
2024-8-22 21:0:56 Author: www.sentinelone.com(查看原文) 阅读量:5 收藏
Emerging technologies have given rise to CISOs becoming strategic in their company’s growth. CISOs are now expected to be key decision-makers, influencing corporate strategy and guiding their organizations through the complexities of the current age. They are slowly transitioning from being technical experts in security architecture, security operations, infrastructure security, and network security to visionaries in strategic cybersecurity and business growth. As they make this transition, it is increasingly vital for CISOs to understand the fundamentals of risk management.
While many general risk management elements are in practice for organizations as part of the risk mitigation process or, due to compliance and regulatory requirements, some key risk management fundamentals still need to be thoroughly understood by CISOs as they step into these strategic roles.
As CISOs take on more strategic responsibilities, they must apply cyber risk fundamentals as they work with other executive leaders to implement holistic security measures for all parts of the organization. This blog delves into the importance of cyber risk management fundamentals across all business operations, offering insights into how they can help current and future CISOs succeed.

The Challenge of Centralizing Risk Management Across the Organization
Traditionally, risk management is perceived as a non-technical skill that does not fall under the traditional scope of a security practitioner. While risk management is not a new concept for non-IT or non-security teams, it is often considered unfamiliar territory for IT and security professionals. For security leaders, there is commonly little to no formal training nor emphasis on understanding risk management fundamentals. In fact, many learn these skills on the job while facing the issue of fragmented risk responsibilities and requirements spread thinly across various business units.
Based on the cyber maturity of the organizations, Cyber Governance, Risk & Compliance (GRC) teams typically take the lead in managing cyber risk. However, they often do so in isolation from broader enterprise risk management activities, which can create a disconnect between security teams and the overall business strategy. This siloed approach can give the impression that risk management is not essential for the success of security teams.
Though CISOs are fit to offer subject matter expertise in niche tech areas, what’s missing is a holistic approach aligning risk-based business decisions across the entire organization. This knowledge gap becomes much more evident when CISOs engage with executives and the task of translating cyber risk to business terms begins to overshadow the rest of the discussion.
From SMBs to Large Enterprises | Integrating Cyber Risk into Business Strategy
Commonly, risk management is a directive driven by finance or legal teams to fulfill standard compliance requirements. This is especially the case for small and medium-sized businesses (SMBs) where there is no dedicated enterprise risk management team or available resources to help centralize risk management across all business units.
In such situations, security is approached in isolation and those responsible often do not try to link risk management with mitigation measures. This disconnect can hinder security teams from securing the necessary budget and support from senior management. Sometimes, cyber risk management is discussed only after a security incident has already occurred, or when a trend in the cyber threat landscape suddenly emerges. This reactive approach is no longer sufficient to keep businesses secure and profitable.
These challenges and the gaps are more evident today than in the past as CISOs increasingly step into strategic conversations. CISOs can facilitate collaboration across departments and ensure that security controls are implemented effectively and aligned with the organization’s overall objectives.
Addressing the Gaps in Enterprise Risk Management
Given the evolving risk landscape and rapid technology adoption across all industries, the rise in dependency on technology systems is what places the evaluation of cyber-specific risks firmly amongst the task of building out organizational risk strategy. Integrating cyber risk into enterprise risk is a collaborative effort where organizational leaders establish centralized risk management, which then trickles down and supports business units to implement risk response sub-strategies specific to their responsibilities.
As NIST describes, Enterprise Risk Management (ERM) requires identifying and understanding the various types of risk that an enterprise faces. This includes determining the probability that these risks will occur and estimating their potential impact. For an ERM program to be effective, it requires input from every department and the presence of a risk management lifecycle to be effective. Cyber risk is an integral part of ERM and has gained importance over the years because of increased digitization.
If there is no streamlined approach to the risk management function within the organization, CISOs can work collaboratively with other departments to discuss the need for a risk management program. Consulting with departments like finance and legal, for example, ensures that functional leaders can make informed decisions about the risk management component of security budgets and ROI discussions.
Understanding Risk Terminology, Concepts & the Risk Management Lifecycle
Risk Appetite and Risk Tolerance
The two fundamental concepts of risk management are risk appetite and risk tolerance. As referenced by NIST, risk appetite is the type and amount of risk that an organization, on a broad level, is willing to accept in its pursuit of value. Risk appetite is set by the senior management and provides direction for setting strategy and objectives. Risk tolerance is the organization or stakeholders’ readiness to bear the remaining risk after responding to or considering the risk to achieve its objectives. These terms are the basis for CISO decision-making and help frame why certain risk response decisions are made and how resources are allocated for carrying out these decisions.
The Importance of Risk Register
As organizations mature in their risk management processes, CISOs will frequently set up a risk register to effectively communicate cyber risks and integrate them into the overall enterprise risk management process. Risk registers are a repository of risk information including the data understood about risks over time. For a CISO, this is a tool that serves as a comprehensive document that captures and organizes the current, emerging, and potential risks their organization faces. It works by assessing all identified risks, including their description, potential impact, likelihood of occurrence, and what mitigation strategies exist to combat them.
CISOs can also use a risk register to communicate and collaborate with other business units, including assigning risk management tasks, responsibilities, and accountability to specific owners and tracking ongoing reviews and updates. In organizations where risk registers are not used, training and awareness programs need to be conducted among all the relevant departments including IT and security teams. This can help address the knowledge gaps within departments and highlight the need for a risk-based approach. For carrying out these risk responsibilities by security teams, it is crucial to understand the risk management lifecycle.
The Risk Management Lifecycle
The risk management lifecycle provides a structured and continuous approach to identifying, assessing, managing, and monitoring risks within an organization. The lifecycle ensures that all the risks including cyber-based risks are understood and proactively managed tied to the organization’s overall business objectives.
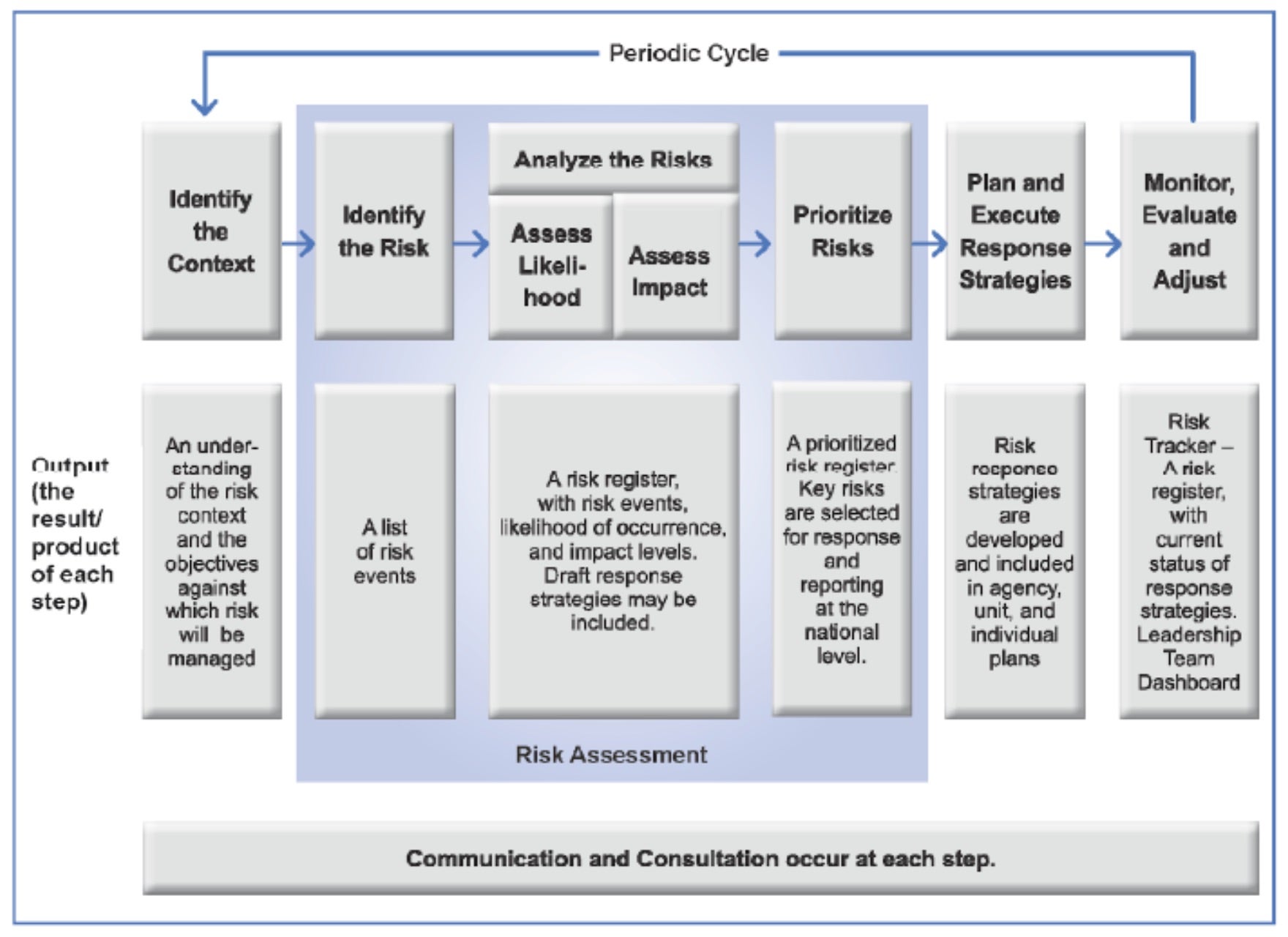
According to NIST, the lifecycle begins with identifying the context and then risk identification, where potential threats are recognized and documented as relevant to the organization. It then moves to risk assessment, where the likelihood and impact of these risks are evaluated, allowing CISOs to prioritize them effectively. Risk treatment (aka risk response) follows, where strategies such as risk mitigation, transfer, acceptance, or avoidance (noted in the section below) are implemented to address the identified risks. This phase is crucial in determining the best course of action to protect the organization from potential threats.
Other integral parts of the lifecycle are continuous monitoring and review, both ensuring that risk management strategies remain effective in a constantly changing threat landscape. For CISOs, this lifecycle approach enables them to take a proactive stance on cybersecurity and help foster a culture of resilience and preparedness across all business units.
Risk Response Strategies for CISOs
One of the key steps as part of the risk management lifecycle is executing risk response strategies. CISOs can answer key questions as to why a particular security technology or cyber insurance package is purchased by taking into account the risk appetite and risk tolerance of the organization. At a brief level, the four risk response strategies are:
- Risk Acceptance – Acknowledging the existence of a risk and deciding to retain it without taking any specific action to mitigate or transfer it. This approach is usually taken when the potential impact of the risk is considered low, or when the cost of mitigation exceeds the benefit. In this case, the organization is prepared to deal with the consequences if the risk materializes.
- Risk Mitigation – The strategies and actions taken to reduce the likelihood or impact of a risk. This might involve implementing security controls, developing contingency plans, or taking steps to lessen the severity of the risk. The goal of risk mitigation is to bring the risk to an acceptable level while ensuring that the organization’s objectives are not compromised.
- Risk Transfer – This is a mechanism where potential loss from an adverse outcome is shifted to an individual or entity. By transferring the risk, the organization reduces its exposure to the potential negative impact of the risk, though it may still retain some level of residual risk. For example, purchasing cybersecurity insurance to cover the costs of a data breach is a form of risk transfer.
- Risk Avoidance – The strategy of eliminating exposure to a specific risk by not engaging in the activities that give rise to it. This might mean choosing not to pursue a particular project, adopting different technologies, or altering business practices to avoid the possibility of the risk occurring altogether. While effective, risk avoidance can also limit opportunities and growth if overly applied.
By understanding these risk response strategies, CISOs can make more informed decisions on managing the risk and more effectively communicate their decision-making steps to the board members and executive leadership. The success of an organization’s cybersecurity strategy ultimately hinges on the ability of its leaders to integrate risk management into every facet of the business, making it not just a technical responsibility but a core component of the overall business strategy.
Conclusion
For cyber risk management to be effective within an organization, support from the executive leadership level is essential as it sets a standard in place and defines the overall risk culture and risk awareness of the organization. Both risk culture and risk awareness play key roles in supporting organizations to approach cybersecurity. A top-down approach sets the tone and helps in establishing security as an integral part of business and employees are well aware of cybersecurity risks, thus building effective defenses against threats.
As CISOs continue to transition from technical to strategic roles, their understanding and application of risk management fundamentals will be key to their success. Once these fundamentals are well ingrained within the organizational ecosystem, it is easier for CISOs to adapt to the new trends and improve risk management processes by automation. Ultimately, the goal is to move from a segmented, check-box approach to a more defense, outcome-based, integrated, enterprise-wide risk management strategy that allows organizations to better manage the risks and enable operations.
90 Days | A CISO’s Journey to Impact
See how our intelligent, autonomous cybersecurity platform harnesses the power of data and AI to protect your organization now and into the future.
如有侵权请联系:admin#unsafe.sh