2024-8-23 21:0:50 Author: www.sentinelone.com(查看原文) 阅读量:6 收藏
The Good | Global Authorities Arrest Multi-Million Dollar Crypto Thieves & Charge An Extortion Gang Member
Plenty of good news this week as global law enforcement efforts rounded up suspects behind a $14 million crypto heist and officially charged a member of a Russian extortion operation responsible for data theft, ransom, wire fraud, and money laundering.
Italian authorities arrested four individuals suspected of stealing millions in cryptocurrency from Holograph, a blockchain technology firm based in the Cayman Islands. When nabbed, the suspects had been found living extravagantly in a luxury villa in Salerno. The cybercriminals are accused of exploiting a vulnerability in Holograph’s smart contract system, which enabled them to mint and withdraw one billion of the platform’s HLG tokens via nine transactions. Further investigation revealed that a former technical contractor with insider knowledge facilitated the attack. As part of the bust, police seized cryptocurrency wallet keys and electronic devices, all expected to aid in recovering the stolen funds and providing crucial evidence for the case.
In the U.S., the FBI successfully extradited and charged 33-year-old Latvian national, Deniss Zolotarjovs – a member of the notorious Russian-based Karakurt ransomware group. Arrested in Georgia in December 2023, Zolotarjovs faces charges for multiple cyberattacks between August 2021 and November 2023.
Russian national, Deniss Zolotarjovs, 33, in Butler County jail after feds extradited him from country of Georgia. He’s accused of stealing personal client info from U.S. companies – including local ones – and extorting money from them so he wouldn’t release it. @Local12 pic.twitter.com/faAuVy4NST
— David Winter (@DavidWinterTV) August 21, 2024
Operating under the alias ‘Sforza_cesarini’, he specialized in negotiating ransom payments and laundering proceeds from data theft and extortion schemes that targeted organizations worldwide. In one notable case, a victim paid over $1.3 million under coercion. Zolotarjovs’ arrest marks the first significant legal action against a Karakurt member and is expected to pave the way for further operations dismantling of the group’s criminal network and activities.
The Bad | Xeon Sender Cloud Hacktool Exploit Legitimate APIs to Conduct Spam SMS & Smishing Attacks
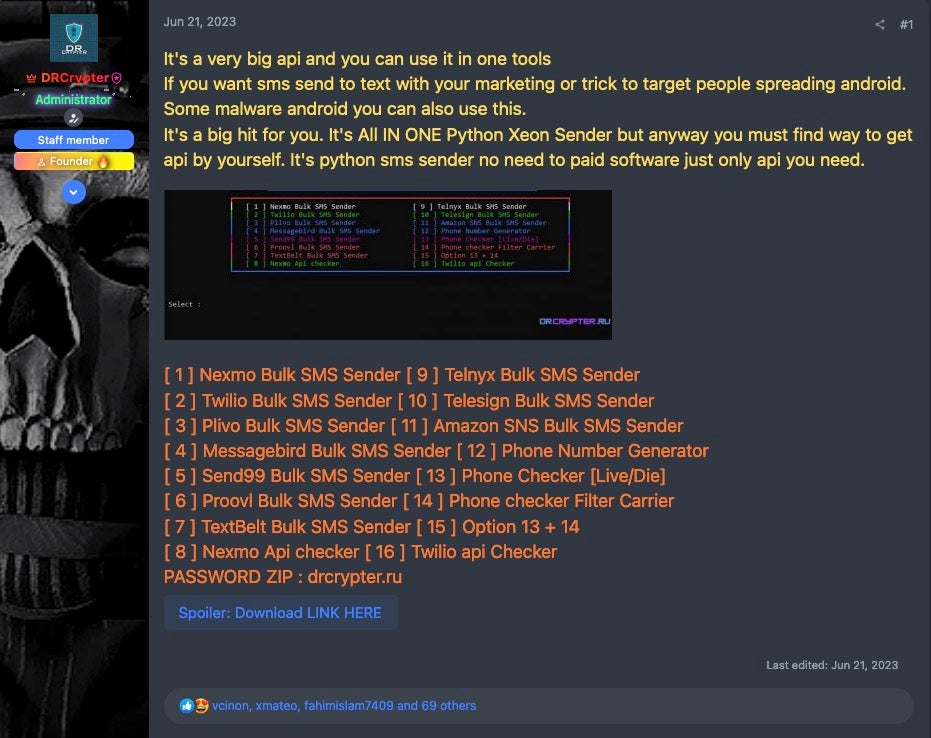
A Python script called ‘Xeon Sender’ has been making its way around the cybercriminal scene, highlighting an ongoing demand for tools that allow threat actors to attack cloud services and enable both SMS spam and smishing campaigns. Initially discovered in 2022, Xeon Sender has been repurposed by multiple threat actors, a common practice in the cloud hacking community, with each branding the tool as their own.
SentinelLabs’ latest report details how the tool exploits legitimate APIs of SaaS providers to carry out bulk SMS attacks. While Xeon Sender does not exploit any vulnerabilities within the nine different providers it uses, it does rely on valid credentials obtained by the attackers. The credentials are used to send the spam messages en masse, targeting recipients in a variety of malicious campaigns.
Xeon Sender is primarily distributed through Telegram and hacking forums, where it is popular due to the low level of technical skills needed to operate it. In one of many incarnations of the cloud attack tool for example, Xeon Sender uses a web-based GUI, removing a barrier for actors who are not comfortable running Python tools and allowing them to use the tool easily.
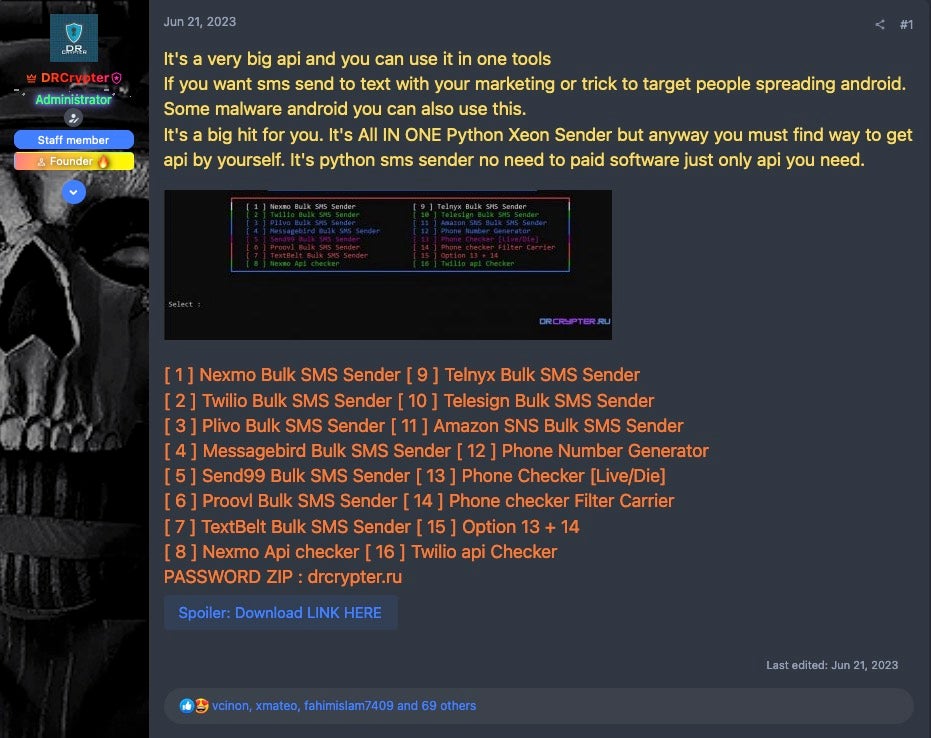
The tool also offers up a number of functions, including account validation for Nexmo and Twilio, phone number generation using the Python random module, and a phone number checker.
Organizations can defend against threats like Xeon Sender by monitoring for unusual SMS-related activities, such as changes to SMS sending permissions or large uploads of recipient phone numbers. Though the tool lacks sophistication, it is likely to continue evolving over time as different threat actors make improvements and incorporate its features in more comprehensive attack toolsets.
The Ugly | DPRK-Based Threat Actors Gain Unauthorized Access via Windows Zero-Day Flaw
New research this week unveiled a zero-day vulnerability in the Windows AFD.sys driver, allowing threat actors to elevate privileges on targeted systems. Exploitation was found to be carried out by a hacking group the researchers referred to as ‘Lazarus’, a widely-used APT reference for several related North Korean-aligned threat actors. The flaw, tracked as CVE-2024-38193 (CVSS: 7.8), was part of a Bring Your Own Vulnerable Driver (BYOVD) attack, where attackers use drivers with known vulnerabilities to gain kernel-level access.
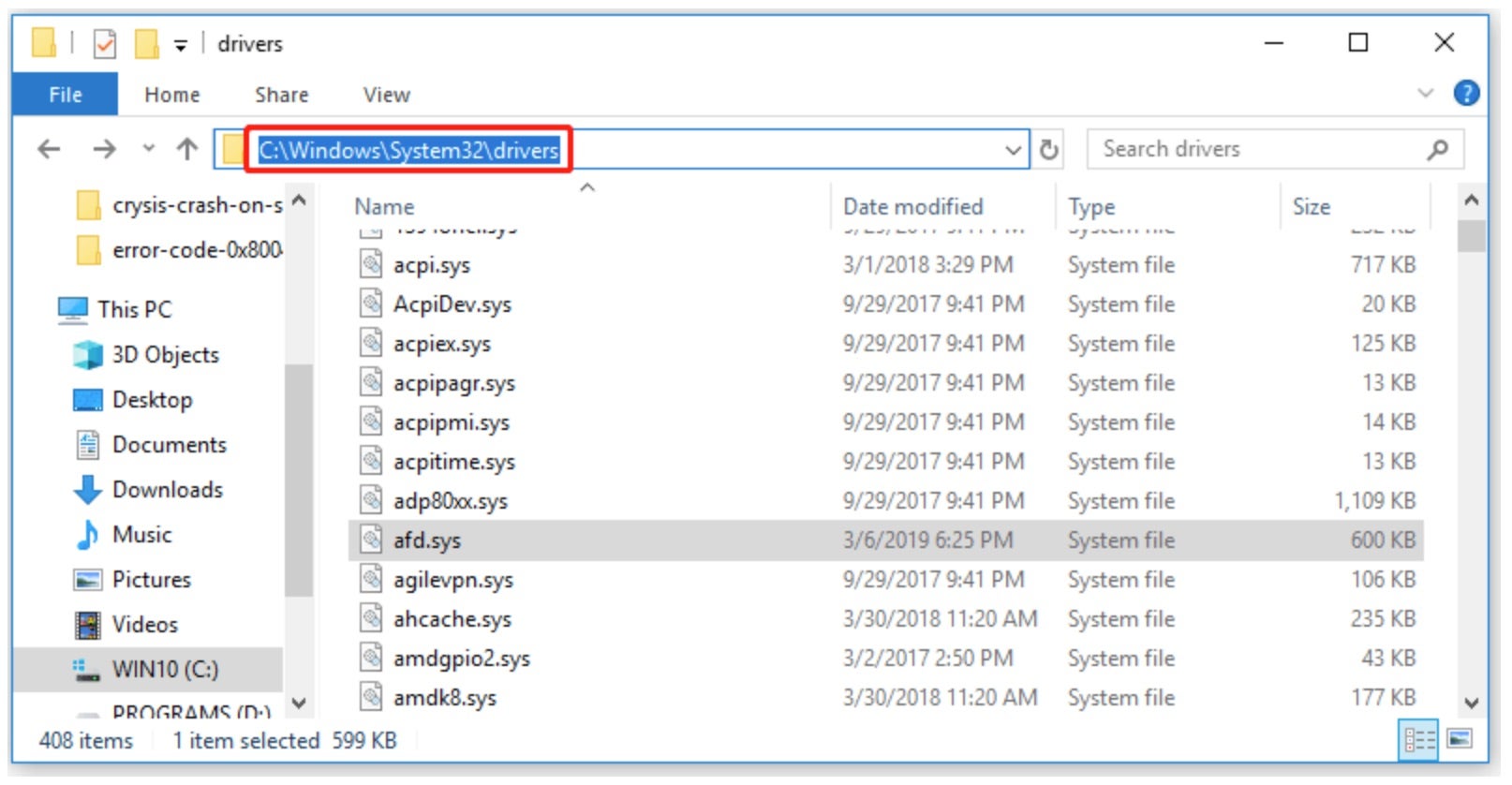
CVE-2024-38193 affects the Windows Ancillary Function Driver for Winsock, a driver that is installed by default on all Windows devices. In the hands of an attacker, it acts as an initial entry point into the Windows kernel. The North Korean threat group exploited the zero-day to disable Windows’ monitoring capabilities and avoid detection before using a rootkit called FUDModule to hide their tracks from security tools. Microsoft addressed this flaw during its August 2024 Patch Tuesday, along with several other zero-day vulnerabilities.
In BYOVD attacks, threat actors exploit known vulnerabilities in legitimate software drivers to escalate their privileges on a compromised system. After installing these drivers to access the Windows kernel – the core of the operating system – actors can execute malicious code, disable security features, and evade detection. Since these attacks leverage trusted drivers, it is difficult for legacy security tools to recognize and block the threat, leading attacks to gain deep control of the targeted environment.
Researchers link these BYOVD attacks to a wider campaign happening in Brazil, where North Korean attackers are targeting cryptocurrency professionals through fake job opportunities before luring them into installing malware. As it stands, the U.S. government has a standing reward up to $5 million for information leading to the identification or location of DPRK-sponsored hackers.
如有侵权请联系:admin#unsafe.sh