
Rapid7 has been a major player in the application security market for years. The company was founded in 2000 and offers a broad range of cybersecurity solutions. However, in recent years, when it came to API security testing, many security professionals have voiced their frustrations with its InsightAppSec DAST tool, especially with modern application types like GraphQL.
Legacy DAST scanners often use irrelevant testing that’s not tied to your actual API configuration, are difficult to configure, and typically lack API discovery.
This disappointing experience has led security engineers to look for solutions elsewhere on the market despite Rapid7's brand recognition.
How can Escape create a better DAST solution for API testing? We'll let you judge if we're better by comparing time to value and scanning results. In this article, we'll show why and what makes us different than Rapid7.
Head-to-head comparison: Escape vs Rapid7
Below you’ll find an in-depth comparison between Escape and Rapid7's InsightAppSec across the entire API security workflow – from API discovery to remediation. We focused on key differences between those two tools. If you want to get a quick recap and an infographic that you can download and share with others, jump to the last section.
We've built this comparison based on the following sources:
- Rapid7 official website
- Demos and official documentation
- Feedback from security professionals (whether Rapid7's and Escape's current customers or not)
- Feedback from an independent industry analyst
API Discovery
You can't secure what you can't see, so the faster you get to see what are the APIs exposed on the internet, the more you reduce the risk of API security breaches.
Escape is built to help you get the value out of it in the shortest time possible. It allows you to discover your APIs within a matter of minutes. Escape uses a sophisticated combination of subdomain enumeration, AI-powered fingerprinting, and OSINT techniques to identify and inventory APIs. This ensures that all APIs, including those not actively in use, are discovered and documented.
Rapid7 simply doesn't offer automated API discovery and API inventory support.
Scan setup
The next point of comparison is the ease of scan setup and its maintenance.
Rapid7 requires manual upload of API schemas to start scans, as it doesn't automatically generate schemas.
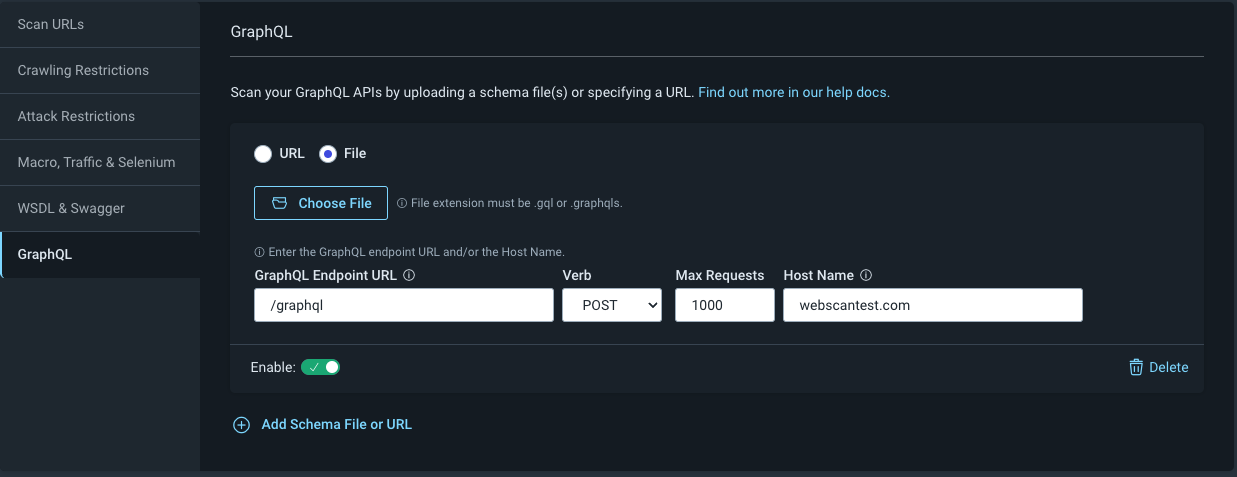
In contrast, Escape uses a proprietary machine learning algorithm to automatically reconstruct API schemas. Of course, to improve overall coverage, you might need to configure authentication and upload specifications you might have on your side, but it's not a requirement to start initial scans.
This ensures that any changes in your API structure are immediately reflected, allowing for continuous and accurate security scanning, without the need for constant intervention.
API Testing
Escape relies on its proprietary feedback-driven Business Logic Security Testing algorithm. It excels in detecting even complex business-logic vulnerabilities, especially in modern API types like GraphQL. Escape's algortihm addresses this complexity by autonomously generating legitimate traffic to test API's business logic.
Through techniques like Sourcing Inference and Strong Typing Inference, Escape ensures the accuracy of generated requests, while integration with generative AI enhances adaptability, particularly in complex attack scenarios.
Escape’s business logic testing is robust, and it includes comprehensive secret detection across various environments, not just repositories. Here is the full list of secrets that Escape can detect.
In contrast, Rapid7 InsightAppSec lacks secret detection capabilities and offers limited testing functionality. A significant amount of manual configuration is required to set up various modules. While InsightAppSec provides a set of pre-built default attack templates tailored to common application security needs, its algorithm does not adapt or learn from the business logic of APIs. This is because it treats APIs and applications the same, without distinguishing between the unique requirements of API security.
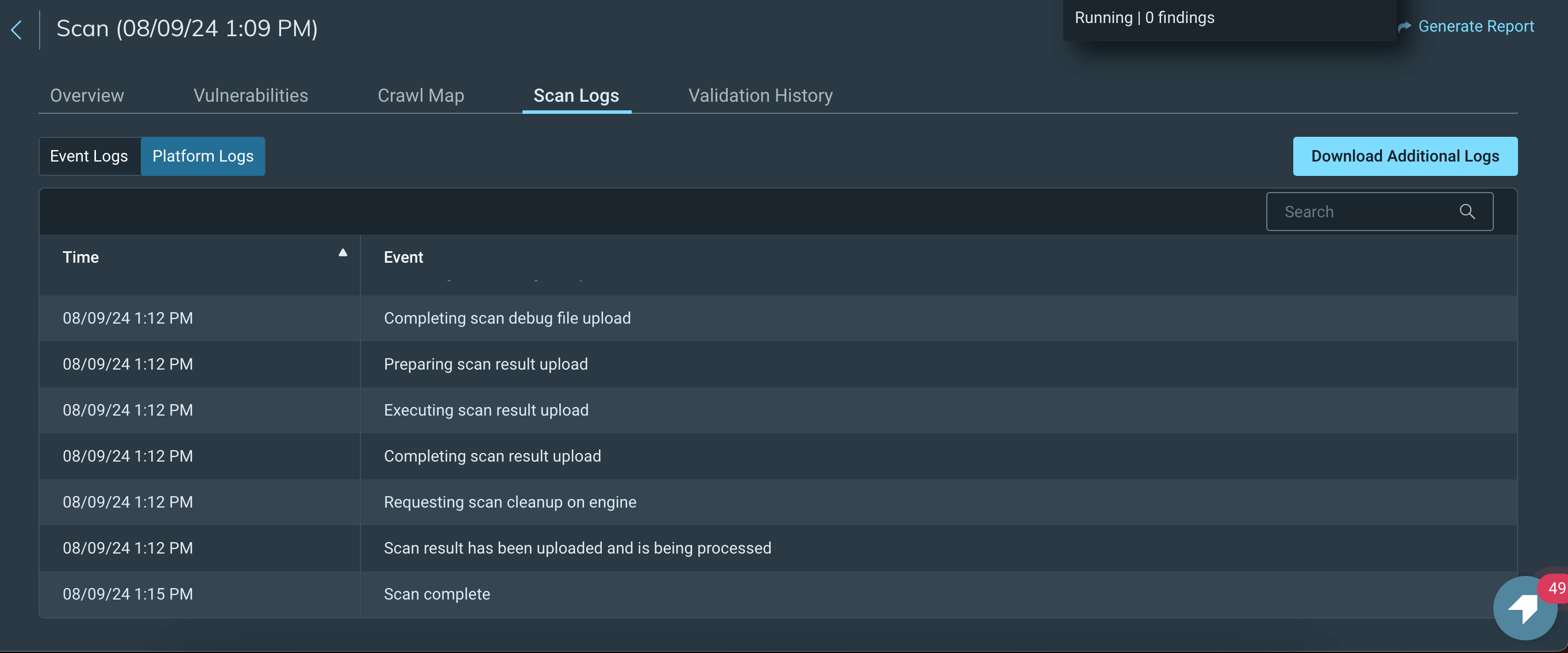
We’ve also received feedback from security practitioners indicating that Rapid7's scanning processes can be time-consuming, often resulting in extensive but less effective crawls that generate excessive noise.
Coverage
Comprehensive API coverage is crucial because it ensures that all endpoints and data flows are thoroughly tested, reducing the risk of vulnerabilities being overlooked, which could lead to potential breaches.
Escape focuses on providing thorough and accurate coverage by leveraging its proprietary feedback-driven algorithms.
This approach ensures that all potential attack surfaces are explored comprehensively, particularly in complex APIs like GraphQL. Escape’s logging and coverage mechanisms are designed to adapt dynamically, capturing detailed insights that are relevant and actionable for security teams.
💡
How Escape's coverage is computed?Coverage = Covered Endpoints / Total Number of Endpoints, where:
Covered Endpoints = OK + SERVER ERROR
Total Number of Endpoints = OK + SERVER ERROR + UNAUTHORIZED + RATE LIMITED + REDIRECTED + SKIPPED
The platform also prioritizes reducing noise, ensuring that logs are concise and directly tied to meaningful vulnerabilities. This results in a more efficient scanning process that minimizes unnecessary data, making it easier for teams to focus on critical issues.
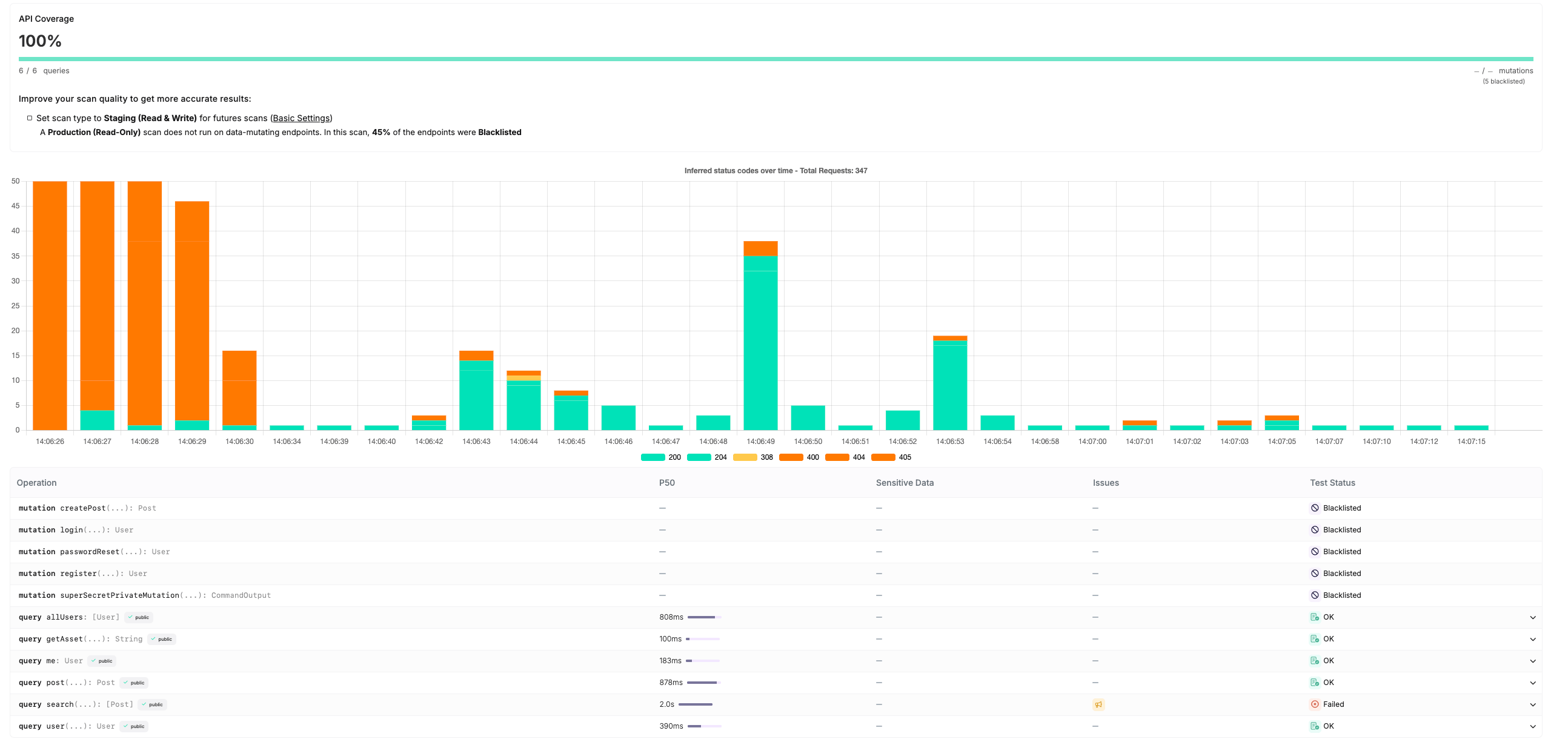
Going beyond, Escape provides step-by-step recommendations to configure scans properly and benefit from Escape’s full testing engine capabilities. You can find more information about Escape's coverage in the docs.
Rapid7 InsightAppSec's "Universal Translator" technology is designed to handle a wide range of application formats and protocols, including modern web technologies. However, one noted issue is that it can generate a high volume of logs, partly due to the scanning of duplicate content and extensive crawling. This can lead to longer scan times and potentially overwhelm users with excessive data that might not all be relevant.
Rapid7 does require manual configuration to optimize scanning for different environments, which can be complex and time-consuming. While this allows for detailed targeting, it also introduces the risk of human error, where important areas might be missed if not correctly configured. You can define max links to crawl and if scanner has a hard time to understand the application, you can use the Macro, traffic and selenium options.
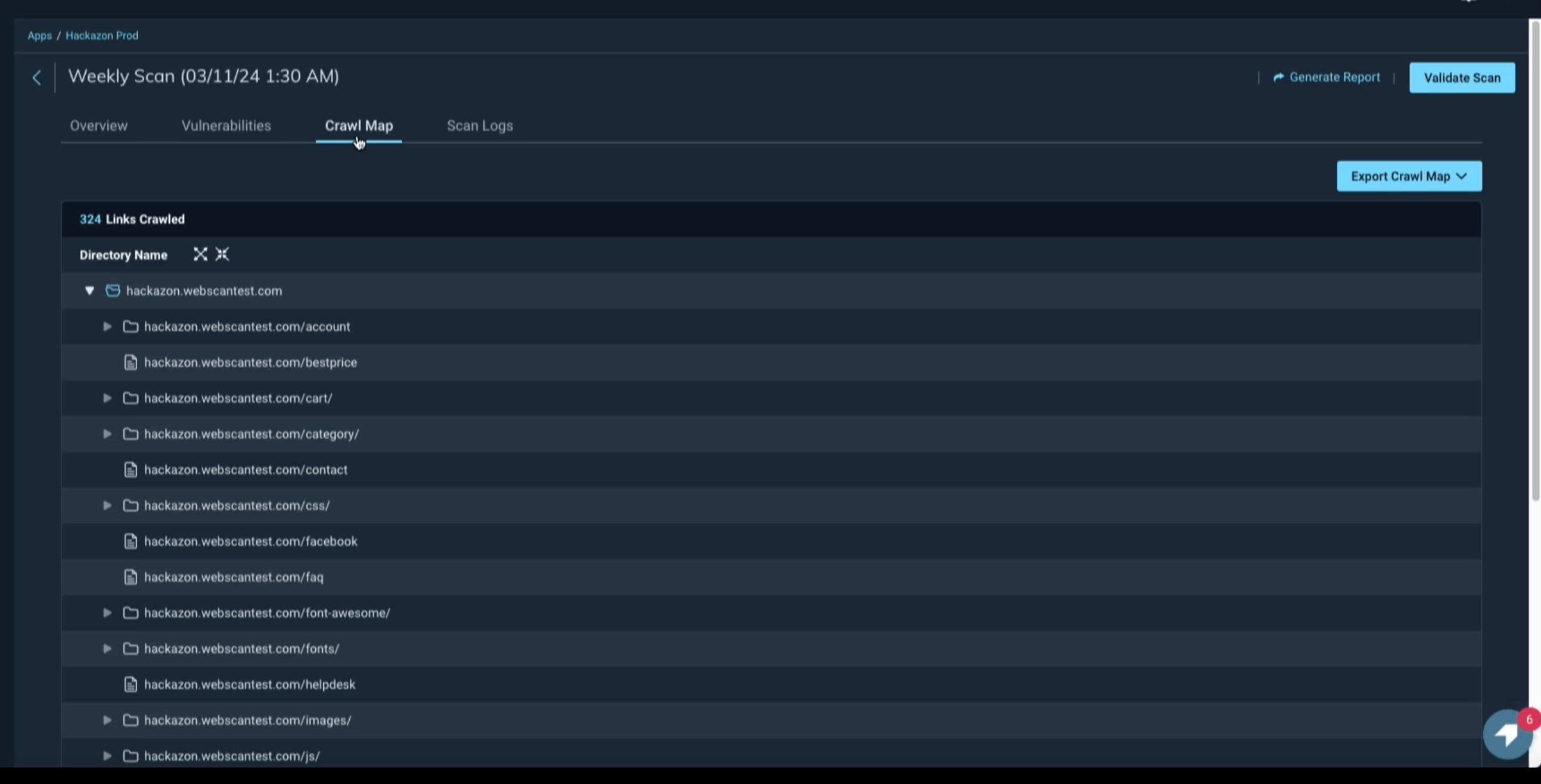
The platform does offer features like crawl maps, scan logs (can help you detect authentication or access failures early in the scan) and advanced scan settings, but achieving optimal results often involves manual tweaking.
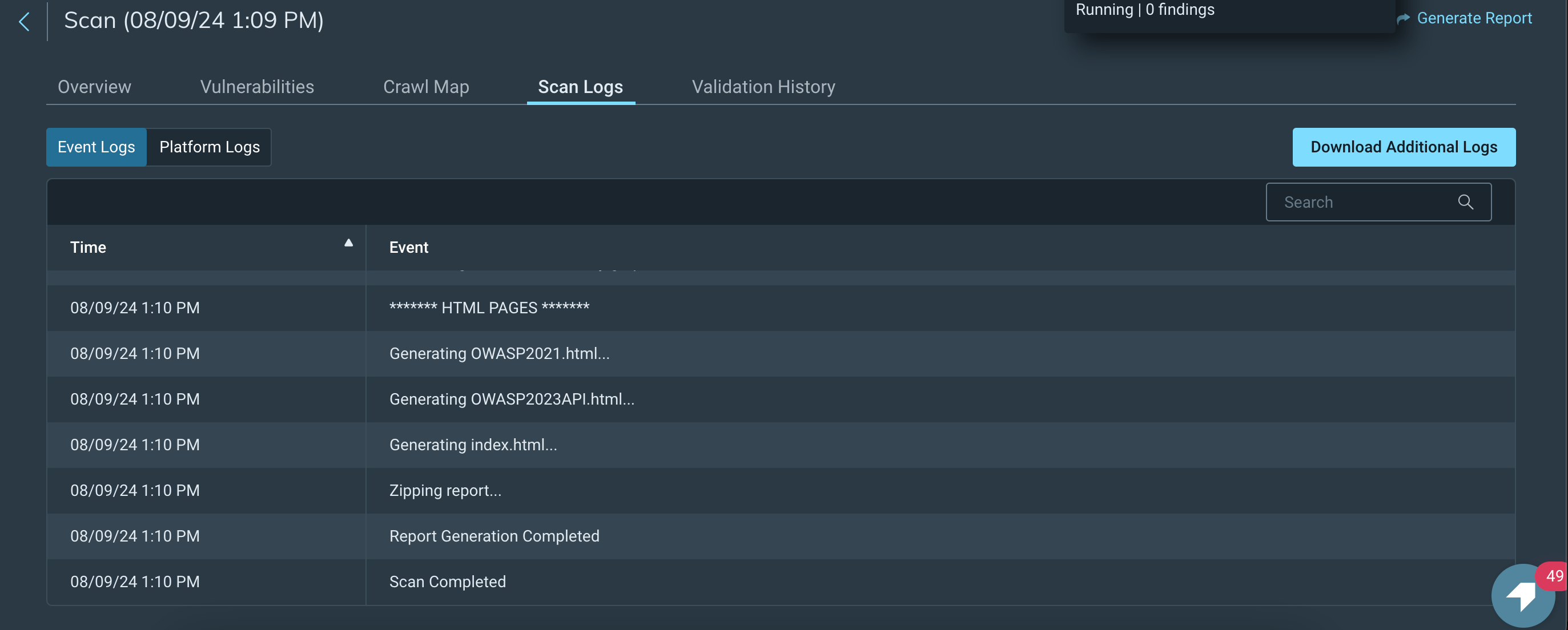
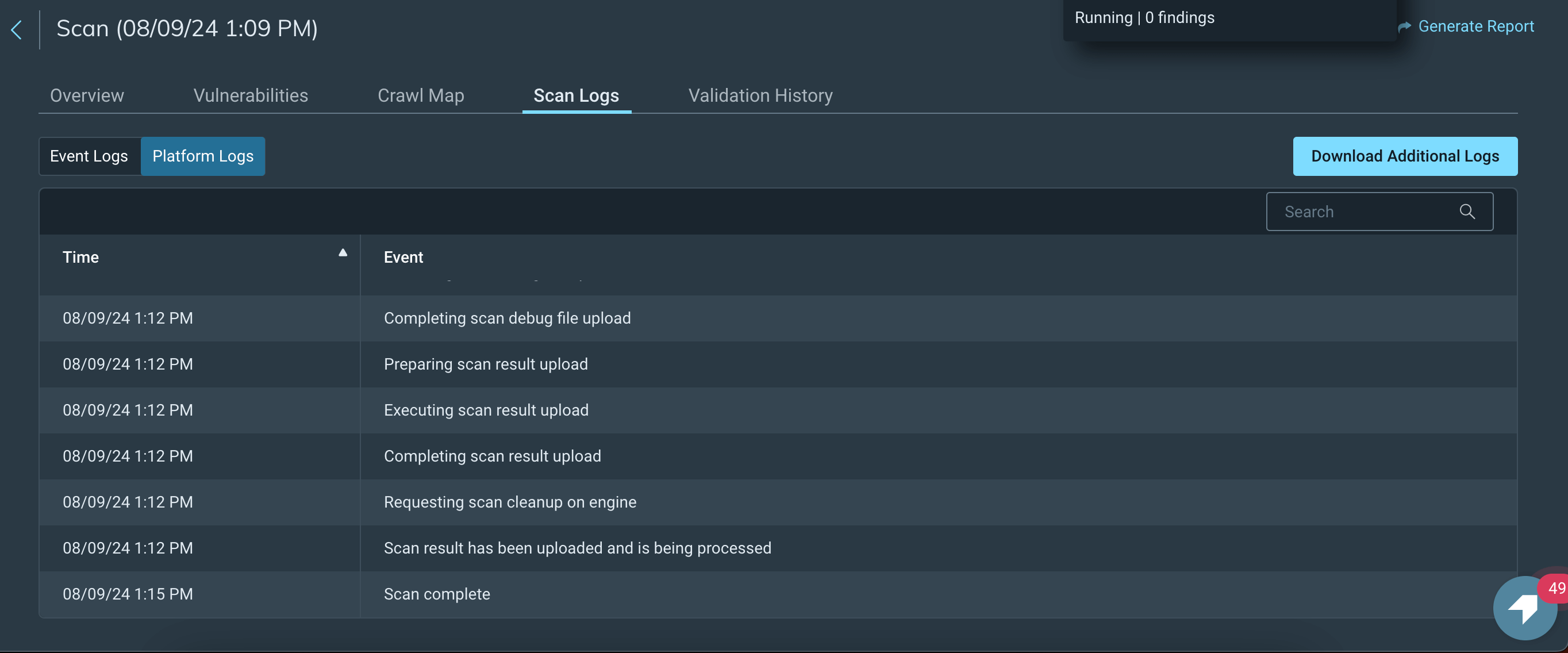
Rapid7 InsightAppSec logs do not provide information on covered application routes.
In contrast, Escape's approach to coverage and logging is more automated and adaptive, focusing on minimizing noise while ensuring comprehensive scanning of all relevant endpoints.
GraphQL API support
GraphQL, a query language for APIs, has gained significant traction in recent years due to its flexibility and efficiency.
Escape has exceptional support for GraphQL Security Testing, integrating 100 GraphQL-specific tests, like aliasing and batching attacks, and even the most complicated access control issues.
Contrarily to other scanners, Escape handles GraphQL natively and not as another HTTP API. Even better, our engine is capable of suggesting code fixes for all findings and all GraphQL engines to maximize developer productivity when fixing issues.
Escape relies on a powerful feedback-driven graph exploration algorithm that can explore and understand the business logic of your GraphQL API.
On the other hand, according to their website, Rapid7 InsightAppSec scans GraphQL schemas using an attack template that incorporates attacks for the following vulnerabilities:
- SQL injection
- Blind SQL injection
- OS commanding
- Server Side Request Forgery
- Local File Inclusion/Remote File Inclusion
Custom tests
Both Escape and Rapid7 offer solutions for custom security tests. On Escape's side, this feature is called "Escape rules," while on Rapid7 you can define custom attack modules.

Once implemented, security scanners run these tests in addition to its built-in scanning routine, helping you to make your testing workflow as efficient as possible.
In contrast with Escape's simple setup based on the YAML operators (detectors/transformations), Rapid7 doesn't provide any actionable guidance on how to set custom attack templates up and might require a much steeper learning curve for less experienced users.
The biggest difference is also in the feedback-driven exploration engine and the scalar inference system that is built into Escape, helping you cover all the routes with confidence and abstractions of data manipulated, and easily available through Custom Tests.
Remediation for developers
Detecting vulnerabilities is only the first step; providing developers with actionable remediation guidance is equally important.
Escape goes above and beyond by offering tailored remediations and code snippets to address identified vulnerabilities efficiently.
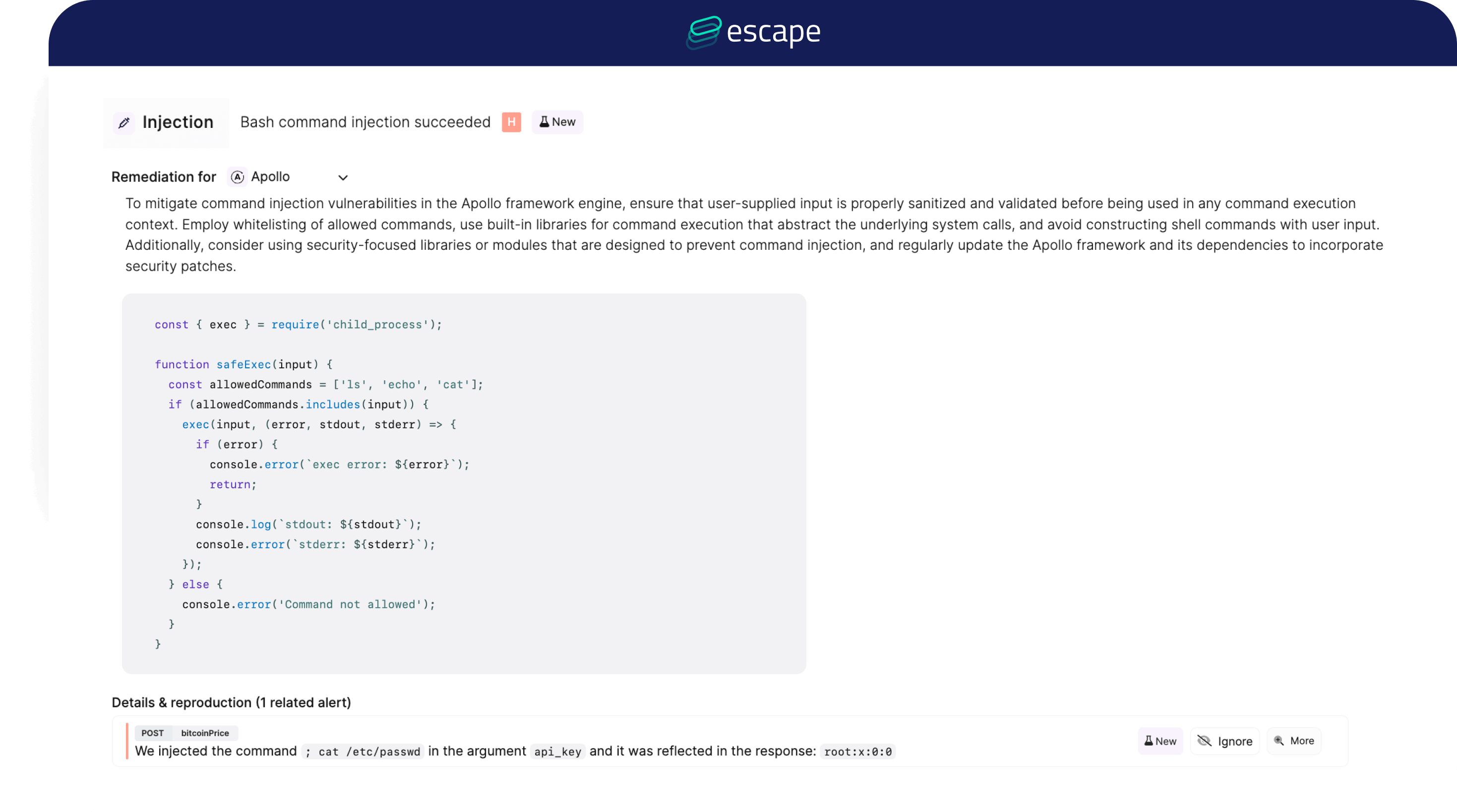
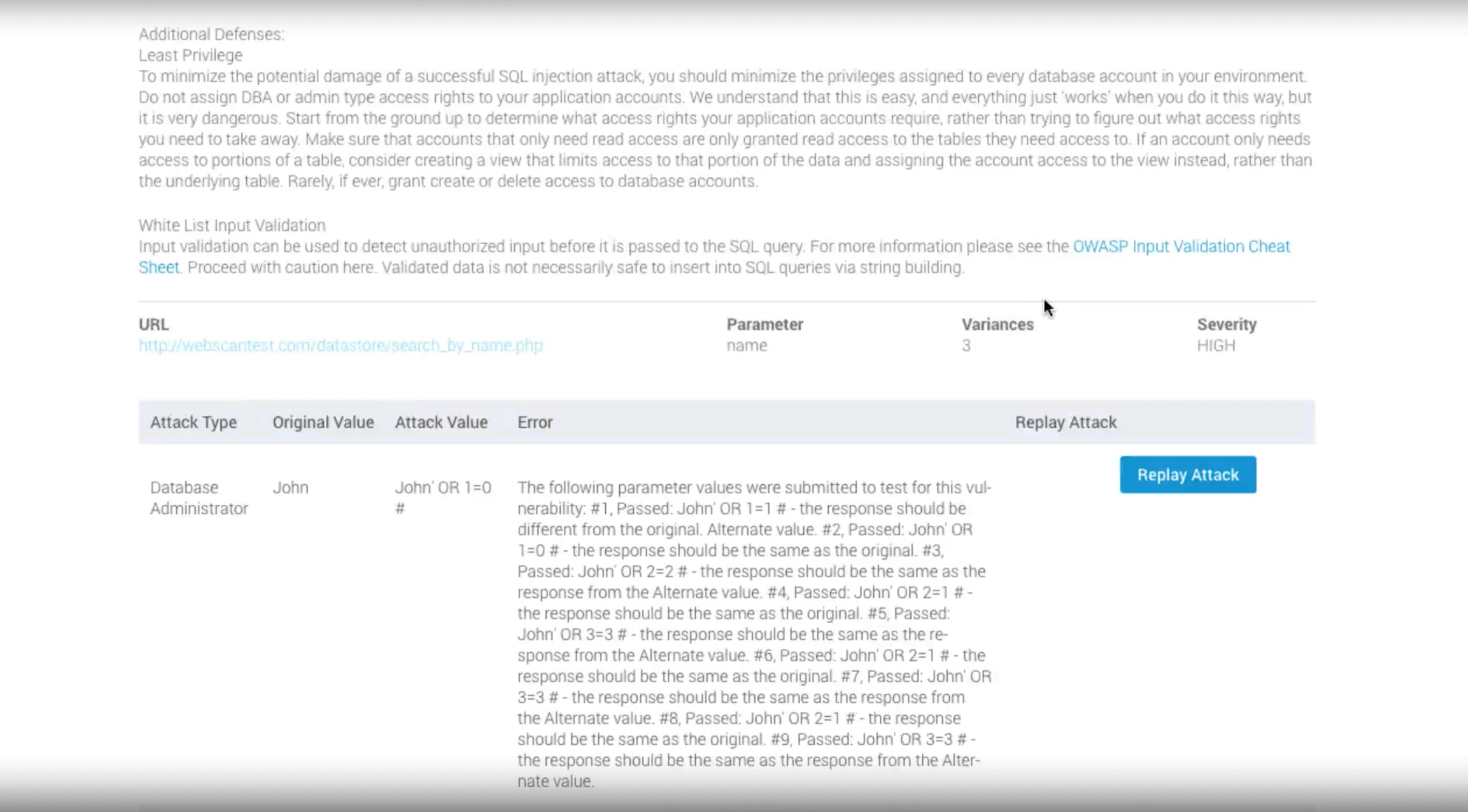
In contrast, while Rapid7 allows you to replay the attack and provides a detailed explanation, it does not provide any actionable guidance. You can't pass any tailored code snippets to your developers, potentially increasing their burden and introducing friction in the remediation process.
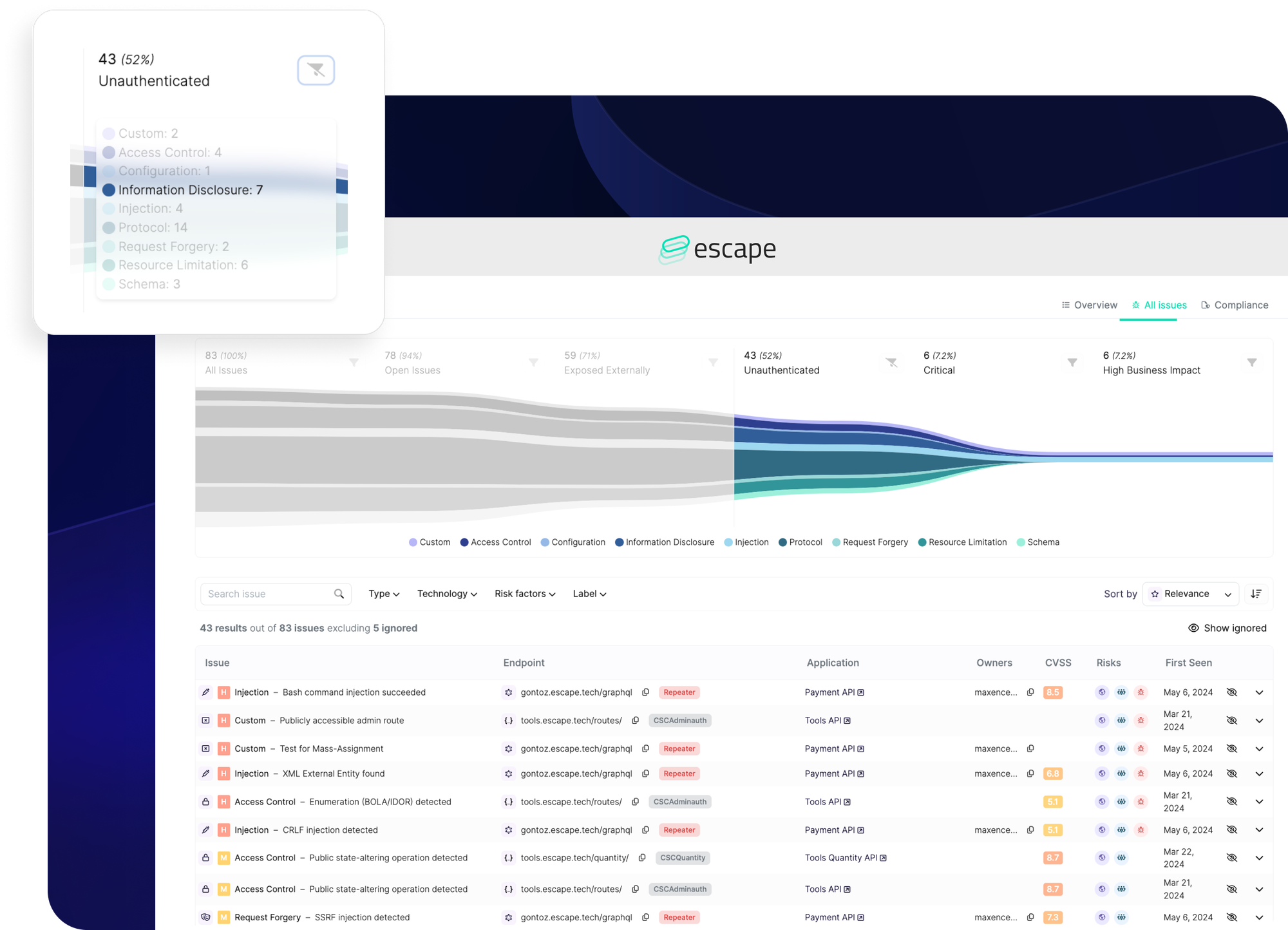
Reporting
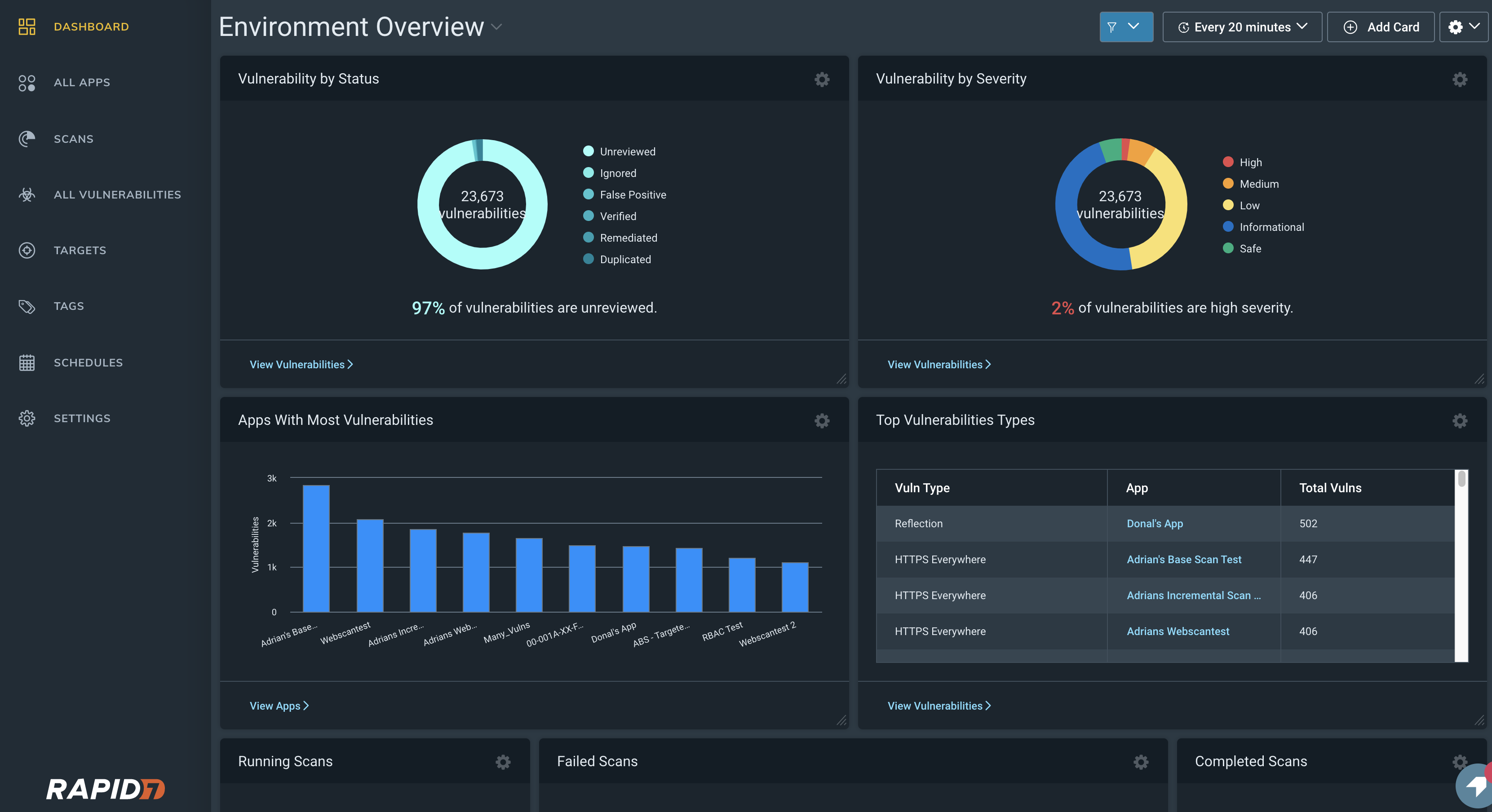
Escape shines in this aspect with its robust reporting capabilities, offering dashboards, vulnerability prioritization funnel Compliance Matrix, Pentest PDF exports, CSV exports, and developer-friendly exports.
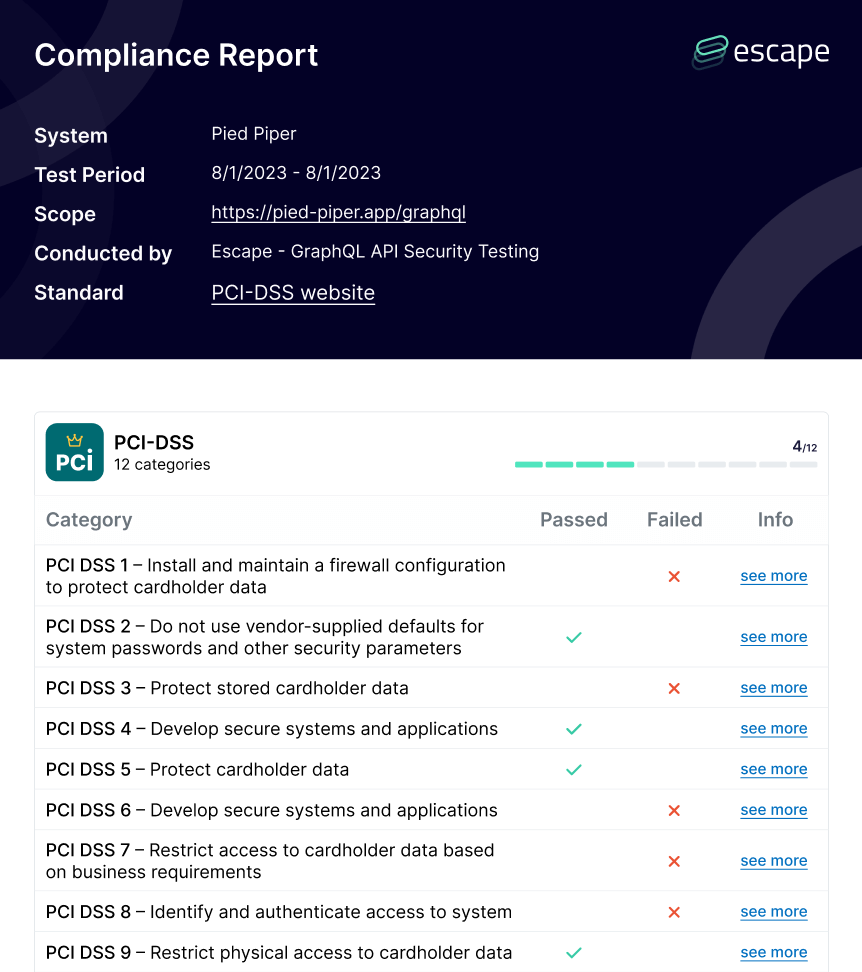
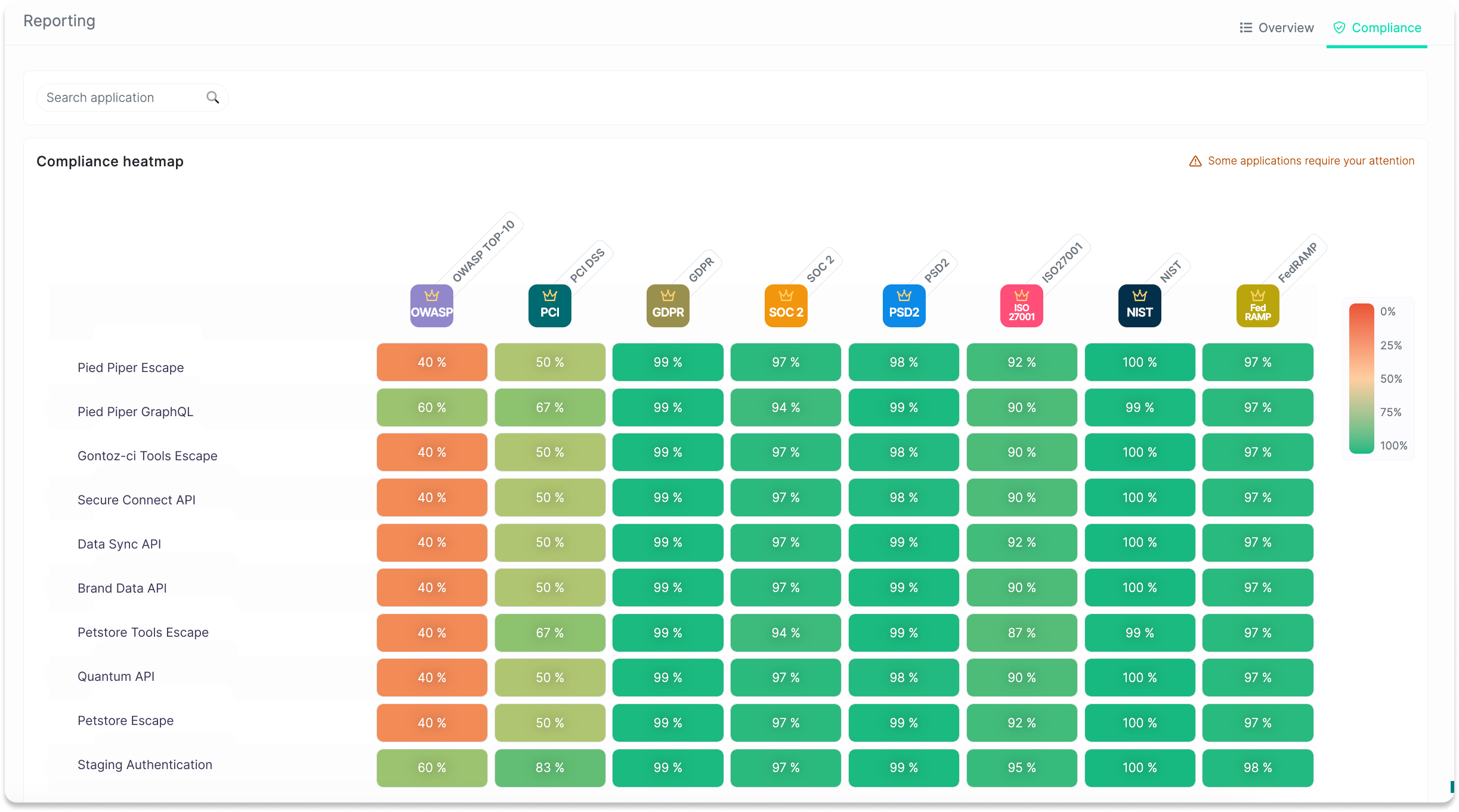
A general example of PCI DSS Escape Compliance Report and Compliance Matrix
While Rapid7 offers extensive customization options for its dashboards, available information doesn't help prioritize fixes of business-critical vulnerabilities or view applications that are compliant with relevant frameworks in a single pane of glass.
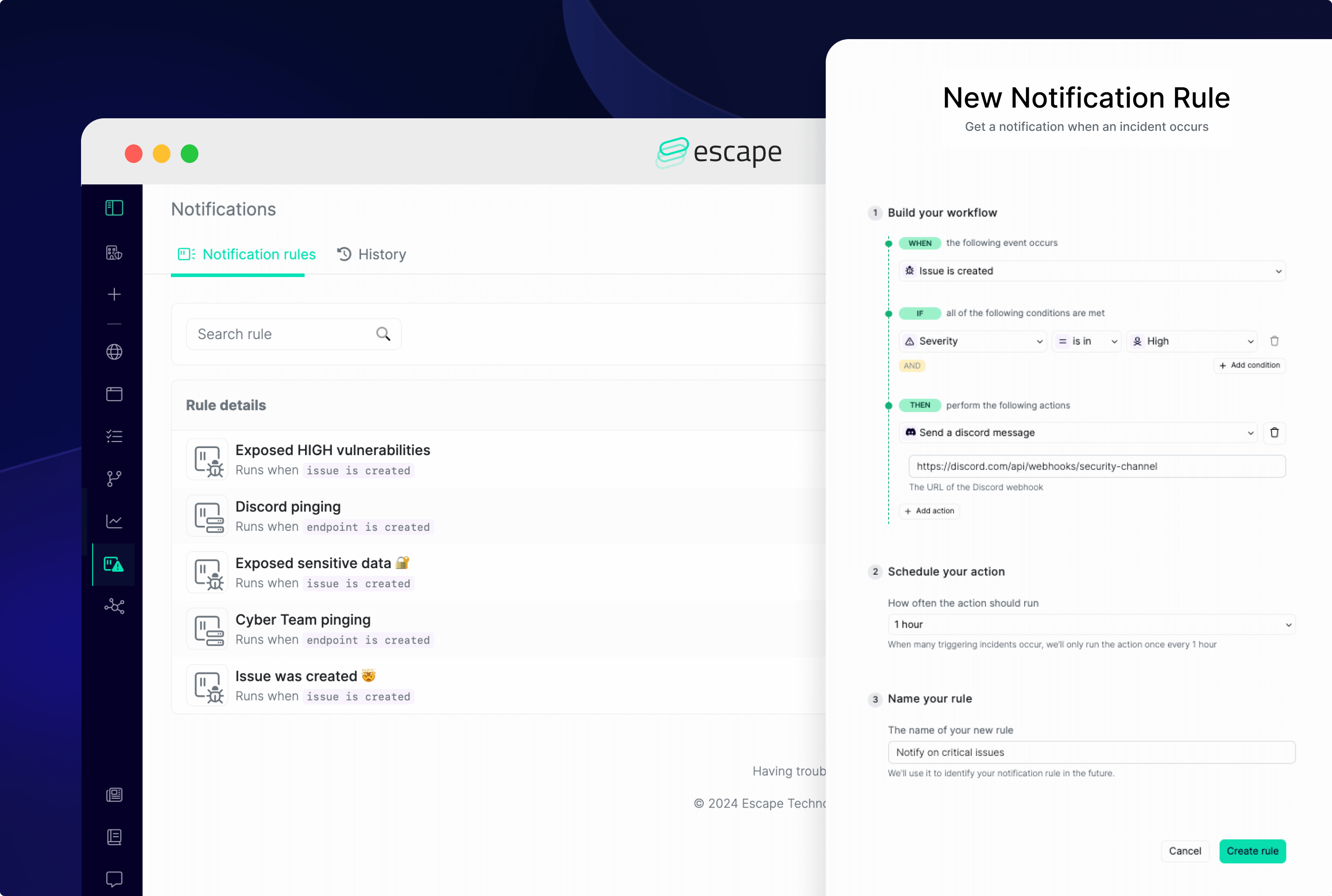
What's really missing from Rapid7 InsightAppSec is the possibility of setting custom notification rules. Staying updated on the state of your API security is critically important for application security engineers. Every second counts in identifying and mitigating vulnerabilities that could compromise sensitive data or disrupt operations.
On the contrary, Escape offers you to get notified when urgent issues arises without constantly logining in:
- When a new vulnerability has appeared in your application(s)
- When a new endpoint is created
- When scan is started
- When a scan is ended
- When a scan is failed
Recap: Pros and Cons
Side-by-side comparison table
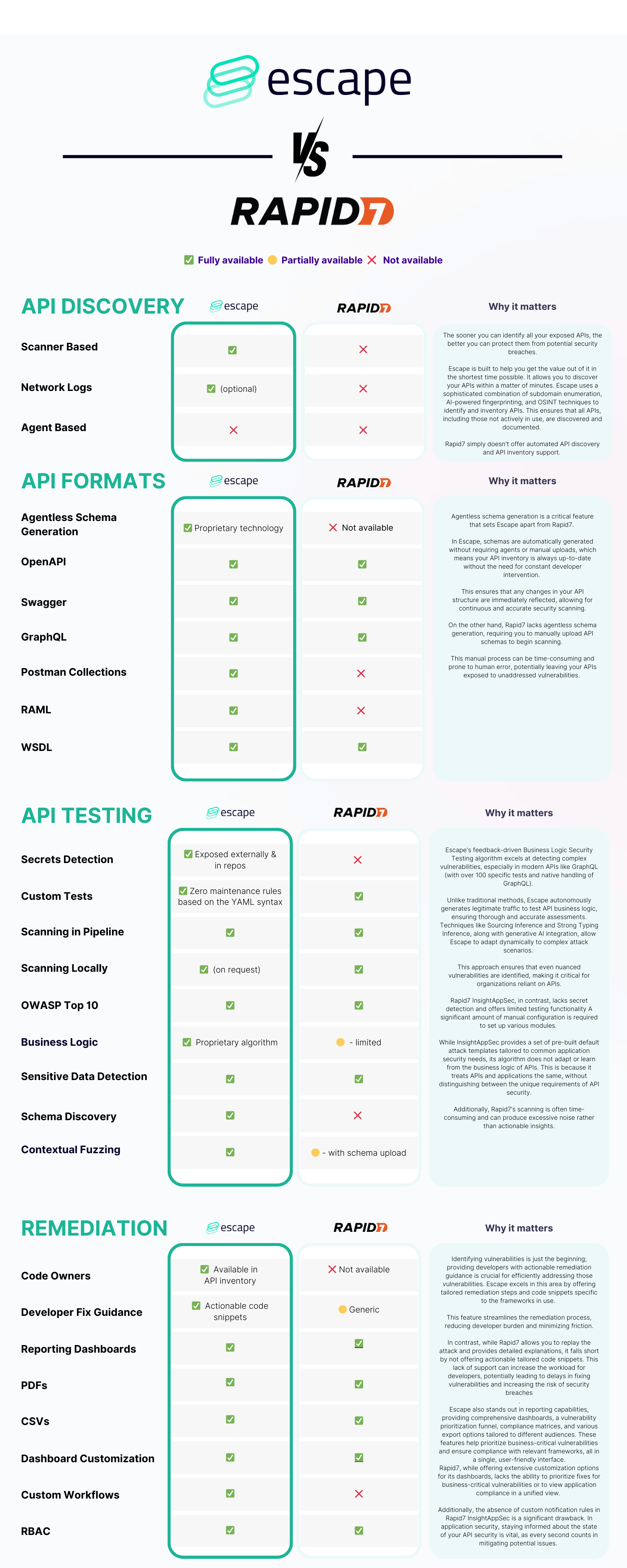
Rapid7
Pros
- Part of the overall comprehensive vulnerability platform
- Covers various applications
- Extensive dashboard customization options
- Supports Swagger files
- Custom attack templates that help to customize security testing but might require a lot of maintenance
Cons
- Lack of API discovery and inventory
- It treats APIs and applications the same, without distinguishing between the unique requirements of API security
- Long scanning times & lots of false positives
- Testing requires manually uploading schemas when they change – it doesn’t automatically detect them
- You can't accelerate the remediation process because of the lack of actionable remediation code snippets for developers.
- Lack of alerting workflows
Escape
Pros
- Addition of API discovery to its DAST scanning: Exceptional ability to discover even Shadow APIs in minutes by scanning exposed source code, reducing the time to value and risk of overlooked vulnerabilities
- Automated schema generation that helps you to launch scans right away and reduces the need for maintenance
- In-depth GraphQL testing capabilities and lowest false-positive rate
- Ability to prioritize the most critical API by business context, data sensitivity, and exposure.
- Actionable remediation code snippets for developers that help you build better relationships with them
Cons
- Advanced feature sets may require specialized knowledge
- Number of integrations with some of the operational tools
Conclusion
While Rapid7 offers a solid DAST application security scanning, it falls short in several key areas such as comprehensive API discovery, detailed testing capabilities, tailored specifically to APIs, and actionable remediation.
Escape provides a more holistic and automated approach to API discovery and security. Its focus is on agentless API discovery, automated schema generation, advanced security testing, and actionable insights for developers.
If you still have doubts, take a moment with our team and see directly during a demo what APIs your organization left exposed.
💡Want to learn more? Discover the following articles:
- Reinventing API security: Why Escape is better than traditional DAST tools
- Escape vs Burp Suite Enterprise
- Escape vs StackHawk
*** This is a Security Bloggers Network syndicated blog from Escape - The API Security Blog authored by Alexandra Charikova. Read the original post at: https://escape.tech/blog/escape-vs-rapid7-comparison/
如有侵权请联系:admin#unsafe.sh
