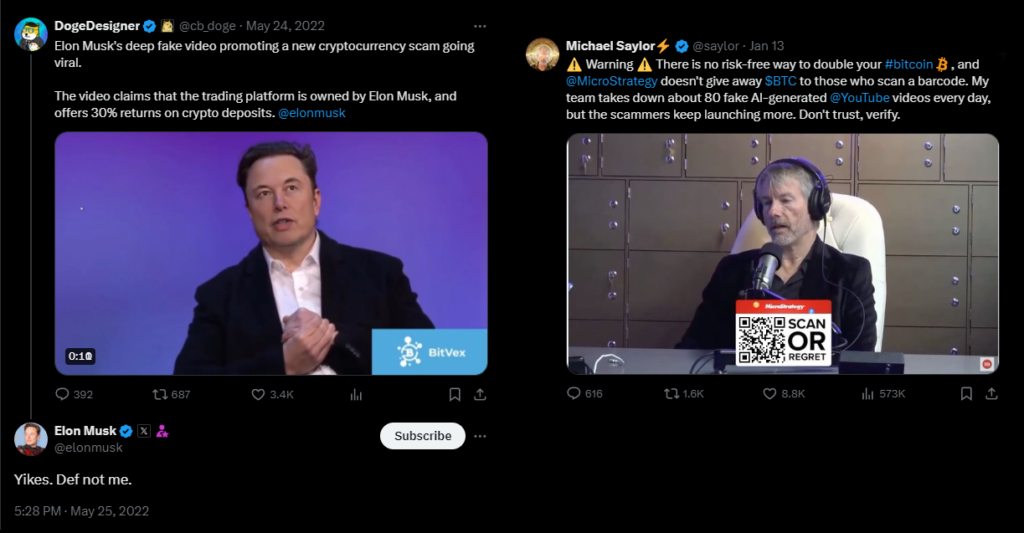
Additionally, the misused personalities have published official statements against these scams but are largely ineffective in stopping them [16, 17].
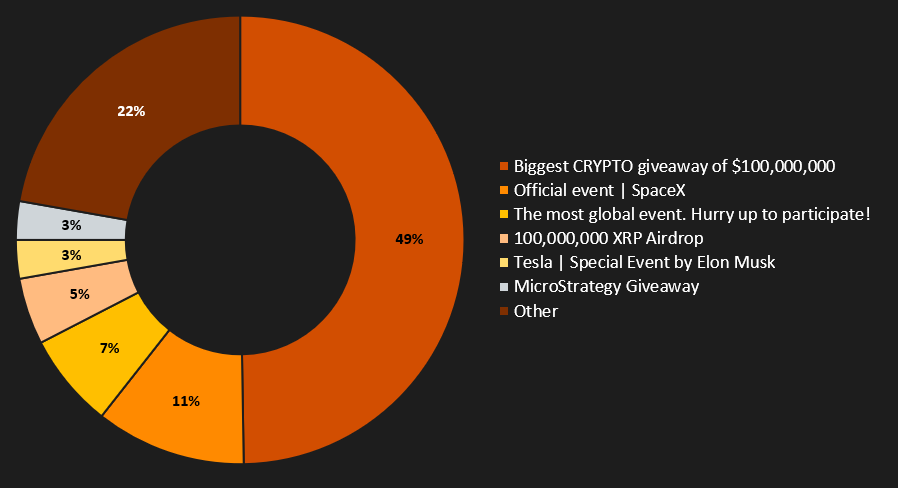
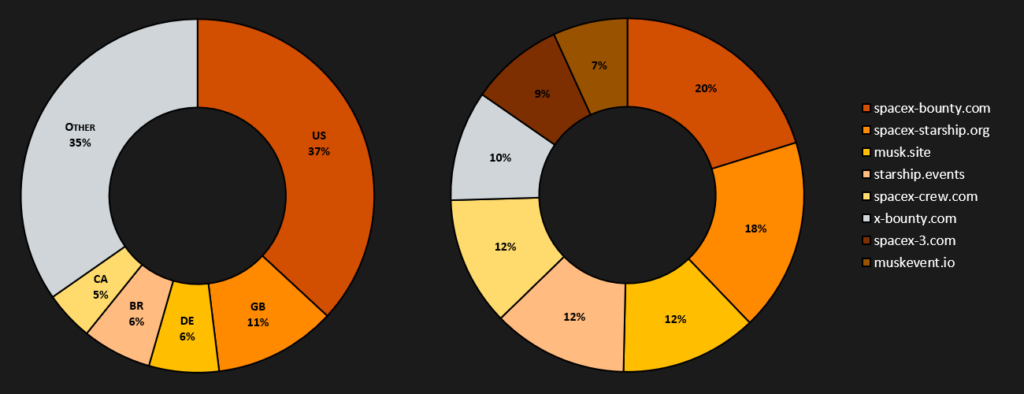
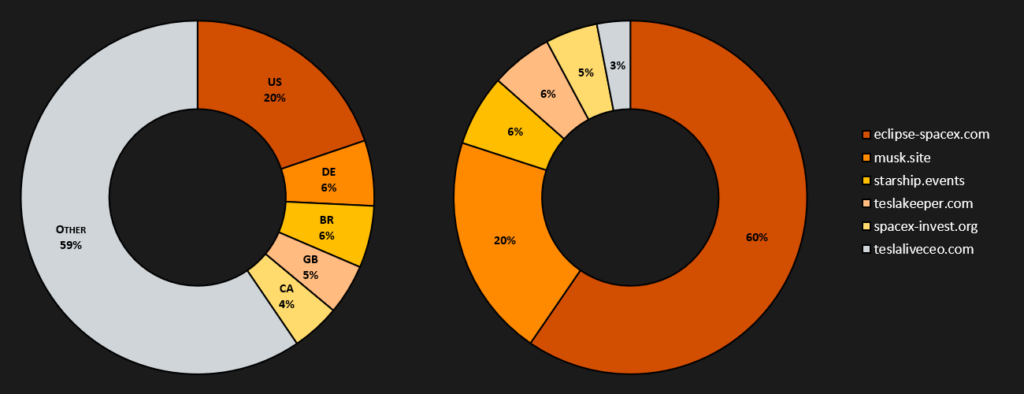
Fraudulent Websites Statistic
The statistics of information extracted from the exposed pages come from a time window spanning from January to June 2024 (6 months). During this period, we detected 340 different domains containing scams generated through the CryptoCore framework. The graphs below show the distribution of headlines used on these fraudulent websites. In summary, the most exploited themes are MicroStrategy, SpaceX, and Tesla.
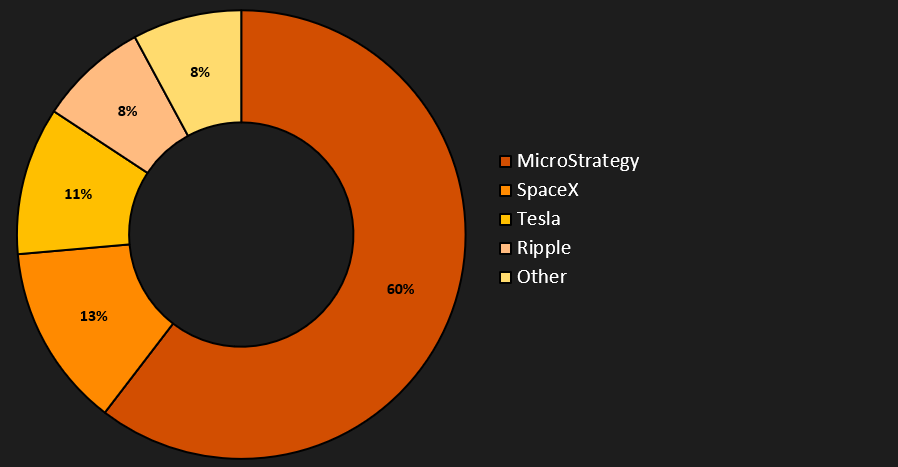
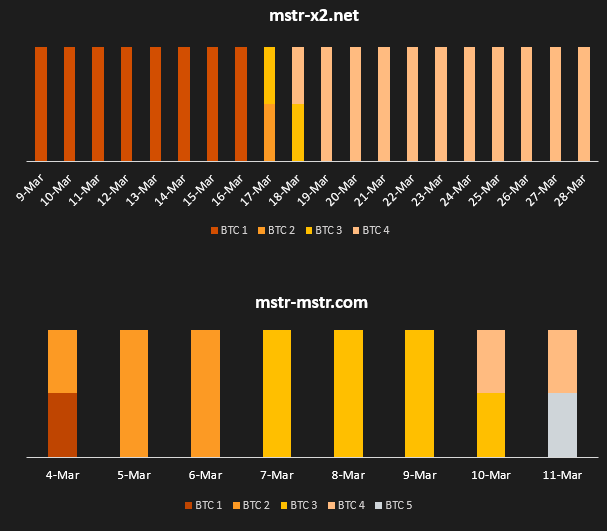
Interestingly, attackers sometimes change their wallets on fraudulent sites. It may happen when the wallets are flagged on some crypto-scam list. The graph below illustrates how wallets have been changed in two domains over time. Therefore, collecting crypto wallet information is an ongoing process that requires regular monitoring of the content on these fraudulent sites.
Technical Analysis
We additionally analyzed the fundamental technical aspects of fake websites and the infrastructure built by the framework. The web design of these websites is predominantly built upon obfuscated Java Scripts. It easily facilitates the concealment of crypto wallets, constants, other features, and variables that shape the dynamically generated content. Similarly, the wallets’ QR codes are generated by another obfuscated JavaScript and stored locally in memory.
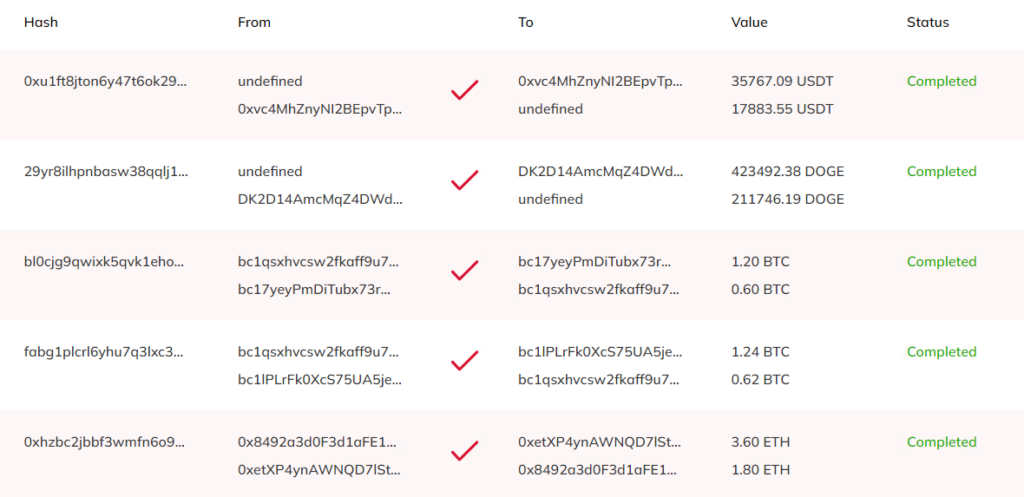
Online Transaction Dashboard
Every five seconds, random transaction numbers and wallet addresses are generated to simulate completed transactions and increase the event’s credibility.
The wallet definition also includes variables determining how fake online transactions will be randomly generated. A random node is defined for each wallet, containing information about the format for a hash transaction and a recipient wallet, including the prefix and length.
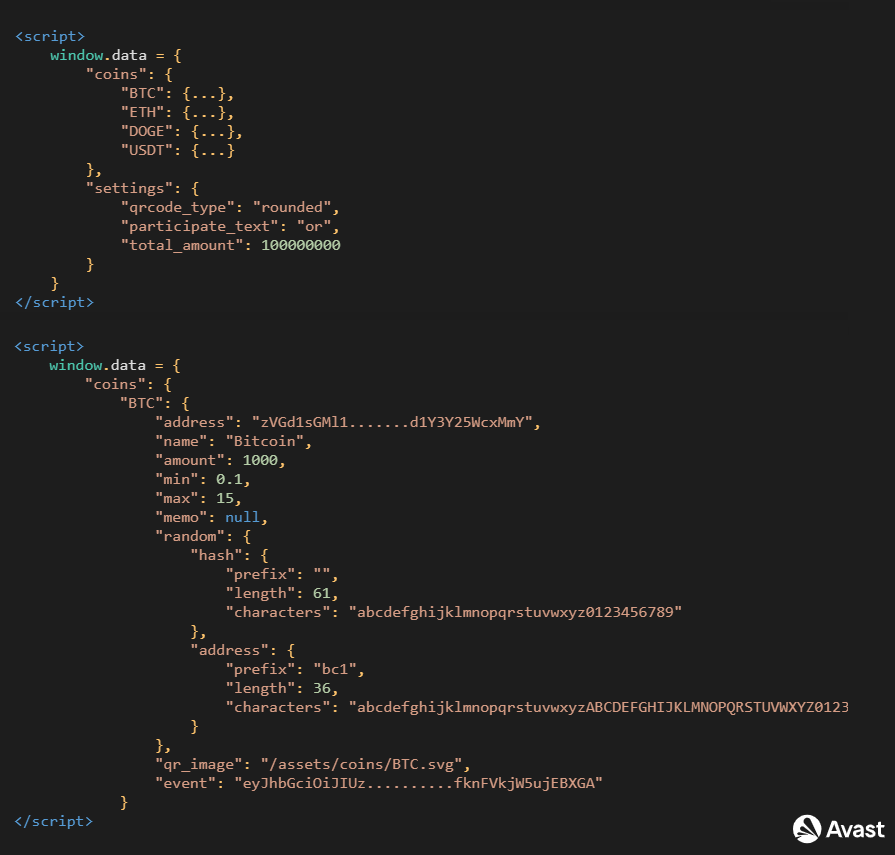
Therefore, the resulting effect looks professional and legal, but the hashes and wallets are deliberately abbreviated, so they cannot be verified.
Anti-debug Protection
The JavaScript codes also employ several techniques to prevent detailed inspection of the fraudulent pages. Specific keyboard shortcuts that allow access to implementation details, such as Ctrl+U, Ctrl+S, F12, etc., are disabled, and a user is redirected to /clarity page with the CryptoCore about page.
Moreover, the pages also intercept and prohibit copy events; copying for wallet via a button is allowed only via JavaScript code. So, when the “copy address” button is clicked, a defined event is sent to the backend. The API event is structured as: api/event?id=<event>, where <event> is defined for each wallet. Finally, the wallet addresses in the JavaScript code are encrypted using a simple Base64 encoding written in reverse order.
Online Chat
The online chat for communicating with the “support team” is implemented using third-party services such as LiveChat, Tawk.to, and Smartsupp. All three services also offer trial or free versions. On sites launched earlier, we have observed that chats are already often blocked.
Still, the chats are always functional and ready to communicate with a potential victim on newly launched sites.
Web Crawling Protection
Before the desired page is rendered, attackers implement several mechanisms to prevent simple web crawling. The first mechanism involves managing cookies, which are calculated on the client side based on constants sent during the initial contact with the C2 server. The specific code for deriving the cookies is as follows:
document.cookie = "0x=" + toHex(slowAES.decrypt(c, 2, a, b)) + "; expires=Wed, 01 Jan 2025 22:22:22 GMT; path=/";
The constants a, b, and c are defined by the C2 server and are linked to the victim’s IP address. This allows attackers to block selected ISPs better. Additionally, sessions are non-transferable, and if the cookies do not match, the server continually sends a request with the calculation of the current and correct cookies for the given IP address. Hence, if everything matches, the server sends the requested content.
The second mechanism involves checking user agents in the HTTP header. If the user agent is on a blocklist (such as wget, curl, etc.), the web server returns a 403 Forbidden response. Additionally, there is ISP filtering, which results in a 404 Not Found response for blocked ISPs.
Cloudflare Protection
There was an interesting difference between collected domains and resolved IP addresses. We have collected a total of 340 different domains with suspicious websites but approximately 440 IP addresses. This discrepancy is due to the websites typically hosted behind dynamic reverse proxies. Therefore, we collected many IP addresses.
The overwhelming majority (99%) of these proxies (IPs) are provided by Cloudflare, with only 1% observed using Akamai Technologies. The use of reverse proxies makes it very difficult to track and determine the exact location of the web servers. Additionally, reverse proxies complicate automated web crawling by requiring bot verification.
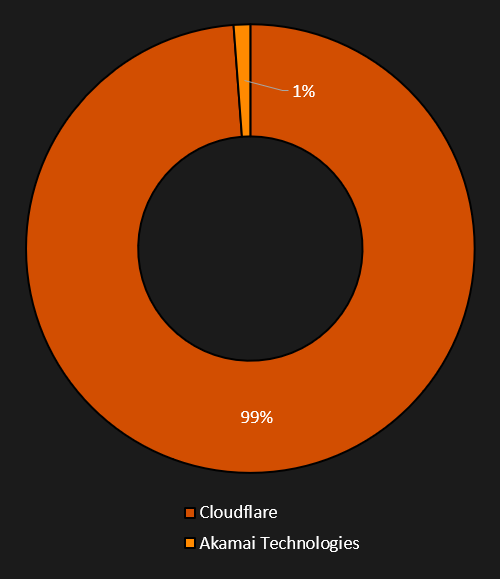
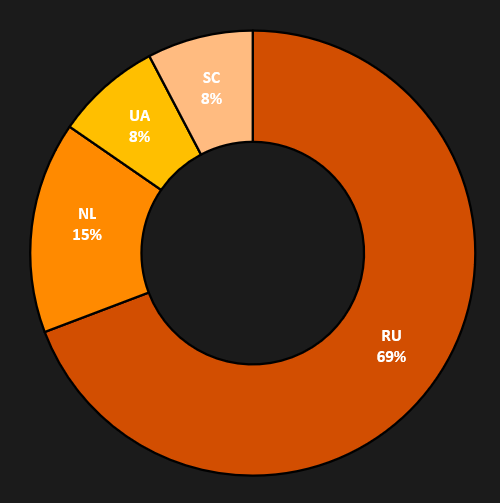
However, based on historical data from 2021, when the group did not yet use reverse proxies, we have determined that nearly 70% of the web servers were hosted in Russia and 15% in the Netherlands. These web servers were running on Ubuntu with the nginx web server.
Tech Support Chat
An integral part of professional websites and large companies is the support chat. In the case of CryptoCore, chat is implemented using third-party plugins. Previous publications have noted that the chat may be connected to a particular form of LLM [18].
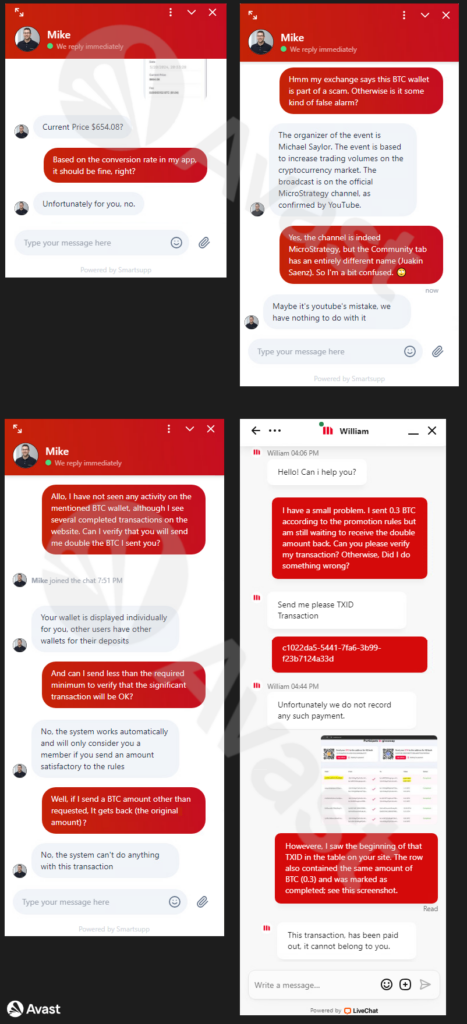
Several test communications with the purported technical support lead us towards the presumption that there are real people responding to the communication. A few examples of these interactions are shown below. Generally, the support team tries to convince you of their legitimacy. If you inquire about a transaction, you made but did not receive the promised double return, they will ask for the transaction hash or a screenshot. Unsurprisingly, no complaint resulted in a refund.
Case 1: Forged Transaction Confirmation
We created a fake screenshot showing a transfer of 0.33 BTC but with a current price of only $600. The support team explicitly questioned the current price amount. This indicates that the support team can respond to images and more complex content (such as suspicious BTC price), presumably ruling out simple LLM-based chatbots.
Case 2: Suspicious YouTube Channel
In the second case, we confronted the support team that their wallets were listed on the Crypto Scam Tracker. They responded that it was an official event by Michael Saylor, including a verified YouTube account. Our follow-up argument was that the YouTube account contained posts from another (hijacked) user. This apparent discrepancy was explained as a YouTube error, with no connection to them. A detailed story of this YouTube channel can be found in the Hijacked YouTube Examples section.
Case 3: No Transactions on Wallets
We confronted the support team that their transaction dashboard showed numerous transactions, but we needed help finding a transaction on the blockchain. Their response was rather unconvincing. Additionally, they stated there was no way to verify that our investment would be returned.
Case 4: Forged Transaction System Dashboard
We again created a fake screenshot showing a BTC transfer and a fake dashboard with the same transaction ID, currency, and amount of BTC. We have asked why we did not receive the payment when the transaction appeared on the dashboard. The brief response claimed the transaction had been paid out and could not be ours.
Detections
Detections related to giveaway scams are focused on the fraudulent pages on desktop and smart devices (mobile smart phones). However, scammers encourage victims to use a smart device and scan a QR code to avoid antivirus solutions because more than 50% of smart devices have no protection [19]. Our telemetry data shows that the hit ratio for CryptoCore detections on desktop and smart platforms is 2:5, which indicates a rather significant success in redirecting victims to generally less protected platforms.
Our telemetry also demonstrates a correlation between the detection hits and events abused by the scam groups. In total, we can identify five significant events in the crypto world that have a demonstrable connection to the CryptoCore detections. The details of the abused events are summarized in the section Abused Events.
The countries that are the most affected by CryptoCore risk are the United States, the United Kingdom, Brazil, and Germany. There is also a noticeable difference between users of smart devices and desktop computers. On smart devices, we detected the most scams associated with the IFT-3 event, while on desktop devices, the event related to the solar eclipse – seems to have attracted a larger audience.
Conclusion
The giveaway scam campaign spread by the scam group CryptoCore is a sophisticated operation that exploits the popularity of cryptocurrencies and the trust of users in well-known personalities and events. The scammers use deepfake technology, hijacked YouTube accounts, and professionally designed websites to deceive victims into sending their cryptocurrencies to the scammers’ wallets.
CryptoCore has been operating on a large scale for at least five years. The platforms, e.g., YouTube and Cloudflare, block giveaway scams only sporadically or with significant delays, despite the modus operandi remaining unchanged for years. Moreover, we continue to observe several newly hijacked YouTube accounts for each campaign that represent a substantial risk in conjunction with parked accounts from previous campaigns. Additionally, we have documented several cases of hacked accounts where owners had to recover the channels built for many years. Statistics show that nearly 65% of accounts compromised by CryptoCore have over 100k followers, and 20% have over a million subscribers. Therefore, we strongly recommend all YouTube account owners take additional security precautions such as using 2FA and strong passwords, being aware of potential phishing campaigns, regularly checking account activity to detect unauthorized access, ensuring account recovery options (such as another email or phone number), and using reputable antivirus and security software to protect devices from malware that could compromise the accounts.
Although we primarily focused on YouTube, we have seen similar scam attacks on other platforms, evidently from the same scam group. Previous studies indicate that the group’s activity is extensive; during our six-month observation, we estimated nearly $5.4 million in stolen crypto coins. Moreover, if attackers exploit the right event, they can gain almost $1.5 million within a few days. However, this suggests the group’s annual profit must be significantly higher.
Tracing the whole attack vector is complicated because scammers split the vector across two platforms. For that reason, redirecting victims to smart devices increases the probability that fraudulent sites will not be detected by antivirus software since many people do not protect their smart devices. Consequently, we observe the highest incidence of fake sites just on smart devices. Everything indicates that such attacks will continue, with the group seeking attractive events to exploit until the targeted platforms effectively protect their users and visitors.
Note that we named the scam group as the used scam framework CryptoCore; however, based on the analysis CryptoCore-associated campaigns, the giveaway scam is a complex scam project probably delegated to other paid services, often illegal. Moreover, the deepfake videos have continuously improved over the observed year. In terms of directions for future research, further work could analyze the collected crypto wallets.
Users must stay informed about these scam risks. As the cryptocurrency landscape evolves, so will the scams that exploit it. Users should always be cautious if an offer seems too good; no one gives anything for free. Users should also be wary of YouTube accounts with many subscribers but suspiciously low activity and inconsistent content. Finally, having a good antivirus program installed on smart devices is essential. Therefore, continuous research and vigilance are necessary to protect potential victims and safely navigate the evolving cryptocurrency scene. Remember, if it sounds too good to be true, it probably is. Stay safe!
If this type of scam has compromised your accounts, do not hesitate to contact us and share your information and experiences. By doing so, you help improve protection against attackers and limit the reach of fraudsters.
IoC
Crypto Scam Wallets
Hijacked YouTube Accounts
The cc-yt-accounts list summarizes the most active YouTube accounts abused in CryptoCore campaigns, and the “Status” column describes each one’s state. It is a snapshot of August 7, 2024.
The “active” state indicates that the account contains artifacts typical for hijacking (background image, account name, etc.), but without scam videos. So, we cannot determine whether these accounts are still under the control of bad actors or have been returned to their original owners and have not been rolled back to their original state yet.
Reference
[1] Twitter: Fake Elon Musk scam spreads after accounts hacked
[2] Phishing campaign targets YouTube creators with cookie theft malware
[3] Scammers hijack YouTube channels to promote Elon Musk-themed crypto schemes
[4] Give and Take: An End-To-End Investigation of Giveaway Scam Conversion Rates
[5] Technical analysis from one of the scam kits distributed on the dark web
[6] Beware of scams! Elon Musk is not giving away bitcoin on Twitter
[7] Fake ‘Elon Musk’ Crypto Giveaway Scam Campaigns Run Rampant on TikTok
[8] Verified Twitter accounts hacked in $580k ‘Elon Musk’ crypto scam
[9] How Hackers Hijacked Thousands of High-Profile YouTube Accounts
[10] Deep fakes power account takeovers on YouTube to maximize crypto-doubling scams
[11] Hacking YouTube channels with stolen cookies
[12] Michael Saylor Commences Plan to Sell $216M Worth of MicroStrategy Shares
[13] SpaceX Starship integrated flight test 3
[14] Exclusive: Musk’s SpaceX is building spy satellite network for US intelligence agency, sources say
[15] SpaceX Starship integrated flight test 4
[16] X – Elon Musk status
[17] X – Saylor status
[18] A Deep Dive into Stream-Jacking Attacks on YouTube and Why They’re So Popular
[19] Antivirus in the Age of Evolving Threats: 2024 Antivirus Market Report