
2024-8-23 05:33:38 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
In the escalating battle against malicious headless bots, basic detection methods are no longer sufficient. As cybercriminals refine their techniques and leverage headless browsers to automate attacks with increasing sophistication, the need for advanced detection strategies has never been more critical. This blog post dives into the world of headless browsers, exploring how they are used in attack automation and the evolving techniques employed to detect and mitigate these threats effectively.
Headless Browsers: Both Good and Malicious Actor Tools
Headless browsers are web browsers without a graphical user interface (GUI). They function like typical browsers such as Chrome or Firefox but operate in the background, executing tasks without displaying any visual output. This headless nature makes them particularly efficient and well-suited for automation tasks that do not require user interaction. Originally created for purposes like automating testing across different web environments and platforms, headless browsers have now become indispensable tools for web scraping, automated interactions, and, unfortunately, malicious activities.
Popular Headless Browsers
- Headless Chrome: A headless version of the popular Chrome browser, offering the same capabilities as Chrome but without the GUI, making it a powerful tool for automated tasks. This accounts for an estimated 60-70% of all headless browsers usage due to its ease of integration with automation frameworks, robustness, and compatibility with modern web standards (ongoing support from the Chromium project).
- Headless Firefox: Leveraging the Gecko rendering engine, this headless browser accounts for around 5-10% of all headless browsers usage.
- Headless WebKit: Targeting iOS mobile platform applications for Safari’s rendering engine, this headless browser accounts for around 5% of all headless browsers usage.
Popular Headless Browser Frameworks
- PhantomJS: An early pioneer in headless browsing, extensively used for web testing and automation until it was discontinued in 2018.
- Puppeteer: A Node.js library that provides a high-level API to control Chrome or Chromium, often used for tasks like web scraping and generating PDFs.
- Playwright: A versatile Node.js library offering automation capabilities across multiple browsers, including Chrome, Firefox and WebKit, providing extensive cross-browser testing support.
Attack Automation Using Headless Browsers and Plugins
By integrating plugins and custom scripts, attackers can fine-tune headless browsers to mimic genuine user behavior, evading traditional security measures.
Previously, cybercriminals relied on custom scripts interacting directly with HTTP request libraries, manually crafting each request to replicate the behavior of a legitimate user. This often involved forging headers, cookies and even client-side fingerprints to bypass detection mechanisms. However, the advent of headless browsers has significantly simplified and streamlined this process, allowing for more scalable and efficient attacks with a much lower skill level needed.
Attackers are also increasingly leveraging large language models (LLMs) to craft headless browser attacks with ease. LLMs, such as those underlying advanced AI tools, can generate highly realistic and complex code snippets, automate attack sequences, and even adapt in real-time to circumvent detection mechanisms. By feeding these models with data on security measures, attackers can quickly produce scripts that mimic legitimate user behavior, including nuanced browser interactions, timing patterns and randomized inputs.
This capability not only accelerates the development of headless browser attacks but also enhances their effectiveness, making it more challenging for traditional detection systems to identify and mitigate such threats. The use of LLMs in this context represents a significant escalation in the arms race between attackers and defenders, as attackers are able to quickly adapt to detection techniques.
The rise of headless browser attacks has also fueled the growth of the web scraping industry, which is rapidly expanding due to advances in AI and the adoption of machine learning. The industry’s worth is estimated to be $1.5-2 billion in 2024, driven by the ever-growing need for real-time data in decision-making across all sectors.
But how does this criminal industry impact legitimate businesses? It leads to increased operational costs and lost revenue due to:
- Pricing undercutting
- Customer poaching
- Higher server/infrastructure costs
- Duplicate content
- IP theft
- Degraded website performance
- Degraded user experience
Evolving Detection Techniques for Headless Browsers
Identifying headless browsers has always been a cat-and-mouse game between attackers and defenders. Initially, detection methods focused on static indicators such as specific values in the window object or HTML elements, which differed between headless and full browsers. These indicators included properties like navigator.webdriver, specific User-Agent strings or even discrepancies in the rendering behavior.
As attackers adapted by modifying headless browser libraries and obfuscating or outright removing these telltale signs, detection methods had to evolve. This shift requires more sophisticated detection techniques, which focus on the unique behaviors of headless browsers at a lower level.
A Real-World Example
To understand the scale of this challenge, consider one of our customers that faced an onslaught of headless browser traffic. On a typical day, they might see upwards of 20 million requests originating from headless browsers. Without advanced detection mechanisms, these attacks could lead to significant fraud and account takeovers.
To benchmark the prevalence and sophistication of malicious headless browsers nowadays, we ran a test using real-world traffic, both with and without our more advanced detection signals. This allowed us to see how much of this malicious activity would be detected and stopped by what we believe are the standard models in the market (table stakes).
Enabling our advanced headless detection signals not only highlighted the significant contribution of headless browsers to the total traffic composition but also demonstrated the limitations of standard models. As we suspected, basic models, while successful in catching a large portion of malicious traffic, still allowed a considerable number of sophisticated malicious attacks to go undetected. Returning to the case of the customer experiencing over 20 million sessions in a single day—just as in this sample exercise—imagine the portion that would likely have gone undetected without advanced detection models.
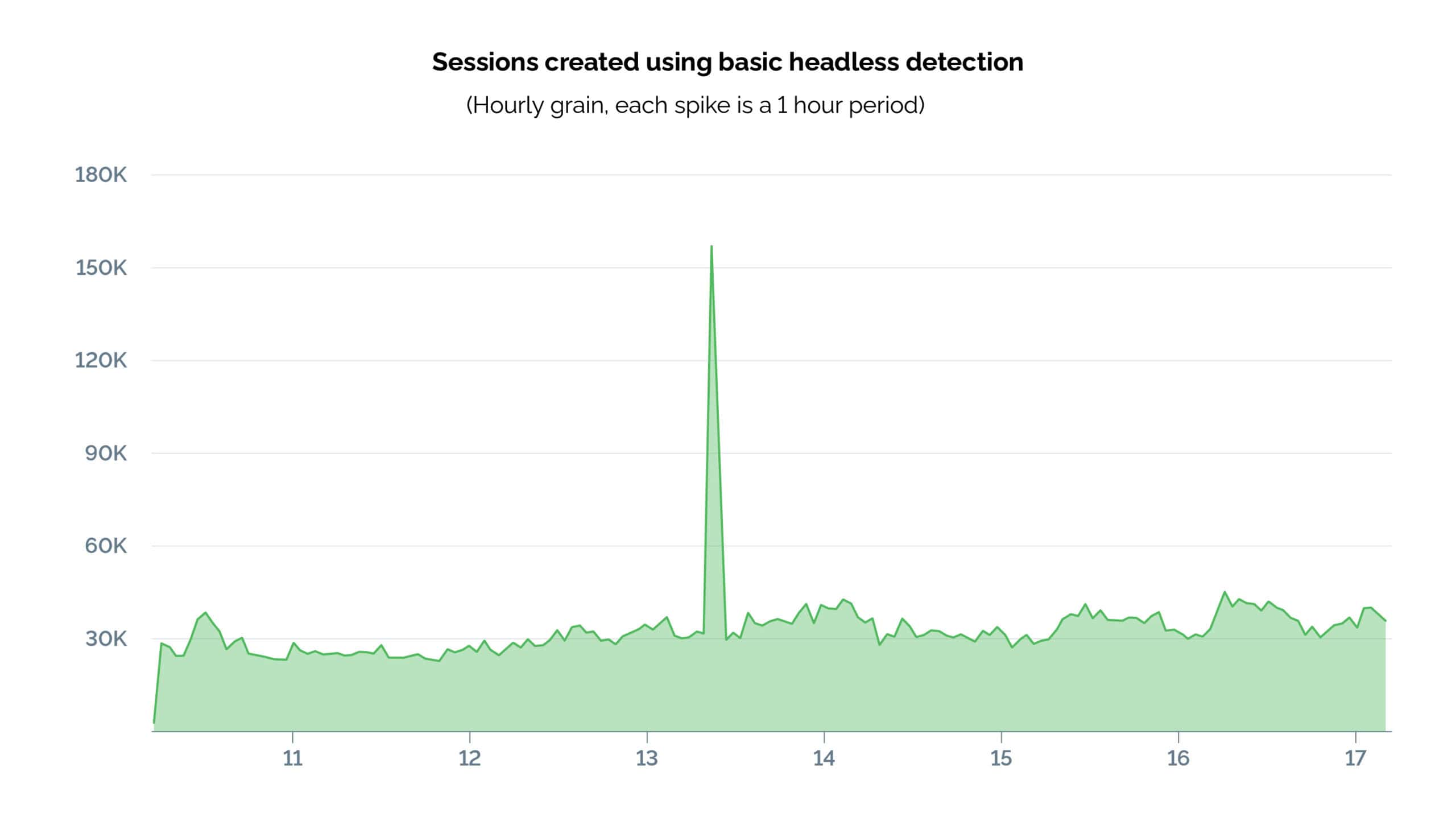
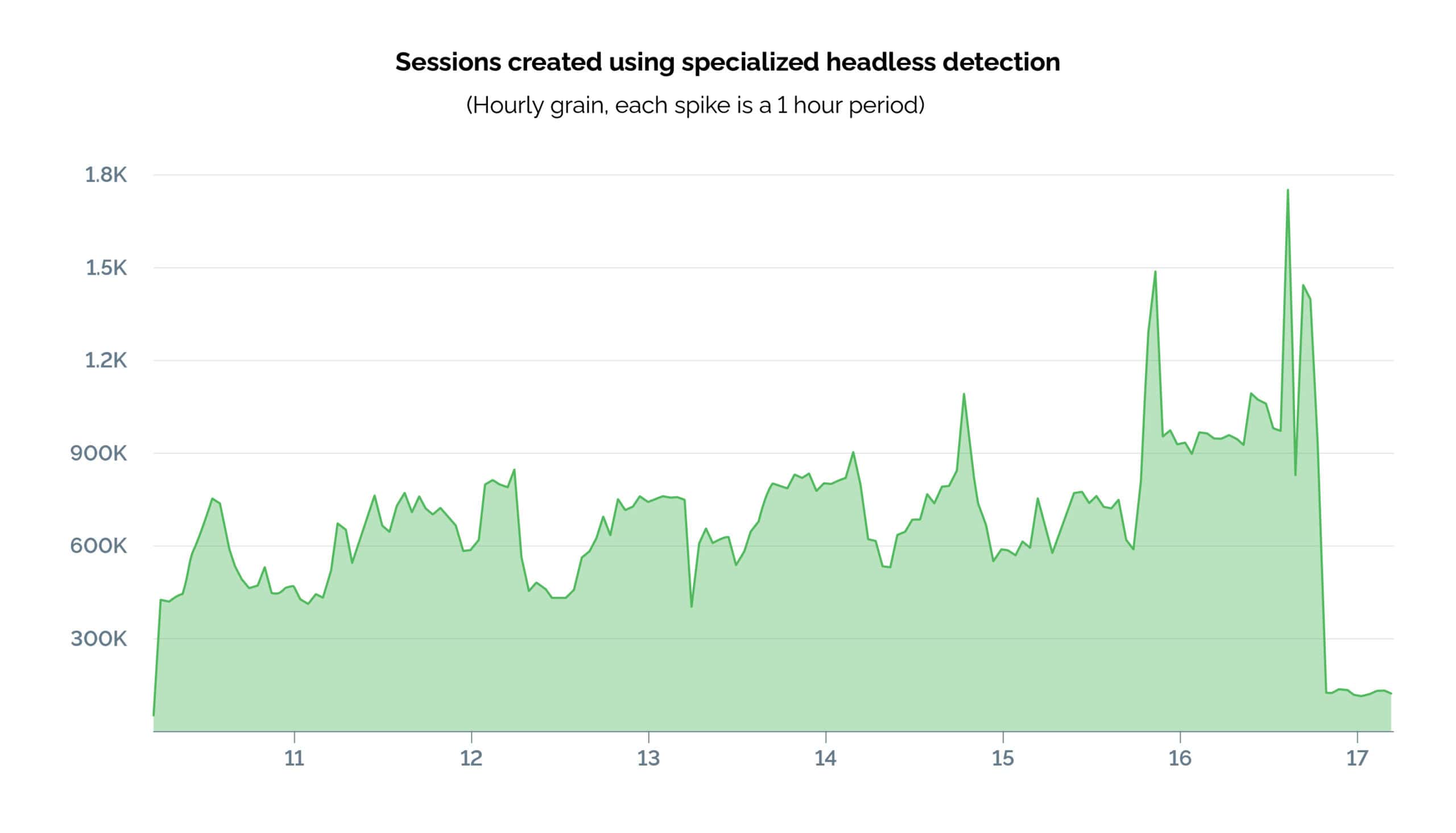
This lift not only highlights the importance of evolving detection techniques but also underscores the necessity of specialized, research-intensive approaches to stay ahead of attackers. With these new detection techniques, we are able to outperform traditional detection methods and outpace the increasingly sophisticated techniques employed by attackers.
Outsmarting Headless Browser Bots
To stay ahead in the battle against increasingly sophisticated headless browser attacks, continuous innovation in detection strategies is crucial. Cybercriminals are constantly refining their tactics, making it essential for organizations to invest in advanced, specialized detection systems. But only by combining cybersecurity expertise with machine learning and behavioral analysis, can your organization protect its digital assets, safeguard its reputation, and provide a trustworthy user experience.
Investing in robust bot detection isn’t just about immediate defense – it’s also a strategic move to outsource what could otherwise become unsustainable and costly if managed in-house over the long term. The question isn’t whether you should invest, but rather, is it better left to industry experts?
Don’t wait until it’s too late. To learn how our advanced detection solutions can help you stay ahead of these ever-evolving threats and ensure the security of your digital environment, contact Arkose Labs today.
*** This is a Security Bloggers Network syndicated blog from Arkose Labs authored by Mitchell Davies. Read the original post at: https://www.arkoselabs.com/blog/challenge-headless-browser-attacks/
如有侵权请联系:admin#unsafe.sh
