2024-8-23 00:47:1 Author: cyble.com(查看原文) 阅读量:9 收藏
Key takeaways
- Cyble Research and Intelligence Lab (CRIL) has identified a phishing site impersonating a VPN provider. The site specifically targets individuals downloading Virtual Private Network (VPN) applications for Windows, Linux, and macOS.
- The Threat Actor (TA) has created distinct binaries for each platform—Windows, Linux, and macOS—targeting users across these systems.
- The Windows version of the stealer targets cryptocurrency-related browser extensions, standalone crypto wallets, and stored browser passwords.
- The Linux Version of the stealer Focuses on cryptocurrency browser extensions, standalone crypto wallets, browser login data, cookies, and SSH keys.
- In addition to cryptocurrency browser extensions and crypto wallets, MacOS version steals browser login data, cookies, SSH keys, MacOS passwords, and Keychain.
- The campaign is linked to a Telegram channel with over 54,000 subscribers, active since 2018, and believed to have undergone a change in operators in 2021.
- The phishing site has undergone multiple registrar changes, with the most recent switch occurring on August 21, 2024.
- Initially, the Threat Actors (TAs) appeared to provide legitimate VPN services, gradually gaining user trust. They later shifted to distributing stealer, exploiting the trust they had built.
Overview
Threat actors (TAs) predominantly rely on phishing websites as a method to distribute malware. A key tactic involves impersonating well-known brands, especially those associated with essential or security-related applications, to enhance the credibility of their campaigns. They create a false sense of legitimacy by showcasing compatibility with various platforms and mimicking trusted applications. This deceptive approach exploits users’ trust in familiar brands, making it easier for TAs to trick unsuspecting individuals into downloading malicious software. The sophisticated blend of brand impersonation and the appearance of security further reinforces the illusion of authenticity, increasing the chances of successful infiltration.
Recently, CRIL has identified a phishing website aimed at individuals downloading VPN applications for Windows, Linux, and macOS. The TA has created separate stealer binaries for each operating system, using a deceptive site that mimics the legitimate “WarpVPN” service. This phishing site offers detailed installation instructions specific to each platform. Once installed, the stealer extracts various sensitive data from the victim’s machine. It targets cryptocurrency-related browser extensions, standalone crypto wallets, stored browser passwords, browser login data, cookies, SSH keys, macOS passwords, and Keychain. The below image shows the phishing website.

Figure 1 – Phishing site
We have named this stealer “Cheana Stealer,” based on the C&C server name “ganache.live” and TA’s frequent use of the string “ganache” in the stealer’s code.
Spreading Mechanism
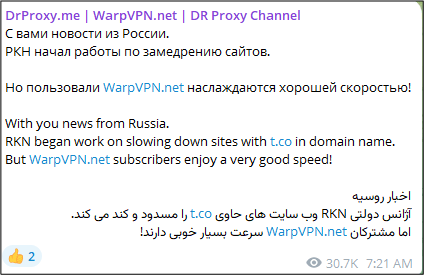
During our investigation, we discovered a Telegram channel linked to this campaign. The phishing website associated with the campaign is referenced in the channel’s bio. This channel has over 54,000 subscribers and plays a crucial role in the distribution of malicious content. The figure below displays the Telegram channel.

Figure 2 – Telegram Channel
Upon further investigation, we found that this channel has been active since at least 2018, with several profile changes over time, as shown in the figure below. Notably, the phishing site was added to its bio in 2021.

Figure 3 – Telegram Profile Changes
The phishing site has switched registrars’ multiple times, with the most recent change occurring on August 21, 2024. We suspect that the TAs initially provided legitimate services and are now taking advantage of the trust they’ve built to distribute stealer malware. Posts from 2021 indicate that the TAs offered free VPN services individually, as illustrated in the figure below, further supporting this claim.

Figure 4 – Warpvpn Site in 2021
The figure below shows the post made in 2021.

Figure 5 – Telegram post made in 2021
We also observed that a Russian native speaker likely wrote posts made before 2021, while posts from 2021 appear to be auto-translated versions, as shown in the figure below. Interestingly, the phishing domain was also added to the channel’s bio in 2021, suggesting that the operator of the Telegram channel may have changed during that time.

Figure 6 – Comparison between 2019 & 2021 posts
Additionally, in 2021, the channel’s profile photo was updated to an image taken by a Russian YouTuber, as shown in the figure below. Moreover, upon investigating the contact person mentioned in the channel, we discovered that they have a history of frequent interactions with Arabic speakers. This further suggests that the channel’s operator might be from a different origin, attempting to pose as a Russian individual.

Figure 7 – Telegram Channel Icon
Technical Analysis
In this campaign, the TAs set up a phishing site that impersonates a legitimate VPN service, offering detailed installation instructions for Windows, Linux, and macOS. The initial infection occurs when users follow the phishing site’s instructions, which involve copying and pasting platform-specific commands into their systems. Each set of commands—tailored for Windows, macOS, and Linux—ensures the malicious code is executed correctly on the respective operating system.
In this section, we will examine how TA steals sensitive information across different platforms, focusing on both common techniques and platform-specific approaches.
Windows
For Windows, the TA utilizes PowerShell commands to carry out the attack. They use ‘Invoke-WebRequest’ to download the “install.bat” file from “hxxps://warpvpn[.]net”. Following the download, ‘Start-Process’ command is used to launch a new instance of ‘cmd.exe’, passing ‘install.bat’ as an argument to execute the batch file. This method ensures the ‘install.bat’ script is run seamlessly as part of the attack. As shown in the image below, the TA instructs users to copy and paste commands intended for PowerShell into the Command Prompt. These commands will not work properly in the Command Prompt and will only execute correctly within a PowerShell environment.

Figure 8 – installation instructions for windows
The “install.bat” script performs the following things:
- Verify if Python is installed silently using the command “python –version >nul 2>&1”. If Python is not installed, download and extract the “python-3.11.3-embed-amd64.zip” from python.org.
- Check if “pip” is installed. If not, download and install it using the ‘get-pip.py’ script from “https://bootstrap.pypa.io/get-pip.py”
- Determine if “virtualenv” is installed. If missing, install “virtualenv” using pip.
- Create a virtual environment and activate it using “call venv\Scripts\activate”.
- Download and install the “hclockify-win” package from “hxxps://ganache.live/media/attachments/hclockify-win.zip”, which masquerades as a legitimate Python “clockify” module
- Use “pip” to install all necessary dependencies for “hclockify-win”.
- Run the “main.py” script from the “hclockify-win” package.
- Use a “goto” statement to invoke a lure function that installs the legitimate Cloudflare application, thereby disguising the malicious intent.
The below figure shows the content of the install.bat.

Figure 9 – Content of Install.bat
The malicious python package “hclockify-win” contains scripts to orchestrate sensitive information collection and exfiltration by calling various modules. These modules target cryptocurrency browser extensions, Crypto Wallets, and Stored Browser passwords.
Targeting Browser Extensions
The Python package “hclockify-win” includes a module named “ganache.helperwd” that scans multiple Chromium-based browsers, including Chrome, Brave, Opera, and Microsoft Edge, for cryptocurrency wallet extensions such as Trust Wallet, TronLink, Coinbase, Exodus, Crypto.com, Nami, and Solana. Once these extensions are detected, the module compresses their folders into a zip file and sends the data to the TAs command and control (C&C) server through a POST request, as illustrated in the figure below.

Figure 10 – Targets Browser Extension
By targeting these extensions, the TAs aim to steal cryptocurrency wallet data, including private keys, recovery phrases, and transaction details. This could potentially allow the TAs to gain unauthorized access to the victim’s digital assets. The stolen information can be further exploited or sold on cybercrime forums.
After scanning multiple browsers for cryptocurrency wallet extensions, the module proceeds to search through all Firefox profiles. It targets the prefs.js file to identify the unique ID linked to MetaMask by searching for [email protected]. Once the unique ID is identified, the module uses it to locate MetaMask’s backend data file present in the location “b0kwoimz.default-release\storage\default\moz-extension+++7f784e52-eabb-4316-8e36-850ac47f0760^userContextId=4294967295”.
The script then compresses this data into a zip file and transmits it to the TAs server via a POST request, maintaining the continuity of the data exfiltration process.

Figure 11 – Targets Firefox’s MetaMask extension
Targeting Crypto Wallets
The malicious Python module then searches for cryptocurrency wallets installed on the system, identifying the installation directories for well-known crypto wallets such as Bitcoin, Monero, and Dashcore. After locating these directories, the content of these wallets is compressed into a zip file and subsequently uploaded to the TAs command and control (C&C) server through a POST request, as shown in the figure below.

Figure 12 – Targets Crypto Wallets
Targeting Browser passwords
Additionally, the malicious Python module targets browser passwords stored in an SQLite database called “Login Data.” For Chromium-based browsers, the script first enumerates and retrieves the names of all files within the “Browser-name\User Data\” directory. It specifically looks for the “Local State” file, which holds the encrypted key necessary for decryption. The script then utilizes the “CryptUnprotectData()” function to decrypt this key. With the decrypted key, the script can subsequently decrypt the “Login Data” file, which contains all user credentials. This process allows the attackers to access and exfiltrate saved passwords from the targeted browsers.

Figure 13 – Targets Browsers Password
For non-Chromium-based browsers like Firefox, the TA employs a module called “ganache.fflg” which is capable of extracting credentials across different platforms, including Windows, Linux, and Mac. In our scenario, the focus is on Windows. The module systematically iterates through all Firefox profiles to collect key files such as “prefs.js”, “logins.json”, and, as a fallback for older versions, “signons.sqlite”. It then leverages the Network Security Services (NSS) library nss3.dll to decrypt and extract the browser credentials in plain text. Once decrypted, the decrypted credentials are exfiltrated from the victim’s machine to the TAs command and control (C&C) server.

Figure 14 – Targeting Firefox browser

Figure 15 – nss utility for credential decryption
Ubuntu/Linux
For Linux, the TA crafted a curl command to download the “install-linux.sh” script from ‘hxxps://warpvpn.net’ as shown in the below figure.

Figure 16 – Installation instruction for Linux
The script “install-linux.sh” first attempts to retrieve a unique ID from the
“warpvpn” configuration file located at “~/HOME/.config/warpvpn”. If this file is missing, the script sends a POST request to the server containing the victim’s username, operating system, and the phishing source in order to obtain a unique ID. This ID is then used in all subsequent POST requests, along with the stolen data from the victim’s machine.

Figure 17 – Unique ID
The “install-linux.sh” script is divided into two main components: a stealer that gathers sensitive browser information and a cryptocurrency stealer, along with a function designed to mimic the legitimate Cloudflare Warp application installer.
This Linux module mirrors the Python-based stealing activities observed on Windows systems, targeting browser extensions and cryptocurrency wallets, including Bitcoin and Monero. However, on Linux, the script introduces some notable variations. The bash script is designed to steal Login Data and Cookies files from the victim’s machine and exfiltrate them to C&C server. Furthermore, the script searches for and uploads SSH keys from the “/.ssh” folder, as depicted in the figure below. This comprehensive approach significantly boosts the attacker’s ability to gain and maintain unauthorized access to the compromised system.

Figure 18 – content of install-linux.sh
MacOS
For MacOS, the TA provides similar curl command to download “install.sh” and using default shell “sh” to execute the downloaded script.

Figure 19 – Install instruction for MacOS
Targeting MacOS password:
The script tricks the user into entering their credentials by mimicking a standard system prompt that typically appears during a new application installation, making it appear as a legitimate request. After the user enters their password, the script uses the ‘dscl . -authonly’ command to validate the credentials. If the validation is successful and no errors occur, the credentials, along with data from the “/Library/Keychains” folder, are sent to the attacker’s command and control (C&C) server through a ‘curl’ POST request. If the validation fails, the script repeatedly prompts the user to re-enter their credentials, continuing this process until it succeeds.

Figure 20 – MacOS password exfiltration
The TA aimed to gather information similar to what was observed in previous Linux cases. However, there are notable differences in the scope of the attack. In addition to targeting common cryptocurrency wallets like Bitcoin and Monero, the TA also focuses on a broader range of crypto wallets, including Electrum, Exodus, DashCore, and Guarda. Furthermore, the script searches for and exfiltrates saved SSH keys from the `/.ssh` folder.

Figure 21 – install.sh (Crypto wallet exfiltration)
Fake Message and WarpVPN Installation
During the theft operation, the TA employs a deceptive tactic by displaying a fake “in-progress” message.After successfully exfiltrating the data, the script proceeds to download and install the genuine Cloudflare Warp application on the victim’s machine, as shown in the figure below.

Figure 22 – Fake Message and Legitimate VPN Installation
Exfiltration over HTTPS
Before the exfiltration process, the TA archives the stolen files into ZIP files, ensuring they are organized by data type with distinct archive names for each category. These archives are then transmitted to the attacker’s Command and Control (C&C) server via a POST request to “hxxps://ganache.live/api/v1/attachment”. The communication occurs over port 443, allowing the data to be sent securely under the guise of legitimate HTTPS traffic.

Figure 23 – Exfiltration over HTTPS
The TA utilizes a Django Rest Framework-based interface to manage and view the exfiltrated data. This setup provides them with a structured and accessible way to organize and analyze the stolen information, ensuring efficient exploitation of the compromised data.

Figure 24 – attacker’s login
Conclusion
This phishing campaign masquerades as a trustworthy VPN provider. This campaign is spreading from a Telegram channel, carefully cultivating user confidence over time before pivoting to malicious objectives. This Telegram channel boasts over 54,000 subscribers, which has been operational since 2018 and is believed to have undergone a change in operators in 2021.
The campaign’s reach is underscored by its targeting of multiple platforms—Windows, Linux, and macOS—demonstrating a comprehensive approach to malware distribution. By creating distinct malicious scripts tailored for each operating system, the attackers ensure that their payloads are effectively executed across different environments. This multi-platform strategy allows the phishing operation to maximize its reach and impact, compromising a wide array of systems and harvesting sensitive information from a diverse user base.
Recommendations
- The initial infiltration is taking place via phishing websites. It is crucial to only download and install software applications from well-known and trusted sources.
- Conduct awareness campaigns to educate users about the risks of phishing attacks and the importance of verifying the authenticity of VPN services.
- Deploy advanced endpoint protection solutions that can detect and block malicious scripts and payloads across different operating systems. Ensure that these solutions are updated regularly to identify and mitigate new threats.
- Use network security tools to monitor and block communications with known Command and Control (C&C) servers. Implement firewalls and intrusion detection systems to detect and prevent unauthorized access.
- Enable MFA on all accounts to add an extra layer of security and reduce the risk of unauthorized access even if credentials are compromised.
- Develop and maintain an incident response plan to quickly address and mitigate the impact of malware infections. Regularly test and update the plan to ensure effectiveness.
MITRE ATT&CK® Techniques
| Tactic | Technique | Procedure |
| Initial Access (TA0001) | Phishing (T1566) | This malware reaches users via VPN phishing sites. |
| Execution (TA0002) | Windows Command Shell (T1059.003) | cmd.exe is used to run commands |
| Execution (TA0002) | PowerShell (T1059.001) | Invoke-WebRequest is used for downloading batch files |
| Execution (TA0002) | Python (T1059.006) | Python stealer is used for targeting windows users |
| Execution (TA0002) | User Execution (T1204) | User is instructed to execute the commands |
| Credential Access (TA0006) | Credentials from Password Stores: Credentials from Web Browsers (T1555.003) | Retrieves passwords from Login Data |
| Credential Access (TA0006) | Credentials from Password Stores: Keychain (T1555.001) | Attempts to exfiltrate Keychains from MacOS system |
| Credential Access (TA0006) | Steal Web Session Cookie (T1539) | Steals browser cookies |
| Collection (TA0009), Credential Access (TA0006) | Input Capture: GUI Input Capture (T1056.002) | Shows command window to enter password on MacOS |
| Credential Access (TA0006) | Unsecured Credentials: Private Keys (T1552.004) | Tried to exfiltrate ssh keys |
| Collection (TA0009) | Archive via Utility (T1560.001) | Zip utility is used to compress the data before exfiltration |
| Collection (TA0009) | Archive via Library (T1560.002) | Zip library is used to compress the data before exfiltration |
| Exfiltration (TA0010) | Exfiltration Over C2 Channel (T1041) | Exfiltration Over C2 Channel |
Indicators Of Compromise
| Indicators | Indicator Type | Description |
| 70f08497d7a9e6a8e5f2dd3683a20563d20668e1c78df636ff1e36a014c9d493 | SHA-256 | install-linux.sh |
| acf807def82c4b56752a9fa9b081dbb37ba9cc9f6e1c522568ff502b6b49b6db | SHA-256 | install.bat |
| 48964c11fcbefd6508164239866c94b55ca2798e9745671c37447ad0a6f3e1c4 | SHA-256 | install.sh |
| d3ece8616d0dd8244666af574cc2475d947180ed240f49b1a6e61443a896f65d | SHA-256 | main.zip |
| 3ef838502663c167f5c502585e810ffae3e03152b3f82544b813389c19a33dce | SHA-256 | main.py |
| ac4aeab3952f6ca960cbd48c3123f09a68f50818f9bdf35c9d811570893fa102 | SHA-256 | fflg.py |
| 6a68e95ae67aa8c61bd74ecf5f57f98fbdc0bbe0489ae71b7c8732edf49ac3a9 | SHA-256 | helperwd.py |
| c044b1a36249f6fe7219e6c48270d9927bf359110ff3583129dcbdff809f2d2d | SHA-256 | utils.py |
| ba8058b704a55e50c24383a765fd74b38d7dbbf8546c4f179266c265403174b8 | SHA-256 | Warpvpn.zip |
| warpvpn.net | Domain | Phishing site |
| hxxps://ganache.live | Domain | C&C |
Related
如有侵权请联系:admin#unsafe.sh