

August 27, 2024
Authors: Rui Ataide, Hermes Bojaxhi
The GuidePoint Research and Intelligence Team (GRIT) has been tracking a highly sophisticated threat actor, with skilled social engineering and intrusion capabilities that include native English speakers.
Based on our team’s research, we have identified several attacker domain names and IP addresses related to an ongoing campaign. This campaign is currently targeting over 130 US organizations in various industry verticals. This attack starts with the targeting of individual users within an organization to harvest credentials as well as one-time passcodes via social engineering methods.
The type of social engineering used in this campaign is particularly hard to detect given that it normally happens outside of the traditional visibility of security tools, such as via direct calls to user’s cell phones and the use of SMS/Text messaging. Unless users report receiving these types of calls or messages, the security teams might not even be aware of the attack. The threat actor can also target multiple users via this method until they successfully get a user that is susceptible to this type of attack.
Since 26 June 2024, this threat actor has registered domain names that resemble the VPN technologies used by the targeted organizations. As of the date of this blog we have observed the following domain names:
| Registration Date | Domain Name |
| 2024-06-26T11:29:19Z | ciscoweblink.com |
| 2024-06-26T11:44:28Z | ciscolinkweb.com |
| 2024-06-26T12:20:24Z | ciscolinkacc.com |
| 2024-06-26T12:29:44Z | ciscoacclink.com |
| 2024-07-01T18:52:53Z | linkciscoweb.com |
| 2024-07-03T17:42:12Z | fortivpnlink.com |
| 2024-08-20T10:16:12Z | vpnpaloalto.com |
| 2024-08-20T09:01:15Z | linkwebcisco.com |
Typically, this threat actor will call individual users on their cell phones and introduce themselves as a member of the help desk or IT staff team, calling to fix a VPN login issue. If the social engineering is successful, the threat actor then sends the user a link via SMS that points them to the malicious site that pretends to be related to the company VPN.
The threat actor has also setup custom VPN login pages for each of the targeted organizations. These pages resemble the legitimate ones from each organization, including the the available VPN groups. However, in some instances the threat actor added VPN groups, such as “TestVPN” and “RemoteVPN”, to the drop-down menu on the fake login page, likely as part of the social engineering attack.
Through these fake login pages the threat actor harvests the username, password, and token of the user if multifactor authentication (MFA) is implemented. If the MFA solution uses a push method, then the threat actor instructs the user to approve the push notification during the social engineering phone call.
The final stage of this process redirects the user to the legitimate VPN address of the targeted organization, where the user may be instructed to log in again to reassure the user that the issue is fixed.
Once this threat actor gains access to a network via VPN, they will immediately start to scan the network to identify targets for lateral movement, persistence, and further privilege escalation.
This threat actor is financially motivated, and if successful in gaining a foothold into your network, they will proceed to steal data, destroy backups, and ultimately deploy Ransomware.
What should you do?
- Check your logs for suspicious activity from VPN assigned IP addresses from the past 30 days from the day of this notification. If you identify signs of successful compromise, there may be an imminent Ransomware attack coming. You should immediately declare an incident and perform a thorough investigation.
- Inform your users of this type of social engineering method for awareness, and to immediately report calls from unknown numbers claiming to be part of the IT or help desk staff.
Indicators of Attack
Based on Validin data, the current IP addresses associated with the domain names of this campaign are shown below, along with First Seen and Last Seen dates.
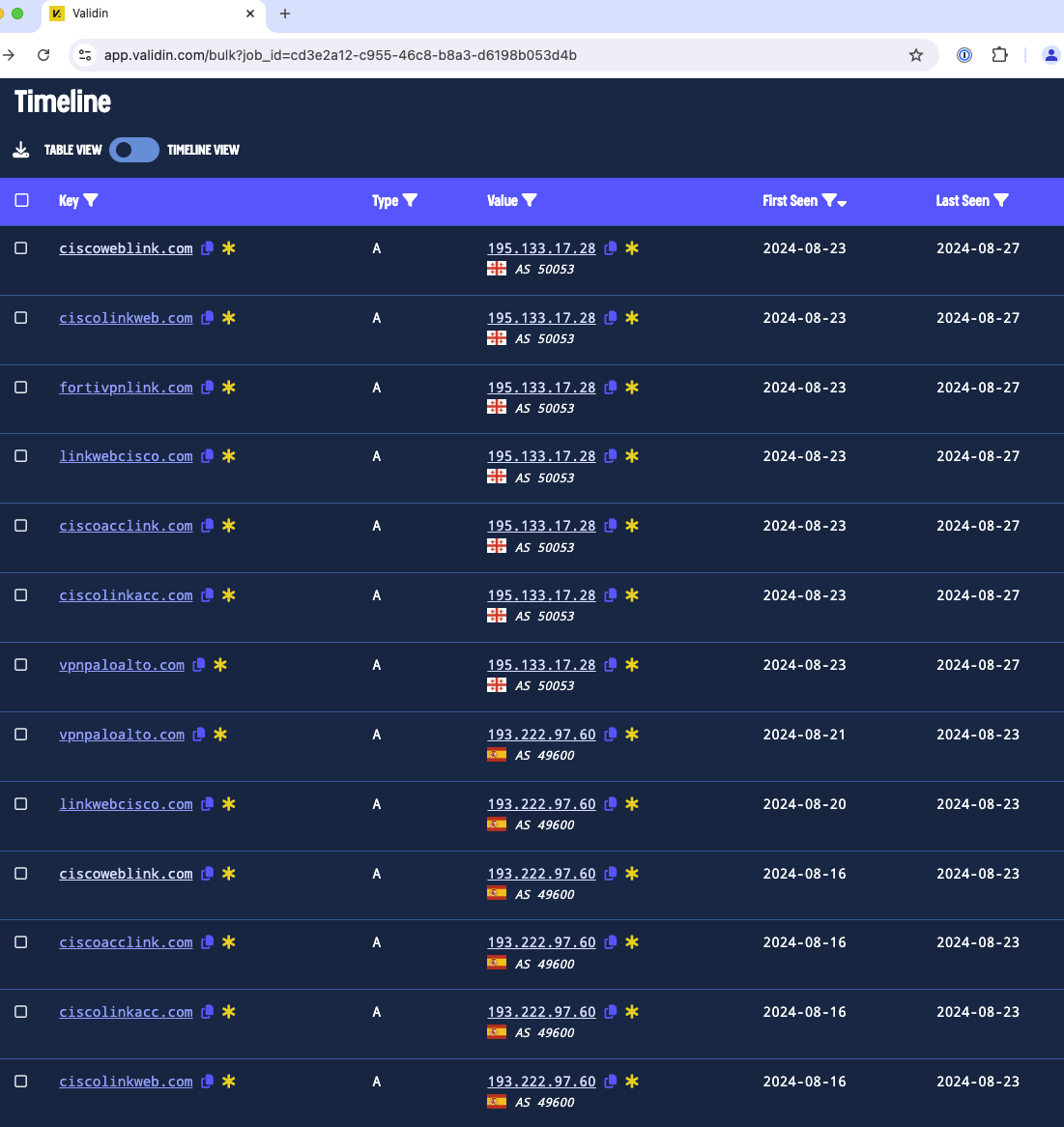
The unique list of IP addresses observed as of the date of this blog is as follows:
195.133.17.28
193.222.97.60
147.45.114.159
147.45.114.99
185.218.0.78
185.68.93.232
185.68.93.72
193.17.183.136
194.169.163.156
212.113.103.123
45.76.239.33
The list of domain names associated with this campaign as of the date of this blog is as follows:
ciscoweblink.com
ciscolinkweb.com
ciscolinkacc.com
ciscoacclink.com
linkciscoweb.com
fortivpnlink.com
vpnpaloalto.com
linkwebcisco.com
For more information related to this threat or for help defending against it, please Contact Us.
*** This is a Security Bloggers Network syndicated blog from The Guiding Point | GuidePoint Security authored by GuidePoint Security. Read the original post at: https://www.guidepointsecurity.com/blog/so-phish-ticated-attacks/
如有侵权请联系:admin#unsafe.sh
