
2024-8-22 18:42:46 Author: securityboulevard.com(查看原文) 阅读量:5 收藏

Did it ever cross your mind to ask if your password can defend your sensitive info on the web all by itself? In the digital world of today, where cyber threats are rapidly developing, the traditional way of protecting the system with single password has become more and more insecure.
Therefore, it is the user who is more exposed to such cyberattacks. Just to mention, more than 81% of data breaches are associated with weak or stolen passwords. This scary fact clearly emphasizes how crucial it is to impose stronger security techniques.
MFA can be your key tool in protecting digital security. It works by asking for more than one way to prove your identity, like a password, a pin, or a fingerprint. This extra step makes it much harder for someone to break into your account. In fact, MFA can stop almost all attempts to hack into accounts, according to Microsoft.
So, why should MFA be on your radar?

In this blog, we’ll explore how MFA works, its vital role in modern cybersecurity strategies, and why it should be a standard practice for both organizations and individuals.
Definition of Multifactor Authentication
Multifactor authentication (MFA) refers to a security scheme that requires more than one method of authentication from different independent authentication units to verify a user’s identity for login or other services. MFA includes at least two authentication factors different together like fingerprints. This technique provides a layered defense and makes it more difficult for an unauthorized person to gain access to a target such as a physical location, computer equipment, network, or database.
Significance of MFA in enhancing online security
MFA is there to make sure only the right person can get in. Whether it’s securing your online banking, defensive private data, or ensuring that your employer’s community remains secure, MFA acts as a critical barrier.
Cybersecurity experts often say that “the best password is the one you never have to remember,” but just using passwords can be dangerous. Passwords can be taken, guessed, or even bought on the dark web.
MFA, however, calls for additional evidence—like a fingerprint or a one-time code sent for your telephone—making it tougher for attackers to gain access.
As cybersecurity professional Bruce Schneier aptly places it, “Security is a process, not a product.” Implementing MFA is an important step in that technique. A Verizon’s study found that 61% of facts breaches involved stolen or compromised credentials. MFA extensively mitigates this chance by making unauthorized access a lot more difficult.
Types of Multifactor Authentication
MFA typically involves combining different types of factors: knowledge-based, possession-based, and inherence-based. Each has its unique advantages and potential challenges.
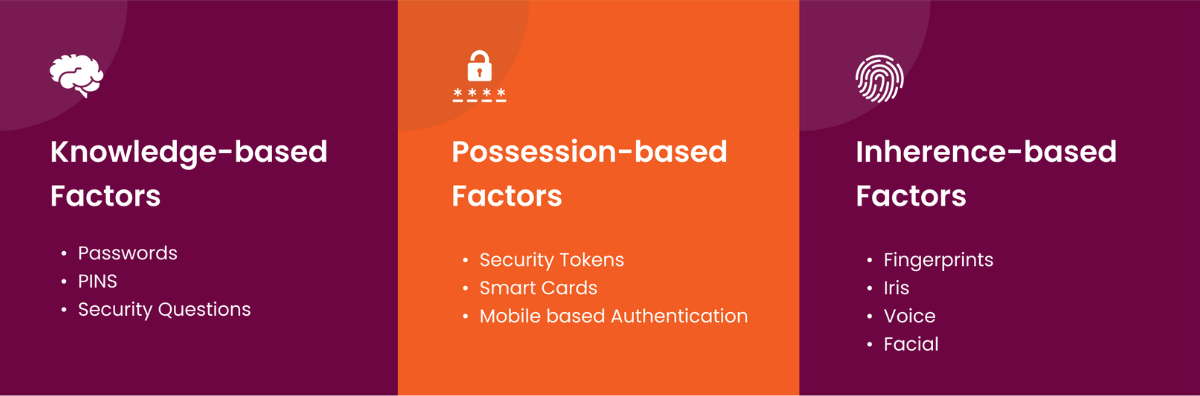
Knowledge-based Factors
Knowledge-based factors require users to provide something they know. This category includes:
- Passwords
- PINs (Personal Identification Numbers)
- Answers to security questions
While these methods are familiar and easy to implement, they come with risks. To mitigate this, it’s essential for users to create complex passwords and avoid reusing them across multiple sites.
Possession-based Factors
Possession-based factors involve something the user physically has. Examples include:
- Security tokens (hardware devices that generate secure codes)
- Smart cards
- Mobile phone authentication apps that generate time-limited codes
This method adds a layer of security by requiring physical access to a device. 87% of technology companies use Multi-Factor Authentication (MFA). 95% of MFA users choose software like mobile apps for extra security.
Inherence-based Factors
Inherence-based factors, often referred to as biometrics, include:
- Fingerprint scans
- Facial recognition
- Voice recognition
- Iris scans
These methods rely on unique physical characteristics, offering a high level of security. Since biometric data is hard to replicate or steal, it provides robust protection.
Benefits of Implementing Multifactor Authentication
The beauty of MFA lies in its simplicity yet effectiveness. Knowing that your accounts are secured by multiple checkpoints lets you breathe easier and confidently.
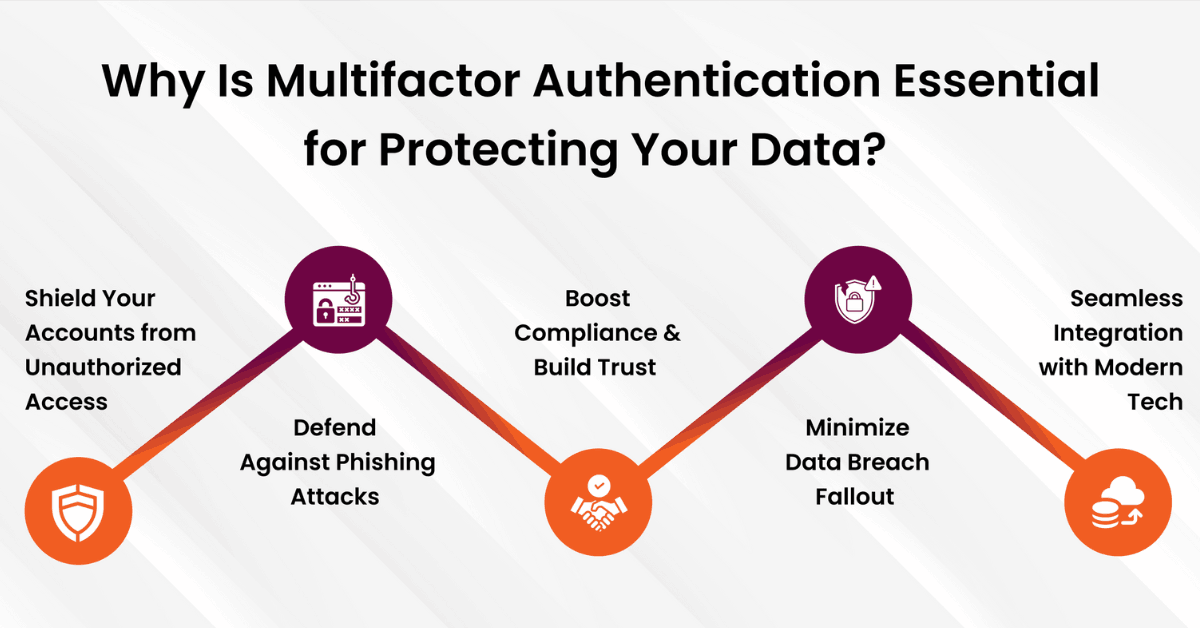
Here are few explained benefits of MFA:
-
Reduced Risk of Unauthorized Access: Due to requiring multiple forms of verification, MFA makes it very hard for attackers to access your account, even if they somehow get access to your password. -
Protection Against Phishing Attacks: MFA provides extra security layers that stop unauthorized access if a phishing attack captures your password. -
Greater Compliance and Trust: MFA helps organizations act according to field regulations and enhances customer trust since it serves as proof of practicing tight security measures. -
Reduced Data Breach Impact: If there is a leakage of data, MFA limiting the damage requires extra authentication beyond a compromised password. -
Smooth Technology Integration: State-of-the-art devices and apps can be integrated seamlessly with MFA to offer greater security without disrupting user experience.
Common Challenges in Implementing Multifactor Authentication
Implementing Multifactor Authentication (MFA) is essential for strengthening security, but it presents challenges that require thoughtful solutions:
User resistance:
Implementation of MFA often meets resistance because users may find additional steps inconvenient. However, this barrier can be reduced by highlighting the safety benefits and potential risks of using MFA.
Integration complexity:
Integrating MFA into existing systems can be difficult, especially in older projects. Ensuring compatibility with all applications requires careful planning and technical expertise, making it a complex process.
Cost considerations:
MFA implementation costs including hardware, software, and IT services can be substantial. However, when these costs are weighed against the potential economic impact of a data breach, they make the investment worthwhile.
What are the best practices for setting up multi-factor authentication?
Setting up multifactor authentication is a good idea of being extra careful about security, but what’s the best way to do it? Here’s a breakdown of best practices to ensure your MFA setup is both effective:
Select the Best Security Options
Not every multi-factor authentication (MFA) method offers the same level of security. Although SMS codes provide some protection, they are not as safe as other choices. Think about adopting app-based tools such as Google Authenticator or Authy or using physical devices like YubiKey for added security. Ask yourself: Am I using the safest option I can?
Educating users about MFA
It is essential to train your team about MFA to maximize the effectiveness of MFA. Training should include:
- Reasons why MFA is critical for security
- Step-by-step guidance on how to enroll and use MFA systems
- Troubleshooting common issues
- Best practices for maintaining security, such as not sharing tokens or authentication codes.
Regularly reviewing and updating security measures
Technology evolves, and so do threats. MFA settings and configurations should not be stagnant. Regular reviews and updates are necessary to adapt to new security threats. This involves:
- Analyzing security breach attempt patterns to adjust MFA settings
- Updating the authentication software and hardware
- Reassessing user roles and access rights to ensure they are still appropriate
- Conducting periodic audits and compliance checks to ensure MFA effectiveness
Ask yourself: When was the last time you checked your MFA settings?
Pros and Cons of MFA: Is It Worth the Extra Step?
When it comes to securing our online accounts, Multifactor Authentication (MFA) often pops up as a go-to solution. But is it worth the extra step?
Pros of MFA
- Enhanced Security: MFA provides additional security by requiring more than just a password. Even if someone had your password, they would also need a second method of authentication, such as a code sent by text or your fingerprint, etc. making it very difficult to access you mathematically without permission.’
- Reduced risk of data breaches: A Microsoft study showed that MFA can withstand more than 99.9% of attacks that attempt to hijack accounts. This dramatically reduces data traffic, preserving all sensitive personal and business information.
- Options to use: Today’s MFA systems offer many ways to verify your identity, including text codes, email verification, fingerprint scanning and special software. This technique allows people to choose the system that works best for them and is easy to use.
- Compliance and trust: Companies using MFA can help them comply with government regulations and inspire customers and partners to feel more confident. Knowing that extra security is in place makes everyone feel more comfortable about protecting their data.
Cons of MFA
- Usability Challenges: MFA can sometimes be perceived as a problem, especially if users find it difficult to find their second product. For example, losing a phone or being in an area with poor signal can complicate the authentication process.
- Cost and Implementation: Establishing an MFA, especially at a large institution, can be time-consuming and expensive. It requires investment in technology and staff training to ensure a seamless adoption.
- Potential for False Sense of Security: While MFA greatly improves safety, it is not foolproof. Over-reliance on MFAs can lead to relief in other safety practices, and potentially vulnerabilities elsewhere.
- User Resistance: Some users may resist accepting MFA because of perceived discomfort or lack of understanding of its benefits. This can lead to compliance vulnerabilities and potential security gaps.
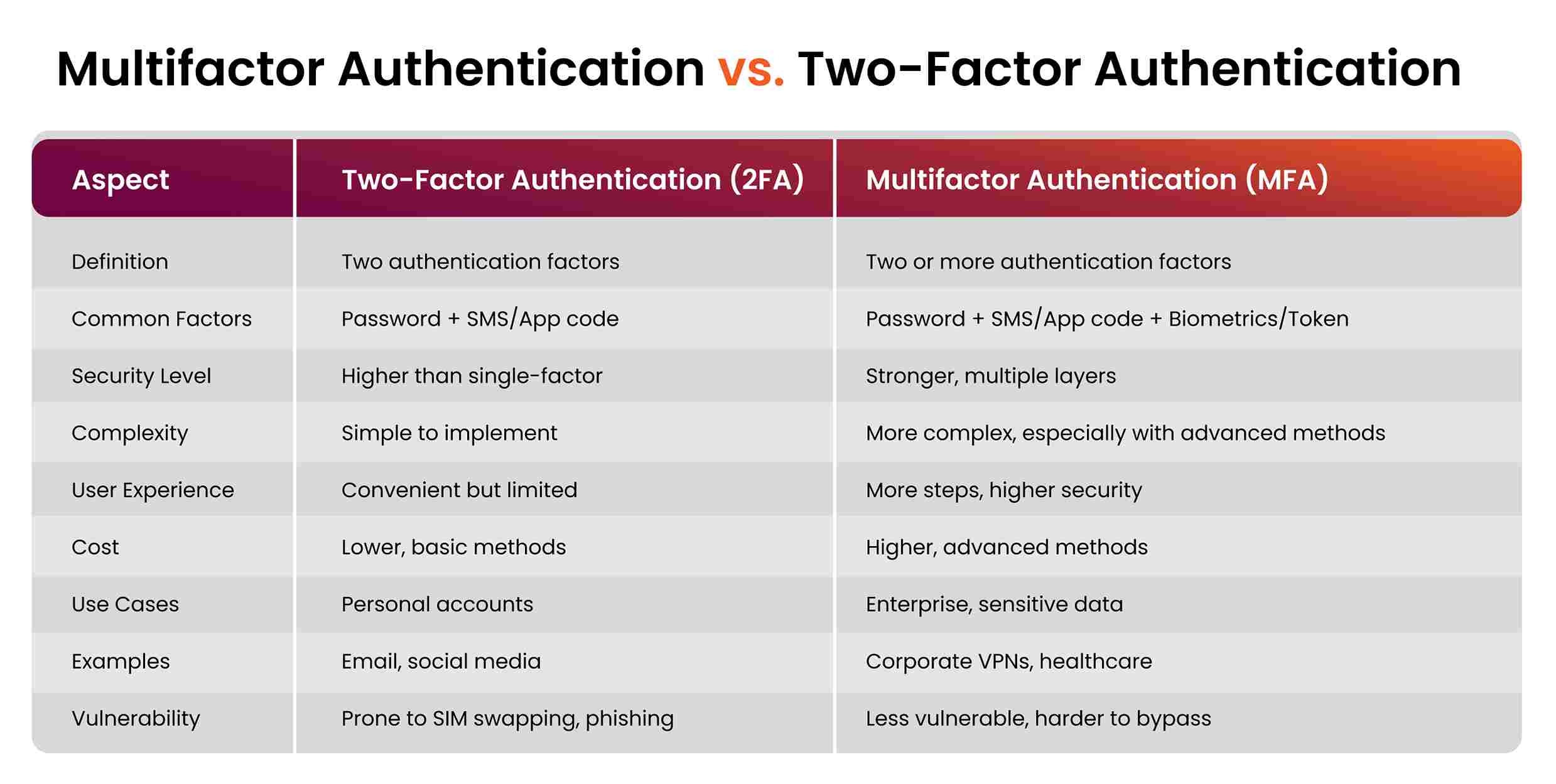
Multifactor Authentication vs. Two-Factor Authentication
In cybersecurity, it’s important to understand how Multi-factor Authentication differs from Two-Factor Authentication. It’s simply that 2FA is one of the methods applied in MFA. Basically, they are similar in that both force users to prove their identity before systems give access or share data but differ highly in terms of their complexity and level of security.
Two-Factor Authentication (2FA): This involves two factors or modes for authentication. Normally, it would be something you know, like a password or PIN, and something you have, such as a smartphone app to receive the code or even a hardware token. This is much more secure compared to just a simple password method but can still be compromised if one of the factors is divulged.
Multifactor Authentication (MFA): Several studies suggest that MFA improves security by demanding more than one factor for verification, hence significantly reducing the risk of any unauthorized access. These may include the following factors:
- Something you know—a password or a PIN.
- Something you have: security token or smartphone app.
- Something you are: This would include biometric data, such as fingerprints or facial recognition.
This makes MFA better in terms of security because it will require one to compromise quite several independent credentials in case of a breach, making it very hard for the cybercriminal to get through an attack.
How Parablu Ensures MFA for Protecting Customer’s Data
Parablu has MFA at the forefront to provide a seamless user experience while ensuring security. We do this by baking Multi-Factor Authentication into its security protocols. In that respect, even in the unlikely event of somebody getting hold of your password, it is further authenticated with another verification step, like a code sent to your phone, before your data can be accessed.
Our solution calculates risk by looking at user behavior and request context, using this information to adapt the level of authentication requirements dynamically. Where there is least risk involved, there will likely be straightforward authentication; high-risk situations will trigger additional authentication factors.
Parablu continually assesses its MFA mechanisms for emerging threats and updates them whenever required to keep them effective. Finally, with robust practices in place for MFA, Parablu protects customer data using advanced, multi-layered security measures that greatly reduce the risk of data breaches and foster trust in customers’ digital interactions.
Today, one of the strongest pillars that holds up cybersecurity defenses is multifactor authentication. Other than the requirement for multiple layers of verification in a multifactor authentication process, it almost eliminates the risk of unauthorized access and makes sensitive data more secure against sophisticated cyber threats. For both individuals and organizations, MFA offers one of the most necessary actions needed to secure online interactions and transactional data. In today’s digitally developing cyber threats landscape, the adoption of MFA is no longer a recommendation but a crucial step toward robust and resilient online security.
如有侵权请联系:admin#unsafe.sh
