2024-8-21 01:1:28 Author: cyble.com(查看原文) 阅读量:5 收藏
Key Takeaways
- Attacks on the software supply chain have occurred at a rate of at least one every two days in 2024.
- U.S. companies and IT providers have been by far the most frequent targets, accounting for one-third of all software supply chain attacks.
- The UK, Australia, Germany, India and Japan have also been frequent targets, as have the aerospace & defense, healthcare and manufacturing sectors.
- These attacks are particularly damaging and costly because of their multiplication factor on downstream victims and trusted access to customer environments.
- Even when the codebase isn’t breached, customer databases contain critical information for threat actors to use in phishing, spoofing and credential attacks.
- A defense-in-depth approach is required to reduce risk, based on principles of zero trust, cyber resilience, and secure code practices.
Overview
Software supply chain attacks burst into public consciousness in 2020 with news of the SolarWinds Orion attack, and a Kaseya VSA ransomware attack in mid-2021 further underscored the risks that third-party software suppliers can pose to their unsuspecting customers.
Attacks resulting from infiltration of an IT supplier’s code base are relatively rare, but the software supply chain – the code, dependencies and applications that all modern organizations rely on – is a source of near-constant vulnerabilities and cyberattacks that place all organizations at risk.
Because of their trusted access to IT environments, a category of security tools called third-party risk management (TPRM) has evolved to monitor the security of trusted providers – and to alert downstream users when the risk from these services has increased.
Because of their trusted access to customer environments, third-party providers are one of the biggest targets for threat actors. While codebase breaches are relatively rare, a breach of any partner’s business environment can lead to sensitive data being leaked that could give attackers a critical advantage in breaching other environments, including phishing, spoofing and credential attacks. And because of the interconnectedness and increasing digital nature of the physical supply chain, any manufacturer or supplier with downstream distribution can be considered a cyber risk.
We’ll look at the frequency and nature of supply chain attacks in 2024 before we focus on important defenses that all organizations with trusted partners should have in place.
How Common Are Software Supply Chain Attacks?
Successful supply chain attacks have become a near-daily occurrence in 2024, according to Cyble threat intelligence data.
Cyble’s dark web monitoring found 90 cybercriminal claims of successful supply chain attacks in a six-month period that encompassed February 2024 to mid-August 2024.
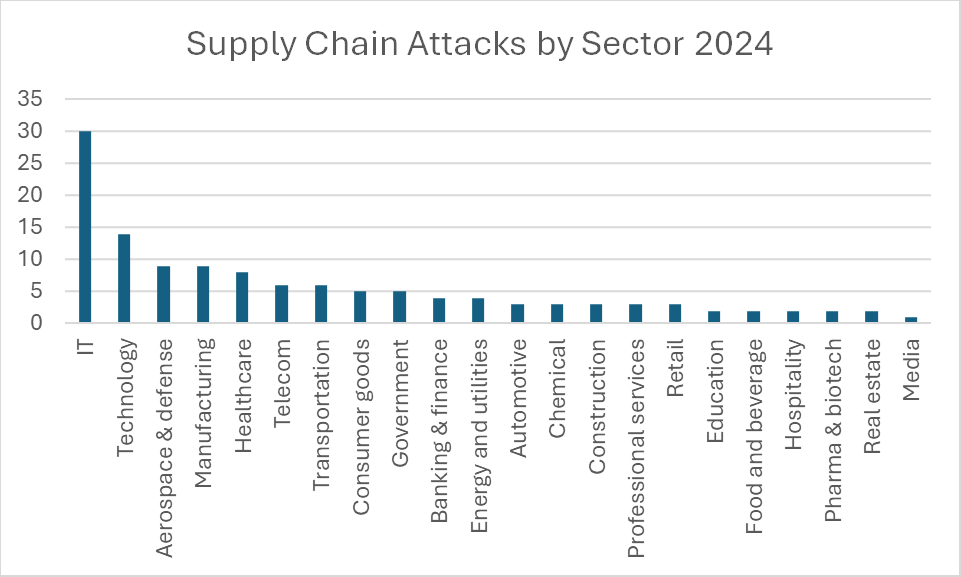
Not surprising given their reach, IT providers suffered the greatest number of those breaches, 30, or one-third of the total, followed by technology product companies, which experienced 14 of the 90 breaches.
Aerospace & defense (9 breaches), manufacturing (9 breaches), and healthcare (8 breaches) were the next most frequent victims of supply chain attacks.
In all, 22 of the 25 sectors tracked by Cyble threat researchers have experienced a supply chain attack in 2024 (chart below).

The U.S. experienced by far the greatest number of supply chain breaches claimed on the dark web – 31 in all – followed by the UK (10). Germany and Australia each had five, and Japan and India had four each.
A Look at the Nature of Supply Chain Attacks in 2024
Supply chain attacks in 2024 have ranged from the theft of business and customer data to the theft and hijacking of source code, but regardless of the sensitive data access, all such attacks pose a serious threat because of the reach of these suppliers. A recent report from Cyentia found that 99% of Global 2000 companies are directly connected to a vendor that has been hit by a supply chain breach. Here is a look at the range and nature of supply chain attacks and breaches thus far in 2024.
jQuery
On July 5, a supply chain attack on the JavaScript npm package manager involving trojanized versions of jQuery was discovered by cybersecurity researchers. The attack targeted the popular JavaScript library jQuery by distributing trojanized versions through npm, GitHub, and jsDelivr. The attackers modified the legitimate jQuery code to exfiltrate sensitive form data from websites. The attack’s scope was significant, impacting multiple platforms and package names. The attackers used tactics like obfuscation and misleading version warnings. The attack underscored the urgent need for developers and website owners to verify package authenticity and scrutinize code for suspicious modifications to mitigate supply chain attacks.
Polyfill
In late June, a widespread supply chain attack hit over 100,000 websites, including many well-known names, originating from a fake domain that impersonated the Polyfill.js library to inject malware that redirected users to sports betting or pornographic sites. The malware dynamically generated based on HTTP headers, making detection challenging. The attack highlighted the risks of using external code libraries and the importance of vigilance in website security. Mitigation steps included removing cdn.polyfill.io, replacing it with secure alternatives, and caution against relying on unknown entities for JavaScript. The incident underscored the security implications of third-party scripts and the potential for malicious takeovers of widely deployed projects.
Programming Language Breach
On July 26, threat actor (TA) IntelBroker, posting on the BreachForums cybercrime forum, claimed to offer unauthorized access to a node package manager (npm) and GitHub account pertaining to an undisclosed programming language, for US $20,000. The TA said the offer also includes access to the X (Twitter) account of the associated organization with about 100,000 followers, and private repositories with privileges to push and clone commits. Below is a screenshot of the TA’s claims:

CDK Global Inc.
On June 19, automotive dealership software provider CDK Global Inc. was hit by a ransomware attack reportedly perpetrated by the Black Suit ransomware group that disrupted sales and inventory operations of many North American auto dealers, including large dealer networks belong to Group1 Automotive Inc., AutoNation Inc., Premier Truck Group, and Sonic Automotive, all of which informed U.S. authorities that they experienced a multi-week service outage and disruption to dealership operations, including those supporting sales, customer relationship management systems, inventory and accounting functions. However, none of the CDK Global customers reported any malicious activity within their networks, suggesting the attack may have been limited to a service disruption.
Insula Group Pty Ltd.
On July 25, BianLian ransomware group claimed to compromise Australia-based Insula Group Pty Ltd. The company provides software solutions used in residential construction and finance broking industries. The ransomware group allegedly exfiltrated 400 GB of documents that included project data, construction data, client information, server data, and company source code.
Access Offered to More than 400 Companies
On June 15, IntelBroker, again appearing on BreachForums, offered to sell unauthorized access to more than 400 companies compromised via an undisclosed third-party contractor. The data allegedly included access to integration services of Jira, Bamboo, Bitbucket, GitHub, GitLab, SSH, SFTP, DA, Zabbix, AWS S3, AWS EC2, SVN and Terraform. Additionally, the TA also provided revenue of four significant impacted organizations. Open-source research based on the companies’ revenue and location suggested the impacted organizations could be Lockheed Martin Corporation, Samsung Electronics Co Ltd, General Dynamics, and Apple Inc.
Smart-ID
On June 21, the functionality of the Smart-ID electronic identification and authorization app was disrupted after a cyberattack, resulting in difficulties accessing internet banking and other e-services in Latvia, Estonia and elsewhere.
Cartier International SNC
On Aug 5, IntelBroker leaked data on BreachForums allegedly pertaining to Cartier International SNC, a France-based luxury goods brand. The TA said the data was stolen from the U.S,-based BORN Group, a global digital marketing agency that specializes in digital transformation and commerce solutions. The TA claimed the data was exfiltrated from AWS S3 storage and also leveraged a local file inclusion (LFI) vulnerability, which led to the exposure of internal files, images, and source code.
Code Base Injection Not Required for Supply Chain Attack
Threat actors don’t need to inject malicious code into a tech company’s code base to hack the software supply chain – they only need to exploit a zero-day or unpatched flaw that already exists, as happened in recent attacks hitting customers of MOVEit and Ivanti. And “software dependences,” like an open-source component used in proprietary software, can also introduce vulnerabilities, further expanding the attack surface.
The software supply chain falls under the broader category of third-party risk management (TPRM), the partners, vendors, service providers, suppliers and contractors who can unwittingly introduce risk into an organization’s environment. A number of studies have found that more than half of all organizations have experienced a third-party breach, and these breaches tend to be more costly than incidents that occur within an organization.
Here are some of the best practices and technologies organizations can use to protect against these growing third-party risks.
Zero Trust and Cyber Resilience Help Control Supply Chain Risks
In cybersecurity, organizations should always “assume breach” and trust no one, and this applies to third-party partners too. If security teams assume that no one can be trusted and that no one can be given safe access to assets, they architect accordingly, with critical systems and data isolated with security controls and duplicated with ransomware-resistant backups.
The concept of cyber resilience has been repeatedly stressed in recent years. Instead of focusing solely on the network perimeter and endpoints, resilience and recovery should be built around critical applications and data using practices such as:
- Network microsegmentation
- Strong access controls, allowing no more access than is required, with frequent verification
- A strong source of user identity and authentication, including multi-factor authentication and biometrics, and machine authentication with device compliance and health checks
- Encryption of data at rest and in transit
- Ransomware-resistant backups that are immutable, air-gapped and isolated as much as possible
- Honeypots that lure attackers to fake assets for early breach detection
- Proper configuration of API and cloud service connections
- Monitor for unusual activity with SIEM, Active Directory monitoring, and data loss prevention (DLP) tools
- Routinely assessing and confirming controls through audits, vulnerability scanning and penetration tests
Best Practices for Secure Development – and Third-Party Risk Management
Ideally, the most effective place to control software supply chain risks is in the continuous integration and development (CI/CD) process – and customers of these services also have a role to play here.
Carefully vetting your partners and suppliers and requiring good security controls in contracts are ways to improve third-party security. Threat intelligence services like Cyble will help you assess partner and vendor risk – and alert you to places where you may want to shore up your own security defenses. Cyble’s third-party risk intelligence module evaluates partner security in areas such as cyber hygiene, dark web exposure, spoofing activities, and attack surface and network exposure, noting specific areas for improvement, while Cyble’s AI-powered vulnerability scanning capabilities can help you find and prioritize your own web-facing vulnerabilities.
The U.S. National Institute of Standards and Technology (NIST) offers a number of guides on supply chain risk management and best practices. These are important resources both for developers and companies evaluating third-party providers. Make security reviews and requirements part of your procurement process from the start.
Here are some questions you should ask vendors and service providers as part of a digital supply chain risk assessment:
- Is the vendor’s software and hardware design process documented, repeatable and measurable?
- Does the vendor maintain a software component inventory such as a software bill of materials (SBOM) that spells out the components and other attributes of software developed by the vendor and third parties?
- Is the mitigation of known vulnerabilities factored into product design through product architecture, run-time protection techniques, and code review?
- How does the vendor stay current on emerging vulnerabilities? What are vendor capabilities to address new “zero day” vulnerabilities?
- What controls are in place to manage and monitor production processes?
- How is configuration management performed? Quality assurance? How is testing done for code quality and vulnerabilities?
- What levels of malware protection and detection are performed?
- What steps are taken to make sure products are tamper-proof? Are the back doors closed?
- Are physical security measures documented and audited?
- What access controls, both cyber and physical, are in place? Are they documented and audited?
- How is customer data protected, stored, retained, and destroyed?
- What type of employee background checks are conducted and how frequently?
- What security practice expectations are there for upstream suppliers, and how is adherence to these standards assessed?
- How secure is the distribution process? Have approved and authorized distribution channels been clearly documented?
Services like Cyble’s third-party risk intelligence can help you get started on this process. As more organizations make security a buying criterion, vendors will be forced to respond with better security controls and documentation.
Related
如有侵权请联系:admin#unsafe.sh