
2024-8-23 23:0:17 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
The adoption of Cloud Native Application Protection Platforms (CNAPPs) has surged, reflecting a growing recognition of the need for comprehensive security across cloud environments. According to industry reports, the global CNAPP market is projected to grow at a CAGR of over 25% from 2023 to 2028 – and 40% of enterprises already have one. This spike is fueled by the increasing complexity of cloud infrastructures and the ever-evolving threat landscape.
CNAPP Brings a New Level of Visibility
CNAPPs have proven to be powerful tools for identifying a wide array of cloud-specific security gaps, and are reporting a lot of findings in the realm of cloud identity and permissions. These platforms excel at revealing over-permissioned identities, misconfigured access policies, and potential points of exploitation. However, while CNAPPs provide valuable visibility, they often fall short when it comes to remediation, requiring findings to be dealt with one at a time, or not providing remediation paths at all. And when you factor in the sheer volume of alerts (I don’t need to go over the statistics about “alert fatigue” from SIEM / XDR / CNAPP / insert-acronym-here), you can imagine how large this backlog of unresolved issues is.
Addressing identity and permissions issues at scale is a significant challenge. Many CNAPP solutions offer detailed insights, prioritize the issues and some even offer automated remediation bots, but they all lack the capabilities to resolve these issues efficiently across large cloud environments. It’s not for lack of skill or effort: it’s an issue of volume and coordination.
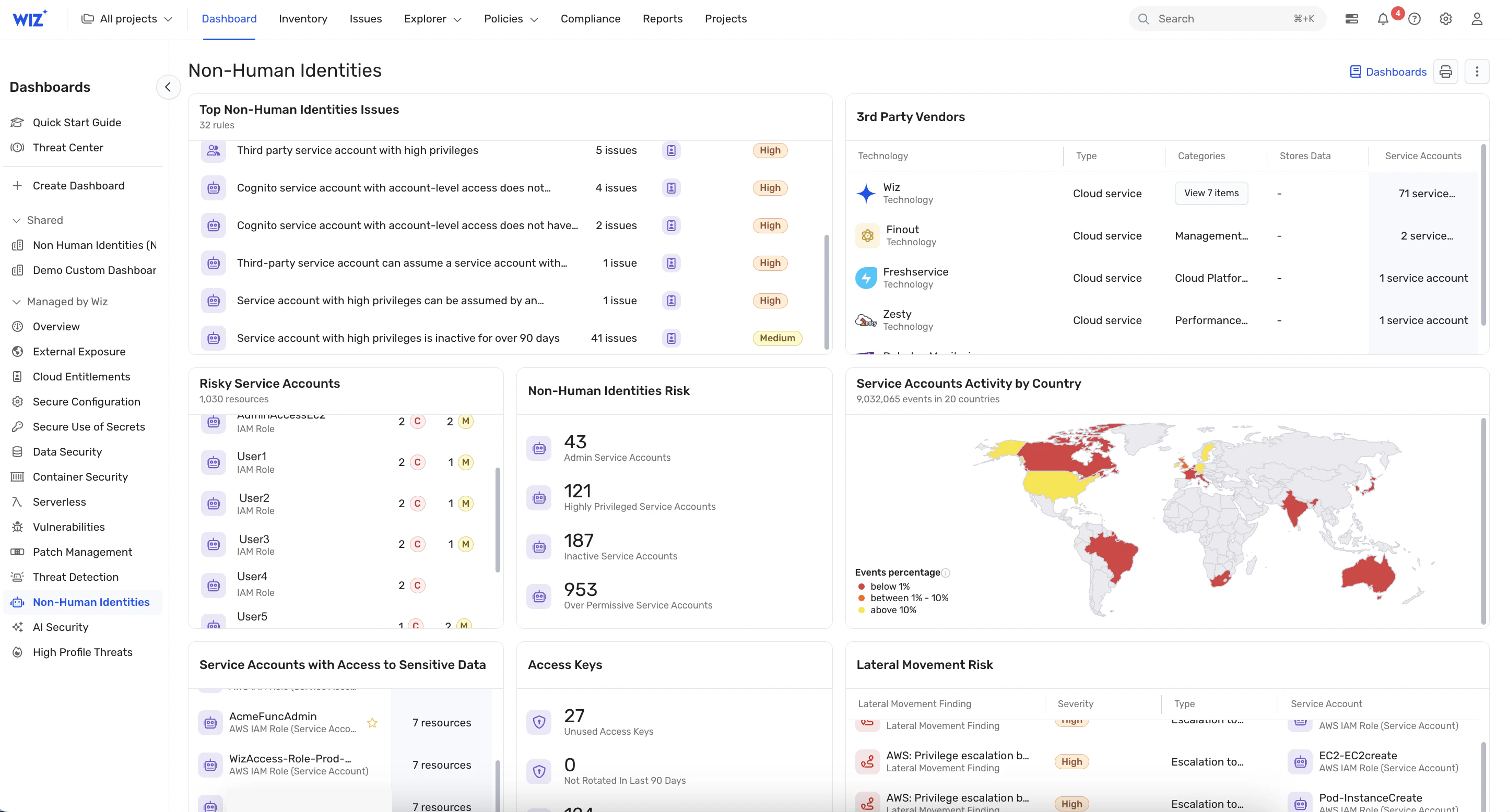
CNAPPs are finding thousands of permissions issues, particularly in machine identities. Most are struggling to clean them up. (Image courtesy Wiz blog)
A lot of Findings, A Lack of Action
Here’s what I mean: take something as simple as an unused identity. CNAPP should be able to find this easily. Once found, can you safely delete it? Are you sure it’s not there for a reason? Who owns the identity? What workload will (eventually) break if it’s removed? Answering these questions requires finding the right person – as in, who owns that account / OU / part of the cloud. If it’s a machine identity (it usually is), it’s not overtly tied to a given person or team. Now you’re on a hunt for a person, adding the complication of human coordination, scheduling, and communication to an issue that should be between you and the cloud console. Since the average cloud has 11k identities, and 61% have been unused for 90 days, multiply this process by oh, 6,000 or so. Good luck getting these cleaned up in this decade.
Along with unused identities, overpermissioned identities, lateral movement risks, and privilege escalation scenarios make for a bundle of fun that cloud teams are finally seeing, but not acting on. They simply can’t: CNAPP shines a light on the large set of problems of the modern cloud, but it doesn’t give you a machete to cut through the jungle. And if you’re not in the Dev org, you’re afraid of breaking something that’ll slow down code deployment. We’ve got bulk visibility, but not bulk action. So you’re choice is one of two options: One, take on the Sisyphean task of manually remediating hundreds, if not thousands, of permissions and identity-related risks; or Two, accept the risk and hope you’re achieving real risk reduction with the 1% of remediations you can get to. Option one means your intel is out of date even before you finish, Option two is gambling your job on a hunch that you know which unused principals and permissions are more attractive vessels for lateral movement.

Enabling the ‘Bulk Fix’ in the Identity World
Sonrai Security’s Cloud Permissions Firewall is the key to bridging the gap left by CNAPP’s intense focus on identifying issues. Instead of just highlighting problems, this solution empowers organizations to take action, enabling bulk resolutions that tackle the majority of identity and permissions issues all at once. What sets it apart is its ‘default deny’ approach, which ensures a least-privilege state is consistently maintained, even as your cloud environment grows and evolves. This capability is essential for keeping your cloud operations secure and compliant, particularly as your organization scales.
The Sonrai Cloud Permissions Firewall takes automated “bulk fixes” to the next level by combining detailed permissions analysis with a laser focus on the most critical risks. With centralized control over permissions and access, it enables swift, comprehensive actions to eliminate unused sensitive permissions, identities, services, and regions across your cloud environment. What makes this approach so effective is its ability to restore permissions on demand within seconds, ensuring that your development teams stay productive without compromising security or disrupting operations.
Consider the example of enforcing least privilege for both human and machine identities. A typical least privilege tool scans audit logs, compares the permissions actually used with those assigned to a principal, and identifies which privileges can be safely removed as “unused.” Sounds straightforward, right? But challenges arise: Which unused privileges are actually essential? Who is responsible, and who needs to approve the new policy? What could change or break if we implement it? Does this permission even pose a real security risk? And what if those permissions are needed later? The Cloud Permissions Firewall addresses these concerns by:
- Automatically identifying ownership: Quickly determines who is responsible for each permission.
- Preserving underlying permissions: Keeps the original permissions and credential grants intact.
- Focusing on risky permissions: Controls only the unused sensitive permissions that could be exploited in an attack.
- Implementing centralized restrictions: Uses a centralized policy to restrict access to unused permissions without altering existing grants. Restrictions are applied to:
- Unused sensitive permissions
- Unused identities
- Unused services
- Unused regions
- Restoring permissions as needed: Grants access back to permissions when necessary, with approval, ensuring seamless operations.
The Cloud Permissions Firewall automates the entire process, from assigning ownership to identities and analyzing logs to identify unused permissions, to writing centralized policies and generating the necessary infrastructure as code templates. It even handles exceptions and updates the relevant policies automatically. This centralized control and automation take the burden off the development teams, placing it in the hands of cloud security operations teams—without the time-consuming hassle of deploying individual policies.
Working with your CNAPP
The Cloud Permissions Firewall complements any CNAPP solution to tackle identity issues, reducing alerts, alarms, and overall risk in your cloud environment. Customers have reported that it cuts the time needed to resolve identity issues by 97%, making the goal of achieving least privilege in your cloud a reality. Instead of endlessly hacking away at a big stack of problems, Sonrai resets the paradigm: sensitive permissions and services use is regulated like network traffic used to be. Explicit grants govern all principal’s permissions – but existing traffic patterns are allowed to flow as they were, keeping productivity up.
Like any security innovation, cloud permissions risk follows the same pattern: the first step is identifying it, the second is designing a remediation, the third step is operationalizing the fix in a productive way. The first step gets all the hype. The third step is often overlooked as unsexy, but it’s the most important. After all, what’s awareness of risk worth if you can’t fix it in a timely fashion, before it gets exploited?
If you’re interested in operationalizing CNAPP’s findings and making real impact to your cloud permissions risk, check out the Cloud Permissions Firewall.

*** This is a Security Bloggers Network syndicated blog from Sonrai | Enterprise Cloud Security Platform authored by James Casagrande. Read the original post at: https://sonraisecurity.com/blog/whats-next-after-cnapp-bulk-fixes/
如有侵权请联系:admin#unsafe.sh
