
2024-8-29 02:56:32 Author: securityboulevard.com(查看原文) 阅读量:9 收藏
There’s a well known mental model that lays out the premise that “the map is not the territory.” It’s a reminder that the representation of something is not the thing itself. If it were to represent it with perfect fidelity, it would no longer be a reduction and thus would no longer be useful to have as a separate tool. I’ve been thinking about this analogy in relation to dspm vendors.
At Symmetry, we’ve used the analogy before that Data Security Posture Management (DSPM) vendors provide a map to your data. As a result, we’ve invested in insightful data visualization to make our product as user friendly and outcome focused as Google Maps. Just like with a map, we’re not looking for a tool that merely shows us where we are, but one that guides us through the actual, often complex terrain of datasets and permissions to that data to get us safely where we need to go.
TLDR: In this blog, we outline how a DSPM vendor shouldn’t just illustrate your current state of data but actively guide you through the complexities of securing your data environment, and how to make this decision.
The Map: DSPM Vendors need to get you to an outcome
Maps are one of the oldest tools that humanity has relied on to understand and navigate the world around us. But a map is just that—a representation, a simplified version of reality. When you open a map application like Google Maps or Apple Maps, you’re not engaging with the actual roads, streets, and landscapes. Instead, you’re looking at a tool that translates the complexities of the real world into something you can use to navigate it effectively.
In the world of data security, the same principle applies. Your organization’s data environment is vast, complex, and constantly evolving. A DSPM vendor, much like a map, provides a way to visualize and manage that complexity. However, just like a map is not the physical terrain, a DSPM tool is not your actual data landscape—it’s a representation. The tool should help you understand and navigate this landscape, but it’s essential to remember that it’s not the territory itself.
The real value of a map isn’t in its ability to show you where you are —something you likely already know—but in its ability to guide you to where you need to be. Similarly, a DSPM vendor should not just confirm the classification of known data repositories but should also help you discover uncharted data stores, identify unseen attack surfaces to that data, and guide your security posture to a more resilient state. The journey toward a secure data environment is ongoing and dynamic, requiring tools that do more than just provide static snapshots of your data security.
The Importance of the Journey: DSPM Vendor Efficiency and Adaptability
When you choose a map application, you’re not looking for something that merely displays your current location. You want a tool that can efficiently guide you from point A to point B, offering the best possible route while avoiding obstacles like traffic or road closures. This efficiency is crucial because it saves time, reduces stress, and ensures you reach your destination without unnecessary detours. Google Maps and others do this, by sampling activity on the roads to forecast what is happening on the roads.
In the same vein, a DSPM tool needs to be efficient and adaptable. It should provide real-time insights into your data security posture, by monitoring what is happening and thereby helping you quickly identify and address risks. But more importantly, it should adapt to the ever-changing landscape of data security. New threats emerge constantly, and your tool needs to evolve alongside these challenges. Just as a map application updates in real time to reflect current traffic conditions, a DSPM tool should continually update its assessments and recommendations based on the latest threats and vulnerabilities.
Efficiency also extends to how the tool integrates with your existing processes and systems – the ease of CarPlay is a great example. A good DSPM tool should seamlessly fit into your organization’s workflow, providing value without adding unnecessary complexity. It should help you streamline your data security operations, making it easier to manage and protect your data. The goal is to enhance your security posture without overwhelming your team with additional tasks or steep learning curves.
Choosing the Gartner DSPM Vendor needs Real World Testing
When deciding whether a map tool is right for you, you don’t test it in your backyard, where you already know the layout. Instead, you take it on the road, testing it in unfamiliar places where you need reliable guidance. You rely on it to navigate through unfamiliar cities, find the quickest route during rush hour, or locate the best detours when the main road is blocked. This real-world testing is crucial because it reveals the tool’s true capabilities and limitations.
Similarly, when selecting a DSPM tool, you need to evaluate it in real-world environments. It’s not enough to run the tool against known data or obvious security risks—doing so only proves that it can handle what you already know and could have found out yourself. Instead, test it in the unpredictable, messy, and often chaotic reality of your real world environment. Your organization’s data is likely spread across multiple environments—on-premises, in the cloud, across various third-party services—and a good DSPM tool needs to be able to navigate all of these terrains effectively.
During your evaluation, consider how well the tool uncovers hidden data stores or identifies risks that weren’t on your radar. Does it offer actionable insights, or does it simply point out the obvious? How does it perform when faced with emerging threats or newly discovered vulnerabilities? A robust DSPM tool should provide real-time, actionable intelligence, guiding you through the complexities of securing your data environment, no matter how challenging the terrain.
Furthermore, consider how the tool handles ongoing changes in your data environment. Your data landscape is not static—it’s constantly evolving as your organization grows, adopts new technologies, and faces new security challenges.
Real World Testing needs Strong Safeguards
Testing a DSPM properly is only possible with a deployment model that firstly doesn’t relinquish control and custody of your data to a third party, and with an architecture and proven capability to not impact production in any way. This effectively discounts the use of agents or any proxy implementation.
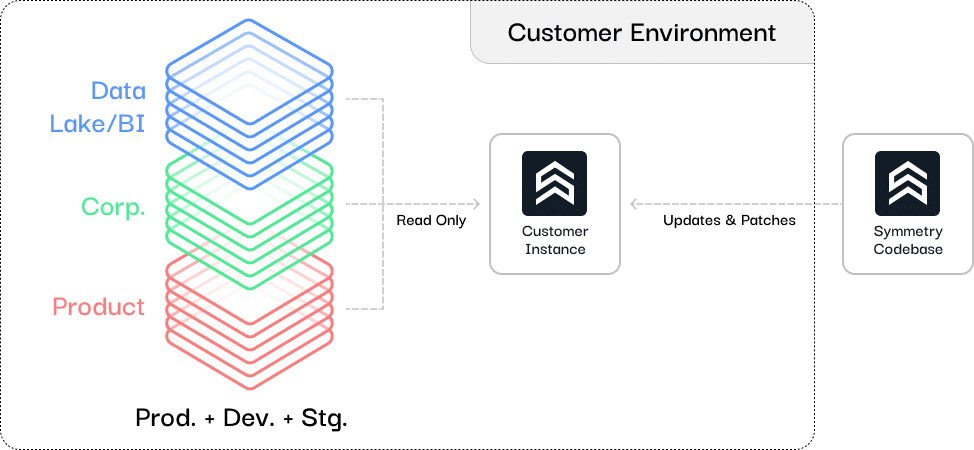
Recognizing the Territory: Navigating the Complex Data Landscape
“The map is not the territory” also reminds us that no tool can perfectly represent the complexities of real-world data environments. Every organization’s data landscape is unique, shaped by its specific needs, challenges, and goals. A DSPM tool should go beyond simply illustrating this landscape; it should help you understand and navigate it effectively.
Consider the difference between a DSPM tool that offers actionable guidance versus one that attempts to “classify every byte” of your data. The latter approach is akin to trying to catalog every detail of a territory on a map—mapping out every tree, rock, and blade of grass. While this may sound thorough, it’s often impractical and overwhelming. The more time you spend categorizing every byte of data, the more you risk losing sight of the bigger picture—what truly matters for your security posture. Just as a map focuses on roads, landmarks, and routes that help you navigate, a strong DSPM tool should prioritize what’s most important: identifying high-risk areas, uncovering hidden vulnerabilities, and guiding you to secure your critical assets. It’s about understanding where to focus your efforts, rather than getting bogged down in the minutiae.
Pay for every byte when you classify every byte
At first glance, the “classify every byte” approach might appear cost-effective, especially when the costs are hidden behind venture-funded investments. When a tool is subsidized by external funding, the financial burden on the end-user might seem minimal or even negligible in the short term. This can create an illusion of value—an enticing offer of comprehensive data classification at a fraction of the actual cost. However, this perceived cost-effectiveness is often deceptive. As the venture funding diminishes or the true costs of maintaining and scaling such an approach become apparent, organizations may find themselves facing unexpected financial burdens. The initial subsidy masks the significant resources required to sustain the “classify every byte” methodology, which can include not just financial costs, but also time, manpower, and the potential for analysis paralysis.
Instead, a good DSPM tool should recognize the complexity of your data environment and provide targeted, actionable insights in a cost effective way – i.e. it’s the map not the territory. By understanding the directions and not getting lost in the details, you can make informed decisions that strengthen your organization’s security posture and keep your data protected against evolving threats.
Conclusion: Choose a DSPM Vendor that delivers Outcomes that Matter
In the end, the right DSPM vendor is not just a Gartner DSPM vendor —it doesn’t just show you what you already know, it helps you navigate, adapt to changes, and reach your destination safely without having to memorize the entire terrain.
As you evaluate your options, keep in mind the importance of real-world testing, adaptability, and the ability to navigate the unique complexities of your data environment. Choose a DSPM tool that not only maps out your current data security state but also guides you through the ever-evolving challenges of data security, ensuring that your organization remains secure, resilient, and prepared for whatever lies ahead.
如有侵权请联系:admin#unsafe.sh
