2024-8-20 07:30:18 Author: securityboulevard.com(查看原文) 阅读量:3 收藏

Attackers are constantly refining their techniques for advanced phishing attacks to exploit the trust inherent in our digital systems. A recent incident we’ve captured highlights the alarming sophistication of modern phishing attempts, demonstrating how cybercriminals leverage trusted enterprise solutions to deceive even the most vigilant users. Let’s break down this attack and explain how our cutting-edge defenses, powered by machine learning, computer vision, social graph analysis, generative AI, and our virtual browser cloud, are crucial in identifying and blocking these threats. If you’d like to learn more and protect your organization from advanced phishing attacks, make sure to register here.
The Anatomy of an Advanced Phishing Attack
The attack in question is a masterclass in social engineering, exploiting the trust associated with popular enterprise solutions. The cybercriminals crafted a convincing email masquerading as an internal invoice from Coupa (see Figure 1, element ‘A’), a widely used procurement-to-pay platform. The email purportedly contained an invoice for Salesforce (see Figure 1, element ‘B’), a critical customer relationship management tool for many businesses.
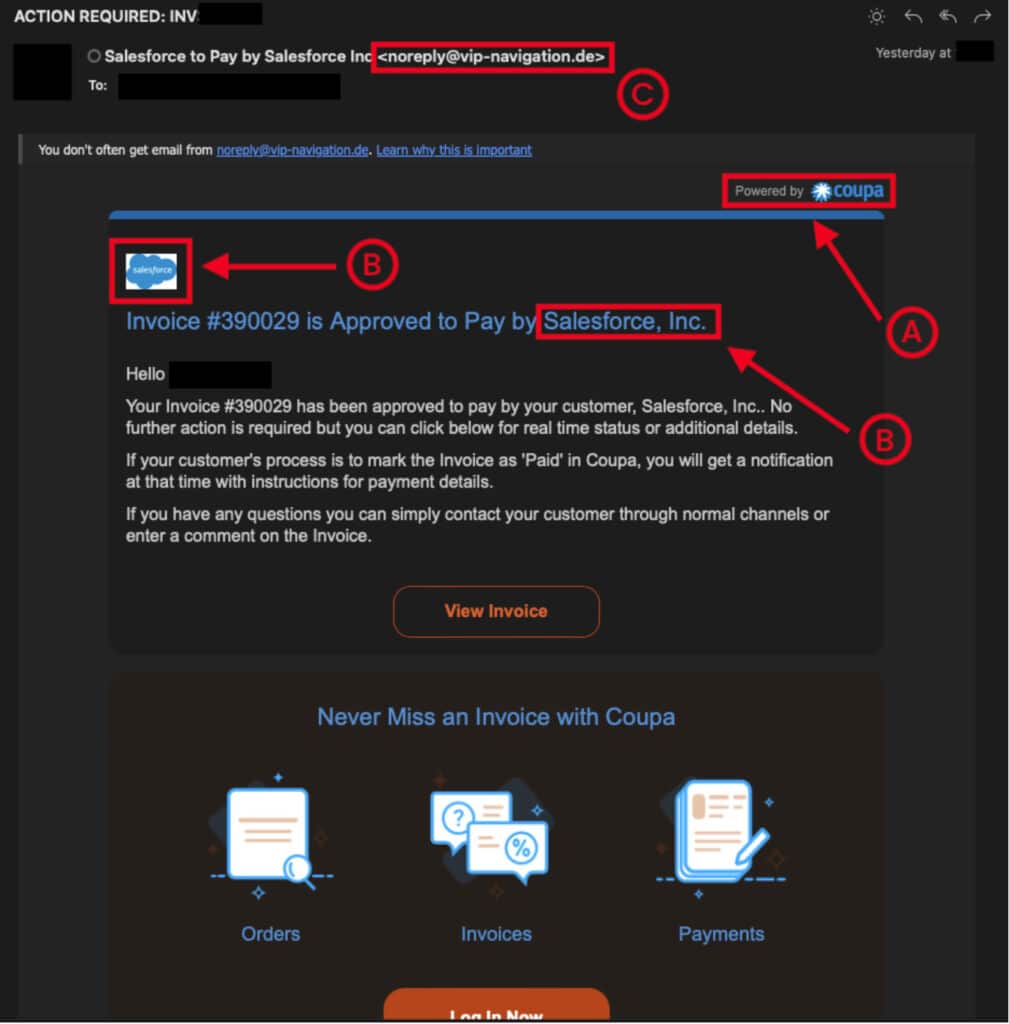
Figure 1. Inbound Email Malicious Indicators with Identifiers
Upon clicking the link, users would be directed to a page hosting what appeared to be a OneDrive for Business PDF document (see Figure 2). This page leverages user psychology by utilizing the Salesforce brand name (see Fig. 2, element A), but also includes an extremely suspicious link with a russian top-level domain (TLD) (see Fig. 2, element B).
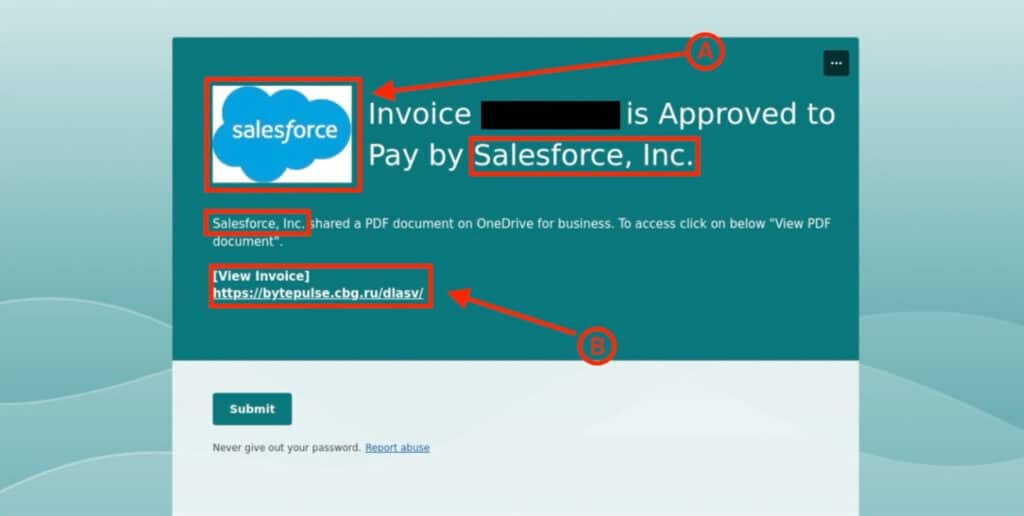
Figure 2. Malicious OneDrive for Business PDF document
This is where the true danger lies. Downloading this PDF could trigger a variety of malicious actions:
- Execution of hidden malware within the attachment
- Sideloading of malicious web content
- Credential harvesting without browser engagement
The attackers cleverly exploited the routine nature of invoice processing, betting that in the high-volume environment of accounts payable, this fraudulent invoice might slip through unnoticed.
Leveraging Trusted Domains
One particularly insidious aspect of this attack was the use of a compromised legitimate domain: vip-navigation.de (see Figure 1, element ‘C’). By hijacking a real website, the attackers added an extra layer of credibility to their scheme, making it even more challenging for traditional security measures to detect. For a closer look at this, register here.
The Deceptive Details
The level of detail in this phishing attempt is striking. The landing page included logos from both Coupa and Salesforce, lending an air of authenticity to the scam. Even more cunningly, the page featured a fake “Report Abuse” link, a common trust signal on legitimate sites. This small touch serves to further disarm potential suspicions, showcasing the meticulous planning behind these attacks.
Defending Against Advanced Threats
At SlashNext, we recognize that traditional security measures are no longer sufficient to combat these sophisticated attacks. Our approach leverages a suite of advanced technologies to provide comprehensive protection:
- Machine Learning: Our AI models are trained on vast datasets of both benign and malicious content, allowing them to identify subtle patterns indicative of phishing attempts.
- Computer Vision: By analyzing the visual elements of web pages and emails, we can detect brand spoofing and other visual cues that might escape text-based analysis.
- Social Graph Analysis: We map the relationships between various online entities to identify anomalous connections that might indicate malicious activity.
- Generative AI: This technology allows us to predict and simulate potential attack vectors, staying one step ahead of cybercriminals.
- Virtual Browser Cloud: Our cloud-based virtual browsers safely render and analyze suspicious content, providing a secure environment for threat detection without risking end-user systems.
Real-Time Threat Detection and Prevention
In the case of the attack described above, our multi-layered approach would have flagged several suspicious elements:
- The mismatch between the sender’s domain and the purported origin of the invoice
- The use of a compromised legitimate domain (vip-navigation.de) for hosting malicious content
- Visual inconsistencies in the spoofed Coupa and Salesforce branding
- The presence of a fake “Report Abuse” link
- Anomalous behavior in the PDF download process
By correlating these signals in real time, our system can block the threat before it reaches the end-user, preventing potential data breaches or financial losses.
The Importance of Continuous Evolution
As cybercriminals continue to refine their tactics, our defenses must evolve in tandem. SlashNext’s commitment to ongoing research and development ensures that our AI models are constantly updated to recognize new threat patterns. This proactive approach is crucial in maintaining an effective defense against the ever-changing landscape of phishing attacks.
Conclusion
The sophistication of modern phishing attacks demands an equally sophisticated defense. By harnessing the power of machine learning, computer vision, social graph analysis, generative AI, and cloud-based threat analysis, SlashNext provides a robust shield against even the most advanced phishing attempts. As we continue to innovate, we remain committed to staying one step ahead of cybercriminals, ensuring the safety and security of our clients in an increasingly complex digital world. To discover how these cutting-edge technologies can protect your organization from evolving cyber threats, make sure to register here.
The post Unmasking the Sophisticated: How AI-Powered Defenses Thwart Advanced Phishing Attacks first appeared on SlashNext.
*** This is a Security Bloggers Network syndicated blog from SlashNext authored by Barry Strauss. Read the original post at: https://slashnext.com/blog/how-ai-powered-defenses-thwart-advanced-phishing-attacks/
如有侵权请联系:admin#unsafe.sh