2024-8-26 21:0:0 Author: www.trustwave.com(查看原文) 阅读量:5 收藏
3 Minute Read
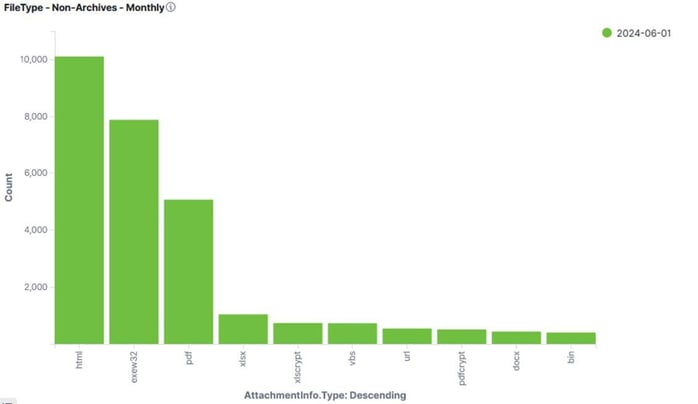
The Trustwave SpiderLabs team regularly collects a trove of data while protecting clients from email-based attacks. HTML attachments, malicious QR codes, and business email compromise (BEC) are the favored attack methods. A recent snapshot of data from June 2024 from Trustwave MailMarshal shows that email-based threat actors still favor HTML attachments to deliver a variety of malware types. Figure 1: HTML remains ahead of file types like PDFs and Excel The HTML attachments are usually used as part of general phishing attacks, redirectors, and HTML smuggling. HTML smuggling converts an executable file into an encoded text and embeds that text into the page's HTML source to evade detection. Trustwave SpiderLabs found the EXE32 attachments were most often used to deliver the following: The malicious PDF attachments spotted tended to have links redirecting victims to malware, while Excel files with macro-enabled documents can execute harmful scripts once the document is opened, potentially downloading malware. A Blended Threat is an attempt to compromise information security using multiple vectors. Attackers typical craft Blended Threat email messages to appear to be from a trusted sender, contain links to a website hosting malicious code, or attempt to entice the user into providing personal information. The BTM within MailMarshal received a major update in June 2023, with the addition of the PageML validator that inspects HTML content, extracts features, and applies an ML-based classifier to determine if the email is phishing or other suspicious content. The BTM scans incoming emails and modifies links before delivering them to the recipient. Then, the Trustwave Link Validator cloud service is activated when a user clicks on a link to check if the link is associated with phishing or other malicious activities. MailMarshal’s PageML results in more blocked phishing sites and warning displays for end users and admins. Early estimates show at least more phishing URLs are detected through PageML. It’s important to note that no action is necessary by clients, PageML is autonomous. When it came to phishing tactics and the methodologies threat actors are using to trick targets into clicking malicious links, Trustwave SpiderLabs noted that QR-code phishing remains popular, with HR-themed phishing using subject lines like Annual Leave Compliance, Bonuses, Salary Reviews, Employee Performance, and Termination notices for social engineering to trick readers into opening the email. The recent campaigns we observed use legitimate form builder services to redirect to credential harvesting sites, including 'Cognito Forms’ and 'Jot Form.' Another noticeable trend is fake e-signature phishing emails that utilize DocuSign and Adobe Sign. These are still very noticeable along with an increase in reward scams, which impersonate known brands to offer fake rewards to steal financial information. Generally, after completing a survey, users are asked for credit card information before getting the reward. Figure 2: A common rewards scam email. Trustwave SpiderLabs breaks down email spam into theme-based categories. General product offers and health (mostly advertising fake pills) spam are popular. However, phishing and malware are also significant parts of the mix of spam. Phishing was high in June due to many Japanese phishing emails mimicking Mastercard and Amazon. In June, Trustwave blocked 4,000 phishing, 1,500 malware, and 100 Business Email Compromise emails per day in MailMarshal Cloud for our clients. In per month terms, that is about 120,000 Phishing, 45,000 malware, and 3,000 BEC emails. According to data from MailMarshal cloud, BEC emails were overwhelmingly sent via free webmail platforms, with Google's Gmail being by far the most prevalent. Trustwave SpiderLabs spotted 788 BEC incidents from Gmail accounts, with Hotmail and a few other types accounting for less than 50 other attacks. The top lure, 46%, is still Request for Contact, where threat actors send short emails asking for mobile number/WhatsApp contact. Second on the list is Payroll Diversion, 31%, with subject lines like Task, Invoice Transaction, and Wire Transfer all garnering in the single digits. Figure 3: Top BEC Lures used Here is an example of how a threat actor designs an email purportedly from a CEO. It includes a level of urgency and purportedly comes from an executive that any employee would want to please. Figure 4: example of how a threat actor designs an email purportedly from a CEO Trustwave SpiderLabs' data derived from MailMarshal underscores the critical importance of robust email security solutions like MailMarshal to protect organizations from these evolving threats. By understanding the latest attack methods and leveraging advanced technologies, businesses can significantly reduce their risk of falling victim to these sophisticated attacks. MailMarshal:
MailMarshal's Blended Threat Module (BTM)
Phishing

Email Spam
Business Email Compromise


The Benefits of Trustwave MailMarshal
如有侵权请联系:admin#unsafe.sh