Additional contributors to this report: Jason Baker, Justin Timothy, Ryan Silver, and JP Mouton
July 2024 yielded some answers to our ongoing questions about the future of ransomware, but also raised additional questions as the ecosystem continues to adjust to shakeups among its major players. Following one of LockBit’s quietest months in recent memory, the group has attempted to return to its previous dominance by posting 31 victims, a number which edged out fellow Established group Akira but fell short of RansomHub’s continued high tempo. Despite appearing to be at death’s door following international law enforcement disruption and the imposition of sanctions, LockBit still shows some signs of life but with a potentially altered target base. US-based organizations accounted for 42% of observed victims claimed by LockBit in July, a lower rate than that of the wider ransomware ecosystem at an average of 52%. Lower numbers of US victims could reflect decreased targeting of US organizations based on a drastically reduced likelihood of payment in the face of sanctions, making such operations unprofitable to any affiliates still flying the LockBit flag. If this hypothesis holds true, we would expect to see continued decreases in US-based organizations claimed by LockBit and the near-to-mid-term.
The ascendant Ransomware-as-a-Service group, RansomHub, maintains its dominance amid its peers in terms of victim volume, likely fueled at least in part by displaced affiliates from the now-disrupted LockBit and Alphv. RansomHub shows no sign of slowing down, having posted an average of 1.81 victims per day to claim a total of 56 victims in July. While the remaining Established groups compete for affiliates, we continue to observe an increase in newly discovered Emerging groups, with the addition of five new groups to GRIT’s tracker in July. Among these new groups are FOG, another Emerging group that has demonstrated considerable operational maturity; and ElDorado, which entered the landscape with an uncharacteristically high 15 victims in July. Join GRIT as we analyze the impacts and movements of dozens of ransomware groups, old and new, in this month’s edition of the Ransomware Report.
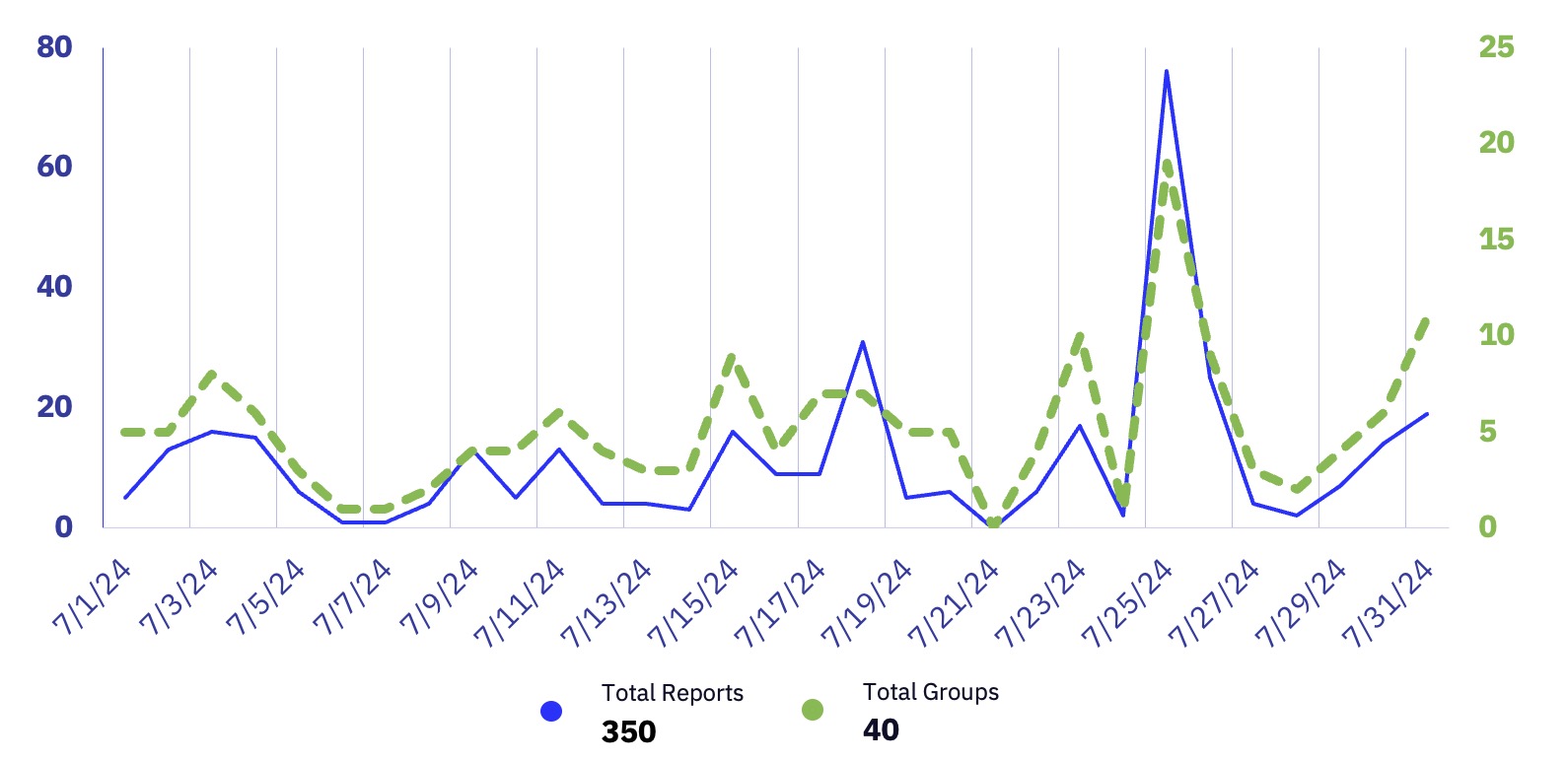
| Total Publicly Posted Ransomware Victims | 350 |
| Number of Active Ransomware Groups | 40 |
| Average Posting Rate (per day) | 11.3 |
Ransomware Trends
July’s victim posts began to accumulate slowly compared to previous months. Spikes of activity on the 18th and 26th from batch postings by both LockBit and RansomHub brought the month’s total victim volume to within the average range relative to June 2024.
The total of 40 distinct ransomware and data extortion groups is the highest that we have observed in a single month in 2024. Continued reductions in barriers to entry and probable realignment of experienced affiliates are expected to drive continued diversity and the emergence of new groups in the near term.
In previous years, the total number of observed attacks tended to start climbing in Q3, following a perennial summer lull. Based on this, we anticipate an increase in observed victims in August relative to July.
Ransomware Victims by Country
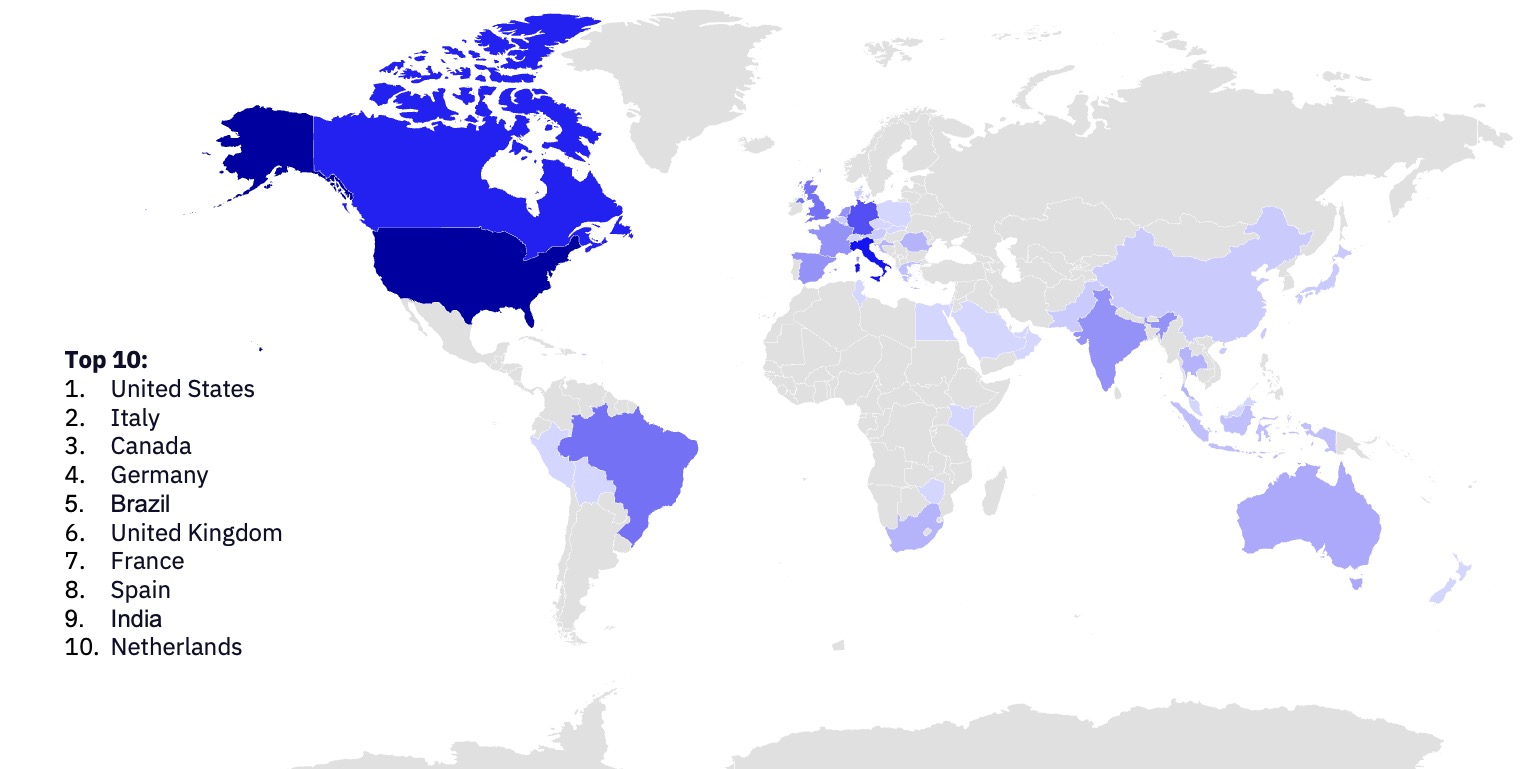
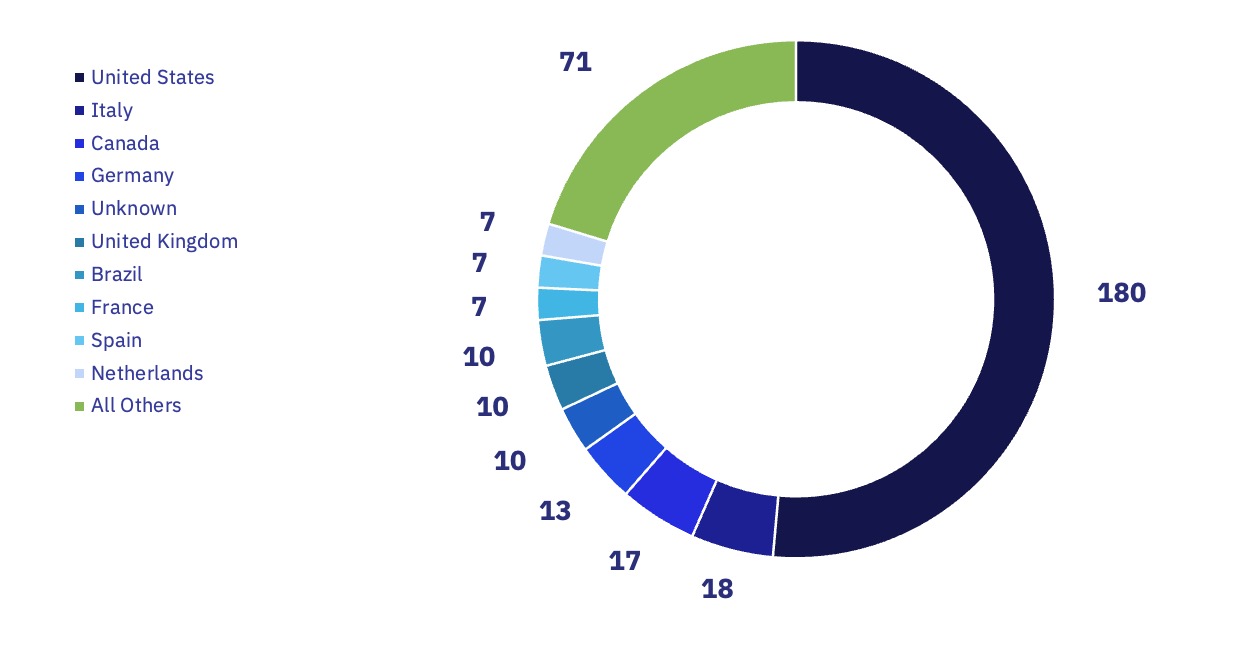
GRIT’s analysis of ransomware trends in July has revealed continued shifts in the geographic impacts of ransomware groups, as evidenced by the increase in observed attacks impacting Italian organizations. Based on GRIT’s ransomware data, Italy has felt the effects of a steady increase in ransomware attacks dating back to January 2024, with July resulting in the second-highest number of observed Italian victims in recent years, following only November 2023.
The increased number of Italian ransomware victims observed by GRIT may be due in part to Italy’s higher propensity to pay ransoms; Sophos’ Ransomware Trends 2023 report previously indicated that Italian organizations were among the most frequent payers, with 56% opting to pay the ransom. Reporting or internal knowledge of Italian organizations could, in turn, drive increased operations that target Italian victims, specifically by ransomware groups seeking a greater likelihood of receiving payment.
US-based organizations remain the most impacted by global ransomware attacks, despite recent decreases in their proportion of attacks. By comparison, the United Kingdom has experienced a recent drop off in attacks, decreasing from 27 and 24 observed attacks in May and June of 2024 to only 10 in July. This decrease could be in part attributed to international sanctions imposed against LockBit, which has historically been responsible for as much as 40% of observed attacks impacting the UK.
Threat Actor Trends
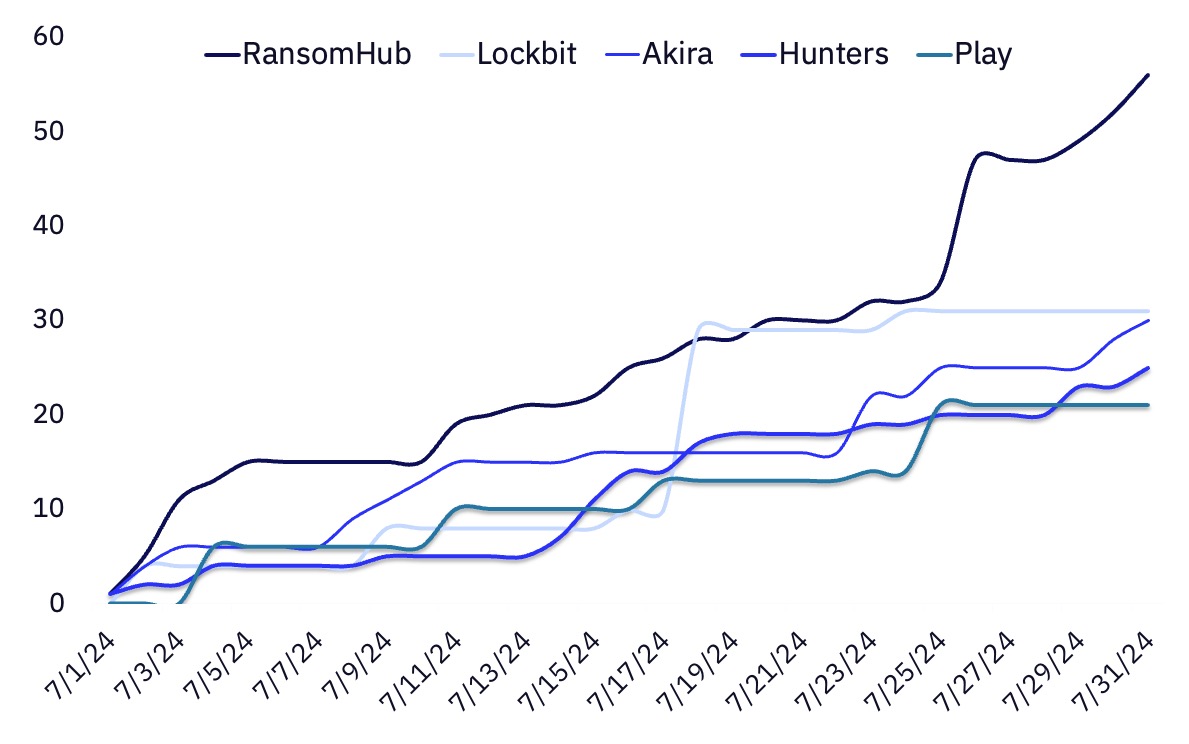
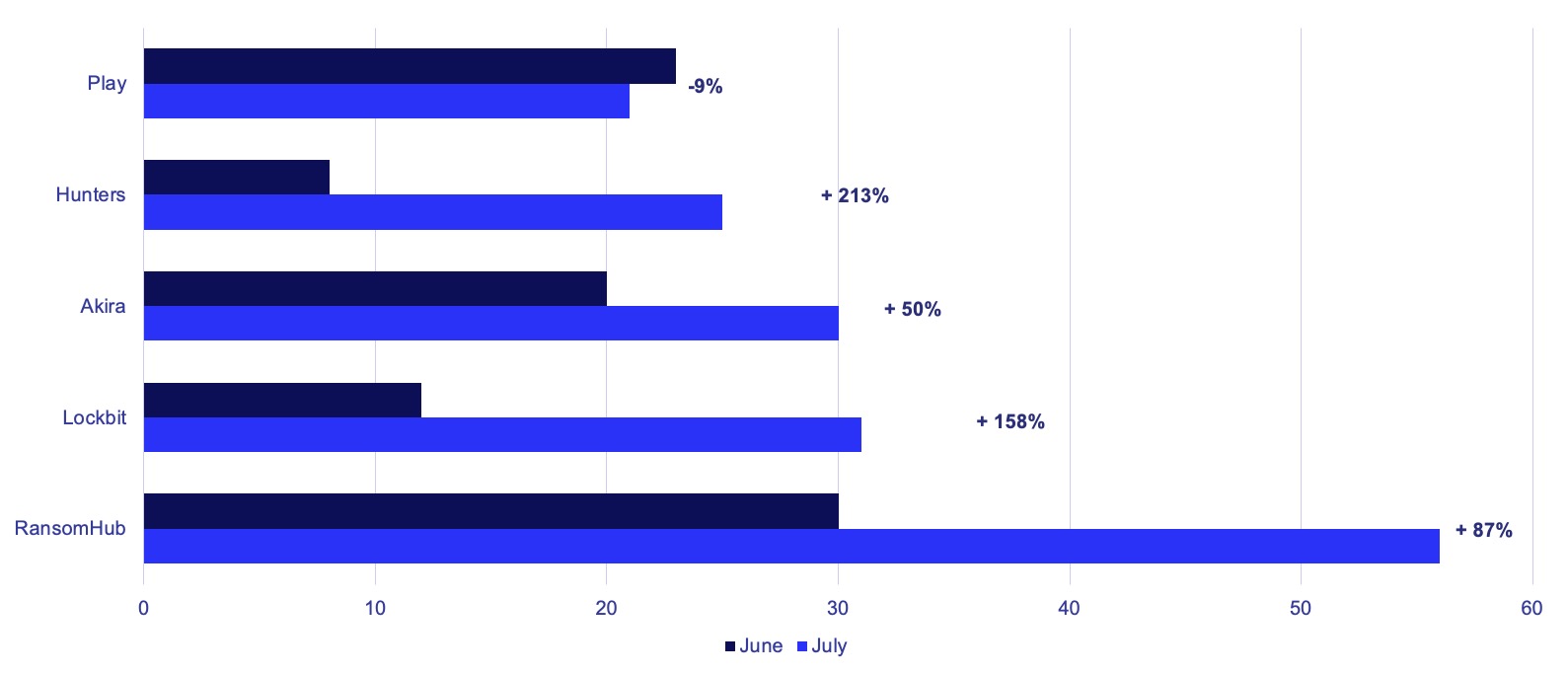
RansomHub continues its high-operational tempo following their emergence and ascendance in the first half of 2024. The group has maintained its position as the most impactful ransomware group by victim volume for a second month, accounting for 16% of observed victims in July and increasing their total number of posted victims by 87% month-over-month. As we have previously assessed and in line with recent reporting, RansomHub’s victim volume is likely attributable at least in part to its attraction of experienced affiliates from disrupted ransomware groups such as LockBit and Alphv.,
Akira also demonstrated continued impactful operations in July, reporting a 50% increase in victim volume month-over-month even while seemingly taking weekends off. Outside of a decrease in operations observed following the publication of a working decryptor to the group’s earlier ransomware, Akira has continued operations without disruption since April 2023.
LockBit returned to the scene following a pronounced period of decreased operational activity in the preceding months and claimed responsibility for 9% of observed victims in July. However, we note a lower-than-average portion of LockBit’s victims appear to be US-based – 42% vs. the wider ransomware landscape’s average of 52% – which could reflect a decreased emphasis on US-based organizations in the wake of international sanctions. The victim organizations GRIT observed in July skew smaller and disproportionately associated with healthcare, potentially reflecting looser targeting or a decreased capacity to pursue “big game hunting” operations following the departure of experienced affiliates.
Threat Actor Spotlight: FOG (Emerging)
The Emerging ransomware group, FOG, was added to GRIT’s tracker in mid-July following a series of posts impacting five educational institutions and two others, a bold entrance for a previously unheard-of group. FOG employs common double-extortion tactics, which involve both the encryption of victim data and the exfiltration of sensitive data, allowing the group to extort victims in a redundant fashion for both decryption and in exchange for not leaking the sensitive data. This method increases the pressure on victims and allows for extortion regardless of a victim’s ability to recover from encryption.
Since appearing in May 2024, FOG has demonstrated an emphasis on educational institutions among its victims, with initial access most frequently obtained through the use of compromised VPN credentials. As reported by Arctic Wolf Labs, 80% of FOG’s initial victims have been from the education sector, and though this ratio has decreased to 50% in the closing weeks of July, the shared industry impacts likely highlight either a common victim base or common technology that the group has likely sought to target. We lack visibility or insight into the volume or efficacy of FOG’s operations prior to the establishment of its data leak site in early July of 2024. Despite its recent emergence, FOG’s operational consistency mirrors that of Established groups, suggesting that they may grow to be a major player in the near term. Their focus on the education sector and use of double-extortion tactics make them a significant threat that warrants close monitoring by cybersecurity professionals.
Other Notable Ransomware Events
New Ransomware Groups Tracked by GRIT in July 2024:
GRIT began tracking four new ransomware groups in July, which were accountable for an average of eight victim posts each across the month. Uncharacteristically for newly Emerged groups, several appeared with relatively high volumes of victims for ostensible Freshmen; FOG opened their data leak site with a “batch” of seven victims and continued with additional victims throughout the month; El Dorado similarly demonstrated a higher volume of victims early on with 15 victims; and Mad Liberator opened their data leak site with six victims in one day.
GRIT has observed similar behavior from a smaller number of Emerging groups that would go on to become long-term Established groups, including Akira and 8Base, and though the behavior is not entirely novel, it has historically been an exception rather than a rule – the majority of Emerging groups claim low numbers of victims, and a substantial portion appear to cease operations within 1-3 months of first appearing. This early-stage “washout” of most Emerging ransomware groups aligned with the smaller portion that would continue operations in the long term. In the mid-term, GRIT will monitor whether the increased number of early victims signals a greater number of Emerging groups that are likely to persevere over time or a tendency towards greater numbers of victims observable earlier in Emerging groups’ tenure.
GRIT notes that one potential explanation for this shift in observed victim volume among seemingly Emerging groups could be the displacement of experienced affiliates from Alphv and LockBit. This would provide ample opportunity for operators to “splinter” into new groups or attach themselves and their experience to other new groups. In both cases, we would expect to observe the emergence of overlapping TTPs with historical RaaS groups, as former affiliates with past experience bring their habits with them to new organizations.
Pryx and the Evolving Definition of Ransomware
Pryx is a likely financially motivated threat actor which first posted victims to a data leak site in early July 2024, beginning with alleged data breaches from the Rowan College at Burlington County and the government of the United Arab Emirates. Open-source reporting quickly emerged of Pryx as a “new ransomware group,” and Pryx was added to many ransomware-focused feeds. GRIT’s Ransomware Report specifically scopes its data to insular ransomware groups, ransomware-as-a-service groups, and data extortion groups, de facto requiring disruptive file encryption and/or data exfiltration and an accompanying ransom demand to “make the cut.” Our scope takes out aggregators of victims from other groups, “hacktivist” groups, and groups or individuals that post data breaches freely or for sale to external patrons.
Pryx falls into this latter category. While reporting has called Pryx a “ransomware group,” the group itself claims on the “about” page of its data leak site that it “is definitely not a ransomware group.” While Pryx has seemingly attempted to sell data it claims to have breached, there is no indication that the actor has attempted to directly extort its two posted victims.
The information posted to Pryx’s data leak site includes multiple obscenities and slurs reminiscent of behavior on low-tier illicit forums, and the breaches referenced on the site appear to have first been posted by a user named “pryx” on the dark web forum XSS and later Breach Forums in June 2024. Without discounting the impact of Pryx’s breaches or the sophistication of any preceding intrusion, the evidence available only allows us to conclude that an actor using the name Pryx has posted breached data on a basic data leak site, and that likely the same actor previously posted the same data for free on at least two illicit forums. We have seen no evidence of direct data extortion of victims or ransomware operations attributed to this actor.
Why does this matter? Most importantly, for other users of this data source and consumers of reporting that cites it, data curation is necessary to provide an accurate understanding of the ransomware and data extortion landscape. Each month GRIT discards dozens of potential entries that do not qualify as ransomware or data extortion groups, in turn influencing our understanding of victim volume “in the wild”; failure to do so, by comparison, would yield different insights over the short and long-term. Secondly, this represents a recent and visible example of improper inflation of a group’s maturity, sophistication, and/or behavior based on non-credible reporting. Now as ever, it is vital that threat intelligence professionals validate and corroborate their security reporting to prevent such errors.
Healthcare Takes the Top Spot
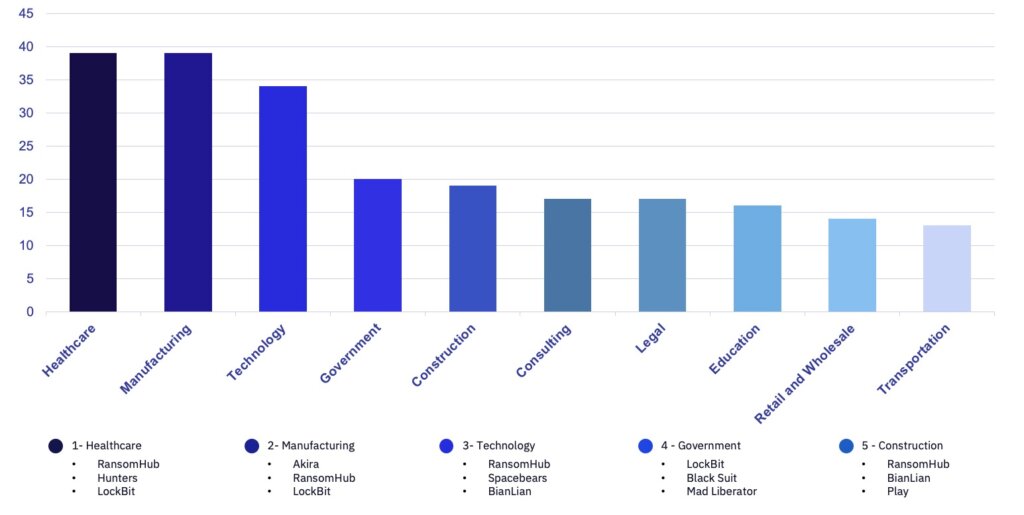
GRIT’s ransomware reporting in 2024 has repeatedly emphasized the increased number of attacks impacting victims in the healthcare industry. This trend continues with a record-high 39 ransomware attacks observed against the healthcare industry in July 2024, surpassing the previous peak of 35 from April 2023.
Personal Health Information (PHI) remains a valuable commodity to cybercriminals and regulatory liability for healthcare organizations, likely increasing the attractiveness of healthcare organizations to ransomware groups. While the data of most non-paying victims may hold little value outside of the owner, healthcare data presents a secondary opportunity for ransomware groups to extract value from their operations, with the option to sell or auction PHI retained by threat actors regardless of whether a direct victim pays the demanded ransom or not. The sensitive nature of healthcare data is likely a substantial driver of healthcare organizations’ increased propensity for paying ransoms to prevent public release; In 2023, Sophos reported that 56% of healthcare organizations affected by ransomware opted to pay the ransom.
Scattered Spider’s RaaS Ties
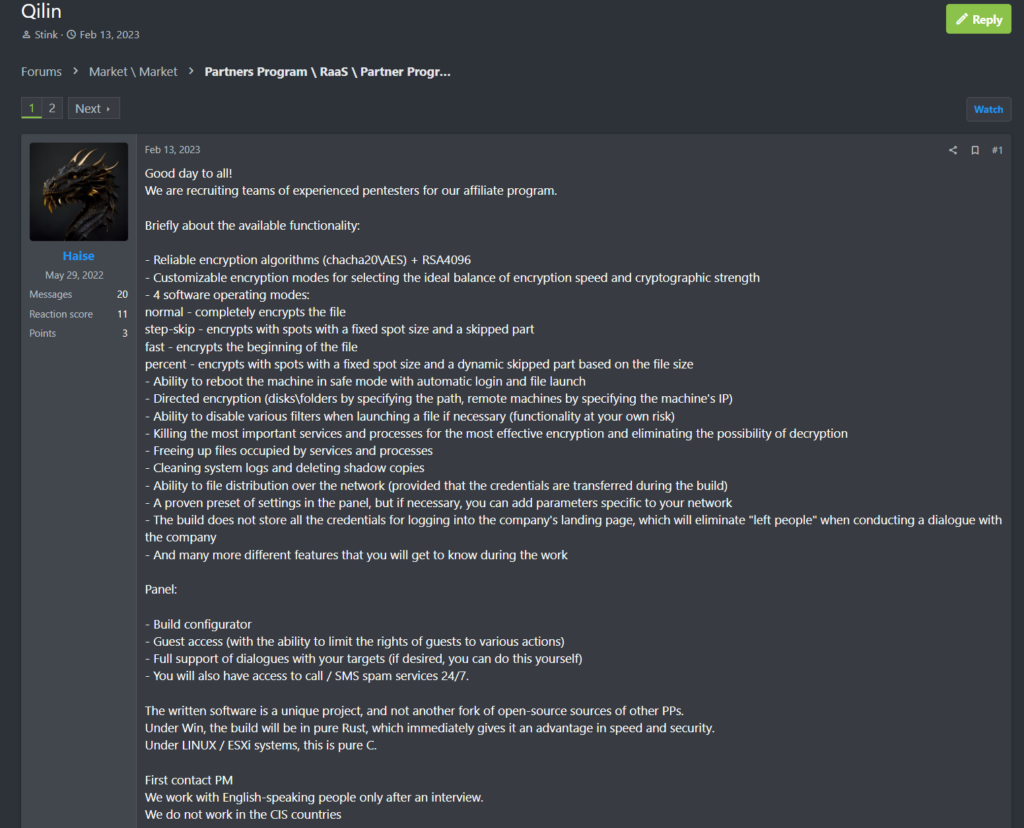
Corroborating our June 2024 blog, “Worldwide Web: An Analysis of Tactics and Techniques Attributed to Scattered Spider,” which linked Scattered Spider affiliates with the RansomHub RaaS group, recent reporting by Microsoft has tied members of Scattered Spider to both RansomHub and Qilin RaaS operations. Scattered Spider rose to prominence in the wake of purported attacks against MGM Entertainment and Caesars in late 2023, which were undertaken by members of the group operating as affiliates of Alphv / Black Cat at the time. Following Alphv’s disruption and subsequent “exit scam” departure in early 2024, Scattered Spider appears to have continued conducting ransomware operations as affiliates of RansomHub and Qilin, both of which have posted “recruitment” advertisements to illicit forums, such as RAMP, since February 2024.
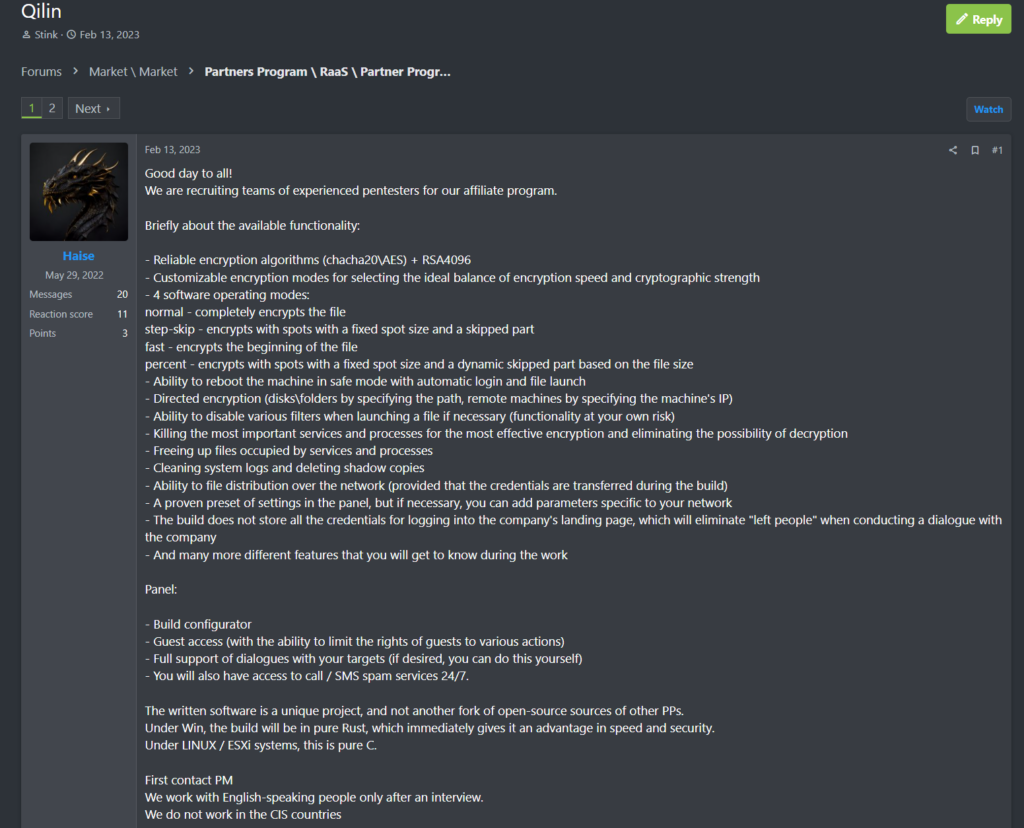
As seen in this example, a RAMP forum user under the moniker “Haise” created a post on the forum that invited affiliates to join the Qilin RaaS service by explaining the benefits of the group’s encryption malware. The Haise moniker has replied to the thread multiple times since posting to preserve its visibility, including as recently as July 21st, 2024.
GRIT assesses that members of Scattered Spider will likely remain affiliated with RansomHub or Qilin or affiliate with other groups depending on the level of profitability and efficacy associated with each; as financially motivated threat actors, continued affiliation is likely to be based on the viability of either in generating ransom revenue over the long-term. We cannot rule out the possibility of personal relationships contributing to the movement of Scattered Spider affiliates to RansomHub and Qilin specifically (e.g. if former peers or Scattered Spider affiliates “vouched for” or were known in either group), but future affiliation of Scattered Spider affiliates with other ransomware groups in the future could indicate searches for “greener pastures” in other RaaS organizations.
New ESXi Vulnerability Empowers Actors
On July 29th, 2024, Broadcom published a security advisory disclosing an authentication bypass vulnerability, CVE-2024-37085, which impacts VMware’s ESXi hypervisor platform. The vulnerability, which specifically impacts installations of ESXi connected to Active Directory environments, enables an attacker to achieve administrative privileges on the platform by creating or adding a user to a Domain Group specifically named “ESX Admins,” even if the group never existed previously or if the title is applied to another existing Domain Group.
ESXi and other hypervisors have historically been an attractive target to ransomware operators seeking to attack their victims in the most impactful way possible, with recovery only viable with proper backups. Groups such as Akira, RansomHub, and Hunters International have all offered Linux versions of their ransomware to affiliates, specifically enabling intrusions where the affiliate has gained access to an ESXi host server. Attacking ESXi hypervisors presents fewer risks than “traditional” encryption at the operating system level, which can trigger Endpoint Detection and Response agents and other defensive detections in the process.
Hypervisor-level encryption greatly simplifies the path to victory for an attacker, necessitating access to only one system in order to greatly disrupt an organization’s operations. CVE-2024-37085 makes achieving access to VMware ESXi as simple as compromising an Active Directory account with permissions to modify a single group. This extremely useful vulnerability was observed as under active exploitation by the ransomware groups Akira and Black Basta “in the wild” to compromise targets before a patch was released. Organizations that have not updated their ESXi environments remain vulnerable to exploitation and attack via the vulnerability. Due to the simplicity of exploitation and the value of the target, GRIT assesses that ransomware groups with access to ESXi encryption capabilities will continue to attempt to exploit this vulnerability for the foreseeable future.
Identity Security and its Ties to Ransomware
In the course of GRIT’s daily operations, we have recently fielded a series of questions about increased instances of “identity theft” or information-stealing malware, particularly as the growth of ransomware operations appears to have stalled. To compile these answers and their connection to the contemporary ransomware and data extortion economy, we are opting to revisit the topic here.
First things first: Is information-stealing malware on the rise? We lack unique intelligence collection into information-stealing malware’s prevalence, but several reports in 2024 suggest that this is the case. IBM’s 2024 X-Force Threat Intelligence Index reported that “Infostealer malware activity” increased 266%, and an April 2024 report from Kaspersky claims a 643% increase in devices compromised by “data-stealing malware” from 2020-2023.
So why might information-stealing malware activity persist or increase even while some other forms of cybercrime stagnate or decrease? The simplest answer is that the theft of identity information, including valid credentials, remains an attractive means of generating revenue for cybercriminals, as the data has a wide range of downstream uses. Third-party criminals conducting ransomware operations, business e-mail compromise, and follow-on data theft are all consumers and possible purchasers of this information, resulting in a redundant customer base that is resilient to upticks or decreases in any one particular form of cybercrime.
A recent high-profile example of information-stealing malware’s utility is the H1 2024 spate of data compromises allegedly impacting multiple customers of Snowflake, a cloud service provider. Multiple public data breaches emerged from April to May 2024 amongst victims who shared Snowflake as a service provider, leading to early speculation of supply chain compromise. A subsequent investigation by Mandiant uncovered that the root cause of initial access was instead the threat actor’s use of “credentials previously stolen via infostealer malware” impacting systems not owned by Snowflake. At a low cost (information stealing malware logs for infected devices often sell for between $5-$10 each on illicit marketplaces), threat actors can gain the ability to access sensitive environments in a potentially undetected manner – an inarguably faster and more effective means of initial access than brute force.
Information-stealing malware is widely available on easily accessible forums or marketplaces and increasingly includes an intuitive User Interface that minimizes technical barriers to entry. Far from requiring in-depth technical expertise, information-stealing malware can be widely deployed at scale using pre-formatted phishing messages, managed in an intuitive interface, and packaged or sold on multiple Deep and Dark Web marketplaces or forums. In summation, information-stealing malware is easier to acquire than ever, easier to use than ever, and likely maintains its marketability based on redundant customer bases.
Information and identity theft are not limited solely to information-stealing malware. After years of ransomware groups posting of victim data, there is also an abundance of openly available or historical PII, PHI, and credential information (passwords), which can be scraped, correlated, and repackaged at low to no cost by threat actors focused on compromising identity. In an example of such use, we have observed multiple attempts by threat actors to “re-extort” organizations under fraudulent premises, using previously leaked data from historical compromises to imply a new intrusion that has not occurred. Similarly, low-tier threat actors may use historically compromised identity data to attempt generally unsophisticated extortion of individuals, such as through so-called “sextortion” emails that leverage historically compromised passwords to assert compromise of an individual’s personal devices and browsing history. These types of criminal extortion operations require even lower levels of technical prowess than ransomware or data extortion operations, which we may call “unsophisticated” and could notionally be accomplished solely with an email account from a privacy-oriented provider and access to the TOR network.
This problem set, as described, reflects the continued issue of reduced barriers to entry for new and would-be cybercriminals, the increased availability of diverse and affordable tools, as well as the burgeoning cybercriminal marketplace in which the same individuals can generate revenue. These issues are unlikely to disappear or decrease on their own, and their distributed nature makes law enforcement disruption difficult. However, the ready availability of information-stealing malware has resulted in effective detections for many, whether through endpoint or network defenses. Attack surface monitoring and exposure management tooling often offer monitoring solutions that can detect information-stealing malware logs, providing a reactive method for identifying historical information-stealing malware infections and compromised credentials, possibly allowing for account hardening and credential resets before a threat actor can take advantage of the compromised data.
For individual users and less-resourced organizations, commercial antivirus may also aid in identifying and remediating cases of information-stealing malware, and user awareness and security training remain low-cost and high-impact means of preventing information-stealing malware’s introduction to a system altogether. Defenders should consider implementing a combination of these proactive and reactive measures to reinforce defenses against information-stealing malware.
Final Thoughts
Overall, July 2024 demonstrated that the ransomware ecosystem continues to be healthy, but we are no longer seeing the month-over-month unchecked growth observed in the past. The 351 victims posted this month pales in comparison to the 490 that were posted in July 2023 showing that the disruption of top players truly does affect the overall impact of ransomware. As the stagnation of the ransomware economy continues, one cannot help but notice the impact of a lack of a single dominant group on the overall victim rates. Groups like Lockbit and Conti before them drove tremendous month-over-month growth in the number of victims, seemingly by themselves. But in reality, their meteoric rise and sustained victim numbers were achieved with the assistance of complex affiliate programs, sophisticated operations, and bulletproof infrastructure. In hindsight, the record numbers of ransomware in 2023 were a result of hypercentralization around a minority of extremely busy ransomware programs. With a majority of the most productive actors all under one “roof” and supported by a streamlined platform, the only check to the number of attacks committed was the financial motivations of the affiliates themselves. As of now, in July 2024 there is no longer a single centralized entity with a dominant majority of the ransomware business. The appearance of newly formed groups does show that the system is healthy and capable of accepting new players; however, they do not drive growth like a centrally dominating actor. RansomHub looks to be the best candidate for changing this reality, but they are still a long way off of the posting rates and operational maturity of Lockbit and Clop in their heyday. As the ransomware ecosystem expands and contracts, the friction of affiliates changing groups seems to be the major limiting factor preventing exponential growth. This is by no means the “death of ransomware.” Transitional periods, like the one we are seemingly experiencing now, inevitably lead to stagnation of growth. As we transition into Q3 2024, GRIT assesses that this stagnation will continue until one of the top players is able to establish unequivocal dominance in the space and recentralize affiliates under their flag.
The GRIT Ransomware Taxonomy
By subdividing ransomware groups, GRIT can obtain more detailed insights into how ransomware groups progress in their level of operational maturity and can classify and identify potential rebranding activity.
We distinguish ransomware groups by placing them into these six categories:
EMERGING
This category is reserved for new ransomware groups within their first three months of operations. These organizations may be short-lived, resulting in an Ephemeral group; may be determined to have Splintered or Rebranded from an Established group; or may move on to further develop their operations and TTPs over time.
EPHEMERAL
These groups are short-lived, with varied but low victim rates. Observed victims are usually posted in a single or short series of large postings rather than a continuous flow over time. Ephemeral groups, by definition, terminate operations, spin-off, or rebrand within three months of formation. These groups may or may not have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
DEVELOPING
These groups have conducted operations for three months or longer, resulting in a recurring flow of victims. Developing groups do not appear to be directly linked to other ransomware groups as a Splinter or Rebrand but may include some experienced ransomware operators. Developing groups generally improve their people, processes, or technology over time by recruiting additional members, refining TTPs, or improving the quality of their associated ransomware and encryption. These groups generally have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
SPLINTER
These groups consist of a plurality of members from previously Developing or Established groups and may have formed either by choice or due to exclusion. These groups may be identified by very similar or overlapping TTPs and tooling or through HUMINT gathered through interactions with personas on the deep and dark web. Splinter groups differ from Rebrands by the continued existence of the original organization as the Splinter group operates.
REBRAND
These groups consist in whole, or in part, of former Developing or Established groups. Rebrands often maintain the same people, processes, and technology as the original group. Rebrands are generally undertaken in order to minimize attention from law enforcement or intelligence officials or to avoid negative publicity.
ESTABLISHED
These groups have operated successfully for at least nine months and have well-defined and consistent tactics, techniques, and procedures. Established groups often possess functional business units that enable sustained ransomware operations, with specialists focused on areas such as personnel, encryption, negotiations, etc. These organizations successfully employ technology and redundant infrastructure to support their operations.
There are multiple routes a group can take through the various classifications, and no one route is standard. While one group may begin as “Ephemeral” and move their way through the ranks to “Full-time,” another group may enter as a “Rebrand” as part of a larger obfuscation strategy to avoid attention from law enforcement.
*** This is a Security Bloggers Network syndicated blog from The Guiding Point | GuidePoint Security authored by Grayson North. Read the original post at: https://www.guidepointsecurity.com/blog/grit-ransomware-report-july-2024/
如有侵权请联系:admin#unsafe.sh