2024-8-16 21:0:55 Author: www.sentinelone.com(查看原文) 阅读量:7 收藏
The Good | Two Major Ransomware Ops Disrupted & Criminal Linked to Largest Credential Theft Market Sentenced
Three cybersecurity operations have led to significant victories against ransomware and credential theft operations this past week.
First, a joint international operation, led by the FBI and other global agencies, successfully dismantled the Radar/Dispossessor ransomware operation. This group, known for targeting small to mid-sized businesses (SMBs) across multiple countries, had been exploiting vulnerabilities and weak passwords to steal data and encrypt devices. The takedown included the seizure of servers and domains, significantly disrupting the group’s activities and protecting many potential victims.
In another win, a key figure behind the Ransom Cartel ransomware operation and a prolific malvertising campaign was arrested in Spain and extradited to the U.S. Belarusian-Ukrainian national Maksim Silnikau was responsible for launching ransomware attacks that shared code with the notorious REvil family and distributing malware through deceptive online ads, or malvertising. Described as one of the most prolific Russian-speaking threat actors, his arrest marks a significant blow to GRU-linked cybercriminal networks.
An international operation coordinated by the NCA has resulted in the arrest and extradition of a man believed to be one of the world’s most prolific Russian-speaking cybercrime actors.
FULL STORY ➡️ https://t.co/kgPdMAwqPZ pic.twitter.com/MVjRLco55R
— National Crime Agency (NCA) (@NCA_UK) August 13, 2024
Finally, a Russian national named Georgy Kavzharadze was sentenced to 40 months in prison for his role in selling over 30,000 stolen login credentials on Slilpp, the largest online marketplace for such data until it was seized in June 2021. In total, Kavzharadze’s activities rack up over $1.2 million in fraudulent transactions. The takedown of Slilpp is the result of joint effort between the FBI and international law enforcement agencies, and a significant disruption of a major cybercrime hub, which before the crackdown, had listed over 80 million instances of personal and financial information.
These operations demonstrate the growing effectiveness of global law enforcement in combating cyber threats and safeguarding digital ecosystems from criminal exploitation.
The Bad | SystemBC Malware Observed In Latest Black Basta-Linked Social Engineering Campaign
A recent cluster of intrusion attempts as part of an ongoing social engineering campaign has been linked to Black Basta, a ransomware group that first emerged in early 2022. Latest details on this activity outline Black Basta’s goals in stealing credentials by deploying a malware dropper known as ‘SystemBC’. In the observed attacks, the threat actor uses an email bomb as the initial lure, followed by phone calls via Microsoft Teams to offer fake solutions to targeted victims.
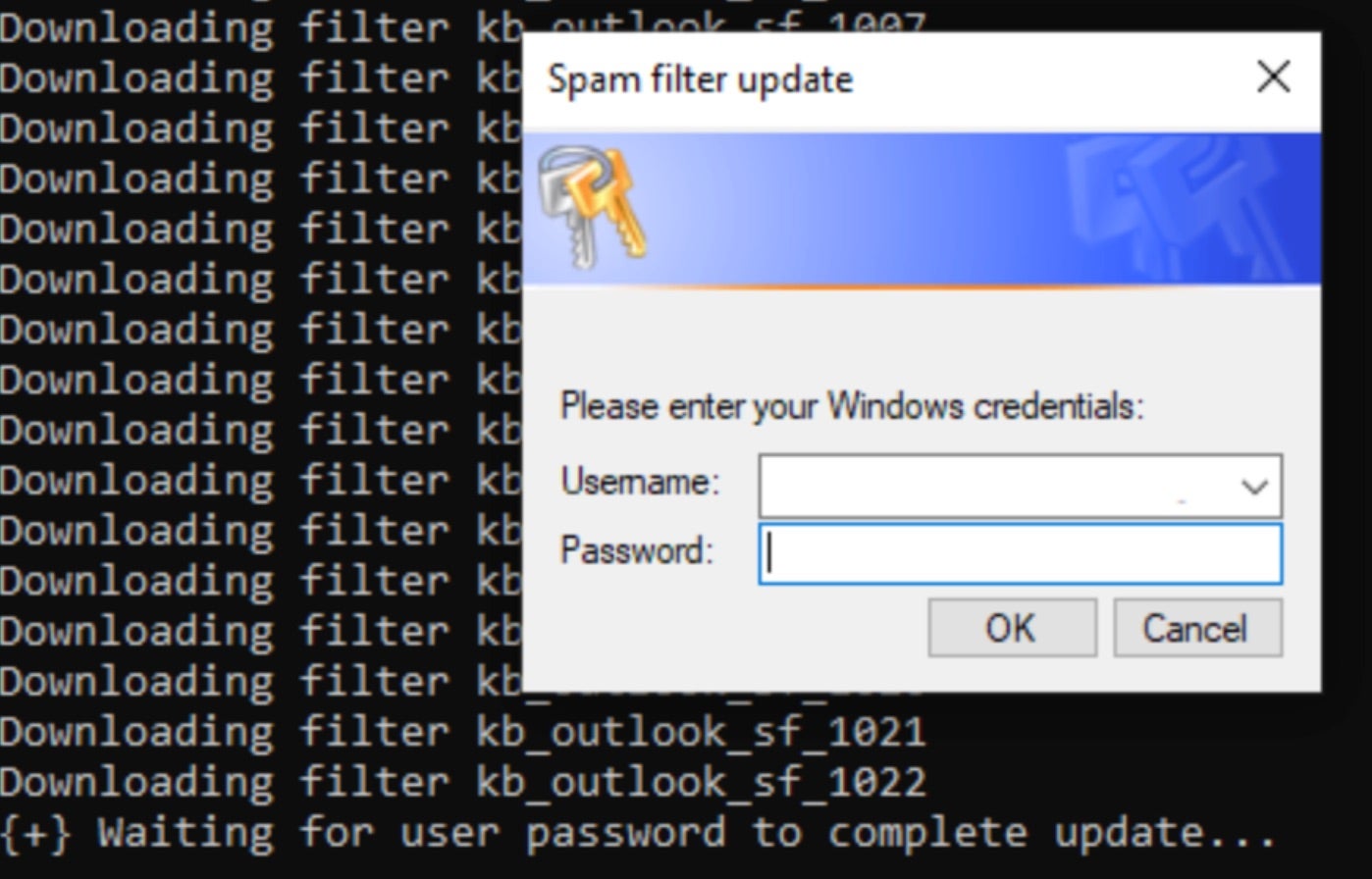
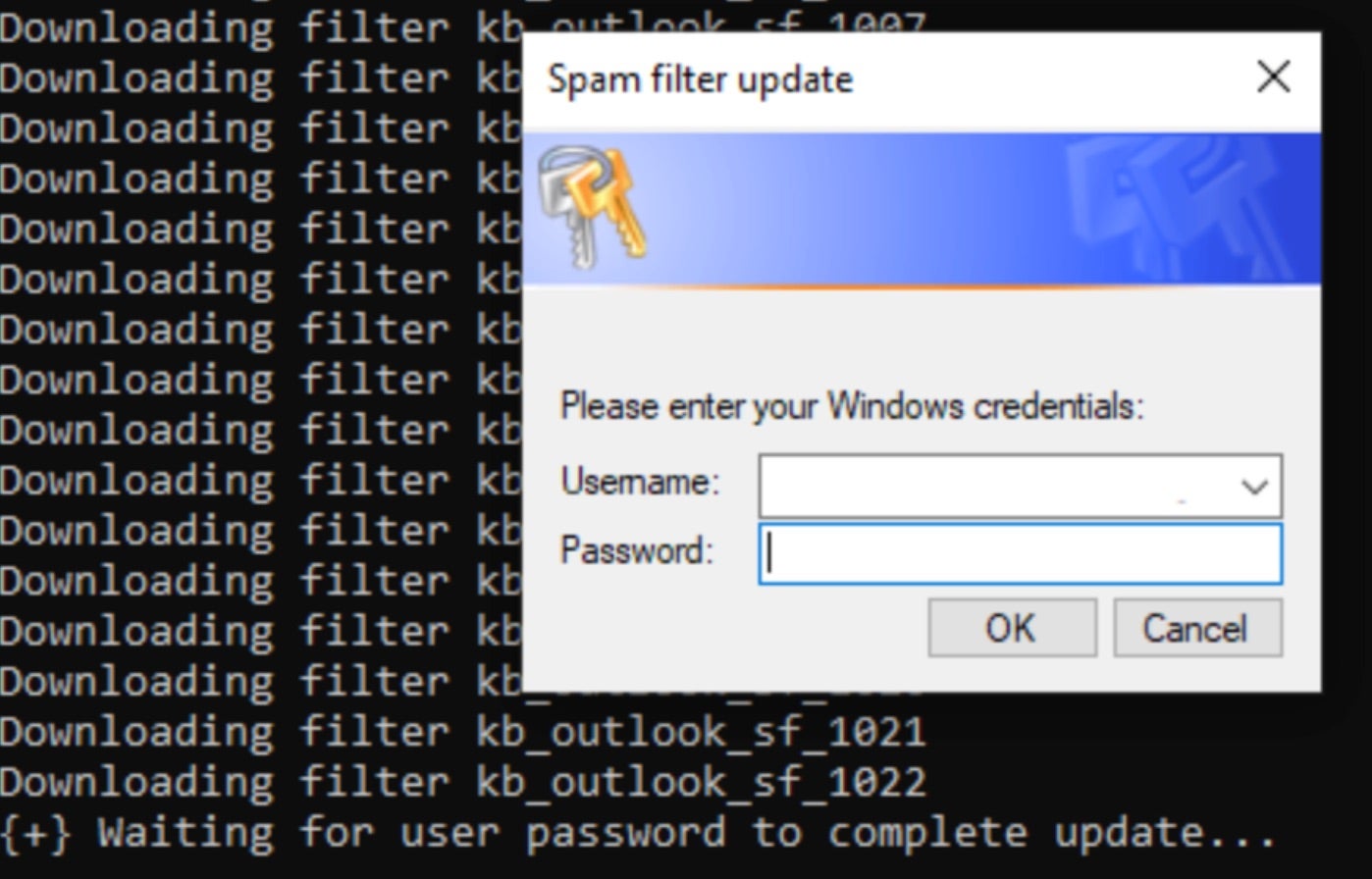
The attackers then convince users to download and install AnyDesk, a legitimate remote access software, which is used to deploy additional malware and exfiltrate sensitive data. A key component of these attacks is an executable called AntiSpam.exe, which falsely claims to install spam filters and prompts the victim to enter their Windows credentials. Following this, multiple binaries, DLL files, and PowerShell scripts are executed, including a Golang-based HTTP beacon connected to an attacker-controlled remote server, a SOCKS proxy, and the SystemBC malware. SystemBC, in particular, is popular with threat actors as it fortifies both C2 communications and persistence within affected environments.
Researchers note that this campaign is part of a broader uptick in phishing and social engineering attacks this year where malware loaders like GootLoader, SocGholish, and Raspberry Robin have become prevalent for facilitating ransomware attacks. These loaders make frequent splashes on dark web forums, usually offered via subscription models to make them accessible to low-level attackers with little technical skill.
These attacks show an ongoing need for robust detection and security measures to protect users from advanced social engineering-based schemes. Organizations are recommended to block unauthorized remote desktop tools and report suspicious calls or messages posing as internal IT staff.
The Ugly | Artifact Abuse Attack Vector Uncovered in Major GitHub Open-Source Projects
High-profile, open-source projects from several tech giants have been found leaking GitHub authentication tokens in CI/CD workflows via GitHub Actions. Affecting the likes of Google, Microsoft, AWS and more, these exposures pose significant risks, allowing attackers to gain unauthorized access to private repositories, steal source code, or inject malicious code.
New research published this week outlines a combination of risk factors linked to the discovery, including user misconfiguration, use of insecure default settings, and a lack of security audits and checks. These risks have led to tokens being leaked, something commonly known as an “ArtiPACKED” attack. In this kind of attack, the first key vulnerability lies in the ‘actions/checkout’ action, which clones repository code during workflow runs. By default, this action stores the GitHub token in a hidden .git directory.
If users mistakenly upload this directory as part of an artifact, the token and other sensitive information like API keys or cloud access tokens become exposed. CI/CD pipelines that use environment variables to store tokens pose an additional risk. If these variables are logged, they can be inadvertently included in uploaded artifacts, providing threat actors with another avenue for exploitation.
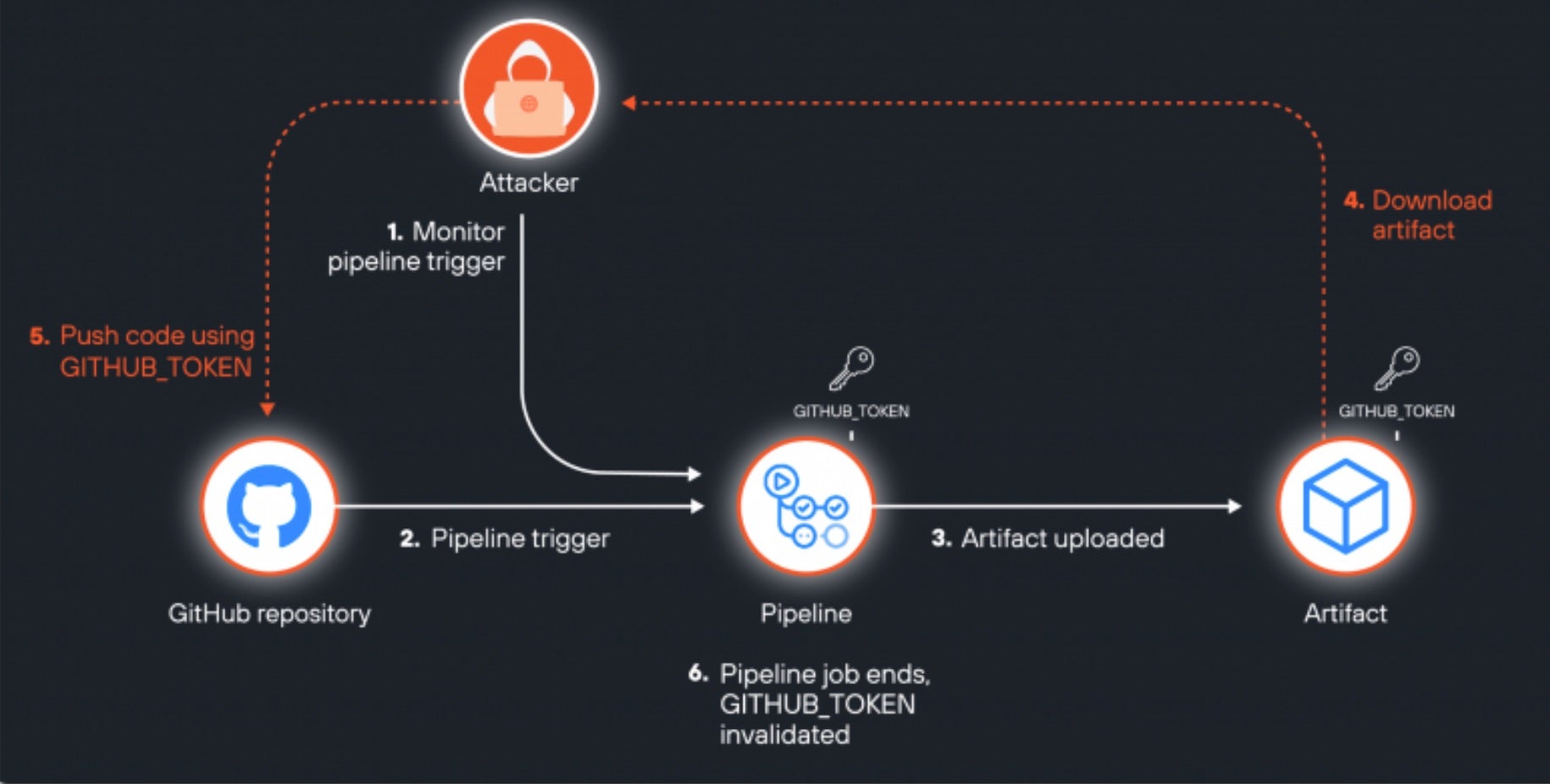
In total, security researchers have found 14 cases of token exposure in popular open-source projects. While the discovery has led to some remediation efforts from repository owners, root issues remain unresolved with the developer platform placing the onus on users to understand and evaluate their risks and exposures to prevent leaks. GitHub users are recommended to avoid uploading entire directories, ensure their logs are sanitized, and review all CI/CD configurations. Users can also adjust default settings and limit token permissions in workflows to further reduce the risk of unauthorized access.
如有侵权请联系:admin#unsafe.sh